Introducing Multi-User Organizations: Share An Account Without Sharing A Login
An enterprise needs security and controls around access.
Your web developer needs to update your website’s logo and make sure it’s live immediately, but doesn’t need access to your SSL keys. Your sysadmin manages your DNS, but doesn’t need to see your visitor traffic. Your marketing team needs to see traffic, but shouldn’t have access to your WAF.
Today CloudFlare is introducing new Multi-User functionality so that many members of a team can work together to manage one CloudFlare account, each with different levels of access.
The Super Admin, and Role-Based Permissions
CloudFlare Multi-User accounts are hierarchical, with the root privileges given to the account’s Super Administrator. The Super Administrator can add or delete users in the organization, change the permissions given to each user, and see and edit all CloudFlare settings. If there is more than one Super Administrator, the Super Administrators can remove each other, which is good practice when an employee leaves the company or switches jobs.
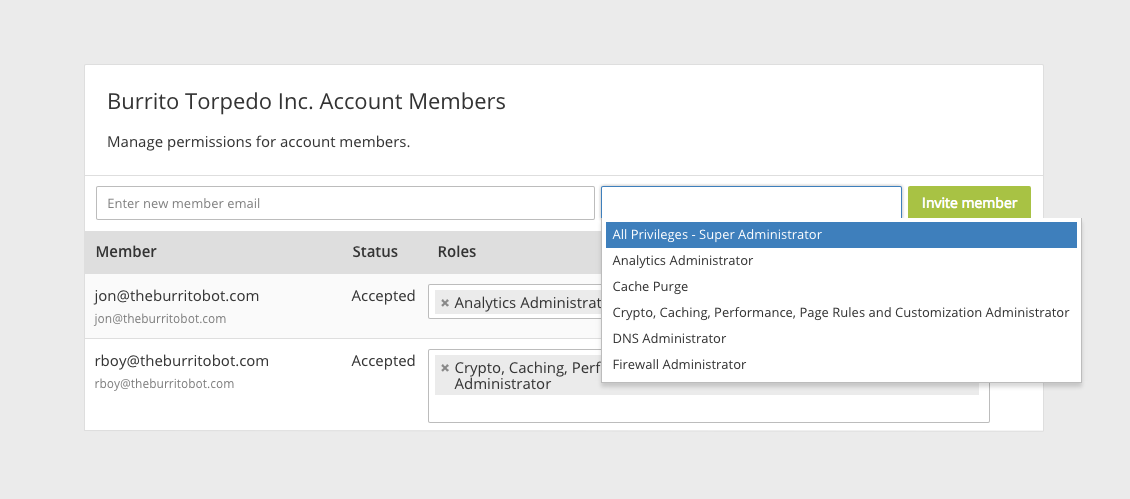
When a user joins a multi-user organization on CloudFlare, they can only see and access the settings that a Super Admin has delegated to them. For example, a user added to the organization as a DNS Administrator would only be Continue reading
Introduction to Storage Networking and Design
Introduction
Storage and storage protocols are not generally well known by network engineers. Networking and srorage have traditionally been two silos, Modern networks and data centers are looking to consolidate these two nettworks into one and to run them on a common transport such as Ethernet,
Hard Disks and Types of Storage
Hard disks can use different type of connectors and protocols.
- Advanced Technology Attachment (ATA)
- Serial ATA (SATA)
- Fibre Channel (FC)
- Small Computer System Interface (SCSI)
- Serial Attached SCSI (SAS)
ATA and SATA and SCSI are older standards, newer disks will typically use SATA or SAS where SATA is more geared towards the enterprise market. FC is used to attach to Storage Area Network (SAN)
Storage can either be file-level storage or block-level storage. File-level storage provides access to a file system through protocols such as Network File System (NFS) or Common Internet File System (CIFS). Block-level storage can be seen as raw storage that does not come with a file system. Block-level storage presents Logical Unit Number (LUN) to servers and the server may then format that raw storage with a file system. VmWare uses VmWare File System (VMFS) to format raw devices.
DAS, NAS and SAN
Storage can Continue reading
An Opportunity for Redemption: Service Providers in the Internet of Things
 IoT strategies and challenges for CSPs
IoT strategies and challenges for CSPs
Going Back to the Mainframes?
25 years ago when I started my networking career, mainframes were all the rage, and we were doing some crazy stuff with small distributed systems that quickly adapted to topology changes, and survived link, port, and node failures. We called them routers.
Yes, we were crazy and weird, but our stuff worked. We won and we built the Internet, proving that we can build networks bigger than any mainframe-based solution could ever hope to be.
Read more ...Cisco ACI Integrates Security from Sourcefire
 ACI strengthens its security story with a next-generation firewall and IPS.
ACI strengthens its security story with a next-generation firewall and IPS.
A fantastic overview of the Elastic Cloud project from Luca Relandini
A fantastic overview of the Elastic Cloud project from Luca Relandini
http://lucarelandini.blogspot.com/2015/03/the-elastic-cloud-project-porting-to.html?
And don’t miss this excellent recent post which explains how to invoke UCS Director workflows via the northbound REST API.
http://lucarelandini.blogspot.com/2015/03/invoking-ucs-director-workflows-via.html