CCIE Data Center Lab, v2 – iPexpert’s Plan
CCIE Data Center Lab, v2 – iPexpert’s Plan
The announcement of the CCIE Data Center Version 2 blueprint has changed the exam that we once knew. No longer are the MDS switches around, plaguing us with the perfectly rational fears of iSCSI gateway configuration, or FCIP configuration nuances. Gone too are the days of fighting the IP protocol stack running on the ever-finicky MDS switches. While some rejoice these facts, I take a step back and try to wrap my head around “what’s next?”
At iPexpert we strive to stay ahead of the proverbial curve within the training market; so immediately after analyzing the impact of the changes (and subsequently drinking quite a bit of beer), we began planning and calculating the changes that we would need in order to adapt to the new version of the exam.
We will most definitely be updating our product portfolio to accommodate the changes. This includes, but is not limited to our:
• CCIE Data Center, Volume 1 – Technology Workbook
• CCIE Data Center, Volume 2 – Full-Scale Mock Lab Workbook
• CCIE Data Center Lab VoD
• CCIE Data Center Written VoD
• CCIE Data Center Lab Bootcamps (Live and Continue reading
Fear itself: Thinking through change and turmoil

Fair warning: this is going to be a controversial post, and it might be considered a bit “off topic.”
Maybe it’s just that time of year. Or maybe it’s several conversations I’ve been involved in recently. Or maybe it’s the result of following over 150 blogs on a daily basis covering everything from religion to politics to technology to philosophy. Whatever it is, there’s one thing I’ve noticed recently.
We’re really afraid.
I don’t mean “concerned about what the future might hold,” but rather — it seems, at least sometimes — sinking into a state of fear bordering on the irrational. Sometimes it feels like the entire world is one long troubleshooting session in the worst designed network I’ve ever encountered. Let me turn to a few completely different areas to illustrate my point. Some of these are going to make people mad, so hold on to your hats — and hear me out before you jump all over me or shut down.
We’re afraid of what the future might hold for us as engineers and as people. Maybe this entire software defined thing is going to destroy my entire career. Maybe I’ll end up like a buggy whip maker Continue reading
MPLS Guide: What Enterprise Architects Need To Know
MPLS is the foundation for many enterprise WAN architectures. This guide covers how MPLS works, its benefits and how it compares to other WAN technologies.MPLS Guide: What Enterprise Architects Need To Know
HPE Cues Up Network Monitoring Software
 The latest version of NNMi provides visibility across physical and virtual infrastructures.
The latest version of NNMi provides visibility across physical and virtual infrastructures.
What’s Ahead For SDN In 2016
Dan Pitt, executive director of the Open Networking Foundation, shares the ONF's predictions for how software-defined networking will evolve next year.#WhoIS is BACK!
WOW it has been a long time. It has taken life and career changes to get me back to the point that I have been able to really think about picking this up again. I have had amazing feedback from the original audience and I am hoping to do even better for you al this …Running Open Daylight in Production Network on Software Gone Wild
Nick Buraglio used OpenDaylight and OpenFlow-enabled switches to build a part of the exhibition network of a large international supercomputing conference and was kind enough to talk about his real-life experience in Episode 47 of Software Gone Wild.
We covered:
Read more ...Stretch’s Hierarchy of Network Needs
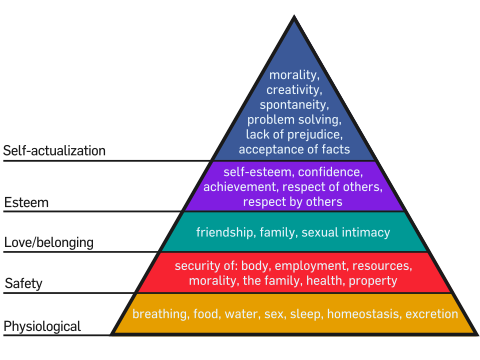
Remember Maslow's hierarchy of needs from school? The theory asserts that every human shares the same set of basic physical and psychological needs in order to be happy, with more primal needs like food and shelter taking precedence over emotional needs like love and companionship.

A while back, I was pondering what would be necessary to fully automate a network, and it occurred to me that a very similar hierarchy of needs can be laid out for a computer network to achieve its optimal state.
1. A Functioning Network
At the very bottom of the hierarchy is everything a network requires to function: Routers, switches, cabling, power, and so on, just as tier one of Maslow's hierarchy encompasses everything a human needs to stay alive. At this stage, a network can function, and can even function well, but it cannot adapt or grow.
Many small businesses operate their networks at this stage for years with no major problems. After all, when left alone, computers and networks tend to just keep chugging along. And if your entire network comprises a cable modem, a switch, and a few access points, it's entirely possible that it will run for years without needing Continue reading
Stretch’s Hierarchy of Network Needs
Remember Maslow's hierarchy of needs from school? The theory asserts that every human shares the same set of basic physical and psychological needs in order to be happy, with more primal needs like food and shelter taking precedence over emotional needs like love and companionship.

A while back, I was pondering what would be necessary to fully automate a network, and it occurred to me that a very similar hierarchy of needs can be laid out for a computer network to achieve its optimal state.
1. A Functioning Network
At the very bottom of the hierarchy is everything a network requires to function: Routers, switches, cabling, power, and so on, just as tier one of Maslow's hierarchy encompasses everything a human needs to stay alive. At this stage, a network can function, and can even function well, but it cannot adapt or grow.
Many small businesses operate their networks at this stage for years with no major problems. After all, when left alone, computers and networks tend to just keep chugging along. And if your entire network comprises a cable modem, a switch, and a few access points, it's entirely possible that it will run for years without needing Continue reading
Stretch’s Hierarchy of Network Needs
Remember Maslow's hierarchy of needs from school? The theory asserts that every human shares the same set of basic physical and psychological needs in order to be happy, with more primal needs like food and shelter taking precedence over emotional needs like love and companionship.
A while back, I was pondering what would be necessary to fully automate a network, and it occurred to me that a very similar hierarchy of needs can be laid out for a computer network to achieve its optimal state.
1. A Functioning Network
At the very bottom of the hierarchy is everything a network requires to function: Routers, switches, cabling, power, and so on, just as tier one of Maslow's hierarchy encompasses everything a human needs to stay alive. At this stage, a network can function, and can even function well, but it cannot adapt or grow.
Many small businesses operate their networks at this stage for years with no major problems. After all, when left alone, computers and networks tend to just keep chugging along. And if your entire network comprises a cable modem, a switch, and a few access points, it's entirely possible that it will run for years without needing Continue reading
Hello world!
Welcome to WordPress. This is your first post. Edit or delete it, then start writing![[ Summary content only, you can read everything now, just visit the site for full story ]]
Cloonix Network Simulator updated to v28
The Cloonix development team recently released a major update to the Cloonix network simulator.
Cloonix version 28 makes major changes to the infrastructure of Cloonix. It changes the installation procedure, the location of Cloonix files on your computer, and the names of the commands used to start and administer Cloonix.

Cloonix version 28 also makes changes to the features available to users. It adds support for multiple Cloonix servers running on the same machine, and standardizes and documents the new interface types used to connect virtual machines to each other.
Read the rest of this post for more details about what’s new in Cloonix v28.
Using Cloonix
In this post, I wrote some examples to show how to use the changed features in Cloonix v28 but I will not discuss the basics of using Cloonix because I assume the reader is already familiar with Cloonix.
If you are not already familiar with Cloonix, you should read the Cloonix documentation. Also, I have written many posts about using the Cloonix network simulator. Please check these posts if you need more information about using Cloonix.
Install Cloonix
The procedure to install Cloonix v28 has changes slightly — one new software dependency has Continue reading
Obsessive Efficiency Disorder
I read this blog post from Mattias Geniar and I think he gave a name of a concept I had in my mind from years. It started a while ago when I tried to find a more efficient ways to do my daily work and it got bigger and bigger up to be almost an… […]Custom events
Measuring Page Load Speed with Navigation Timing describes the standard instrumentation built into web browsers. This article will use navigation timing as an example to demonstrate how custom sFlow events augment standard sFlow instrumentation embedded in network devices, load balancers, hosts and web servers.The JQuery script can be embedded in a web page to provide timing information:
$(window).load(function(){
var samplingRate = 10;
if(samplingRate !== 1 && Math.random() > (1/samplingRate)) return;
setTimeout(function(){
if(window.performance) {
var t = window.performance.timing;
var msg = {
sampling_rate : samplingRate,
t_url : {type:"string",value:window.location.href},
t_useragent : {type:"string",value:navigator.userAgent},
t_loadtime : {type:"int32",value:t.loadEventEnd-t.navigationStart},
t_connecttime : {type:"int32",value:t.responseEnd-t.requestStart}
};
$.ajax({
url:"/navtiming.php",
method:"PUT",
contentType:"application/json",
data:JSON.stringify(msg)
});
}
}, 0);
});The script supports random sampling. In this case a samplingRate of 10 means that, on average, 1-in-10 page hits will generate a measurement record. Measurement records are sent back to the server where the navtiming.php script acts as a gateway, augmenting the measurements and sending them as custom sFlow events.<?php
$rawInput = file_get_contents("php://input");
$rec = json_decode($rawInput);
$rec->datasource = "navtime";
$rec->t_ip = array("type" => "ip", "value" => $_SERVER['REMOTE_ADDR']);
$msg=array("rtflow"=>$rec);
$sock = fsockopen("udp://localhost",36343,$errno,$errstr);
if(! $sock) { Continue reading
SDxCentral Weekly News Roundup — December 11, 2015
 Ericsson wins network management deal with Swisscom; Nokia signs 5-year contract with Wind Mobile.
Ericsson wins network management deal with Swisscom; Nokia signs 5-year contract with Wind Mobile.
