phpipam v1.1 released :: security fixes, performance improvements, mod_rewrite optional
Dear all, I am happy to announce new version of phpipam IP address management – version 1.1.
This release fixed some bugs, provided some new features, but most importantly it was focused on:
- Security fixes (SQL injection, XSS scripting, crypting DB passwords, brute-force attack prevention, …)
- Performace improvements (Caching, reusing SQL connection),..
- mod_rewrite no longer required, selectable URL structure under settings
Some screens:
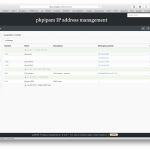
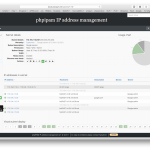
If you find phpIPAM useful for your company donations would be highly appreciated ![]()
You can demo it here: http://demo.phpipam.net/
You can download it on sourceforge site: phpipam-1.1.
Special thanks to all the people submitting bug reports, translators and feature testers!
Full changelog for this release is:
Enhancements: ---------------------------- + Caching of SQL results to avoid multiple queries; + Reduced number of DB queries; + Added selected mail notifications to admins to be notified on IP/subnet change; + Added new subnetId index to ipaddresses table that significantly improves network loading; + Now using only 1 network connection towards MySQL server; + Updated pagination; + mod_rewrite no longer required, selectable URL structure under settings; + Added option not to display free ranges; + Added option to set maximum VLAN number; + Selectable custom fields to Continue reading
Load Balancing in Google Network
Todd Hoff (of the HighScalability fame) sent me a link to an interesting video describing load-balancing mechanisms used at Google and how they evolved over time.
If the rest of the blog post feels like Latin, you SHOULD watch the Load Balancing and Scale-Out Application Architecture webinar.
The beginning of the story resembles traditional enterprise solutions:
Read more ...Powerpoint Doesn’t Stink
“Presentations are just a waste of time.”
“Powerpoint stinks.”
“Can’t we do something other than another long, boring, presentation?”
“We should just ban Powerpoint.”
If I had a nickel for every time I’ve heard someone complain about Powerpoint, or presentations, I’d be rich enough to quit work and stop blogging. ![]() Isn’t it about time we were honest with ourselves, though? Isn’t it about time we told the truth about this particular problem? Blaming Powerpoint for bad presentations is like blaming word processors for badly written books.
Isn’t it about time we were honest with ourselves, though? Isn’t it about time we told the truth about this particular problem? Blaming Powerpoint for bad presentations is like blaming word processors for badly written books.
The problem isn’t Powerpoint. The problem is the person you see every morning looking at you in the mirror. The problem isn’t the tool, it’s that we stink at organizing and presenting our thoughts in any sort of reasonable way. So let’s talk about how to build a better presentation.
To begin: forget everything you’ve ever read in a book about making elevator pitches, making a presentation that impacts, with dash, flair, or whatever. There is a set of presentations that present as a story, with flair and dash, and there is another set that just doesn’t.
As an example, I was the Routing Protocols SGM for Cisco Live for Continue reading
Christmas Change Freeze – Good or Bad?
We’re approaching Christmas, and for many of us, that means we’re about to enter an extended change freeze. This means an extended period when we shouldn’t change anything, hoping to improve stability. ITIL Change Management tells us this is good. I’m not convinced.
The Christmas Change Freeze
Many businesses impose some form of change freeze across all production systems during the Christmas/New Years period. In theory, all network/compute/storage changes are deferred until January. In practice, high priority changes will still be made if you jump up and down enough. The rate of change should still be lower during this period though.
Some change freezes may only run from just before Christmas until early January. Other businesses will go into a change freeze for as long as five weeks. My experience is that Southern Hemisphere businesses have a longer change freeze than Northern Hemisphere ones. I assume this is because many staff take extended leave over the Austral summer.
Why Have One?
There are differing opinions about the usefulness Continue reading
Cisco VIRL ESXi Installation Notes
Note: I was part of the early VIRL beta program. For my efforts in that beta, I was provided a free one year subscription to VIRL, worth $199. I’ve got Cisco VIRL up and running on ESXi 5.5. The installation was mostly smooth, but there were some hurdles to overcome. Here are my installation notes […]3 Months With Little Streaming Boxes
You might recall that I dropped Dish Network a few months back, using a Roku 3 and Apple TV instead. How’s it been going? Just fine, really. No regrets. Here’s what I’ve learned. 1. We use the Roku 3 for almost everything. The Roku has a clean, intuitive, simple, responsive interface. Plus, the Roku […]Scaling Distributed Systems Is Hard
Stumbled upon a hilarious description of challenges encountered when trying to scale distributed systems (cluster of controllers running centralized control plane comes to mind).
It starts with “If someone tells you that scaling out a distributed system is easy they are either lying or drunk, and possibly both,” and gets better and better. Enjoy!
Monitoring leaf and spine fabric performance
A leaf and spine fabric is challenging to monitor. The fabric spreads traffic across all the switches and links in order to maximize bandwidth. Unlike traditional hierarchical network designs, where a small number of links can be monitored to provide visibility, a leaf and spine network has no special links or switches where running CLI commands or attaching a probe would provide visibility. Even if it were possible to attach probes, the effective bandwidth of a leaf and spine network can be as high as a Petabit/second, well beyond the capabilities of current generation monitoring tools.
The 2 minute video provides an overview of some of the performance challenges with leaf and spine fabrics and demonstrates Fabric View - a monitoring solution that leverages industry standard sFlow instrumentation in commodity data center switches to provide real-time visibility into fabric performance. Fabric View is an application running on InMon's Switch Fabric Accelerator SDN controller. Other applications can automatically respond to problems and apply controls to protect against DDoS attacks, reduce latency and increase throughput.
Visit sFlow.com to learn more, evaluate pre-release versions of these products, or discuss requirements.
Alteon’s REST API
AlteonOS has a reach REST API for monitor, operation, and configuration.REST can be used/called with verity of programming languages, or even just using wget. However, since this blog was already using TCL for AppShape++ scripting, we may as well keep using TCL for REST too. However, RESTing with TCL is a bit pain in the ..., so this time I'll use python instead.
All most forgot to explain what REST is. Its a way to run remote procedures calls using HTTP. Example calls:
- Read interface counters
- Update real's weight
- Bring down a real inside a group
Here are two screenshots. The first is how I get the current status of real 1, and the second is how I disable real 1.
Lab goal
Using the base setup, create python script to toggle the status of real 1 from not enabled to enabled and from disable to enable.
Setup
Friday News Analysis: Lightweight Junos for Cloud Builders on an Open Switch
Finally! An Open Switch With a Reliable Operating System (Juniper) Today, Juniper Networks announced a fundamental transformation in the networking industry. Until now, disaggregated networking software and hardware has been in the domain of only those customers who had a large amount of resources to take “unproven software,” combined with original design manufacturer […]Friday News Analysis: Rumors Around Juniper’s Security Products
Juniper whips out knife, slices off security products Note that this is not official Juniper news from what I can tell. The report comes from the tech equivalent of a gossip rag. Maybe I shouldn’t bring it up. But…it seems all too plausible. Here are several bits from the article I stitched into […]Friday News Analysis: Cisco on Network Services Headers
Network Services Headers (NSH): Creating a Service Plane for Cloud Networks (Cisco) Cisco has developed Network Services Headers (NSH), a new service chaining protocol that is rapidly gaining acceptance in the industry. Based on lessons learned in earlier versions of vPath, and realizing that NSH would only succeed with broad acceptance from a […]PlexxiPulse—Facebook’s New Network
The internet has been buzzing about Facebook’s redesigned datacenter architecture. Facebook, which is used by more than 1.35 billion people, recently restructured their infrastructure to increase flexibility and agility to rapidly adjust to application requirements. Our own Marten Terpstra shared his take on the redesigned infrastructure this week on the Plexxi blog—it’s definitely worth a read. Below we share some of the articles that covered Facebook’s new datacenter architecture, as well as other happenings in the networking space this week.
In this week’s PlexxiTube of the week, Dan Backman explains how much fiber is required to connect datacenters using Plexxi’s datacenter transport fabric solution.
Gigaom: Facebook Redesigned the Data Center Network: 3 Reasons It Matters
By Derrick Harris
Earlier this month, Facebook announced a new data center networking architecture that it calls, fittingly, “data center fabric.” The company explained the design and the rationale in an engineering blog post, and Gigaom’s Jonathan Vanian covered the news, but it’s a big enough deal that we had Facebook Director of Network Engineering Najam Ahmad on the Structure Show podcast this week to talk about the new fabric in more detail.
CIO: How (and Why) Facebook Excels at Data Center Continue reading
Friday News Analysis: D-Link for Business Adds New Wireless Controller
D-Link Expands its Unified Wireless Portfolio with New Wireless Controller Supporting up to 256 Access Points D-Link today announced the Unified Wireless Controller (DWC-2000), a new centralized Wireless LAN manager designed specifically for education, hospitality and medium-to-large enterprises. The DWC-2000 can support up to 256 access points per controller, and up to 1,024 […]Imposing Artificial Limitations to Develop Skills
I'm a big fan of imposing artificial limitations on yourself in order to aid skill development. Here are some quick ideas:- When troubleshooting network devices from the CLI, try not to look at the configuration. Use only "show" or "debug" commands instead. I found this enormously beneficial when practicing for CCIE.
- When troubleshooting larger operational issues or learning a new environment, try not to log into individual devices at all. Force yourself to use only your network management system, NetFlow, packet captures, or host-based tools like ping, traceroute, or nmap.
- When learning automation or orchestration skills, force yourself to write scripts, run API calls, or use your favorite orchestration tool to do simple things, even if it doesn't seem like they merit the extra effort.
Imposing Artificial Limitations to Develop Skills
I'm a big fan of imposing artificial limitations on yourself in order to aid skill development. Here are some quick ideas:- When troubleshooting network devices from the CLI, try not to look at the configuration. Use only "show" or "debug" commands instead. I found this enormously beneficial when practicing for CCIE.
- When troubleshooting larger operational issues or learning a new environment, try not to log into individual devices at all. Force yourself to use only your network management system, NetFlow, packet captures, or host-based tools like ping, traceroute, or nmap.
- When learning automation or orchestration skills, force yourself to write scripts, run API calls, or use your favorite orchestration tool to do simple things, even if it doesn't seem like they merit the extra effort.
iPexpert’s Newest “CCIE Wall of Fame” Additions 12/05/2014
Please Join us in congratulating the following iPexpert clients who have passed their CCIE lab!
- Mathew Varghese, CCIE #45557 (Collaboration)
- Nick Thompson , CCIE #45731 (Collaboration)
We Want to Hear From You!
Have you passed your CCIE lab exam and used any of iPexpert’s or Proctor Labs self-study products, or attended a CCIE Bootcamp? If so, we’d like to add you to our CCIE Wall of Fame!
Hotel California Effects of Public Clouds
In his The Case for Hybrids blog post Mat Mathews described the Hotel California effect of public clouds as: “One of the most oft mentioned issues with public cloud is the difficulty in getting out.” Once you start relying on cloud provider APIs to provide DNS, load balancing, CDN, content hosting, security groups, and a plethora of other services, it’s impossible to get out.
Interestingly, the side effects of public cloud deployments extend into the realm of application programming, as I was surprised to find out during one of my Expert Express engagements.
Read more ...