NVIDIA Struts Its Telco Transformation Stuff at GTC, Announces AT&T Adoption of AI
The use of artificial intelligence (AI), and especially GPU-powered AI, can help telcos solve some of their biggest challenges.Killnet and AnonymousSudan DDoS attack Australian university websites, and threaten more attacks — here’s what to do about it


Over the past 24 hours, Cloudflare has observed HTTP DDoS attacks targeting university websites in Australia. Universities were the first of several groups publicly targeted by the pro-Russian hacker group Killnet and their affiliate AnonymousSudan, as revealed in a recent Telegram post. The threat actors called for additional attacks against 8 universities, 10 airports, and 8 hospital websites in Australia beginning on Tuesday, March 28.
Killnet is a loosely formed group of individuals who collaborate via Telegram. Their Telegram channels provide a space for pro-Russian sympathizers to volunteer their expertise by participating in cyberattacks against western interests.
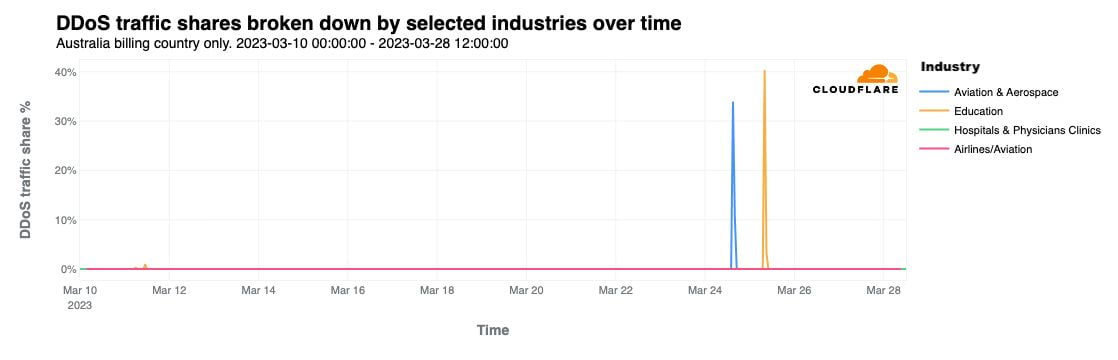
This is not the first time Cloudflare has reported on Killnet activity. On February 2, 2023 we noted in a blog that a pro-Russian hacktivist group — claiming to be part of Killnet — was targeting multiple healthcare organizations in the US. In October 2022, Killnet called to attack US airport websites, and attacked the US Treasury the following month.
As seen with past attacks from this group, these most recent attacks do not seem to be originating from a single botnet, and the attack methods and sources seem to vary, suggesting Continue reading
Studying EVPN to Prepare for a Job Interview
An ipSpace.net subscriber sent me this question:
I am on job hunting. I have secured an interview and they will probably ask me about VxLAN BGP EVPN fabrics. If you have some time, it would be a great help for me if you could tell me 1 or 2 questions that you would ask in such interviews.
TL&DR: He got the job. Congratulations!
Studying EVPN to Prepare for a Job Interview
An ipSpace.net subscriber sent me this question:
I am on job hunting. I have secured an interview and they will probably ask me about VxLAN BGP EVPN fabrics. If you have some time, it would be a great help for me if you could tell me 1 or 2 questions that you would ask in such interviews.
TL&DR: He got the job. Congratulations!
Myth Busting: You Can’t Use Packet Monitoring for Enterprise Security
Security teams today realize the value of packet monitoring for cybersecurity. As they find more uses for packet monitoring, they shatter the myth that the latter is insufficient on its own.Cloudflare’s commitment to the 2023 Summit for Democracy

On Tuesday, March 28, 2023, the US Government will launch the Summit for Democracy 2023, following up on the inaugural Summit for Democracy 2021. The Summit is co-hosted by the United States, Costa Rica, Zambia, the Netherlands, and South Korea. Cloudflare is proud to participate in and contribute commitments to the Summit because we believe that everyone should have access to an Internet that is faster, more reliable, more private, and more secure. We work to ensure that the responsibility to respect human rights is embedded throughout our business functions. Cloudflare’s mission — to help build a better Internet — reflects a long-standing belief that we can help make the Internet better for everyone.
Our mission and core values dovetail with the Summit’s goals of strengthening democratic governance, respect for human rights and human rights defenders, and working in partnership to strengthen respect for these values. As we have written about before, access to the Internet allows activists and human rights defenders to expose abuses across the globe, allows collective causes to grow into global movements, and provides the foundation for large-scale organizing for political and social change in ways that have never been possible before.

What is Continue reading
What Happened to Leaf Switches with Four Uplinks?
The last time I spent days poring over vendor datasheets collecting information for the overview part of Data Center Fabrics webinar a lot of 1RU data center leaf switches came in two form factors:
- 48 low-speed server-facing ports and 4 high-speed uplinks
- 32 high-speed ports that you could break out into four times as many low-speed ports (but not all of them)
I expected the ratios to stay the same when the industry moved from 10/40 GE to 25/100 GE switches. I was wrong – most 1RU leaf data center switches based on recent Broadcom silicon (Trident-3 or Trident-4) have between eight and twelve uplinks.
What Happened to Leaf Switches with Four Uplinks?
The last time I spent days poring over vendor datasheets collecting information for the overview part of Data Center Fabrics webinar a lot of 1RU data center leaf switches came in two form factors:
- 48 low-speed server-facing ports and 4 high-speed uplinks
- 32 high-speed ports that you could break out into four times as many low-speed ports (but not all of them)
I expected the ratios to stay the same when the industry moved from 10/40 GE to 25/100 GE switches. I was wrong – most 1RU leaf data center switches based on recent Broadcom silicon (Trident-3 or Trident-4) have between eight and twelve uplinks.
Tech Bytes: Choosing Single-Vendor SASE For Networking And Security (Sponsored)
Today on the Tech Bytes podcast, sponsored by Palo Alto Networks, we get into Secure Access Services Edge (SASE), which combines SD-WAN with cloud-delivered security services. You can integrate parts from different vendors, but Palo Alto Networks is here to make a case for why you might want to consider a single-vendor approach.
The post Tech Bytes: Choosing Single-Vendor SASE For Networking And Security (Sponsored) appeared first on Packet Pushers.
Tech Bytes: Choosing Single-Vendor SASE For Networking And Security (Sponsored)
Today on the Tech Bytes podcast, sponsored by Palo Alto Networks, we get into Secure Access Services Edge (SASE), which combines SD-WAN with cloud-delivered security services. You can integrate parts from different vendors, but Palo Alto Networks is here to make a case for why you might want to consider a single-vendor approach.Network Break 423: Arista Woos Large Enterprises With New SD-WAN Router; Google Breaks Glass Enterprise
This week's Network Break covers Arista's new WAN routers that get the company into the SD-WAN market, debates whether Aryaka targeting SMEs is a sign of problems or opportunity, and discusses an update on the size of the SASE market. We also look at an HPE acquisition, the use of exploding USBs to target journalists, space networking, and more.
The post Network Break 423: Arista Woos Large Enterprises With New SD-WAN Router; Google Breaks Glass Enterprise appeared first on Packet Pushers.
Network Break 423: Arista Woos Large Enterprises With New SD-WAN Router; Google Breaks Glass Enterprise
This week's Network Break covers Arista's new WAN routers that get the company into the SD-WAN market, debates whether Aryaka targeting SMEs is a sign of problems or opportunity, and discusses an update on the size of the SASE market. We also look at an HPE acquisition, the use of exploding USBs to target journalists, space networking, and more.VyOS dropped packet notifications
VyOS with Host sFlow agent describes how to configure and analyze industry standard sFlow telemetry recently added to the VyOS open source router platform. This article discusses sFlow dropped packet notifications support added to the latest release.Dropped packets have a profound impact on network performance and availability. Packet discards due to congestion can significantly impact application performance. Dropped packets due to black hole routes, expired TTLs, MTU mismatches, etc. can result in insidious connection failures that are time consuming and difficult to diagnose. Visibility into dropped packets offers significant benefits for network troubleshooting, providing real-time network-wide visibility into the specific packets that were dropped as well the reason the packet was dropped. This visibility instantly reveals the root cause of drops and the impacted connections.
vyos@vyos:~$ show version
Version: VyOS 1.4-rolling-202303260914
Release train: current
Built by: [email protected]
Built on: Sun 26 Mar 2023 09:14 UTC
Build UUID: 72b34f74-bfcd-4b51-9b95-544319c2dac5
Build commit ID: d68bda6a295ba9
Architecture: x86_64
Boot via: installed image
System type: guest
Hardware vendor: innotek GmbH
Hardware model: VirtualBox
Hardware S/N: 0
Hardware UUID: df0a2b79-b8c4-8342-a27f-76aa3e52ad6d
Copyright: VyOS maintainers and contributors
Verify that the version of of VyOS is VyOS 1.4-rolling-202303260914 or later.
On VyOS dropped packet monitoring Continue readingIntroducing our first Authorized Service Delivery Partners for Cloudflare One


Cloudflare's commitment to building the most compelling and easy-to-use SASE platform on the market has led to significant growth over the past year. Cloudflare One services have seen the fastest adoption among our customers, with a 3x increase in partner bookings and a 70% YoY increase in transacting partners. Partners consistently cite the simplicity of our platform, our innovation, and our global network as key differentiators that are driving strong customer demand.
To continue building on this momentum and deliver required services that our customers may require, we previously announced the creation of our new specialization track for Authorized Services Delivery Partners (ASDP) as part of our efforts to continue growing our partnership program.
Cloudflare's Authorized Services Delivery Partner track is designed to authorize partners that meet our high standards for professional services delivery around Cloudflare One. Partners who undergo the rigorous technical validation process and meet the criteria for security, performance, and reliability of their services delivery capabilities are designated as Cloudflare Authorized Service Delivery Partners. This designation provides a variety of benefits, including access to Cloudflare One sourced opportunities requiring services, access to named Cloudflare One Service Delivery Managers, and access to special partner incentive funds designed to Continue reading
Home Automation — Finally Roller Curtains and Nightmares
< MEDIUM: https://raaki-88.medium.com/home-automation-finally-roller-curtains-and-nightmares-b8ef1fc473d9 >
Am a fan and enthusiast of home automation, tried various things in the past and now settled with few things which I would like to share.
- Light Automation is the first and most popular thing to do — Initially I started wiring with PIR sensor available in Amazon, later upgraded the entire light system to Philips Hue and along with Philips Motion sensor, so far so good. Its expensive than my initial solution but had to choose that because of wired vs wireless situation in home
- Smart-plugs are another common set of devices — while I have both combinations of commercially available one and also I personally flashed few of Sonoff smart switches with Tasmota firmware
. . .
Lets get to the Curtain Rollers — So for these here is the catch, I have a remote for these and thats about it, nothing more nothing less, My ideas were mostly around having network connectivity and manipulating them.
- First and foremost thought that these are blue-tooth based and am wrong
- I went to DFROBOT and bought IR-Transmitter and IR-Receiver, nope they dint work
- I went Amazon and bought some other IR-transmitter and Receiver — Again, wasted a Continue reading
Enabling Nested-Virtualisation on Google cloud platform Instance
< MEDIUM: https://raaki-88.medium.com/enabling-nested-virtualisation-on-google-cloud-platform-instance-7f80f3120834 >
Important Excerpt from the below page.
https://cloud.google.com/compute/docs/instances/nested-virtualization/overview
You must run Linux-based OSes that can run QEMU; you can’t use Windows Server images.
You can’t use E2, N2D, or N1 with attached GPUs, and A2 machine types.
You must use Intel Haswell or later processors; AMD processors are not supported. If the default processor for a zone is Sandy Bridge or Ivy Bridge, change the minimum CPU selection for the VMs in that zone to Intel Haswell or later. For information about the processors supported in each zone, see Available regions and zones.
Though there are many use cases, I will speak from a networking standpoint. Let us say you need to do some sort of lab based on popular vMX Juniper or Cisco or any other vendor, if you have a bare metal instance, you have the ability to access the virtualised CPU cores and allocate them to the Qemu which will be the underlying emulator.
Issue
Almost by default most of the cloud providers will disable access to VT-x because of various reasons and some instances are not capable of supporting this by default. So either choose a custom instance with Continue reading
