VMware’s Photon Platform Embraces an All-Container World
 But virtualization is a part of it, of course. And vSphere isn't left behind.
But virtualization is a part of it, of course. And vSphere isn't left behind.
Enabling the Software-Defined Data Center Vision
We’re excited to announce our latest tier 1 partnership, this time with VMware, which demonstrates the growing strategic role and importance that Cumulus Linux plays in rapidly building and scaling private and public clouds. VMware has announced VMware EVO SDDC — a software suite that provides a prescriptive and simple way for organizations to build and operate highly scalable and performant private clouds based on VMware’s software-defined data center (SDDC) architecture. With VMware EVO SDDC bundled with OEM hardware, VMware provides compute, storage and network virtualization, and now fully integrated physical networking solutions.
Cumulus Linux comes embedded in VMware EVO SDDC, which also includes a hardware management system (HMS) component with software integration at the network layer. The top of rack (ToR), spine, and management switches all run Cumulus Linux as the network OS on Dell and Quanta platforms. Hyper-converged infrastructure (HCI) solutions based on the suite will be available over time through an exclusive set of VMware partners.
This technology partnership is significant for several reasons. First, to have struck such a strategic OEM partnership with VMware is a ringing endorsement of the enterprise-grade quality of software that Cumulus Linux represents as well as the quality of engineering Continue reading
VMware NSX – It’s About the Platform Ecosystem
The basis of competition has shifted from individual products and technologies to platforms,
but with everyone aspiring to be a platform the bar is set high. A platform must be a value-creation entity, underpinned by a robust architecture that includes a set of well-integrated software artifacts and programming interfaces to enable reuse and extensibility by third parties. Platforms must support an ecosystem that can function in a unified way, foster interactions among its members and orchestrate its network of partners. And finally, platforms must adhere to the network effect theory which asserts that the value of a platform to a user increases as more users subscribe to it, in effect, creating a positive feedback loop.
The VMware NSX network virtualization platform meets this criteria resoundingly. NSX is specifically designed to provide a foundation for a high-value, differentiated ecosystem of partners that includes some of the networking industry’s most significant players. The NSX platform leverages multi-layered network abstractions, an extensible and distributed service framework with multiple entry points, and transparent insertion and orchestration of partner services. What distinguishes NSX from other platforms is its inherent security constructs which partner solutions inherit, and a context sharing and synchronization capability Continue reading
Learn More About SDN Controllers, OpenDaylight, & SDN Solutions with Brocade
 Join SDxCentral and Brocade for the SDN Controller Report webinar on September 29th. Register today!
Join SDxCentral and Brocade for the SDN Controller Report webinar on September 29th. Register today!
PlantUML – Making Complicated Diagrams Simpler
A colleague at work recently told me that I should check out PlantUML. His advice is usually good, and this is no exception.
PlantUML uses a relatively simple text language to describe the desired diagram, then makes generation of the image as simple as processing the UML file. It’s easy to try online at http://plantuml.com/ where there is a text editor with real time image updates as you add more content.
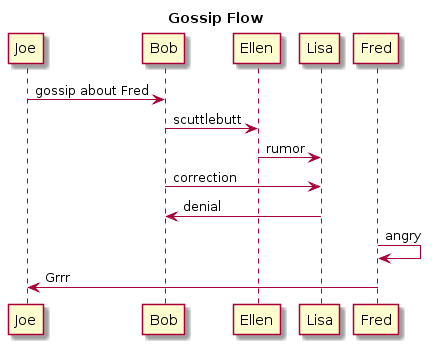
Sequence Diagrams
Sequence diagrams are probably the simplest to build, and are absurdly fast to create. Here’s a simple example of a TCP exchange:
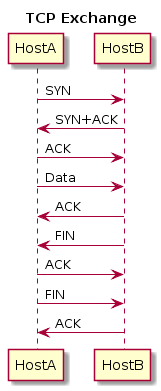 To create this, I used the following PlantUML:
To create this, I used the following PlantUML:
@startuml
title : TCP Exchange
HostA -> HostB : SYN
HostB -> HostA : SYN+ACK
HostA -> HostB : ACK
HostA -> HostB : Data
HostB -> HostA : ACK
HostB -> HostA : FIN
HostA -> HostB : ACK
HostA -> HostB : FIN
HostB -> HostA : ACK
@enduml
You’re not limited to two endpoints, of course:
Use Case Diagrams
Here’s a simple use case with Fred and Joe again:
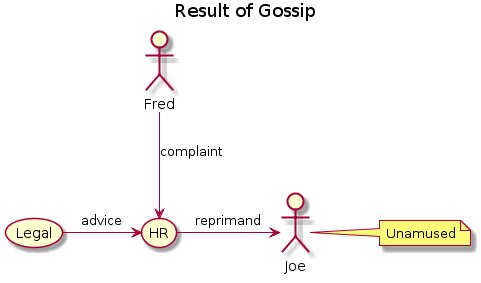 The PlantUML to generate this was:
The PlantUML to generate this was:
@startuml
title : Result of Gossip
Fred --> (HR) : complaint
(Legal) -> (HR) : advice
(HR) -> Continue readingThe Silo of Focus
 How often, in our careers, are we told to focus on one thing at a time? I would guess I see some message about this, such as the image to the left in this post, at least once a week, if not once a day.
How often, in our careers, are we told to focus on one thing at a time? I would guess I see some message about this, such as the image to the left in this post, at least once a week, if not once a day.
In general, I agree with the sentiment. If you really want to get something done, do it, rather than doing a lot of things at once. The reason for this, I think, is because multitasked work tends to result in half-work, which is something to be avoided at all costs.
Avoid half-work more than anything. Do not imitate those people who sit long at their desks but let their minds wander. It is better to shorten the time and use it intensely, to increase its value, which is all that counts. Do something, or do nothing at all. Do ardently whatever you decide to do; do it with your might; and let the whole of your activity be a series of vigorous fresh starts. Half-work, which is half-rest, is good neither for rest nor for work. via Sertillanges, The Intellectual Life
But there is another side to focus we need to be wary of as Continue reading