Boosting CX Through Intelligent Asset Management
Implementing a robust maintenance and support strategy can guard against unplanned outages that create major problems for asset owners and operators.Proxmox VM Bridge Port Mirror
https://codingpackets.com/blog/proxmox-vm-bridge-port-mirror
IAM is the Perimeter

A colleague of mine recently quiped, "'The perimeter' in AWS is actually defined by Identity and Access Management (IAM)." After some reflection, I think my colleague is spot on.
Ask JJX: Can ChatGPT Teach Me Wireless Security?
Happy new year, and welcome to the first edition of “Ask JJX.” I had a few questions to pick from (and I’ll try to work through as many as I can) but this inquiry quite literally made me laugh out loud. “Your book is really long. Can I just use ChatGPT to learn about wireless […]
The post Ask JJX: Can ChatGPT Teach Me Wireless Security? appeared first on Packet Pushers.
Tigera 2023 predictions: Cloud native security and the shifting landscape in 2023
Cloud computing and the use of cloud native architectures enable unparalleled performance, flexibility, and velocity. The speed of innovation has driven significant advancements across industries, but as digitalization continues pushing applications and services to the cloud, bad actors’ intrusion techniques have also become more sophisticated. The burgeoning threat landscape is top of mind for enterprise and midmarket business and security leaders, and should lead their decision-making—from the right solutions to implement, to the right partners to engage.
Economic conditions tightening and macroeconomic forces will continue introducing challenges in the coming year, but businesses that sustainably provide value to their customers and make security a foundational aspect of their organization will thrive.
Here are some trends I anticipate for 2023:
Cloud-native inflection point
While the last few years were dominated by early adopters who thrive in the technical playgrounds of emerging technologies, 2023 will see the ‘early majority’ of mainstream users begin adopting cloud-native architectures as the market reaches an inflection point. This inflection is driven by the accelerating accessibility and usability of the tools and technologies available, as the early majority prioritizes platforms that work easily over those with advanced functions that they likely won’t use.
“Shift left” has become Continue reading
Day Two Cloud 177: IT Security Is Broken; Here’s Ideas On How To Fix It
IT security is broken. Vendors ship insecure products, customers have to bolt on and then operate more and more security products, compliance and regulatory requirements don't necessarily make things safer, and getting business done always takes priority over securing systems and data. On today's Day Two Cloud podcast, guest Mick Douglas shares ideas on how to make security less excruciating and more effective.
The post Day Two Cloud 177: IT Security Is Broken; Here’s Ideas On How To Fix It appeared first on Packet Pushers.
Day Two Cloud 177: IT Security Is Broken; Here’s Ideas On How To Fix It
IT security is broken. Vendors ship insecure products, customers have to bolt on and then operate more and more security products, compliance and regulatory requirements don't necessarily make things safer, and getting business done always takes priority over securing systems and data. On today's Day Two Cloud podcast, guest Mick Douglas shares ideas on how to make security less excruciating and more effective.Four Key Requirements for Multi-Cloud Networking Success
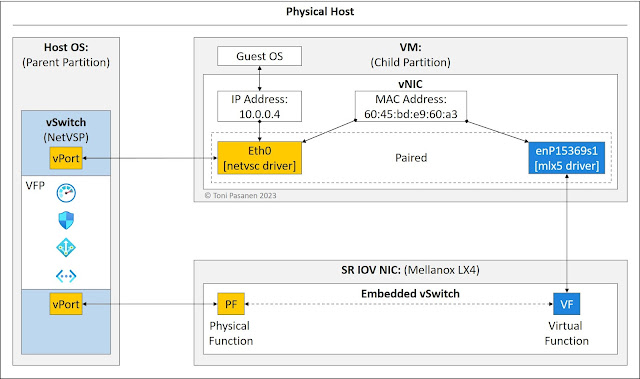
Enterprises that keep simplicity, unity, and automation in mind while creating a multi-cloud networking strategy will alleviate the burden on their IT teams and see the most efficient results.Azure Host-Based Networking: vNIC Interface Architecture – Synthetic Interface and Virtual Function
Before moving to the Virtual Filtering Platform (VFP) and Accelerated
Network (AccelNet) section, let’s look at the guest OS vNIC interface
architecture. When we create a VM, Azure automatically attaches a virtual NIC
(vNIC) to it. Each vNIC has a synthetic interface, a VMbus device, using a
netvsc driver. If the Accelerated Networking (AccelNet) is disabled on a VM,
all traffic flows pass over the synthetic interface to the software switch.
Azure hosts servers have Mellanox/NVIDIA Single Root I/O Virtualization
(SR-IOV) hardware NIC, which offers virtual instances, Virtual Function (VF),
to virtual machines. When we enable AccelNet on a VM, the mlx driver is
installed to vNIC. The mlx driver version depends on an SR-IOV type. The mlx
driver on a vNIC initializes a new interface that connects the vNIC to an
embedded switch on a hardware SR-IOV. This VF interface is then associated with
the netvsc interface. Both interfaces use the same MAC address, but the IP
address is only associated with the synthetic interface. When AccelNet is
enabled, VM’s vNIC forwards VM data flows over the VF interface via the
synthetic interface. This architecture allows In-Service Software Updates
(ISSU) for SR-IOV NIC drivers.
Note! Exception
traffic, a data flow with no flow entries on a UFT/GFT, is forwarded through VFP
in order to create flow-action entries to UFT/GFT.
Figure 1-1: Azure Host-Based SDN Building Blocks.
Continue reading
Email Link Isolation: your safety net for the latest phishing attacks


Email is one of the most ubiquitous and also most exploited tools that businesses use every single day. Baiting users into clicking malicious links within an email has been a particularly long-standing tactic for the vast majority of bad actors, from the most sophisticated criminal organizations to the least experienced attackers.
Even though this is a commonly known approach to gain account access or commit fraud, users are still being tricked into clicking malicious links that, in many cases, lead to exploitation. The reason is simple: even the best trained users (and security solutions) cannot always distinguish a good link from a bad link.
On top of that, securing employees' mailboxes often results in multiple vendors, complex deployments, and a huge drain of resources.
Email Link Isolation turns Cloudflare Area 1 into the most comprehensive email security solution when it comes to protecting against phishing attacks. It rewrites links that could be exploited, keeps users vigilant by alerting them of the uncertainty around the website they’re about to visit, and protects against malware and vulnerabilities through the user-friendly Cloudflare Browser Isolation service. Also, in true Cloudflare fashion, it’s a one-click deployment.
Protecting against deceptive links
With more than a couple Continue reading
How Cloudflare Area 1 and DLP work together to protect data in email


Threat prevention is not limited to keeping external actors out, but also keeping sensitive data in. Most organizations do not realize how much confidential information resides within their email inboxes. Employees handle vast amounts of sensitive data on a daily basis, such as intellectual property, internal documentation, PII, or payment information and often share this information internally via email making email one of the largest locations confidential information is stored within a company. It comes as no shock that organizations worry about protecting the accidental or malicious egress of sensitive data and often address these concerns by instituting strong Data Loss Prevention policies. Cloudflare makes it easy for customers to manage the data in their email inboxes with Area 1 Email Security and Cloudflare One.
Cloudflare One, our SASE platform that delivers network-as-a-service (NaaS) with Zero Trust security natively built-in, connects users to enterprise resources, and offers a wide variety of opportunities to secure corporate traffic, including the inspection of data transferred to your corporate email. Area 1 email security, as part of our composable Cloudflare One platform, delivers the most complete data protection for your inbox and offers a cohesive solution when including additional services, such as Data Loss Continue reading
One-click data security for your internal and SaaS applications


Most of the CIOs we talk to want to replace dozens of point solutions as they start their own Zero Trust journey. Cloudflare One, our comprehensive Secure Access Service Edge (SASE) platform can help teams of any size rip out all the legacy appliances and services that tried to keep their data, devices, and applications safe without compromising speed.
We also built those products to work better together. Today, we’re bringing Cloudflare’s best-in-class browser isolation technology to our industry-leading Zero Trust access control product. Your team can now control the data in any application, and what a user can do in the application, with a single click in the Cloudflare dashboard. We’re excited to help you replace your private networks, virtual desktops, and data control boxes with a single, faster solution.
Zero Trust access control is just the first step
Most organizations begin their Zero Trust migration by replacing a virtual private network (VPN). VPN deployments trust too many users by default. In most configurations, any user on a private network can reach any resource on that same network.
The consequences vary. On one end of the spectrum, employees in marketing can accidentally stumble upon payroll amounts for the Continue reading
Improved access controls: API access can now be selectively disabled


Starting today, it is possible to selectively scope API access to your account to specific users.
We are making it easier for account owners to view and manage the access their users have on an account by allowing them to restrict API access to the account. Ensuring users have the least amount of access they need, and maximizing visibility of the access is critical, and our move today is another step in this direction.
When Cloudflare was first introduced, a single user had access to a single account. As we have been adopted by larger enterprises, the need to maximize access granularity and retain control of an account has become progressively more important. Nowadays, enterprises using Cloudflare could have tens or hundreds of users on an account, some of which need to do account configuration, and some that do not. In addition, to centralize the configuration of the account, some enterprises have a need for service accounts, or those shared between several members of an organization.
While account owners have always been able to restrict access to an account by their users, they haven’t been able to view the keys and tokens created by their users. Restricting use of the Continue reading
How Cloudflare CASB and DLP work together to protect your data
Cloudflare’s Cloud Access Security Broker (CASB) scans SaaS applications for misconfigurations, unauthorized user activity, shadow IT, and other data security issues. Discovered security threats are called out to IT and security administrators for timely remediation, removing the burden of endless manual checks on a long list of applications.
But Cloudflare customers revealed they want more information available to assess the risk associated with a misconfiguration. A publicly exposed intramural kickball schedule is not nearly as critical as a publicly exposed customer list, so customers want them treated differently. They asked us to identify where sensitive data is exposed, reducing their assessment and remediation time in the case of leakages and incidents. With that feedback, we recognized another opportunity to do what Cloudflare does best: combine the best parts of our products to solve customer problems.
What’s underway now is an exciting effort to provide Zero Trust users a way to get the same DLP coverage for more than just sensitive data going over the network: SaaS DLP for data stored in popular SaaS apps used by millions of organizations.
With these upcoming capabilities, customers will be able to connect their SaaS applications in just a few clicks and scan them Continue reading
Updates: AWS Networking
It didn’t make sense to update Amazon Web Services Networking webinar before the re:Invent conference – even though AWS introduced only a few networking features during the conference, at least one of them made a significant impact on the materials.
However, once the conference was over, I went over the to-do list that has been slowly accumulating for months and spent days updating over a dozen videos1. The major changes include:
Updates: AWS Networking
It didn’t make sense to update Amazon Web Services Networking webinar before the re:Invent conference – even though AWS introduced only a few networking features during the conference, at least one of them made a significant impact on the materials.
However, once the conference was over, I went over the to-do list that has been slowly accumulating for months and spent days updating over a dozen videos1. The major changes include: