Another Exciting New Beginning – Juniper!
I’ve recently taken on a new Product Management role at Juniper Networks. I will be handling the EX platform. While this is an exciting time for me and I expect to be challenged, it does curtail my independence somewhat as a blogger. That’s the price to pay when you work for a vendor, (even though … Continue reading Another Exciting New Beginning – Juniper!DDoS Activity in the Context of Hong Kong’s Pro-democracy Movement
In early August, we examined data demonstrating a striking correlation between real-world and online conflict [1], which ASERT tracks on a continual basis [2-7]. Recent political unrest provides another situation in which strong correlative indicators emerge when conducting time-series analysis of DDoS attack data.
The latest round of pro-democracy protests in Hong Kong began on September 22nd when “. . . Students from 25 schools and universities go ahead with a week-long boycott to protest Beijing’s decision to proceed with indirect elections for Hong Kong’s Chief Executive position.” [8]. The protests ramped up on September 28th when a larger pro-democracy group, Occupy Central with Love and Peace, combined forces with the student demonstrators [8-9]. On October 1st, protesters vowed to increased the level of civil disobedience if Hong Kong’s Chief Executive, Leung Chun-Ying, did not step down [10]. Since that time, tensions have increased, with police crackdowns, tear gas, barricades, skirmishes, shutdowns of government buildings and infrastructure, and heavy use of social media to promote both pro-and anti-protest sentiment. By examining Arbor ATLAS Internet-wide attack visibility data we have identified DDoS attack activity in the APAC region which correlates strongly with the ebb and flow Continue reading
Dell World: Driving Innovation in a New Era
I just returned from Dell World in Austin, Texas this past week. It’s one of my favorite events because not only does this week bring out hundreds if not thousands of new and innovative ideas, it also brings together thousands of people from around the world with different experiences and backgrounds.
 This event was like no other Dell event that I’ve attended. First, it actually rained in Austin. For two days straight! But more importantly (and as dramatic), as a private company, Dell had a very different vibe. Michael Dell repeatedly said that this was the first time he was having fun in a long time, and looking at the crowd, you could sense it! The general feel was that this new Dell could take on any new challenge and could do so swiftly. Always optimize for the long run and drive innovation to accelerate business.
This event was like no other Dell event that I’ve attended. First, it actually rained in Austin. For two days straight! But more importantly (and as dramatic), as a private company, Dell had a very different vibe. Michael Dell repeatedly said that this was the first time he was having fun in a long time, and looking at the crowd, you could sense it! The general feel was that this new Dell could take on any new challenge and could do so swiftly. Always optimize for the long run and drive innovation to accelerate business.
It’s very evident that the software-defined world is changing. At Del l World you could feel the buzz and witness each and every company’s evolution and observe how each product is helping evolve the face of the entire IT ecosystem. With all of the hype surrounding the software-defined market, I’m happy to have had Continue reading
l World you could feel the buzz and witness each and every company’s evolution and observe how each product is helping evolve the face of the entire IT ecosystem. With all of the hype surrounding the software-defined market, I’m happy to have had Continue reading
Kicking the Tires on Cisco’s onePK
Recently, I experimented with Cisco’s onePK. What follows are observations on onePK, as well as some details on the mechanics of creating a onePK connection. For those of you that are not familiar with onePK–it is an API created by Cisco that they support on various IOS, IOS-XR, and IOS-XE devices. onePK was announced in 2012 […]
Author information
The post Kicking the Tires on Cisco’s onePK appeared first on Packet Pushers Podcast and was written by Kirk Byers.
Migrating to the Ghost Blogging Platform
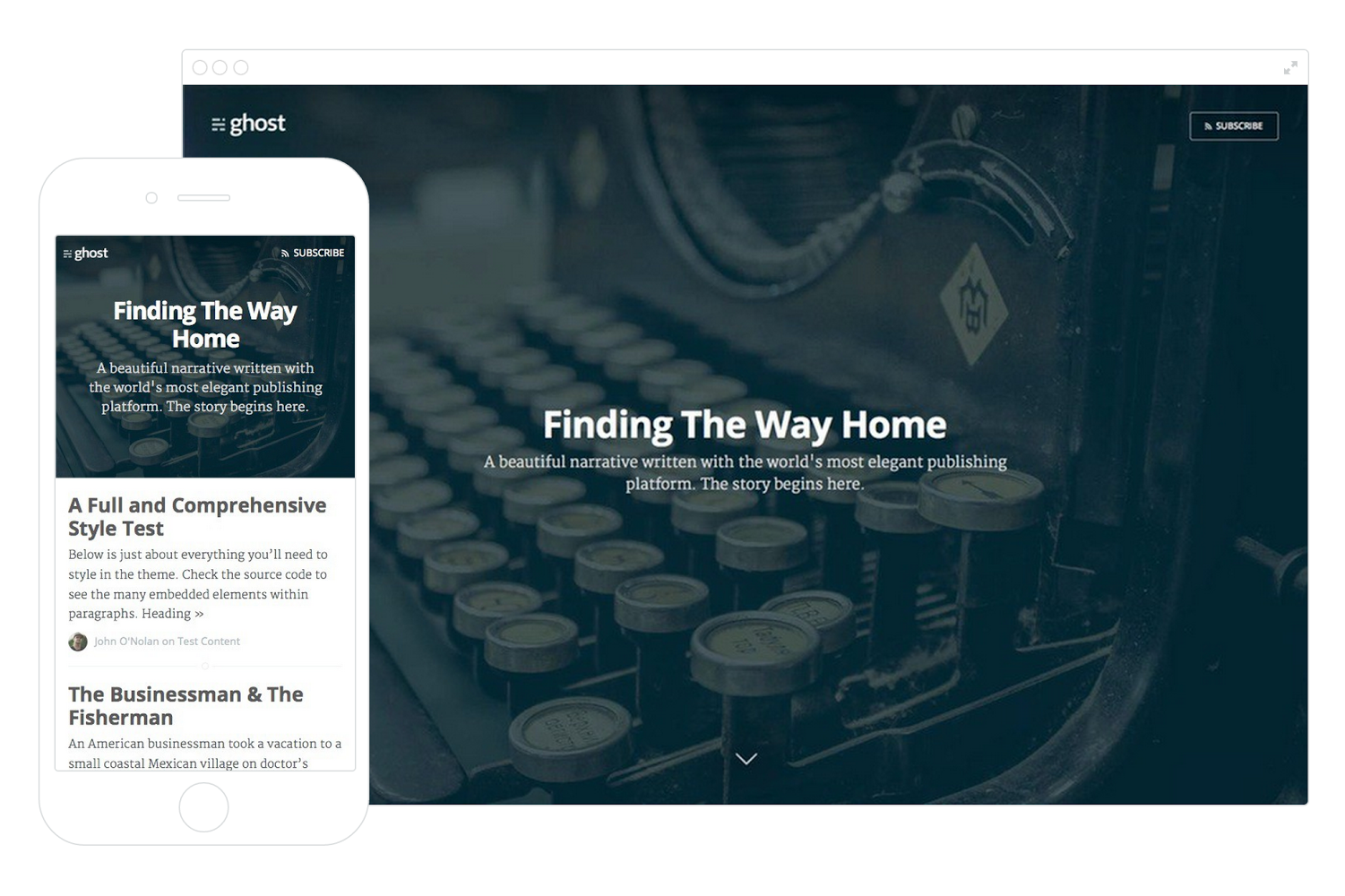
For those of you that follow the CloudFlare blog, you’ll know that we try to be prolific. We have industry leaders like Matthew Prince, John Graham-Cumming, Nick Sullivan, and others publishing pieces weekly from the front lines of internet performance and security. We’re also big fans of open source software, which is used in almost everything we do.
A little over a year ago we watched as a brand new independent open source blogging platform called Ghost started making waves, raising over $300,000 on Kickstarter. A little later, we reached out to the team to see if CloudFlare could help make the lightning-fast Node.js platform even faster and more secure on the Ghost(Pro) hosted service.
In March, Ghost announced that their entire Pro network was powered by CloudFlare, and today we’re pleased to announce that the CloudFlare blog is now running on Ghost.
While things look largely the same, you’ll find new and improved RSS feeds as well as tag and author archives to allow you to browse through our backlog of content more easily. The biggest improvement by far, though, is in the writing tools which we now have available to us—meaning our team is Continue reading
Automatic logon to vCenter using vMA/SDK for Perl
One of the most useful appliance for vSphere administration is a Linux based VM called vMA (vSphere Management Assistant ). It’s a simple SUSE Linux installation with the vSphere SDK for Perl installed. Both method will provide useful tools like esxcli, vmkfstools, vicfg-* and so on. Each command can read credentials as parameters: $ esxcli --server vcenter.example.com --username example\vsphereadmin […]The Trap of Net Neutrality

The President recently released a video and statement urging the Federal Communications Commission (FCC) to support net neutrality and ensure that there will be no “pay for play” access to websites or punishment for sites that compete against a provider’s interests. I wholeheartedly support the idea of net neutrality. However, I do like to stand on my Devil’s Advocate soapbox every once in a while. Today, I want to show you why a truly neutral Internet may not be in our best interests.
Lawful Neutral
If the FCC mandates a law that the Internet must remain neutral, it will mean that all traffic must be treated equally. That’s good, right? It means that a provider can’t slow my Netflix stream or make their own webmail service load faster than Google or Yahoo. It also means that the provider can’t legally prioritize packets either.
Think about that for a moment. We, as network and voice engineers, have spent many an hour configuring our networks to be as unfair as possible. Low-latency queues for voice traffic. Weighted fair queues for video and critical applications. Scavenger traffic classes and VLANs for file sharers and other undesirable bulk noise. These plans take weeks to Continue reading
Response: Cisco, Arista Disaggregating
Jim Duffy wrote an interesting article on Network World’s Cisco Connection blog called “Cisco, Arista Disaggregating?” in which he speculates that Cisco and Arista may make their network operating systems (NOS) available for use on bare metal switches. Is there … Continue reading
If you liked this post, please do click through to the source at Response: Cisco, Arista Disaggregating and give me a share/like. Thank you!
Response: Cisco, Arista Disaggregating
 Jim Duffy wrote an interesting article on Network World’s Cisco Connection blog called “Cisco, Arista Disaggregating?” in which he speculates that Cisco and Arista may make their network operating systems (NOS) available for use on bare metal switches.
Jim Duffy wrote an interesting article on Network World’s Cisco Connection blog called “Cisco, Arista Disaggregating?” in which he speculates that Cisco and Arista may make their network operating systems (NOS) available for use on bare metal switches.
Is there any mileage in this idea?
Old News, New Timing
The idea of the big players selling their software for use on generic hardware has been floating around pretty much since SDN hit the news and the first bare metal switches came out, with Cisco for example looking like they were pretending that SDN wasn’t a thing, and their position was secure if they continued to do what they already did. To be honest, I think Cisco is still paying the price for initially lacking a strategy, then embracing SDN in such a confusing way. Nonetheless, the idea isn’t new, but has the market moved to a position where Cisco and Arista really need to do this? And what of Juniper; are they immune to being sucked into the bare metal market?
Special Sauce
In addition to being a good addition to awesome music of G. Love, for companies like Cisco Arista and Juniper, their “special sauce” these days Continue reading
Integrating HP addons to VMware Update Manager
Honestly I don’t like customized ISO images for VMware ESXi. I prefer to know what software is installed and how to upgrade it. This short guide will show how to integrate HP addons for VMware in the Update Manager (VUM). Open the vClient -> Home -> Update Manager -> Download Settings -> Add Download source: Source […]Understanding IPv6: Solicited-Node Multicast In Action
In the last installment of her IPv6 series, Denise Fishburne explains how to find the MAC address associated with a Layer 3 IPv6 address.VMware Update Managet (VUM) fail after upgrade
Sometimes after a vSphere upgrade Update Manager (VUM) can fail with the following error: There was an error connecting VMware vSphere Update Manager – [vcenter.example.com:443]. Database temporarily unavailable or has network problems. The easiest way is to reconfigure the VUM using the VMwareUpdateManagerUtility.exe utility installed in the VMware Update Manager program path (usually C:Program Files (x86)VMwareInfrastructureUpdate Manager): […]An industry in transition
The tendency of most companies is to talk strategy and vision. Almost every technology company can paint a future that is somehow more elegant based on their product’s fit into customer plans. And, as a sales leader, if you find a company whose vision you find compelling enough to inspire you to share it with customers, you’re probably feeling pretty good about things.
But sales is ultimately measured on wins and losses. And there is no taking solace in a grand vision if you cannot meaningful and immediately make a difference in a customer’s life. So as much as sales is about demonstrating a better future, there is no substitute for solving immediate pain.
This means that the ideal landing spot for anyone in a sales role is a company that thinks big but is committed to enabling the game changing vision for today’s customer problem set.You want to be a part of an organization that wants to do nothing short of changing the world, but who has the focus to do it in ways that provide immediate tangible benefit.
I am certain I have found that in Plexxi.
Before joining Plexxi as the head of Worldwide Sales, I Continue reading
Deploying VMware vCenter Operations (vCOPS)
Deploying the VMware vCOPS appliance is an easy task with only one prerequisite: IP pool. An IP pool is IP pools provide a network identity to vApps. An IP pool is a network configuration that is assigned to a network used by a vApp. The vApp can then leverage vCenter Server to automatically provide an […]Failed to deploy an OVA
Deploying an OVA to a VMware vSphere infrastructure can fail with the following error: Failed to deploy OVF package: The request was aborted: The request was cancelled. The OVA file can be damaged. Because an OVA file is a TAR, the archive can be tested using 7-Zip. Open the archive, use the verify function and see the […]A Month of SDN
My calendar for the following four weeks is jam-packed with SDN events:
- It starts today with a 3-hour SDN presentation in Ljubljana, Slovenia;
- I’m running a 2-day SDN-focused on-site workshop next week, followed by Scaling Overlay Virtual Networks webinar (register now, we’re slowly running out of space);
- The week of November 24th starts with an SDN meetup in Stockholm and continues with SDN/SDDC event in Rome;
- Finally, I’m running an OpenFlow Deep Dive webinar and another on-site NSX/SDN workshop in early December.
All the travel might affect my blogging frequency, but I still have a few podcasts in the editing queue, so you’ll have something to listen to in the meantime ;)
SDN Analytics and Orchestration from the 17th Annual SDN/MPLS Conference
SDN Analytics & Orchestration from the 17th Annual SDN/MPLS Conference
by Steve Harriman, VP of Marketing - November 11, 2014
Last week at the SDN/MPLS [1] conference in Washington, D.C., large service providers, research organizations and academia, and equipment manufacturers from around the world gathered to hear about the latest SDN/NFV developments. Cengiz Alaettinoglu, Packet Design’s CTO, contributed his insights and experience by presenting at the conference on “SDN Analytics: Bridging Overlay and Underlay Networks.” His premise is that underlay routing issues will impact overlay network performance, thus creating the need for SDN analytics to correlate the two and provide management visibility.

Figure 1. SDN Analytics can correlate the impact of underlay network issues on overlay performance.

- Topology (IGP, BGP, RSVP-TE, L2/3 VPNs, OpenFlow tables)
- Traffic (real-time and historical traffic matrices, and projected demands)
- Performance (jitter, packet delay/loss, MOS scores, Continue reading
The Best Presentations on SDN Analytics and Wide Area Orchestration at SDN/MPLS 2014
The Best Presentations on SDN Analytics and Wide Area Orchestration at SDN/MPLS 2014
by Cengiz Alaettinoglu, CTO - November 11, 2014
I attended the SDN/MPLS conference in Washington, D.C. last week, where I presented on the importance of analytics for WAN SDN application bandwidth scheduling and the need for even richer analytics when looking at the data center, network edge and WAN SDN holistically. In my presentation I highlighted the importance of accurate traffic demand matrices and the need to consider failures when selecting paths, so that the network can survive them without creating congestion. I was not the only one talking about WAN orchestration and analytics.
One of the most interesting presentations in my opinion was by Douglas Freimuth of IBM. Douglas presented his work titled “Orchestrated Bandwidth-on-Demand for Cloud Services.” It is a collaboration between IBM, Ciena, and AT&T. They carried out the work in a laboratory test bed.
In the test bed, there were three data centers (Los Angeles, New York and Chicago) running OpenStack. When VM workload in the Los Angeles data center exceeded a threshold, some of the VMs were moved to the New York data center to reduce the load. Continue reading
How to IT: Chasing the Certs
Let me kick this blog off with a little bit of background information about me. I am an IT worker born and raised in Houston, TX. ICloudFlare and SHA-1 Certificates

At CloudFlare, we’re dedicated to ensuring sites are not only secure, but also available to the widest audience. In the coming months, both Google’s Chrome browser and Mozilla’s Firefox browser are changing their policy with respect to certain web site certificates. We are aware of these changes, and we have modified our SSL offerings to ensure customer sites continue to be secure and available to all visitors.
Chrome (and Firefox) and SHA-1
Google will be making changes to its Chrome browser in upcoming versions to change the way they treat certain web site certificates based on their digital signature. These changes affect over 80% of websites.
As described in our blog post on CFSSL, web site certificates are organized using a chain of trust. Digital signatures are the glue that connects the certificates in the chain. Each certificate is digitally signed by its issuer using a digital signature algorithm defined by the type of key and a cryptographic hash function (such as MD5, SHA-1, SHA-256).
Starting in Chrome 39 (to be released this month, November 2014), certificates signed with a SHA-1 signature algorithm will be considered less trusted than those signed with a more modern SHA-2 algorithm. This change Continue reading