Response: RFC 7045 – Transmission and Processing of IPv6 Extension Headers
IETF RFC on the Standards Tracks that talks about the problem of chaining headers in IPv6. I’m getting a sense of deja-vu since this was also has issue with IPv4 and, ultimately, use of chained IPv4 headers died away. If they encounter an unrecognised extension header type, some firewalls treat the packet as suspect and drop it. Unfortunately, […]
The post Response: RFC 7045 – Transmission and Processing of IPv6 Extension Headers appeared first on EtherealMind.
What is Unidirectional Automation?
I was pleased as punch to wake up the other day and read Marten Terpstra’s blog post on getting over the fear of using automation to make changes on our network infrastructure. He illuminated a popular excuse that I’ve heard myself on multiple occasions – that automation is great for things like threshold alarms, or pointing out the percieved root cause of a problem, but not actually fixing the problem. The idea is that the problems that occur on a regular basis, or even performing configuration changes in the first place – is a specialized task that a warm-blooded human being absolutely, no-doubt must take total control of in order to be successful.
With the right implementation, this idea is, of course, rubbish. I asked a question on Twitter not too long ago in preparation for a presentation I was about to give. I have a decent amount of experience working with VMware vSphere, and knew there were some experienced server virtualization folks following me, so I asked about a feature that was thought of in similar light not too long ago:
For those running vSphere, do you have DRS enabled and set to something other than manual? If not, why not? Trying Continue reading
What is Unidirectional Automation?
I was pleased as punch to wake up the other day and read Marten Terpstra’s blog post on getting over the fear of using automation to make changes on our network infrastructure. He illuminated a popular excuse that I’ve heard myself on multiple occasions - that automation is great for things like threshold alarms, or pointing out the percieved root cause of a problem, but not actually fixing the problem.What is Unidirectional Automation?
I was pleased as punch to wake up the other day and read Marten Terpstra’s blog post on getting over the fear of using automation to make changes on our network infrastructure. He illuminated a popular excuse that I’ve heard myself on multiple occasions - that automation is great for things like threshold alarms, or pointing out the percieved root cause of a problem, but not actually fixing the problem.Linking Purpose to Profits
by Andy McFarland, VP of Customer Care - July 8, 2014
Three bricklayers were working side by side. When asked, “What are you doing?” the first bricklayer replied, “I’m laying bricks.” The second bricklayer was asked and he answered, “Feeding my family.” The third bricklayer when asked the question, “What are you doing?” responded, “I’m building a cathedral.”
This story illustrates the power of purpose. In a previous post I suggested that we are all in the customer service business, and I posed some questions to help teams see linkages between what they do and how that impacts customers and the company. The reason this is so important is because purpose leads to employee engagement, which leads to profitability.
To maximize our personal satisfaction and employee engagement, we need three ingredients: purpose, autonomy, and mastery. (See Daniel Pink’s explanation in this video.) As leaders we must work relentlessly to break down barriers to allow our people the freedom to thrive.
To help people understand the purpose of their work, leaders link tasks to outcomes and benefits. Some people see linkages naturally, while others require leaders to communicate Continue reading
IP Subnetting Part 3: Understanding the Binary
I’ve often stated how simple subnetting really is. While each individual concept is rather simple, it is the combination that make the holistic process challenging. If we, as humans, could look at the process more like computers and network devices, subnetting would be a much simpler process. In short, some knowledge of binary is an important requirement prior to sharing more complex subnetting examples.
This article will demonstrate the process of converting binary to and from the more familiar decimal numbering system. This will establish the necessary baseline knowledge required to understand when applying subnet masks to IP addresses. The first question we need to answer is–
What is Binary?
Binary, also known as base-2, is a numbering system in which each position only has two possible values. We often represent one possible value as zero and the other possible value as one. Alternatively, it could be represented many other ways including: positive and negative voltage, black and white colors, voltage and no voltage present, or null and not null. This simplicity in representation is what makes the system so advantageous for a computer’s limited discreet capabilities.
In this article, we will represent binary digits using either a one or a Continue reading
Raspberry Pi as a Deliciously Simple VPN Endpoint
Being the networking nerd I am, I have a pretty big network at home. And as the denizens of the Packet Pushers IRC channel know, I do a lot of work with VPNs. One of my use cases is sharing the resources on my home network. My friends, family, and coworkers sometimes like to use my network […]
Author information
The post Raspberry Pi as a Deliciously Simple VPN Endpoint appeared first on Packet Pushers Podcast and was written by iggdawg.
Show 195: HP – Real SDN and Virtual Application Networking
HP and Software Defined Networking. HP was one of the earliest supporters of OpenFlow and Software Defined Networking and have continued to build a portfolio of products. In this podcast we talk about SDN applications on security, application management and QoS management.
Author information
The post Show 195: HP – Real SDN and Virtual Application Networking appeared first on Packet Pushers Podcast and was written by Greg Ferro.
Understanding IPv6: The Journey Begins
Why is IPv6 so difficult to understand? Denise Fishburne explains how she began unraveling this complex topic.Ansible Rapid Development Environment using Vagrant
First off, this post isn’t a straight-up networking post; although it does contain networking content (enabling Vagrant VMs to communicate over a physical data network) it’s more about constructing a rapid development environment for Ansible. Ansible is a configuration management tool that manages nodes over SSH, and only requires that Python 2.4 or later is […]
Author information
The post Ansible Rapid Development Environment using Vagrant appeared first on Packet Pushers Podcast and was written by Will Dennis.
Community Show – Multicast Design and Deployment Considerations with Beau Williamson and Orhan Ergun
In this first part of the Multicast Design and Deployment Series , Orhan Ergun talks with Mr.Multicast Beau Williamson about many multicast concepts. They both start from the basic and deep dive many multicast concepts while giving real life examples. Why Multicast?. What are the general use cases in real life ? Layer 2 […]
Author information
The post Community Show – Multicast Design and Deployment Considerations with Beau Williamson and Orhan Ergun appeared first on Packet Pushers Podcast and was written by Orhan Ergun.
Community Show – Multicast Design and Deployment Considerations with Beau Williamson and Orhan Ergun
In this first part of the Multicast Design and Deployment Series, Orhan Ergun talks with Mr. Multicast Beau Williamson about many multicast concepts. They both start from the basic and deep dive many multicast concepts while giving real life examples.
The post Community Show – Multicast Design and Deployment Considerations with Beau Williamson and Orhan Ergun appeared first on Packet Pushers.
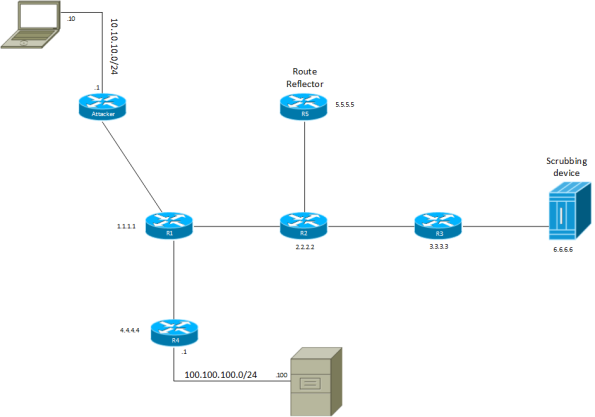
Routing Considerations in DDoS Protection Environments
Lately I have done some studying for the CCDE and one of the things I was
looking at is how to protect against DDoS attacks. I’m not expecting it
to be a big topic for the CCDE but it has some interesting concepts relating
to routing. Take a look at the following topology:
There is an attacker at the top left. R1 is the edge device and then there are a
few more routers, all peering BGP with the RR, which is R5. The server of interest
is 100.100.100.100 and there is a scrubbing device to the far right. All routers
peer iBGP from their loopbacks to the RR, including the scrubbing device.
Normally traffic to 100.100.100.100 would flow through R1 to R4 and then to the
server.
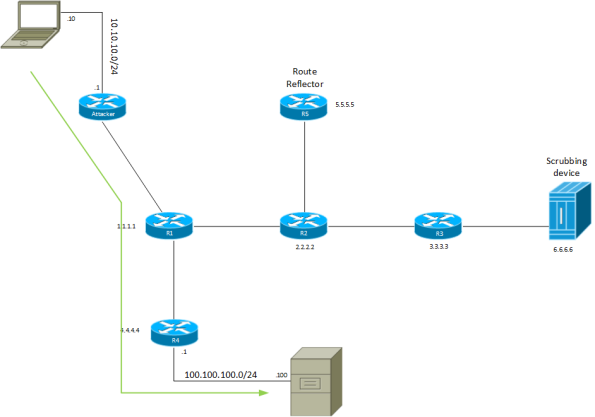
The attacker now starts to flood the server with malicious traffic. This is detected
by the DDoS scrubbing device which starts to announce via BGP a more specific route
than the one advertised by R4. R4 normally advertises 100.100.100.0/24 but the
scrubbing device advertises 100.100.100.100/32. All the other routers will start
to forward traffic to 100.100.100.100 towards Continue reading
Advertising a Default Route Into EIGRP
Let’s get an IPv4 default route into EIGRP. There are a few methods to do it. I hate most of them, though. I think it will be obvious which one I like.
Here’s the lab I have set up to test everything. I want R4 to generate the default in each case.
Default Network – Candidate default. I don’t think I’ve ever used that all my years in networking, but here’s how to use it in EIGRP for a default route. You basically say “If you don’t know where to send a packet, send it to where network X lives.” We’re going to set the 192.168.1.0/24 as the default network, so, in our case X = 192.168.1.0. R4 will tag that route as a default candidate when it advertises it to the rest of the network. The config is easy but requires a stateful (yes, stateful) network to beconfigured as the default.
R4 config: R4(config)#ip default-network 192.168.1.0 ! R1 routes: R1#sh ip route ... 4.0.0.0/24 is subnetted, 1 subnets D 4.4.4.0 [90/435200] via 192.0.2.3, 00:08:33, FastEthernet0/0 [90/435200] via 192.0.2.2, Continue reading
Using Cisco’s DevNet “All-in-One VM” as a Free Router Lab
I know many have been [not so patiently] waiting for the arrival of a Cisco virtual lab. Although I haven’t heard any official release date for VIRL or CML, there is a small scale virtual router lab available today. This lab is the All-in-One Virtual Machine made available on the Cisco DevNet site.
While not a comprehensive lab, it is a quick and easy way to get some real command line experience or test smaller layer 3 challenges. This VM includes 3 routers with a total of 10 routed interfaces in use. There is no access to layer 2, so the topology can only be manipulated by shutting down interfaces on the routers.
Using the DevNet All-in-One Virtual Machine
- Download the OVA File
- Import into VMWare
- Launch the Virtual Machine
- Set Passwords
- Access the Routers
This product downloads as an OVA file. The file is easily imported into VMWare. In my case, I used VMWare Fusion running on OSX. Once downloaded and imported, the VM is launched like any other virtual machine. As it boots, you will notice that this is running in Ubuntu. The initial credentials are cisco/cisco123 and the operating will prompt to change the password.
 Once installed and logged in, you will be Continue reading
Once installed and logged in, you will be Continue reading
Asking for Clarity
 I have a lot of discussions with vendors, peers and other friends in the business. One of the things that I find challenging is the nuances with the language of technology. Our conversations include things like traffic flow, NAT, SDN, Cloud and many of the other industry buzzwords. Our use of terminology often has different meanings to different people (and in different contexts).
I have a lot of discussions with vendors, peers and other friends in the business. One of the things that I find challenging is the nuances with the language of technology. Our conversations include things like traffic flow, NAT, SDN, Cloud and many of the other industry buzzwords. Our use of terminology often has different meanings to different people (and in different contexts).
While I don’t fully subscribe to the, There is no bad question philosophy, I believe questions should be asked liberally. The only questions I hate to hear are from those trying to prove their [superior] knowledge. Beyond that, individual research can help with the learning process. However, everyone should have the confidence to ask those questions necessary to grasp the conversation at hand. More than likely others will benefit from the clarification as well.
The post Asking for Clarity appeared first on PacketU.
Response: IP PBX sales decline 10% | Dell’Oro
The IP PBX business is shrinking as mobile phones replace desk phones. More importantly, voice calls are replaced with chat applications like Skype, FaceTime, SnapChat. Modern companies are using messaging platforms like Slack to replace time wasting telephone calls – we run the Packet Pushers business zero telephone calls. I’ve been predicting this for a year […]
The post Response: IP PBX sales decline 10% | Dell’Oro appeared first on EtherealMind.
Getting ready for next-gen IRF !
HP Comware switches have had IRF (Intelligent Resilient Framework) for years, and it was the basis of more simplified network topologies. Now it seems HP is preparing a next-generation of IRF ! The current IRF implementation (known as IRF2) supports … Continue readingThe crux of the matter
I’ve initially joined Juniper Networks in 2001 and over the years i’ve had the opportunity to establish a relationship with a few of the field people, specially in Europe where i just happen to know a lot of the old timers that built up Juniper’s business in the region.
Over the past few weeks i’d a couple of conversations with some of them that forced me to try to distill my perspective on the current trends in the networking industry to a small set of observations. Often the question that starts the conversation is how I see the applicability of OpenStack and OpenContrail to the key networking markets: carrier, enterprise and cloud/content provider. The question often implies a certain doze of healthy skepticism.
OpenStack and OpenContrail are tools; the evolution that we are seeing at that moment in the industry is deeper than that.
The traditional workflow for a network deployment is to go through architecture, design and operations phases. Traditionally the architecture group selects the top level goals and the technology approach for the deployment and produces an architecture document; from that document the design team then starts working on qualification of equipment, detailed design and operational guide; when Continue reading