Zero Touch Provisioning in a Bare Metal World
Who doesn’t like automation? If you’re speaking to somebody in IT, then the short answer is “nobody”.
While the term Zero Touch Provisioning (ZTP) might be increasingly more common to networking, the concept of automation has existed for years in IT. At its core, ZTP is an automation solution that’s designed to reduce errors and save time when an IT administrator needs to bring new infrastructure online.
This is particularly useful for data center servers, where scale and configuration similarities across systems make automation a necessity. In the server world, the Linux-based operating system has revolutionized on boarding and provisioning. Rather than using command-line interfaces (CLI) to configure these systems one at a time, administrators can use automation tools to roll out the operating system software, patches, and packages on new servers with a single command, or the click of a mouse.
Advanced scripting capabilities also allow administrators to tailor the boot configuration of these systems with profiles for specific applications. So for example, if you need ten servers for a new Hadoop cluster, you can load this with one profile, but if you need six new servers for a new web application, you can Continue reading
phpipam MySQL database optimizations
Having large amount of subnets (and other tables) on unoptimised MySQL database server can significantly increase page loads. To see which parameters need to be change I usually use mysqltuner perl script, which connects to database, analyses data and proposes which parameters need to be changed that are not optimally set based on current load.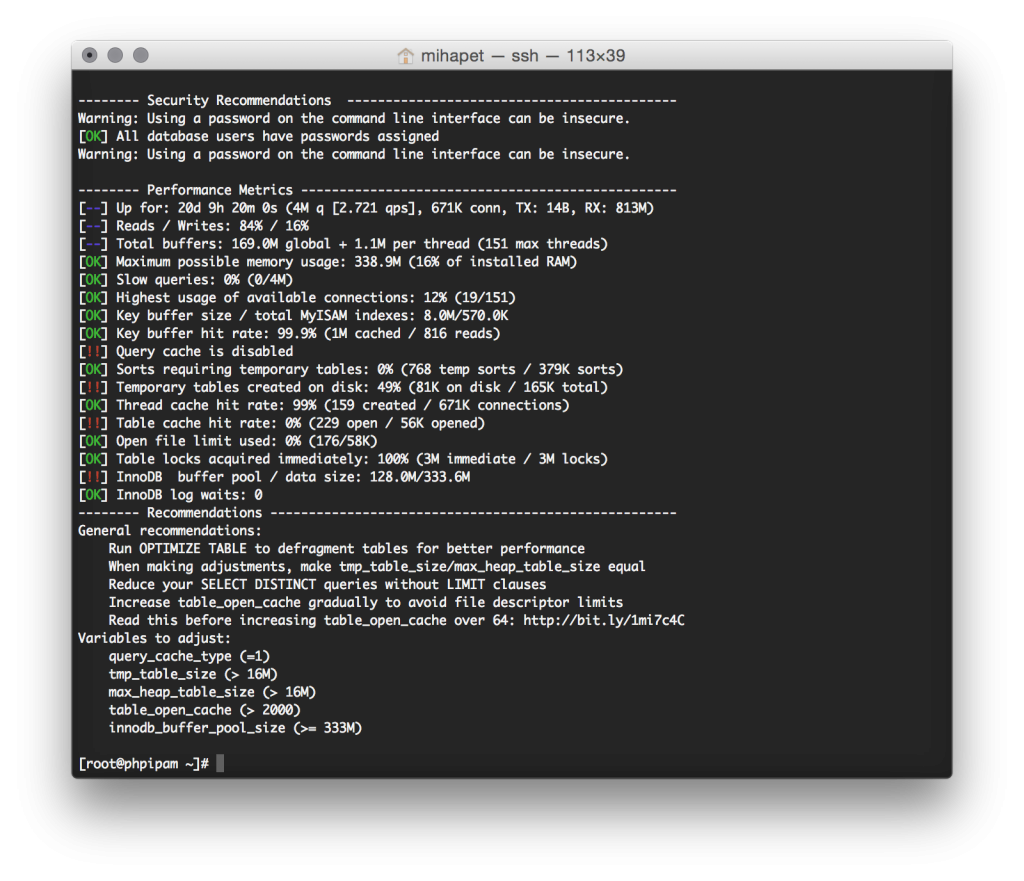
Installation is simple:
1.) Fetch mysqltuner on FreeBSD:
cd ~ fetch http://mysqltuner.pl
or wget on linux:
wget http://mysqltuner.com
2.) Make it executable:
chmod +x mysqltuner.pl
3.) And run it to analyse database, you have to provide administrative credentials.
./mysqltuner.pl
Any other similar scripts out there you would recommend?
brm
How to Explain Highly Technical Ideas to Non-Technical People
by Kevin Dooley, originally published on the Auvik blog I often find myself having to explain highly technical networking or securityLeaky Abstractions
Much of our life, as engineers, is about building, manipulating, and using abstractions. For instance, C is nothing but an abstraction on top of the actual register set provided by a particular processor. HTML is nothing but an abstraction for formatting and display (a markup language), implemented in — well, C. There is a lot of power in such abstractions, of course. Without them we couldn’t build operating systems, applications, browsers, web pages — or networks.
Ethernet is an abstraction of electronic signals (anyone remember Manchester Encoding?). IP is an abstraction of every physical layer in the world. TCP is an simulation, or abstraction, of a reliable connection oriented link over (completely unreliable) IP. HTTP is an abstraction of a flow of information, a stream, between two computers. It’s all abstractions — as the philosopher might say, “it’s abstractions all the way down.” So what’s wrong with this?
All abstractions are leaky. What do I mean when I say abstractions are leaky? Let’s turn to the originator of the phrase, Joel Spolsky:
![]() Abstractions fail. Sometimes a little, sometimes a lot. There’s leakage. Things go wrong. It happens all over the place when you have abstractions.
Abstractions fail. Sometimes a little, sometimes a lot. There’s leakage. Things go wrong. It happens all over the place when you have abstractions.
This is the Continue reading
VMware NSX: a short introduction and HOWTO install it
NSX is the SDN solution by VMware. NSX is available as: NSX for vSphere (NSX-V) NSX Multi-Hypervisor (NSX-MH) NSX-MH is NSX for Multi Hypervisors (ESXi, KVM, Xen, Hyper-V). This post is focused on NSX-V. Acronyms DFW: Distributed FireWall DLR: Distributed Logical Router LIF: Logical InterFace UWA: User World Agent VDS: VSphere Distributed Switch VIB: VSphere Installation Bundle VNID: VXLAN […]Switching is not working on VMware NSX
In this scenario we have three VMs deployed on a NSX vSwitch with VNI 5002. Two are running on the same hosts and they can ping each other, the other one is running on a separated host and cannot ping the other VMs. Check if at least one interface is configured for VXLAN: ~ # […]PQ Show 41 – HP Networking’s Sarwar Raza on the Meaning of Open
This sponsored podcast is a continuation of our series recorded at HP Discover Barcelona 2014. Our thanks to Chris Young for organizing the topics and guests. The interesting conversations in Barcelona at HP Discover 2014 continued with a chat about the shifty meaning of “open.” In the world of technology, being open means a lot of different […]
Author information
The post PQ Show 41 – HP Networking’s Sarwar Raza on the Meaning of Open appeared first on Packet Pushers Podcast and was written by Ethan Banks.
BGPSEC: Leaks and Leaks
This is the final post in my series on BGPSEC — I will probably follow this up, at some point, with a couple of posts on some alternatives to BGPSEC, and the larger issue of the evolution of BGP. Basic Operation Protections Offered Replays, Timers, and Performance Signatures and Performance In this final post, I […]
Author information
The post BGPSEC: Leaks and Leaks appeared first on Packet Pushers Podcast and was written by Russ White.
Network Programmability and SDN
What’s the difference between network programmability and SDN? Matt Oswalt explained his view on the topic in the Network Programmability 101 webinar.
Taming Netlink
Netlink is a Linux Kernel interface that is used to talk Networking between Kernel processes, or from userland to Kernel processes. This post documents how I tamed Netlink and make working with it in Golang easier.
If you want to create an interface, set an MTU, set an IP address etc... on a Linux machine then you have to talk Netlink to do it. For Golang, there are a number of libraries, but this one seems to be gaining a lot of traction recently. Honorable mentions go to Tenus and Docker's libcontainer.
Now, this library is good, but it isn't complete and some of the behavior I need is missing. So how does one go about implementing it you might ask?
Here's my process:
1. Browse the iproute2 source code
The iproute2 utility is insanely useful - it replaces ifconfig and route for those with memories long enough.
In my case, the feature I wanted was here and I could take a look at the exact message structure required :)
2. Debugging Netlink
Once I'd written my tests and code, I wasn't surprised to see that things were not working.
strace will get you part of the way, but it's Continue reading
Taming Netlink
Netlink is a Linux Kernel interface that is used to talk Networking between Kernel processes, or from userland to Kernel processes. This post documents how I tamed Netlink and make working with it in Golang easier.
If you want to create an interface, set an MTU, set an IP address …
Taming Netlink
Netlink is a Linux Kernel interface that is used to talk Networking between Kernel processes, or from userland to Kernel processes. This post documents how I tamed Netlink and make working with it in Golang easier.
phpipam MySQL database optimizations
MySQLtuner instructions to optimize MySQL database for phpipam.Unique RD per PE in MPLS VPN for Load Sharing and Faster Convergence
This post describes how load sharing and faster convergence in MPLS VPNs is possible by using an unique RD per VRF per PE. It assumes you are already familiar with MPLS but here is a quick recap.
The Route Distinguisher (RD) is used in MPLS VPNs to create unique routes. With IPv4, an IP address is 32 bits long but several customers may and probably will use the same networks. If CustomerA uses 10.0.0.0/24 and CustomerX also uses 10.0.0.0/24, we must in some way make this route unique to transport it over MPBGP. The RD does exactly this by prepending a 64 bit value and together with the IPv4 address, creating a 96-bit VPNv4 prefix. This is all the RD does, it has nothing to do with the VPN in itself. It is common to create RD consisting of AS_number:VPN_identifier so that a VPN has the same RD on all PEs where it exists.
The Route Target (RT) is what defines the VPN, which routes are imported to the VPN and the topology of the VPN. These are extended communities that are tagged on to the BGP Update and transported over MPBGP.
MPLS uses Continue reading
Setting Up Untangle NGFW in a GNS3 Environment.
Building on the premise set up in Lab Blueprint for CEH Aspirants or something gutsy to do on GNS3 !!. Let me introduce you to ( if you areHeadwinds, or Uphill?
As some of my readers know, I’ve done a fair bit of bike touring. Two of the challenges of bike touring are riding uphill, and riding into headwinds.
Riding uphill is tough. 2,300m passes in snow, or 3,200m passes in sunshine, it’s tough going. But you put your head down, and keep turning the pedals, because you know that eventually you will reach the top, and there will be a downhill reward.
Riding into headwinds is a different story. You can battle into headwinds for days, and never get any reward. It saps your energy, and you don’t know if or when it will ever end. The wind could just keep coming from that direction. I’ve gone to different countries just to avoid the wind in the past.
They’re both hard. But one of them has an end, and a reward. The other one can just keep on sucking away your will to live.
Applying it to Life
This applies to the rest of your life. The tricky bit is that sometimes you don’t know if you’re going uphill, or into the wind. Both of them feel hard, and you can’t always see the end in sight.
ASA Discussion
Hello Everyone, There seems to be four major issues among the community. One of them is the ASA. I put together a brief discussionRaspberry Pi RSPAN Capture Box
For some time I have had issues while doing captures such as finding the elusive “spare laptop” you can use, multiple trips out to the site to pick up the captures, or finding another NIC to put in there so you can connect remotely and copy the captures over the network, taking up 2 switch […]
Author information
The post Raspberry Pi RSPAN Capture Box appeared first on Packet Pushers Podcast and was written by Daniel Himes.
I became CCIE# 46173
How does Internet work - We know what is networking
This is the story on how I became CCIE# 46173 To be honest, when I look back, I do not really know the main reason behind going through all this trouble, but I can tell you the story about how I did it. It’s mostly a thriller, and some drama towards the end. I will give you an overview of the whole process including the materials used, videos watched, books read and struggles that I went through. I think that is the right thing to do. This article is for all of you out there who are still trying to study for this exam and need some suggestions.
Pick a Topic for NSX Deep Dive Software Gone Wild Episode
Dmitri Kalintsev, one of the networking guys from VMware NSX team, has kindly agreed to do an NSX technical deep dive Software Gone Wild episode… and you have the opportunity to tell him what you’d like to hear. It’s as easy as writing a comment, and we’ll pick one of the most popular topics.
Do keep in mind that we plan to do a technical deep dive, and it has to fit within an hour or so or nobody will ever listen to it, so please keep your suggestions focused. “Troubleshooting NSX”, “NSX Design”, or “NSX versus ACI ” is not what we’re looking for ;)