Xcitium’s Endpoint Virtual Jail Aims To Lock Up Mystery Malware
Xcitium is an Endpoint Detection and Response (EDR) vendor that sells client software that uses multiple methods to protect endpoints. Methods include anti-virus, a host firewall, a Host Intrusion Protection System (HIPS), and a technique it calls ZeroDwell Containment. The first three components are straightforward. The AV software relies on signatures to detect known malware. […]
The post Xcitium’s Endpoint Virtual Jail Aims To Lock Up Mystery Malware appeared first on Packet Pushers.
Kubernetes Security And Networking 3: Helpful Tips For Securing Your Kubernetes Cluster – Video
Michael Levan reviews security essentials for protecting your Kubernetes infrastructure, including worker nodes. He discusses server hardening using CIS Benchmarks as a guide, running a scanner (using Kubescape as an example), and employing role-based access control (RBAC). You can subscribe to the Packet Pushers’ YouTube channel for more videos as they are published. It’s a […]
The post Kubernetes Security And Networking 3: Helpful Tips For Securing Your Kubernetes Cluster – Video appeared first on Packet Pushers.
IPv6 Buzz 121: Uncovering IPv6 Host Default Address Selection
Today's IPv6 Buzz podcast explore the topic of default address selection with IPv6 hosts as defined in RFC 6724. It's very common for a host to have multiple IPv6 addresses of different types (as well as an IPv4 address in dual-stack environments) and RFC 6724 includes rules for which addresses are used first.
The post IPv6 Buzz 121: Uncovering IPv6 Host Default Address Selection appeared first on Packet Pushers.
IPv6 Buzz 121: Uncovering IPv6 Host Default Address Selection
Today's IPv6 Buzz podcast explore the topic of default address selection with IPv6 hosts as defined in RFC 6724. It's very common for a host to have multiple IPv6 addresses of different types (as well as an IPv4 address in dual-stack environments) and RFC 6724 includes rules for which addresses are used first.Considerations for Managing BYOD Policies in 2023
Companies should exercise caution when it comes to BYOD policies due to the potential downsides of tax issues for employees, minimal business savings, and increased security risks.DHCP Relaying Details
Chinar Trivedi asked an interesting question about DHCP relaying in VXLAN/EVPN world on Twitter and my first thought was “that shouldn’t be hard” but when I read the first answer that turned into “wait a minute, how exactly does DHCP relaying works?”
I’m positive there’s a tutorial out there somewhere, but I decided to go back to the sources of wisdom: the RFCs. It turned out to be a long walk down the IETF history lane.
DHCP Relaying Details
Chinar Trivedi asked an interesting question about DHCP relaying in VXLAN/EVPN world on Twitter and my first thought was “that shouldn’t be hard” but when I read the first answer that turned into “wait a minute, how exactly does DHCP relaying works?”
I’m positive there’s a tutorial out there somewhere, but I decided to go back to the sources of wisdom: the RFCs. It turned out to be a long walk down the IETF history lane.
Day Two Cloud 185: Grappling With Cloud Strategies With Tim Banks
Today on Day Two Cloud we engage in strategic thinking about cloud, workload repatriation, costs and spending, DevOps and Kubernetes, and more with guest Tim Banks. Tim is a Lead Developer Advocate at Dell Technologies and has done stints at AWS, Equinix, and the Duckbill Group. Besides being a techie, Tim Banks is also a Brazilian Jiu Jitsu champion and world-ranked competitor in his class.
The post Day Two Cloud 185: Grappling With Cloud Strategies With Tim Banks appeared first on Packet Pushers.
Day Two Cloud 185: Grappling With Cloud Strategies With Tim Banks
Today on Day Two Cloud we engage in strategic thinking about cloud, workload repatriation, costs and spending, DevOps and Kubernetes, and more with guest Tim Banks. Tim is a Lead Developer Advocate at Dell Technologies and has done stints at AWS, Equinix, and the Duckbill Group. Besides being a techie, Tim Banks is also a Brazilian Jiu Jitsu champion and world-ranked competitor in his class.Enabling SD-WAN and SASE – An Ideal Edge Computing Use Case
Standardized SD-WAN and SASE have emerged as crucial use cases for edge computing as they allow the provisioning of computing resources and connectivity needed to improve application performance, minimize latency, and enhance the user experience.HS0042 Is ChatGPT Coming For Your Job
Short answer is yes. Long answer is long. CHatGPT is useful for demonstrating potential and getting more funding for AI. In terms of potential for real work, well, its not good enough.
The post HS0042 Is ChatGPT Coming For Your Job appeared first on Packet Pushers.
HS042 Is ChatGPT Coming For Your Job
Short answer is yes. Long answer is long. CHatGPT is useful for demonstrating potential and getting more funding for AI. In terms of potential for real work, well, its not good enough.Embrace equity on International Women’s Day (and every day)

This post is also available in 简体中文, 日本語, 한국어, Deutsch, Français, Español and 繁體中文.

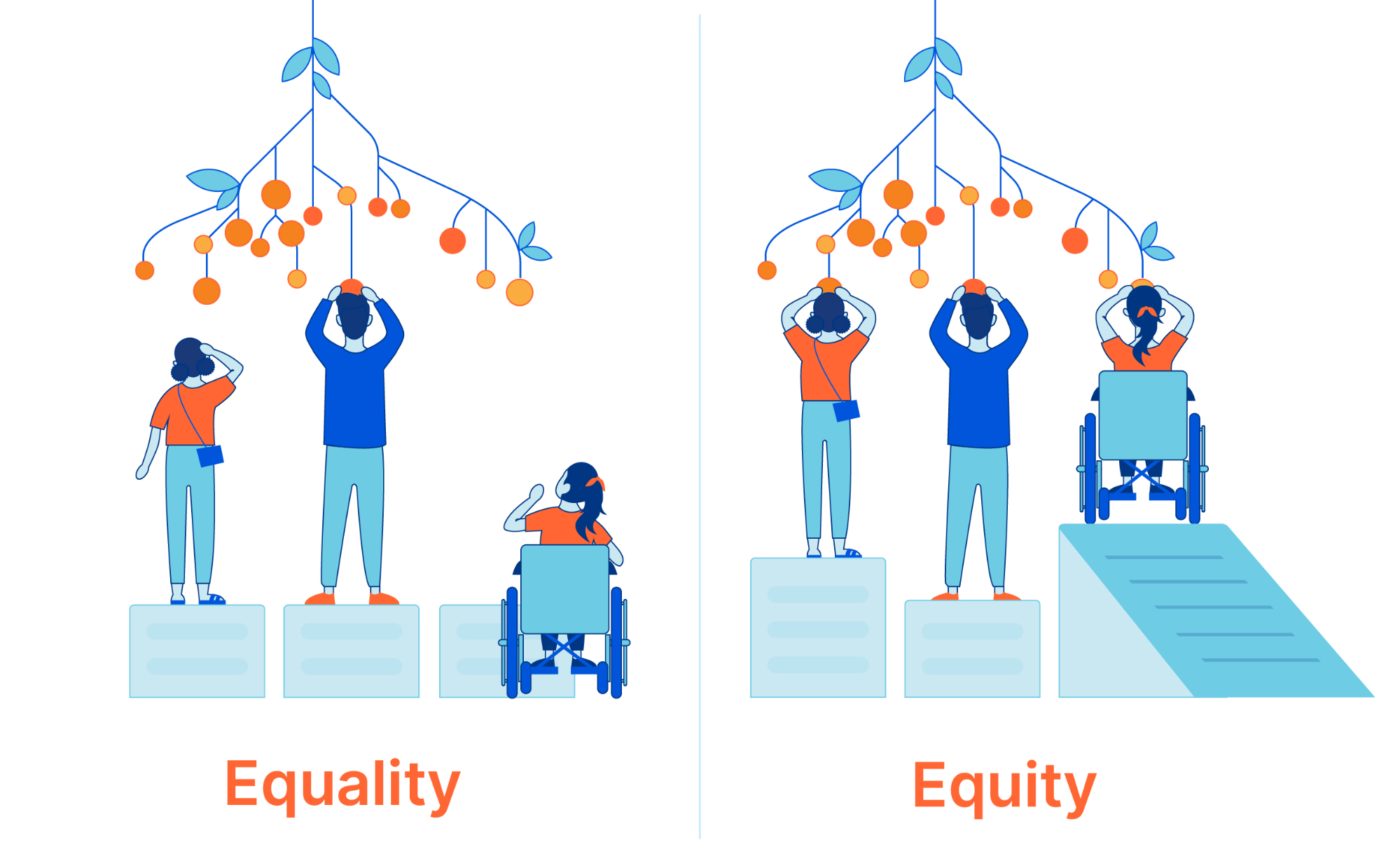
Happy International Women’s Day! The global theme for 2023 is #EmbraceEquity, which is part of an ongoing effort to raise awareness around “Why equal opportunities are no longer enough.” Today is a time to highlight achievements made by women, but also an opportunity to become better informed, and collaborate and brainstorm about the path forward.
“People start from different places, so true inclusion and belonging require equitable action.” — internationalwomensday.com
Help put an end to gender bias and discrimination
Consider taking a few minutes today to learn about pervasive challenges affecting women, including in the workplace. Since unconscious bias is a major driver of hurdles holding women back, it is beneficial for people of all gender identities to educate ourselves about the varied experiences of others.
Here are some resources to get help get you started:
- Recognize the difference between equity and equality and see why striving for equality can interfere with inclusion-related efforts.
- Read highlights from the Women in the Workplace report from McKinsey and LeanIn.Org to examine factors that are holding women back from Continue reading
Accelerate building resiliency into systems with Cloudflare Workers


In this blog post we’ll discuss how Cloudflare Workers enabled us to quickly improve the resiliency of a legacy system. In particular, we’ll discuss how we prevented the email notification systems within Cloudflare from outages caused by external vendors.
Email notification services
At Cloudflare, we send email notifications to customers such as billing invoices, password resets, OTP logins and certificate status updates. We rely on external Email Service Providers (ESPs) to deliver these emails to customers.
The following diagram shows how the system looks. Multiple services in our control plane dispatch emails through an external email vendor. They use HTTP Transmission APIs and also SMTP to send messages to the vendor. If dispatching an email fails, they are retried with exponential back-off mechanisms. Even when our ESP has outages, the retry mechanisms in place guarantee that we don’t lose any messages.

Why did we need to improve resilience?
In some cases, it isn’t sufficient to just deliver the email to the customer; it must be delivered on time. For example, OTP login emails are extremely time sensitive; their validity is short-lived such that a delay in sending them is as bad as not sending them at all. If the ESP Continue reading
New: Anycast Resource Page
I wrote two dozen blog posts describing IP anycast concepts, from first-hop anycast gateways to anycast between DNS servers and global anycast (as used by large web properties), but never organized them in any usable form.
That’s fixed: everything I ever wrote about anycast is nicely structured on the new Anycast Resources page.
New: Anycast Resource Page
I wrote two dozen blog posts describing IP anycast concepts, from first-hop anycast gateways to anycast between DNS servers and global anycast (as used by large web properties), but never organized them in any usable form.
That’s fixed: everything I ever wrote about anycast is nicely structured on the new Anycast Resources page.