IGP LDP Synchronization
I implore all my readers to always remember this topic: IGP LDP synchronization. It is important to use IGP LDP synchronization to avoid blackholing, especially when MPLS networks fails to function effectively. In the topology above, IS-IS is running in the network of the service provider. For the transport label distribution or topmost label/tunnel label, […]
The post IGP LDP Synchronization appeared first on Network Design and Architecture.
2015 End of Year Blog Statistics
Happy New Year! As is my tradition, here are the 2015 blog statistics as compared to 2014.
I'm pretty excited that once again readership and overall reach of this blog has increased by double digits. I'm looking forward to growing these numbers and creating challenging and interesting new content in 2016.
2015 Recap and 2016 Goals
Wow, it’s that time of year again! 2015 went by really quickly, and a lot has changed for me. It’s also worth mentioning that this is the first year-end recap to be published on my new github pages site!
If you haven’t seen this kind of thing before, I make this post yearly to publicly track my own professional development goals. I find this helps me stay accountable to these goals, and it also allows others to give me a kick in the butt if I’m falling behind.
2015 Goal Recap
First, let me recap some of the goals I set for myself at the beginning of the year, and see how well I did.
Public Presence (aka Community Contributions)
Last year I added this goal because I was doing a lot more than just blogging, and wanted to capture it all. This was a good move, since - as expected - I did quite a bit of community-oriented work, and a large portion of it didn’t take place on the blog. So, while I didn’t hit that (admittedly fairly arbitrary) 50 post number, I can say I truly feel good about what little writing I did manage to Continue reading
2015 Recap and 2016 Goals
Wow, it’s that time of year again! 2015 went by really quickly, and a lot has changed for me. It’s also worth mentioning that this is the first year-end recap to be published on my new github pages site! If you haven’t seen this kind of thing before, I make this post yearly to publicly track my own professional development goals. I find this helps me stay accountable to these goals, and it also allows others to give me a kick in the butt if I’m falling behind.2015 Recap and 2016 Goals
Wow, it’s that time of year again! 2015 went by really quickly, and a lot has changed for me. It’s also worth mentioning that this is the first year-end recap to be published on my new github pages site! If you haven’t seen this kind of thing before, I make this post yearly to publicly track my own professional development goals. I find this helps me stay accountable to these goals, and it also allows others to give me a kick in the butt if I’m falling behind.Ian Murdock, Debian Founder, Dies at 42
 The industry mourns a key figure in the history of open source software.
The industry mourns a key figure in the history of open source software.
Huawei Brings Transport SDN to China Unicom
 They like to rename things that everyone else is also doing.
They like to rename things that everyone else is also doing.
Cairo, Egypt: CloudFlare’s 74th Data Center

It’s been a big year of expansion for CloudFlare’s global network as we added new data centers across six continents, and we’re certainly not done. Today we announce the launch of our newest data center in Cairo, Egypt and a partnership with Telecom Egypt. This marks our third data center in Africa, after Johannesburg and Mombasa, and our 74th data center globally.
Faster performance across Egypt
For many years, CloudFlare has been trusted by Egyptian websites to be protected from attacks.
Over half of the 20 most popular websites in Egypt already use CloudFlare to be safe, and are now seeing a 2x improvement in performance.
Reduced latency to Egypt's largest network, Telecom Egypt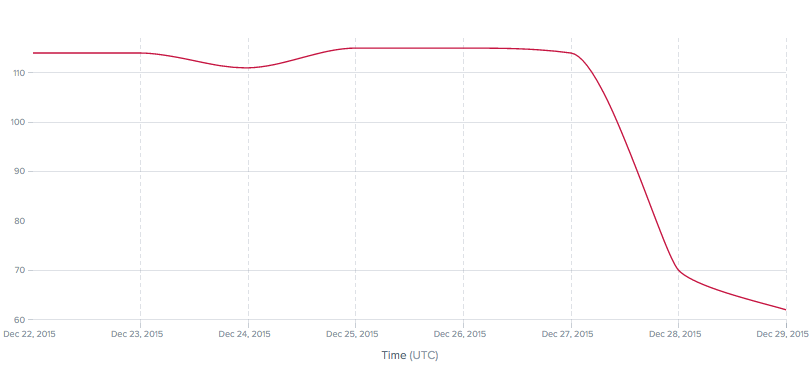
Local Deployments
Just like in Egypt, we partner with ISPs globally by deploying caches directly into their facilities. These points of presence help major networks improve the performance of millions of websites, reduce their costs and capacity used in accessing our customers' content, and provide a direct local interconnect with critical Internet infrastructure. If you are a carrier or Internet service provider in Egypt, elsewhere in Africa or anywhere around the world that would like to request a CloudFlare cache deployment, please reach out to Continue reading
HPE Says Telefónica Just Wants a Multivendor Network
 HPE will have to share the NFV glory but says it's not out of Telefónica's plans.
HPE will have to share the NFV glory but says it's not out of Telefónica's plans.
Avaya NV Report Webinar Q&A + Video: Five Compelling Reasons Network Virtualization and SDN Can (and Should) Extend Beyond the Data Center
 Read the full Q&A and watch the video for the SDxCentral NV Report Webinar sponsored by Avaya where experts elaborate on why network virtualization and SDN should reach further than the data center.
Read the full Q&A and watch the video for the SDxCentral NV Report Webinar sponsored by Avaya where experts elaborate on why network virtualization and SDN should reach further than the data center.
Last Chance! Unlock the Potential of Your Data Center Fabric Through True Analytics & Insight
 Register today for the SDxCentral and Pluribus Networks Network Virtualization Report webinar where you'll learn the true value of analytics and insights in the data center.
Register today for the SDxCentral and Pluribus Networks Network Virtualization Report webinar where you'll learn the true value of analytics and insights in the data center.
NFV: Not Ready for Prime Time but Working on It
 Only a few years old, NFV passed some milestones in 2015.
Only a few years old, NFV passed some milestones in 2015.
Micro-segmentation: Split And Smear Security
Centralized, hardware-based security doesn't scale in modern data center networks. Distributed firewalling in software overcomes the limitations.BGP in Large Scale Data Centers with Clos Networks
Getting to the point where big is never big enough, one may think “What’s cooking?” Well, BGP in the DC is a subject that’s been under my radar for some time, so the purpose of this article is to get things a bit more straight-forward regarding the WHYs and HOWs.
A look in the past
First of all, we should ask ourselves who was Clos. Charles Clos started his work at Bell Labs, mainly focusing on finding a way to switch telephone calls in a scalable and cost-effective way. In 1953, he published the paper “A Study of Non-Blocking Switching Networks”, where he described how to use equipment having multiple stages of interconnections to switch calls.
The crossbar switches (you may think of them as common use switches with a defined number of ports) connected in a three-stage network (ingress, middle, egress) form the so called Clos network.
This had a pretty big use back in the 1950’s but once the level of circuit integration got to the point where interconnections would no longer be a problem, it was no longer of interest, at least for some time. Until huge scale data centers came to be needed (and Continue reading
8 Things I Learned About SDx in 2015
 It's been a year of learning about new products, new markets... and giraffes.
It's been a year of learning about new products, new markets... and giraffes.
Resolve is easy. Planning & execution are hard.
When we fail, we pity ourselves, have a consolation cookie or three, give up, and go back to a moribund contentment with the status quo. Maybe next year, we'll be more serious, we think. More determined. Yes, we'll try it all again at some future point when we can muster up the will to give it another go. This is all wrong. For me, difficulty in realizing goals has never been due to a lack of desire or will.Mac OS X : Collection of CLI tips
This website is a fantastic resource for Mac OS X Users. Hundreds of A curated list of shell commands and tools specific to OS X. “You don’t have to know everything. You simply need to know where to find it when necessary.” (John Brunner) https://github.com/herrbischoff/awesome-osx-command-line
The post Mac OS X : Collection of CLI tips appeared first on EtherealMind.
What’s Wrong With the Internet?
How many times have you received that call or even made the statement that “The Internet is Down?” Or perhaps the “Internet is Slow?” Obviously these statements are very rarely true. As a whole, the Internet is functional and it is FAST. However these statements seem true from the perspective of the individual making them. My frustration is that we never have visibility into the data necessary to assess the health of the Internet from a relevant, holistic perspective over time. As a result, consumers and providers have a limited view of problems that randomly present in this manner.
The Problem
When I think about the impact Internet hiccups have on me, I realize that I could do things much differently if it delivered consistent reliability. Even if it wasn’t as reliable as infrastructures like the PSTN, having some semblance of trust in knowing when and how my connections might fail or degrade would help. The resulting improvements would allow me to use more robust tools like video and voice over the Internet and put my cell phone away. I can’t tell you how many times I’ve spent hours chasing ghosts. These transient issues tend to get resolved when they worsens and the root cause is more easily identifiable. Increasing the trust we have in our services would materially change the way in which we use them. Continue reading
Routing design
Understanding everything about routing design is no brainer, especially if you have the chart below on your wall. The table below highlights the pros and cons of each routing protocol. Of course, you need to consider the design attributes shown in Figure A before embarking on routing design. Should you like the comparison of the […]
The post Routing design appeared first on Network Design and Architecture.
PQ Show 69: Sonus VellOS And QoE For Unified Communications (Sponsored)
Sonus joins the Packet Pushers to talk about VellOS, a network operating system for ensuring quality of experience for unified communications. With VellOS you can automate flows through a network and control bandwidth, packet marketing, MPLS values, and more to guarantee high-quality voice and video calls.
The post PQ Show 69: Sonus VellOS And QoE For Unified Communications (Sponsored) appeared first on Packet Pushers.