Network Break 409: Regulators Tap Brakes On Broadcom, VMware; Google Settles Location Tracking Charges For $392M
This week's Network Break podcast discusses UK and EU regulators wanting a closer look at Broadcom's VMware acquisition, Google settling with 40 US states over location tracking charges, and the FCC publishing responses from the 15 biggest US mobile providers regarding customer geolocation data tracking, plus even more IT news.A simple BPFTrace to see TCP SendBytes as a Histogram
< MEDIUM: https://raaki-88.medium.com/a-simple-bpftrace-to-see-tcp-sendbytes-as-a-histogram-f6e12355b86c >
A significant difference between BCC and BPF is that BCC is used for complex analysis while BPF programs are mostly one-liners and are ad-hoc based. BPFTrace is an open-source tracer, reference below
https://ebpf.io/ — Excellent introduction to EBPF
https://github.com/iovisor/bpftrace — Excellent Resource.
Let me keep this short, we will try to use BPFTrace and capture TCP
We will need
- Netcat
- DD for generating a dummy 1GB File
- bpftrace installed
To understand the efficiency of this, let’s attach a Tracepoint, a Kernel Static Probe to capture all of the new processes that get triggered, imagine an equivalent of a TOP utility with means of reacting to the event at run-time if required
https://github.com/iovisor/bpftrace/blob/master/docs/reference_guide.md#probes — Lists out type of probes and their utility
We can clearly see we invoked a BPFTrace for tracepoint system calls which takes execve privilege, I executed the ping command and various other commands and you can see that executing an inbound SSH captured invoke of execve-related commands and the system banner.
sudo bpftrace -e 'tracepoint:syscalls:sys_enter_execve { join(args->argv); }'
Attaching 1 probe...
clear
ping 1.1.1.1 -c 1
/usr/bin/clear_console -q
/usr/sbin/sshd -D -o AuthorizedKeysCommand /usr/share/ec2-instance-connect/eic_run_authorized_keys %u Continue reading
Tech Bytes: Run On-Prem Infrastructure Like Public Cloud With vSphere+ (Sponsored)
Today’s Tech Bytes podcast, sponsored by VMware, dives into VMware’s vSphere+. vSphere+ allows you to operate your on-prem workloads and infrastructure as if they were a public cloud. It supports VMs and Kubernetes, and provides admin, developer, and add-on services delivered via SaaS.
The post Tech Bytes: Run On-Prem Infrastructure Like Public Cloud With vSphere+ (Sponsored) appeared first on Packet Pushers.
Tech Bytes: Run On-Prem Infrastructure Like Public Cloud With vSphere+ (Sponsored)
Today’s Tech Bytes podcast, sponsored by VMware, dives into VMware’s vSphere+. vSphere+ allows you to operate your on-prem workloads and infrastructure as if they were a public cloud. It supports VMs and Kubernetes, and provides admin, developer, and add-on services delivered via SaaS.The Linux Kernel Key Retention Service and why you should use it in your next application


We want our digital data to be safe. We want to visit websites, send bank details, type passwords, sign documents online, login into remote computers, encrypt data before storing it in databases and be sure that nobody can tamper with it. Cryptography can provide a high degree of data security, but we need to protect cryptographic keys.
At the same time, we can’t have our key written somewhere securely and just access it occasionally. Quite the opposite, it’s involved in every request where we do crypto-operations. If a site supports TLS, then the private key is used to establish each connection.
Unfortunately cryptographic keys sometimes leak and when it happens, it is a big problem. Many leaks happen because of software bugs and security vulnerabilities. In this post we will learn how the Linux kernel can help protect cryptographic keys from a whole class of potential security vulnerabilities: memory access violations.
Memory access violations
According to the NSA, around 70% of vulnerabilities in both Microsoft's and Google's code were related to memory safety issues. One of the consequences of incorrect memory accesses is leaking security data (including cryptographic keys). Cryptographic keys are just some (mostly random) data stored in Continue reading
So You Want to Be a Network Administrator
Thick skin required. Any application or service performance problem incurred will inevitably lead a network administrator having to prove that it’s not a network problem.netlab Release 1.4.1: Cisco ASAv
The star of the netlab release 1.4.1 is Cisco ASAv support: IPv4 and IPv6 addressing, IS-IS and BGP, and libvirt box building instructions.
Other new features include:
- VRRP on VyOS
- Anycast gateway and VRRP on Dell OS10 (with a bunch of caveats)
- Unnumbered OSPF interfaces on VyOS
- Support for all EVPN bundle services
- FRR version 8.4.0
Upgrading is as easy as ever: execute pip3 install --upgrade networklab.
New to netlab? Start with the Getting Started document and the installation guide.
netlab Release 1.4.1: Cisco ASAv
The star of the netlab release 1.4.1 is Cisco ASAv support: IPv4 and IPv6 addressing, IS-IS and BGP, and libvirt box building instructions.
Other new features include:
- VRRP on VyOS
- Anycast gateway and VRRP on Dell OS10 (with a bunch of caveats)
- Unnumbered OSPF interfaces on VyOS
- Support for all EVPN bundle services
- FRR version 8.4.0
Upgrading is as easy as ever: execute pip3 install --upgrade networklab.
New to netlab? Start with the Getting Started document and the installation guide.
Coding Packets the Shazam Edition
https://codingpackets.com/blog/coding-packets-the-shazam-edition
Day Two Cloud Invite: Recording At TopGolf Las Vegas Nov. 30, 2022
If you're headed to AWS re:Invent in Las Vegas, you can catch Ned & me recording a show live. On Wednesday, November 30, 2022, we’ll be at TopGolf with sponsor Prosimo from 4 to 7 pm. Join us to have some fun! Links and drinks, meet fellow engineers building clouds for their companies, and then watch us record the show. Space is limited, so register at prosimo.io. We’ll see you at TopGolf Las Vegas on Wednesday the 30th!
The post Day Two Cloud Invite: Recording At TopGolf Las Vegas Nov. 30, 2022 appeared first on Packet Pushers.
Day Two Cloud Invite: Recording At TopGolf Las Vegas Nov. 30, 2022
If you're headed to AWS re:Invent in Las Vegas, you can catch Ned & me recording a show live. On Wednesday, November 30, 2022, we’ll be at TopGolf with sponsor Prosimo from 4 to 7 pm. Join us to have some fun! Links and drinks, meet fellow engineers building clouds for their companies, and then watch us record the show. Space is limited, so register at prosimo.io. We’ll see you at TopGolf Las Vegas on Wednesday the 30th!Congestion Control Algorithms Are Not Fair
Creating a mathematical model of queuing in a distributed system is hard (Queuing Theory was one of the most challenging ipSpace.net webinars so far), and so instead of solutions based on control theory and mathematical models we often get what seems to be promising stuff.
Things that look intuitively promising aren’t always what we expect them to be, at least according to an MIT group that analyzed delay-bounding TCP congestion control algorithms (CCA) and found that most of them result in unfair distribution of bandwidth across parallel flows in scenarios that diverge from spherical cow in vacuum. Even worse, they claim that:
[…] Our paper provides a detailed model and rigorous proof that shows how all delay-bounding, delay-convergent CCAs must suffer from such problems.
It seems QoS will remain spaghetti-throwing black magic for a bit longer…
Congestion Control Algorithms Are Not Fair
Creating a mathematical model of queuing in a distributed system is hard (Queuing Theory was one of the most challenging ipSpace.net webinars so far), and so instead of solutions based on control theory and mathematical models we often get what seems to be promising stuff.
Things that look intuitively promising aren’t always what we expect them to be, at least according to an MIT group that analyzed delay-bounding TCP congestion control algorithms (CCA) and found that most of them result in unfair distribution of bandwidth across parallel flows in scenarios that diverge from spherical cow in vacuum. Even worse, they claim that:
[…] Our paper provides a detailed model and rigorous proof that shows how all delay-bounding, delay-convergent CCAs must suffer from such problems.
It seems QoS will remain spaghetti-throwing black magic for a bit longer…
Mastodon – Part 3 – statsd and Prometheus
About this series
I have seen companies achieve great successes in the space of consumer internet and entertainment industry. I’ve been feeling less enthusiastic about the stronghold that these corporations have over my digital presence. I am the first to admit that using “free” services is convenient, but these companies are sometimes taking away my autonomy and exerting control over society. To each their own of course, but for me it’s time to take back a little bit of responsibility for my online social presence, away from centrally hosted services and to privately operated ones.
In my [first post], I shared some thoughts on how I installed a Mastodon instance for myself. In a [followup post] I talked about its overall architecture and how one might use Prometheus to monitor vital backends like Redis, Postgres and Elastic. But Mastodon itself is also an application which can provide a wealth of telemetry using a protocol called [StatsD].
In this post, I’ll show how I tie these all together in a custom Grafana Mastodon dashboard!
Mastodon Statistics
I noticed in the [Mastodon docs], that there’s a one-liner breadcrumb that might be easy to overlook, Continue reading
Worth Reading: Troubleshooting EVPN Control Plane
When trying to decide whether to use EVPN for your next data center fabric, you might want to consider how easy it is to configure and troubleshoot.
You’ll find a few configuration hints in the Multivendor Data Center EVPN part of the EVPN Technical Deep Dive webinar. For the troubleshooting part, check out the phenomenal Troubleshooting EVPN with Arista EOS article by Tony Bourke.
Worth Reading: Troubleshooting EVPN Control Plane
When trying to decide whether to use EVPN for your next data center fabric, you might want to consider how easy it is to configure and troubleshoot.
You’ll find a few configuration hints in the Multivendor Data Center EVPN part of the EVPN Technical Deep Dive webinar. For the troubleshooting part, check out the phenomenal Troubleshooting EVPN with Arista EOS article by Tony Bourke.
Palo Packet Captures
Information on running packet captures and debugging commands to follow traffic flows.
An early look at Thanksgiving 2022 Internet trends
"The more you practice the art of thankfulness, the more you have to be thankful for."
— Norman Vincent Peale, American author
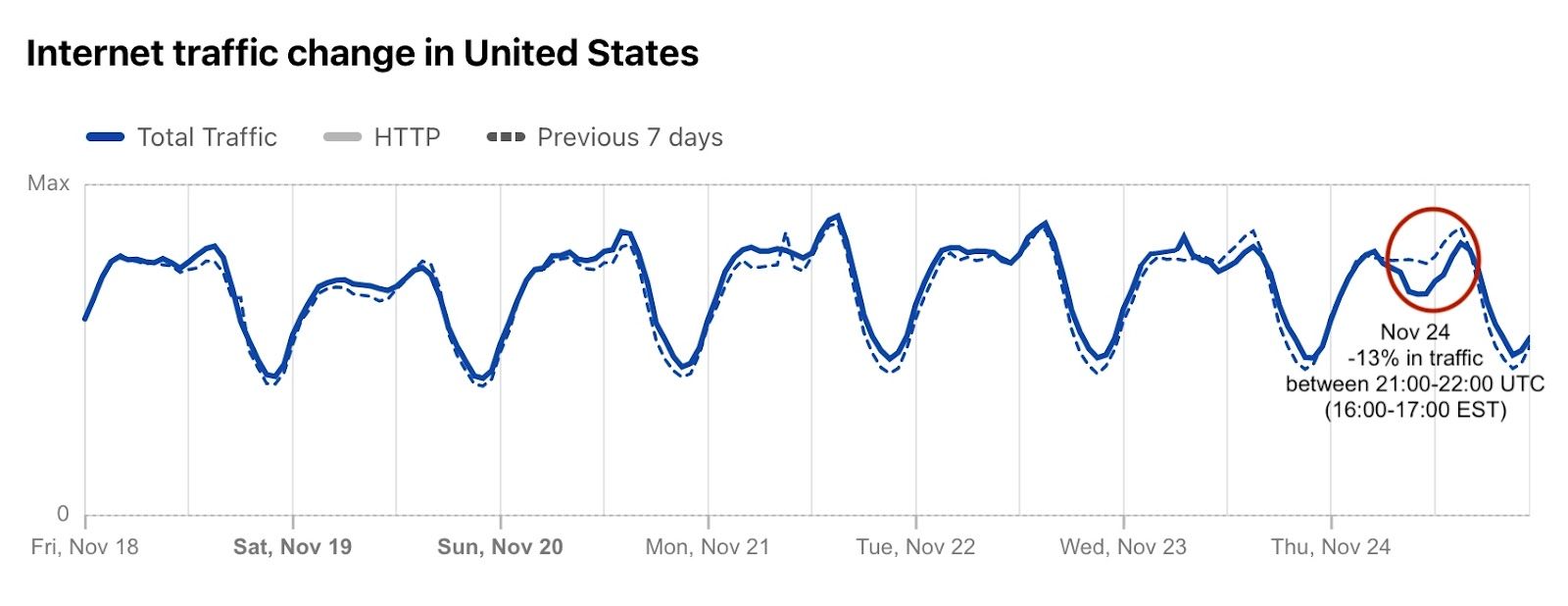
The turkey. The sweet potatoes. The stuffing. The pumpkin pie. Yesterday, November 24, 2022, was Thanksgiving Day in the US. A time for families and loved ones to be together and thankful, according to the tradition. Last year, we saw how the US paused shopping (and browsing) for Thanksgiving. So, how was it this year? Not only did we see Internet traffic go down (by 13%) during Thanksgiving dinner, but it was much higher than usual the day before and the day after (the Black Friday effect… so far). There was also a clear, but short, Thanksgiving day effect on e-commerce DNS trends.
We'll have to wait to see what Black Friday looks like.
Let’s start with Internet traffic at the time of Thanksgiving dinner. Although every family is different, a 2018 survey of US consumers showed that for 42% early afternoon (between 13:00 and 15:00 is the preferred time to sit at the table and start to dig in). But 16:00 seems to be the “correct time” — The Atlantic explains why.
That said, Cloudflare Continue reading