Project Safekeeping – protecting the world’s most vulnerable infrastructure with Zero Trust

This post is also available in 简体中文, 日本語, 한국어, Deutsch, Français and Español.

Under-resourced organizations that are vital to the basic functioning of our global communities face relentless cyber attacks, threatening basic needs for health, safety and security.
Cloudflare’s mission is to help make a better Internet. Starting December 13, 2022, we will help support these vulnerable infrastructure by providing our enterprise-level Zero Trust cybersecurity solution to them at no cost, with no time limit.
It is our pleasure to introduce our newest Impact initiative: Project Safekeeping.
Small targets, devastating impacts
Critical infrastructure is an obvious target for cyber attack: by its very definition, these are the organizations and systems that are crucial for the functioning of our society and economy. As such, these organizations cannot have prolonged interruptions in service, or risk having sensitive data exposed.
Our conversations over the past few months with government officials in Australia, Germany, Japan, Portugal, and the United Kingdom show that they are focused on the threat to critical infrastructure, but resource constraints mean that their attention is on protecting large organizations – immense financial institutions, hospital networks, oil pipelines, and airports. Yet, the small critical infrastructure organizations that Continue reading
DPU Hype Considered Harmful
The hype generated by the “VMware supports DPU offload” announcement already resulted in fascinating misunderstandings. Here’s what I got from a System Architect:
We are dealing with an interesting scenario where a customer had limited data center space, but applications demand more resources. We are evaluating whether we could offload ESXi processing to DPUs (Pensando) to use existing servers as bare-metal servers. Would it be a use case for DPU?
First of all, congratulations to whichever vendor marketer managed to put that guy in that state of mind. Well done, sir, well done. Now for a dose of reality.
DPU Hype Considered Harmful
The hype generated by the “VMware supports DPU offload” announcement already resulted in fascinating misunderstandings. Here’s what I got from a System Architect:
We are dealing with an interesting scenario where a customer had limited data center space, but applications demand more resources. We are evaluating whether we could offload ESXi processing to DPUs (Pensando) to use existing servers as bare-metal servers. Would it be a use case for DPU?
First of all, congratulations to whichever vendor marketer managed to put that guy in that state of mind. Well done, sir, well done. Now for a dose of reality.
How I Overcame My Fear of Commit(ment)

This is a retelling of a presentation I gave at work. In it, I describe a mechanism I've started using to raise the quality of artifacts I check into version control.
Is Secured Routing a Market Failure?
The Internet largely operates in a space defined by markets rather than an intricate framework of regulation. Using a lens of market dynamics and looking at the level to which market-based incentives exist for actors, is the adoption of routing security heading in the direction of market failure? If so, then how should we respond?Network Break 411: Cisco Revamps Certification Schedules; FTC Says Game Over For Microsoft’s Activision Bid
Take a Network Break! On today's episode we cover a new certification roadmap from Cisco, speculate on the future of corporate office space, and delve into an FTC lawsuit that aims to stop Microsoft's $69 billion purchase of game developer Activision. We also cover Broadcom financial results and space networking stories from Apple and SpaceX.
The post Network Break 411: Cisco Revamps Certification Schedules; FTC Says Game Over For Microsoft’s Activision Bid appeared first on Packet Pushers.
Network Break 411: Cisco Revamps Certification Schedules; FTC Says Game Over For Microsoft’s Activision Bid
Take a Network Break! On today's episode we cover a new certification roadmap from Cisco, speculate on the future of corporate office space, and delve into an FTC lawsuit that aims to stop Microsoft's $69 billion purchase of game developer Activision. We also cover Broadcom financial results and space networking stories from Apple and SpaceX.Learn Vi As A Network or Sysadmin Today?
TL;DR: If you’re a sysadmin or network administrator who doesn’t know vi/vim, I wouldn’t worry about it. Nano as a Linux/Unix editor will suffice in just about every situation you’re likely to be involved in.
Vi (and its successor, vim) is a text editor commonly used on Unix-like systems like Linux, the BSDs, and MacOS (I’m not getting into a what is/isn’t Unix discussion). If it’s remotely Unix-like, typing “vi” will likely get you vi, vim, or another variant. You can pretty much count on vi being there.
When I started as a Unix admin back in the 1990s, primarily working with Solaris and SunOS, knowing your way around vi is what I would classify as an essential skill. The other editors were pico (easy to learn) and Emacs (very high learning curve). Vi versus Emacs was one of the first technology “religious” wars.
I don’t have much experience with Emacs. I gave it a go in the late 1990s at one point, but found the learning curve too discouraging. Besides, I could already do everything I needed to with vi and Emacs users didn’t seem to be able to do something I couldn’t do. It felt like to me Continue reading
Tech Bytes: Redefining Secure Remote Access With Fortinet’s SASE Solution (Sponsored)
Today on the Tech Bytes podcast we explore sponsor Fortinet’s Secure Access Service Edge, or FortiSASE, offering, including the FortiClient agent, what cloud-delivered security services are available, SASE use cases, and more. Our guest is Nirav Shah, VP of Products at Fortinet.
The post Tech Bytes: Redefining Secure Remote Access With Fortinet’s SASE Solution (Sponsored) appeared first on Packet Pushers.
Tech Bytes: Redefining Secure Remote Access With Fortinet’s SASE Solution (Sponsored)
Today on the Tech Bytes podcast we explore sponsor Fortinet’s Secure Access Service Edge, or FortiSASE, offering, including the FortiClient agent, what cloud-delivered security services are available, SASE use cases, and more. Our guest is Nirav Shah, VP of Products at Fortinet.Advanced Technology on Display at AWS re:Invent
AWS showcased some real-life examples of many of its advanced technologies in the Expo Hall at the recent AWS re:Invent conference.Expanding Area 1 email security to the Athenian Project

This post is also available in 简体中文, Deutsch, Français and Español.

Election security encompasses a wide variety of measures, including the protection of voting machines, election office networks, voter registration databases, and other systems that manage the electoral process. At Cloudflare, we have reported on threats to state and local governments under the Athenian Project, how we prepare political campaigns and state parties under Cloudflare for Campaigns for election season, and our work with organizations that report on election results and voting rights groups under Project Galileo.
Since the 2022 US midterm elections, we have been thinking about how we help state and local governments deflect larger cyber threats that target the election community and have been analyzing the biggest problems they are facing. In October 2022, Jen Easterly, the director of the Cybersecurity and Infrastructure Security Agency, said, “The current election threat environment is more complex than it has ever been.” Amid threats, intimidation toward election workers, and cyber attacks against election infrastructure and operations, preparing for elections is no easy task.
At Cloudflare, our mission is to help build a better Internet. The Internet plays a key role in promoting democracy and ensuring Continue reading
Two months later: Internet use in Iran during the Mahsa Amini Protests


A series of protests began in Iran on September 16, following the death in custody of Mahsa Amini — a 22-year-old who had been arrested for violating Iran’s mandatory hijab law. The protests and civil unrest have continued to this day. But the impact hasn’t just been on the ground in Iran — the impact of the civil unrest can be seen in Internet usage inside the country, as well.
With the proliferation of smartphones and the ubiquity of the Internet that has resulted, it’s no longer simply the offline world impacting the Internet; what happens on the Internet is impacting the offline world, too. For that reason, it’s not surprising that in order to limit the spread of the protests — both news of it happening and the further organization of civil unrest — the Iranian government introduced limits on the Internet. This included banning certain social media and communications tools: most notably including Instagram and WhatsApp, which are estimated to be used by over 50% of the Iranian population.
But despite the threat that the protests pose, and the Internet’s enabling role in them, it has not been cut off altogether. In fact, from the perspective of Cloudflare, Continue reading
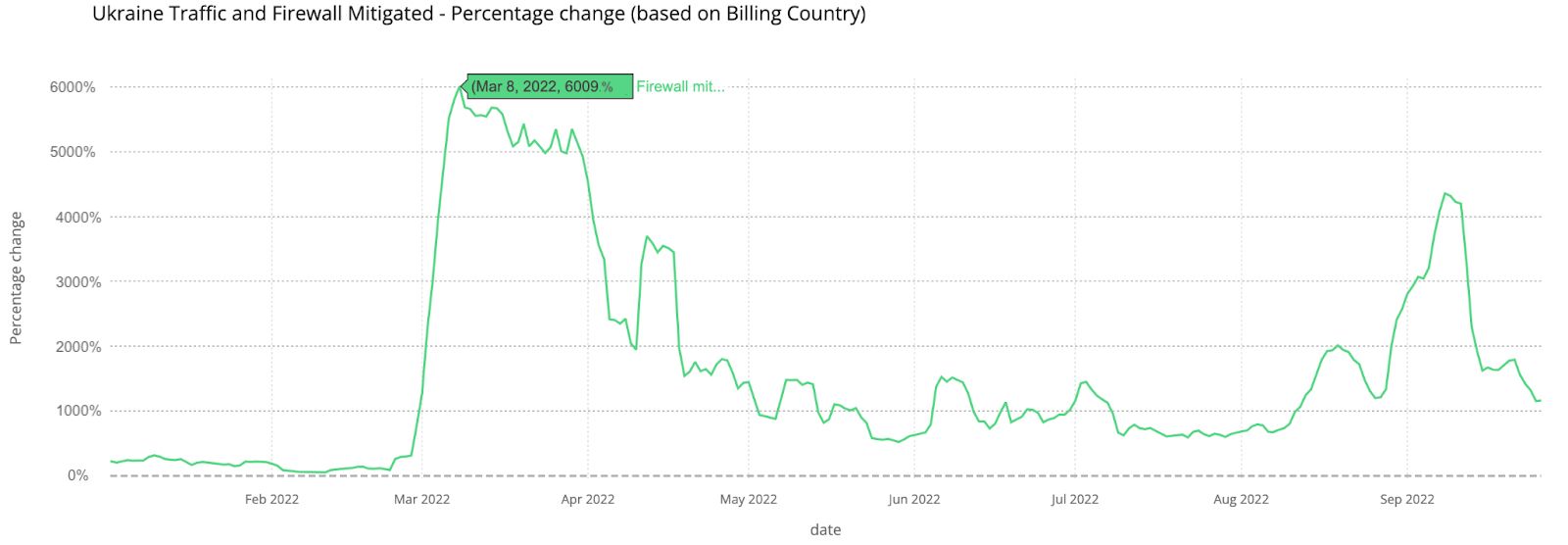
The latest on attacks, traffic patterns and cyber protection in Ukraine


On February 24, 2022, when Russia invaded Ukraine, Cloudflare jumped into action to provide services that could help prevent potentially destructive cyber attacks and keep the global Internet flowing. In the nearly 10 months since that day, we’ve posted about our actions, network traffic patterns, cyberattacks and network outages we’ve seen during the conflict.
During Impact Week, we want to provide an update on where things currently stand, the role of security companies like Cloudflare, and some of our takeaways from the conflict so far.
Cyberattacks on Ukrainian infrastructure and Cloudflare’s assistance
Since the time of the invasion, Ukrainian government and civilian infrastructure has come under a barrage of DDoS and other common cyberattacks. Although the public perception has been that cyberattacks have not played a significant role in the conflict, cyberspace has been an active battlefield. Ukrainian websites saw a significant spike in application layer firewall mitigated attacks in March 2022 and another spike in mid-September. Ukrainian sites have also seen a significant increase in the percentage of requests that were mitigated as attack traffic on a daily average, when compared with Q4 2021. Those spikes are shown below, using a seven-day rolling average:
The challenges of sanctioning the Internet


Following Russia’s invasion of Ukraine, governments around the world, including the US, UK, and EU announced sweeping sanctions targeting the Russian and Belarussian economies. These sanctions prohibit a specified level of economic activity in an effort to use economic influences to punish targeted countries. Almost overnight, we saw unprecedented restrictions put in place for multinational companies doing business in Russia or Belarus.
Separately, recent events in Iran led the US government to authorize additional Internet/communications activities, which were being used widely by average Iranians protesting against the government. This was done by expanding some existing licenses, or exceptions, to sanctions the US has imposed on Iran.
While the use of sanctions as a tool for responding to foreign relations crises is nothing new, the wide-ranging multilateral sanctions that have been imposed on Russia and the recent authorizations in Iran are significant and provide fresh examples of how sanctions can affect access to a free and open global Internet.
Balancing interests in sanctions policy
Cloudflare is committed to complying with all applicable sanctions, including US, UK, and EU sanctions, and we have put in place programs to ensure that compliance. At the same time, we recognize the important role we and Continue reading
How Cloudflare helps secure the inboxes of democracy

This post is also available in 简体中文, 日本語, Français, Español.

We at Cloudflare believe that every candidate, no matter their political affiliation, should be able to operate their campaign without having to worry about the risk of cyberattacks. Malicious attackers such as nation-state threat actors, those seeking monetary reward, or those with too much time on their hands often disagree with our mission and aim to wreak havoc on the democratic process.
Protecting Email Inboxes Is Key In Stopping Attacks
In the past years, malicious actors have used email as their primary threat vector when trying to disrupt election campaigns. A quick search online shows how active attackers still are in trying to compromise election official’s email inboxes.1 Over 90% of damages done to any organization are caused by a phishing attack, making protecting email inboxes a key focus. A well crafted phishing email paired, or an errant click could give an attacker the opportunity to see sensitive information, disseminate false information to voters, or steal campaign donations.
For the United States 2022 midterm elections, Cloudflare protected the inboxes of over 100 campaigns, election officials and public organizations supporting elections. These campaigns ranged from new officials Continue reading
Democratizing access to Zero Trust with Project Galileo

This post is also available in Deutsch, Français, Español, 简体中文.

Project Galileo was started in 2014 to protect free expression from cyber attacks. Many of the organizations in the world that champion new ideas are underfunded and lack the resources to properly secure themselves. This means they are exposed to Internet attacks aimed at thwarting and suppressing legitimate free speech.
In the last eight years, we have worked with 50 partners across civil society to onboard more than 2,000 organizations in 111 countries to provide our powerful cyber security products to those who work in sensitive yet critical areas of human rights and democracy building.
New security needs for a new threat environment
As Cloudflare has grown as a company, we have adapted and evolved Project Galileo especially amid global events such as COVID-19, social justice movements after the death of George Floyd, the war in Ukraine, and emerging threats to these groups intended to silence them. Early in the pandemic, as organizations had to quickly implement work-from-home solutions, new risks stemmed from this shift.
In our conversations with partners and participants, we noticed a theme. The digital divide in terms of cyber security products Continue reading
Network Dictionary: necropost
 What is a necropost?
What is a necropost?