How to define SDN?
Someone recently asked me what SDN is? Even though I have written multiple blogs related to SDN, I was not able to give a crisp answer which I was satisfied with. Since its fashionable to associate any new development in Networking to SDN, the definition becomes complex. In this blog, I will mention the different … Continue reading How to define SDN?How to set up Cisco vIOS in GNS3 v1.x and get it working ?
Before we begin. There are many blogs out there that show you the method to do this. A great one is by Radovan Brezula atComware link-aggregation: LACP edge-port
Comware has 2 types of link-aggregation: static link-aggregation: no control protocol is used, based on the configuration, the link-aggregation member interfaces will be actively participating (Selected) in the link-aggregation at the moment the interfaces come up. dynamic link-aggregation: LACP control … Continue readingHow to build Mininet documentation
After installing the Mininet software-defined network simulator on a virtual machine, you may want to build the documentation. Documentation is available on the Mininet web site but, if you installed a beta version of a new development release or installed an old version, you may want to use the documentation specific for the version you are using.
Mininet documentation is built into the source code and can be generated using the doxypy program. This post details the simple steps required to install doxypy and other required software, and to build and view the documentation.
Install doxypy
Start the Mininet virtual machine and log into it via SSH. See my previous post about setting up the Mininet SDN Network Simulator virtual machine.
On the Mininet VM, run the following command to install doxypy, and supporting software packages:
$ sudo apt-get install doxypy doxygen doxygen-latex help2man
This could take a while because it downloads over one Gigabyte of data, such as fonts.
Build the documentation
On the Mininet VM, run the following command to build the documentation
$ cd ~/mininet
$ make doc
This builds a PDF version of the documentation named refman.pdf in the folder: ~/mininet/doc/latex/.
Install a PDF Continue reading
Sorting Bookmarks in Safari for Mac OS X
If you’re anything like me, then you may just be a bit OCD or ANAL when it comes to some things. One of those things is, I like my bookmarks/favorites in alphabetical order with folders sorted...[[ Summary content only, you can read everything now, just visit the site for full story ]]
Sorting Bookmarks in Safari for Mac OS X
If you’re anything like me, then you may just be a bit OCD or ANAL when it comes to some things. One of those things is, I like my bookmarks/favorites in alphabetical order with folders sorted...[[ Summary content only, you can read everything now, just visit the site for full story ]]
Sorting Bookmarks in Safari for Mac OS X
If you’re anything like me, then you may just be a bit OCD or ANAL when it comes to some things. One of those things is, I like my bookmarks/favorites in alphabetical order with folders sorted...[[ Summary content only, you can read everything now, just visit the site for full story ]]
Sorting Bookmarks in Safari for Mac OS X
If you’re anything like me, then you may just be a bit OCD or ANAL when it comes to some things. One of those things is, I like my bookmarks/favorites in alphabetical order with folders sorted first....[[ Summary content only, you can read everything now, just visit the site for full story ]]
CoreOS – Using fleet to deploy an application
At this point we’ve deployed three hosts in our first and second CoreOS posts. Now we can do some of the really cool stuff fleet is capable of doing on CoreOS! Again – I’ll apologize that we’re getting ahead of ourselves here but I really want to give you a demo of what CoreOS can do with fleet before we spend a few posts diving into the details of how it does this. So let’s dive right back in where we left off…
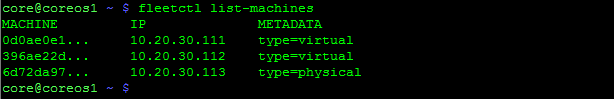
We should have 3 CoreOS hosts that are clustered. Let’s verify that by SSHing into one of CoreOS hosts…
Looks good, the cluster can see all three of our hosts. Let’s start work on deploying our first service using fleet.
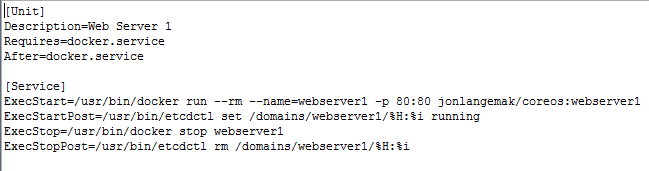
Fleet works off of unit files. This is a systemd construct and one that we’ll cover in greater detail in the upcoming systemd post. For now, let’s look at what a fleet unit file might look like…
Note: These config files are out on my github account – https://github.com/jonlangemak/coreos/
Systemd works off of units and targets. Suffice to say for now, the fleet service file describes a service Continue reading
iPexpert’s Newest “CCIE Wall of Fame” Additions 12/12/2014
Please Join us in congratulating the following iPexpert clients who have passed their CCIE lab!
- Chris Hayden, CCIE #45781 (Collaboration)
- Ahmed Samir , CCIE #45697 (Wireless)
We Want to Hear From You!
Have you passed your CCIE lab exam using any iPexpert or Proctor Labs self-study products, or attended our CCIE Bootcamp? If so, we’d like to add you to our CCIE Wall of Fame!
The End of Fixed Voice
IP Telephony is an end stage market. Here is why.
The post The End of Fixed Voice appeared first on EtherealMind.
The Definitive QEmu Guide for GNS3
Ahoy Matey! We'd be sailing through uncharted waters here! *Makes pirate voice*. Seriously, I have searched and searchedOn Policy in the Data Center: Congress
By Tim Hinrichs and Scott Lowe with contributions from Alex Yip, Dmitri Kalintsev, and Peter Balland
(Note: this post is also cross-published at RuleYourCloud.com, a new site focused on policy.)
In the first few parts of this series, we discussed the policy problem, we outlined dimensions of the solution space, and we gave a brief overview of the existing OpenStack policy efforts. In this post we do a deep dive into one of the (not yet incubated) OpenStack policy efforts: Congress.
Overview
Remember that to solve the policy problem, people take ideas in their head about how the data center ought to behave (“policy”) and codify them in a language the computer system can understand. That is, the policy problem is really a programming languages problem. Not surprisingly Congress is, at its core, a policy language plus an implementation of that language.
Congress is a standard cloud service; you install it on a server, give it some inputs, and interact with it via a RESTful API. Congress has two kinds of inputs:
- The other cloud services you’d like it to manage (for example, a compute manager like OpenStack Nova and a network manager like OpenStack Continue reading
PlexxiPulse—Reflections in Networking
2014 was a busy year in networking, and our friend Marcia Savage did a great job of summarizing the industry highs and lows – from ACI to white box switches – this week in a slideshow for Network Computing. It’s definitely worth a read before you head out for the weekend. Check out Marcia’s year end wrap up below as well as other happenings in the networking space this week.
In this week’s PlexxiTube video of the week, Dan Bachman explains how Plexxi incorporates optical transport into datacenter transport fabrics.
Computer Weekly: Cisco is missing the transition to software-defined networks
By Alex Scroxton
Little doubt remains that the future of networking will be defined by software, but market-watchers warn Cisco is missing this move. Cisco’s hardware forms the backbone of most enterprise networks around the world. But this world is changing and many buyers no longer see compute, storage and networking as distinct silos… Software-defined networking (SDN) company Plexxi, which recently appointed former EMC executive Richard Napolitano as its CEO, is one such company looking at the networking industry’s transition from networking towards an application and data-focused world. “We stand today at a transition point in the IT landscape,” says Continue reading
Friday News Analysis: Cisco Sues Arista For Patent + Copyright Infringement
Cisco is suing Arista in a pair of actions that will be interesting to follow as they wind their way through the courts. See post entitled “Protecting Innovation” here. In the thirteen years I’ve been General Counsel of Cisco, I can count on one hand the number of times we’ve initiated suit against a competitor, […]Basic Python Multithreading
The first ‘proper’ Python app I made logged onto a list of devices and pulled out OSPF state. This worked perfectly fine. The app correctly works out whether it can log into a device or not, and waits a few seconds to ensure a device actually responds. The issue is that if I have a […]Internets of Interest – 12 December 2014
Collection of useful, relevant or just fun places on the Internets for 12 December 2014 and a bit commentary about what I've found interesting about them:
The post Internets of Interest – 12 December 2014 appeared first on EtherealMind.
L2VPN over IPv6 with Snabb Switch on Software Gone Wild
Highly customizable high-speed virtual switch written in Lua sounds great, but is it really that easy to use? Simon Leinen was kind enough to get me in touch with Alex Gall, his colleague at Switch, who's working on an interesting project: implementing L2VPN over IPv6 with Snabb Switch.
Read more ...Big Switch Chaos Monkey Network Testing
Whenever you build a complex system, you need to test that it works as expected, including properly handling failures. It’s easy enough to do simple component failure testing, but harder to do rapid automated failure tests. Big Switch is showing that it can be done though. Hopefully we can keep improving our testing to pick up some more of the software failures.
Testing is hard
Over the course of my career I’ve built many clustered systems – HP-UX Serviceguard, firewalls, routers, load balancers, RedHat Clusters, etc. Good clusters have redundant everything – servers, power supplies, disks, NICs, etc.
The commissioning process always included testing. We’d go through each of the components, trying to simulate failures. Unplug each of the power cables, the network cables, unseat a hard drive, remove a hot-swappable fan, etc. That would test out the redundant components within each server, and then of course you’d simulate a complete system failure, forcing full failover.
This is all important stuff, but it doesn’t pick up all the failures – e.g. What happens if you’ve got a faulty patch lead, and the link starts flapping? Sometimes a simple failure gets messy when it happens repeatedly over a short Continue reading
phpipam 1.1.010 update released
phpipam 1.1.010 update released with following fixes:
== 1.1.010 Bugfixes: ---------------------------- + Fixed login fails with LDAP when escape characters are in password; + Fixed login not working with spaces in password for AD login; + Fixed Ivalid action when adding vlans from subnet popup menu; + Fixed custom fields not appearing properly on IP request editing; + Fixed Invalid ID error for IP address details on sorting; + Fixed warnings if no VLAN search results are present; + Fixed test mail not sending; + Fixed unable to login if $phpsessname not defined; + Fixed unable to login after upgrade;
I apologise for any inconvenience some users experienced with upgrade.
brm