Video: Bridging Beyond Spanning Tree
In this week’s update of the Data Center Infrastructure for Networking Engineers webinar, we talked about VLANs, VRFs, and modern data center fabrics.
Those videos are available with Standard or Expert ipSpace.net Subscription; if you’re still sitting on the fence, you might want to watch the how networks really work version of the same topic that’s available with Free Subscription – it describes the principles-of-operation of bridging fabrics that don’t use STP (TRILL, SPBM, VXLAN, EVPN)
Why the SMB Market Will Determine the Future of SASE
SASE enables a corporate network to be deployed over the internet, which is a route many SMBs take because it's a scalable solution that doesn't require specialized hardware.Kubernetes Unpacked 011: Containers Past, Present And Future
On today's Kubernetes Unpacked podcast, Michael catches up with Eric Wright to discuss the current and future of containers and Kubernetes, as well as a look into how the world of containers has evolved. They dive into virtualization, how orchestration actually works, and how to think about ephemeral workloads.
The post Kubernetes Unpacked 011: Containers Past, Present And Future appeared first on Packet Pushers.
Kubernetes Unpacked 011: Containers Past, Present And Future
On today's Kubernetes Unpacked podcast, Michael catches up with Eric Wright to discuss the current and future of containers and Kubernetes, as well as a look into how the world of containers has evolved. They dive into virtualization, how orchestration actually works, and how to think about ephemeral workloads.Financial Firms: It’s Time to Get Serious About Network Automation
A return to the office following COVID-19 has fueled massive bandwidth and cloud connectivity challenges that are driving significant change in how we build networks.Cute Best Friend Halloween Costume Ideas
Best friends are the family that we get to choose. We share secrets, inside jokes, and a bond that is unbreakable. So it only makes sense that we want to dress up with our BFFs come Halloween!
Dressing up as each other is the perfect way to show off your BFF bond! You can either go for a traditional look by twinning your outfits, or get creative and put your own spin on it.
If you need some inspiration for your costume this year, check out our list of the best friend Halloween costumes below.
PowerPuff Girls
The PowerPuff Girls are the perfect example of best friends who also happen to be sisters. If you and your BFF are looking for a cute costume idea, consider dressing up as Blossom, Bubbles, and Buttercup! You can even add a little bit of flair by carrying around a stuffed animal or wearing temporary tattoos.
2 Broke Girls
If you and your bestie are fans of the TV show 2 Broke Girls, then this costume idea is for you! Dress up as the titular characters, Max and Caroline. They may not have much money, but they sure do have a lot of Continue reading
EVPN VLAN-Aware Bundle Service
In the EVPN/MPLS Bridging Forwarding Model blog post I mentioned numerous services defined in RFC 7432. That blog post focused on VLAN-Based Service Interface that mirrors the Carrier Ethernet VLAN mode.
RFC 7432 defines two other VLAN services that can be used to implement Carrier Ethernet services:
- Port-based service – whatever is received on the ingress port is sent to the egress port(s)
- VLAN bundle service – multiple VLANs sharing the same bridging table, effectively emulating single outer VLAN in Q-in-Q bridging.
And then there’s the VLAN-Aware Bundle Service, where a bunch of VLANs share the same MPLS pseudowires while having separate bridging tables.
EVPN VLAN-Aware Bundle Service
In the EVPN/MPLS Bridging Forwarding Model blog post I mentioned numerous services defined in RFC 7432. That blog post focused on VLAN-Based Service Interface that mirrors the Carrier Ethernet VLAN mode.
RFC 7432 defines two other VLAN services that can be used to implement Carrier Ethernet services:
- Port-based service – whatever is received on the ingress port is sent to the egress port(s)
- VLAN bundle service – multiple VLANs sharing the same bridging table, effectively emulating single outer VLAN in Q-in-Q bridging.
And then there’s the VLAN-Aware Bundle Service, where a bunch of VLANs share the same MPLS pseudowires while having separate bridging tables.
SASE: The Final Destination; A SASE Conversation with Craig Connors of VMware
A conversation about what's driving Secure Access Service Edge (SASE), its benefits, and how best to eliminate confusion in the market.Hedge 150: Micah Beck and Universal Broadband
What would the Internet look like—or what kinds of services would need to be developed and deployed—to make boradband class service available to every user? What could this kind of development do to drive entire societies forward? Micah Beck, from the University of Tennessee, joins Tom Ammon and Russ White to discuss universal broadband on this episode of the Hedge.
Day Two Cloud 167: Interviewing At A Huge Tech Company
On today's Day Two Cloud we talk about what it's like to interview for a job at a massive tech company. How do you get yourself in line? What can you expect from the interview? How do you prepare? How do you overcome your own imposter syndrome? Our guest is Nathaniel Avery, Outbound Product Manager at Google Cloud. He recently ran the gauntlet of the tech interview, and is here to share tips and insights on the process.
The post Day Two Cloud 167: Interviewing At A Huge Tech Company appeared first on Packet Pushers.
Day Two Cloud 167: Interviewing At A Huge Tech Company
On today's Day Two Cloud we talk about what it's like to interview for a job at a massive tech company. How do you get yourself in line? What can you expect from the interview? How do you prepare? How do you overcome your own imposter syndrome? Our guest is Nathaniel Avery, Outbound Product Manager at Google Cloud. He recently ran the gauntlet of the tech interview, and is here to share tips and insights on the process.Tier 1 Carriers Performance Report: September, 2022
The post Tier 1 Carriers Performance Report: September, 2022 appeared first on Noction.
Cloudflare DDoS threat report 2022 Q3

This post is also available in Français, Español, Português, 한국어, 简体中文, 繁體中文, and 日本語.

Welcome to our DDoS Threat Report for the third quarter of 2022. This report includes insights and trends about the DDoS threat landscape - as observed across Cloudflare’s global network.
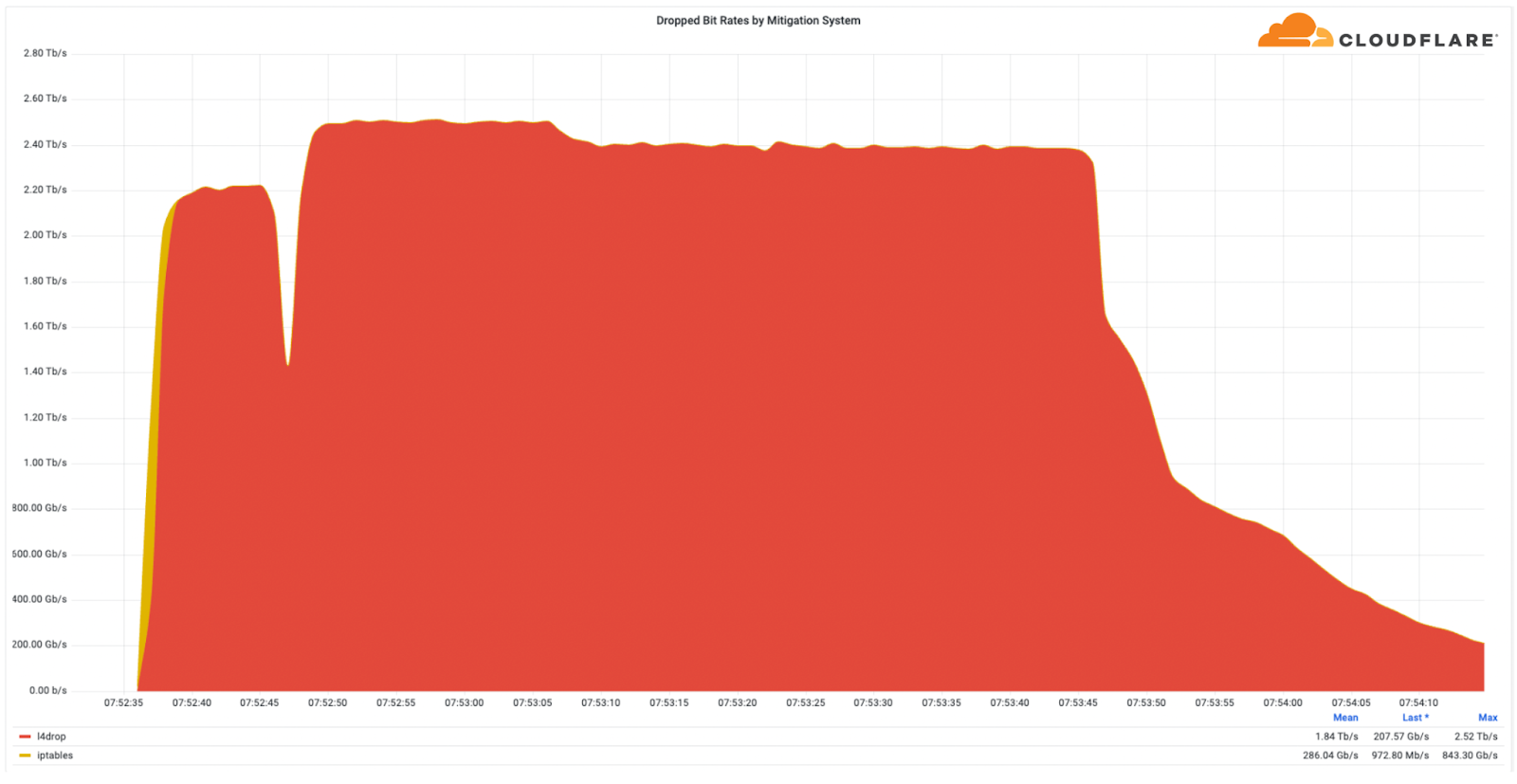
Multi-terabit strong DDoS attacks have become increasingly frequent. In Q3, Cloudflare automatically detected and mitigated multiple attacks that exceeded 1 Tbps. The largest attack was a 2.5 Tbps DDoS attack launched by a Mirai botnet variant, aimed at the Minecraft server, Wynncraft. This is the largest attack we’ve ever seen from the bitrate perspective.
It was a multi-vector attack consisting of UDP and TCP floods. However, Wynncraft, a massively multiplayer online role-playing game Minecraft server where hundreds and thousands of users can play on the same server, didn’t even notice the attack, since Cloudflare filtered it out for them.
General DDoS attack trends
Overall this quarter, we've seen:
- An increase in DDoS attacks compared to last year.
- Longer-lasting volumetric attacks, a spike in attacks generated by the Mirai botnet and its variants.
- Surges in attacks targeting Continue reading