Time To Get More Advanced :: FCIP Pt. 2!
Part 1 of this blog series created a topology, much like you see below, where we configured a single vE (virtual expansion) port from MDS1 to MDS2 across an IP network. We merged VSAN 10 across this FCIP tunnel and verified it by looking into the FCNS database and ensuring that we saw entries from both sides. Today we are going to build upon this topology, and get into some more advanced features like changing the default TCP port, setting DSCP values for the two TCP streams, and controlling who initiates the tunnel!
So first things first…the default port for FCIP is TCP port 3225. We will terminate both of our TCP streams on this port (we have 1 stream for control and another for data traffic). Essentially 1 of the MDS’s will initiate the connection to the other, and their destination port will be TCP/3225. Their source port will be some high-number ephemeral port by default (usually over 65000). We can look at the output of a ‘show int fcip #’ to find out who initiated, and on which ports!
MDS1-6(config-if)# show int fcip1
fcip1 is trunking
Hardware is GigabitEthernet
Port WWN is 20:10:00:0d:ec:1f:a4:00
Peer port WWN is Continue reading
ASA File Operation Tips
Delete from the active, upload to the Continue reading
SCALE13x – My talk: Switch as a Server
This past weekend, I had the opportunity to speak at SCALE13x in Los Angeles, on the Switch as a Server — treating your network switches in the same way you treat your servers. It’s a topic I feel very strongly about!
As strong as my feelings are about open networking, I also love non-automotive forms of transportation! So I decided to bike to the airport. SFO has a lot of bicycle facilities so it was no problem to find parking.


Got to LA on the plane and then Rocket Turtle enjoyed the view by the airport!

… and met some of our great customers!

Scale is a unique conference in that they encourage canine attendance — doggies!

Friday night I helped out with a birds of a feather (BOF) event, giving advice to job hunters. Did I mention we’re hiring?
On Saturday evening I won the Weakest Geek — a Weakest Link-style geek-themed trivia contest, run this Continue reading
SDN, NFV and Skill Development for Network Engineers
Many people say there is no value anymore in taking CCIE these days. With SDN and NFV, everything will be done "auto-magically". We don’t even need network engineers anymore! Yeah, right. Last week I went back in Brussels to work on Network Control System, multi-vendor network device management tool from Tail-F that was acquired by Cisco June last year. NCS is the corner store of Cisco Network Service Orchestration framework for Cisco SDN and NFV solution offering. And I’m here to tell you that the world still need lots of network engineers, and CCIEs, or those who have CCIE-level skill set.
But first, let me talk more about NCS, a service orchestration for real-time service provisioning across multivendor networks.
Network devices were, and are still, configured using CLI. Then SNMP was created to help. Soon, we realized SNMP is great to monitor the network but it fails to become configuration management, as stated Continue reading
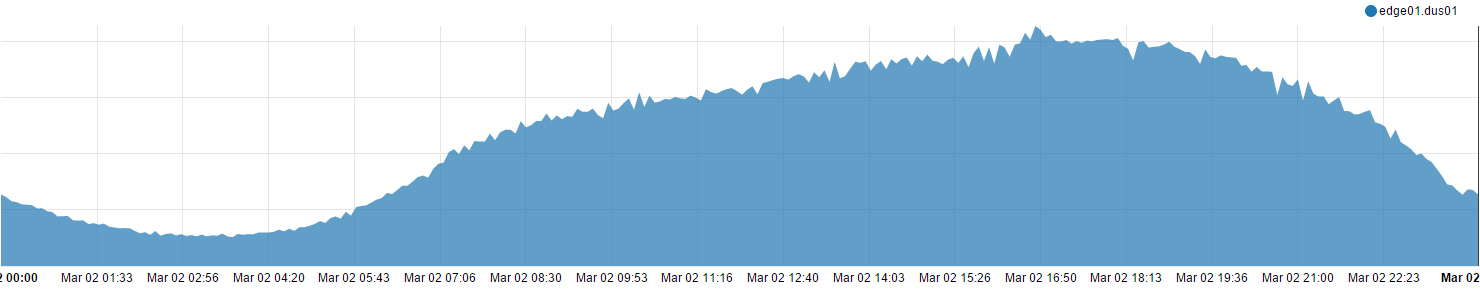
Unser neuer 31er Datacenter: Düsseldorf

Hallo Düsseldorf. Nestled in the center of the Lower Rhine basin lies the bustling city of Düsseldorf, capital of Germany’s most populous state, Northern Rhine-Westphalia. Provided its status as an international business and telecommunications hub, and serving a population larger than the Netherlands, our data center in Düsseldorf is an important addition to our European network. This means not only better performance in Germany and Northern Europe, but additional redundancy for our 10 other data centers throughout Europe, including our first German data center in Frankfurt.
For the local audience: Liebe Freunde in Düsseldorf, euer Internetanschluss ist schneller geworden und ihr könnt jetzt sicher surfen. Viel Spaß.
Not just any data center
Our Düsseldorf data center holds a special place in the heart of our legal counsel Ken Carter. When he’s not helping to build a better Internet, he is likely to be found regaling the office with tales of his adventures in the quaint medieval town of Bad Honnef am Rhein, just south of our new data center. Ban Honnef, most famously known as the world-wide headquarters for Birkenstock, can now add one more tale of note. Equidistant between Frankfurt and Dusseldorf, it is Continue reading
What’s in my toolbag – Update 2 – SergeantClips
Building on the “What’s in my toolbag” series that I revisited last week with the Fluke LinkSprinter, I wanted to talk about the next new item in my tool bag. This week we will take a look at a product called SergeantClip. The SergeantClip is used to help with cable management and switch replacements. I […]
The post What’s in my toolbag – Update 2 – SergeantClips appeared first on Fryguy's Blog.
Response: Open Web Alliance Lobbies to Intercept Your Traffic
The Open Web Alliance is a lobby group that is opposed to secure and safe HTTPS traffic over the Internet and forms lobby group for the HTTP2 process to ensure that your Internet traffic can be intercepted and logged by service providers. This major purpose of this so-called technology innovation is that your personal information to can […]
The post Response: Open Web Alliance Lobbies to Intercept Your Traffic appeared first on EtherealMind.

