Juniper CN2 DPDK vRouter Bringup
How to bring Juniper Cloud Native CN2 DPDK vRouter
https://github.com/kashif-nawaz/Juniper-CN2-DPDK-vRouter-Bringup
Hedge: October Update
What’s going on with the Hedge? What am I teaching this coming month? Listen to this short update to find out all the news.
Worth Reading: VXLAN Drops Large Packets
Ian Nightingale published an interesting story of connectivity problems he had in a VXLAN-based campus network. TL&DR: it’s always the MTU (unless it’s DNS or BGP).
The really fun part: even though large L2 segments might have magical properties (according to vendor fluff), there’s no host-to-network communication in transparent bridging, so there’s absolutely no way that the ingress VTEP could tell the host that the packet is too big. In a layer-3 network you have at least a fighting chance…
For more details, watch the Switching, Routing and Bridging part of How Networks Really Work webinar (most of it available with Free Subscription).
Worth Reading: VXLAN Drops Large Packets
Ian Nightingale published an interesting story of connectivity problems he had in a VXLAN-based campus network. TL&DR: it’s always the MTU (unless it’s DNS or BGP).
The really fun part: even though large L2 segments might have magical properties (according to vendor fluff), there’s no host-to-network communication in transparent bridging, so there’s absolutely no way that the ingress VTEP could tell the host that the packet is too big. In a layer-3 network you have at least a fighting chance…
For more details, watch the Switching, Routing and Bridging part of How Networks Really Work webinar (most of it available with Free Subscription).
Heavy Networking 650: Whether And How To Adopt Whitebox Switches
On today’s Heavy Networking podcast, Kevin Myers joins us for a whitebox conversation. Kevin helps Internet Service Providers build their networks, and has noticed increased adoption of whitebox switches. Why? Are the problems whitebox solves for these ISPs the same you might have at your company? Should you consider whitebox instead of Cisco, Juniper, or Arista? Maybe…and maybe not.
The post Heavy Networking 650: Whether And How To Adopt Whitebox Switches appeared first on Packet Pushers.
Heavy Networking 650: Whether And How To Adopt Whitebox Switches
On today’s Heavy Networking podcast, Kevin Myers joins us for a whitebox conversation. Kevin helps Internet Service Providers build their networks, and has noticed increased adoption of whitebox switches. Why? Are the problems whitebox solves for these ISPs the same you might have at your company? Should you consider whitebox instead of Cisco, Juniper, or Arista? Maybe…and maybe not.How to Tell the Difference Between IT Fads and Trends
Before committing your organization to an emerging technology or methodology, you should first determine its staying power.Cloudflare Pages gets even faster with Early Hints
Last year, we demonstrated what we meant by “lightning fast”, showing Pages' first-class performance in all parts of the world, and today, we’re thrilled to announce an integration that takes this commitment to speed even further – introducing Pages support for Early Hints! Early Hints allow you to unblock the loading of page critical resources, ahead of any slow-to-deliver HTML pages. Early Hints can be used to improve the loading experience for your visitors by significantly reducing key performance metrics such as the largest contentful paint (LCP).
What is Early Hints?
Early Hints is a new feature of the Internet which is supported in Chrome since version 103, and that Cloudflare made generally available for websites using our network. Early Hints supersedes Server Push as a mechanism to "hint" to a browser about critical resources on your page (e.g. fonts, CSS, and above-the-fold images). The browser can immediately start loading these resources before waiting for a full HTML response. This uses time that was otherwise previously wasted! Before Early Hints, no work could be started until the browser received the first byte of the response. Now, the browser can fill this time usefully when it was previously sat Continue reading
Video: Traffic Filtering in the Age of IPv6
Christopher Werny covered another interesting IPv6 security topic in the hands-on part of IPv6 security webinar: traffic filtering in the age of dual-stack and IPv6-only networks, including filtering extension headers, filters on Internet uplinks, ICMPv6 filters, and address space filters.
Video: Traffic Filtering in the Age of IPv6
Christopher Werny covered another interesting IPv6 security topic in the hands-on part of IPv6 security webinar: traffic filtering in the age of dual-stack and IPv6-only networks, including filtering extension headers, filters on Internet uplinks, ICMPv6 filters, and address space filters.
Parsing Text using TTP
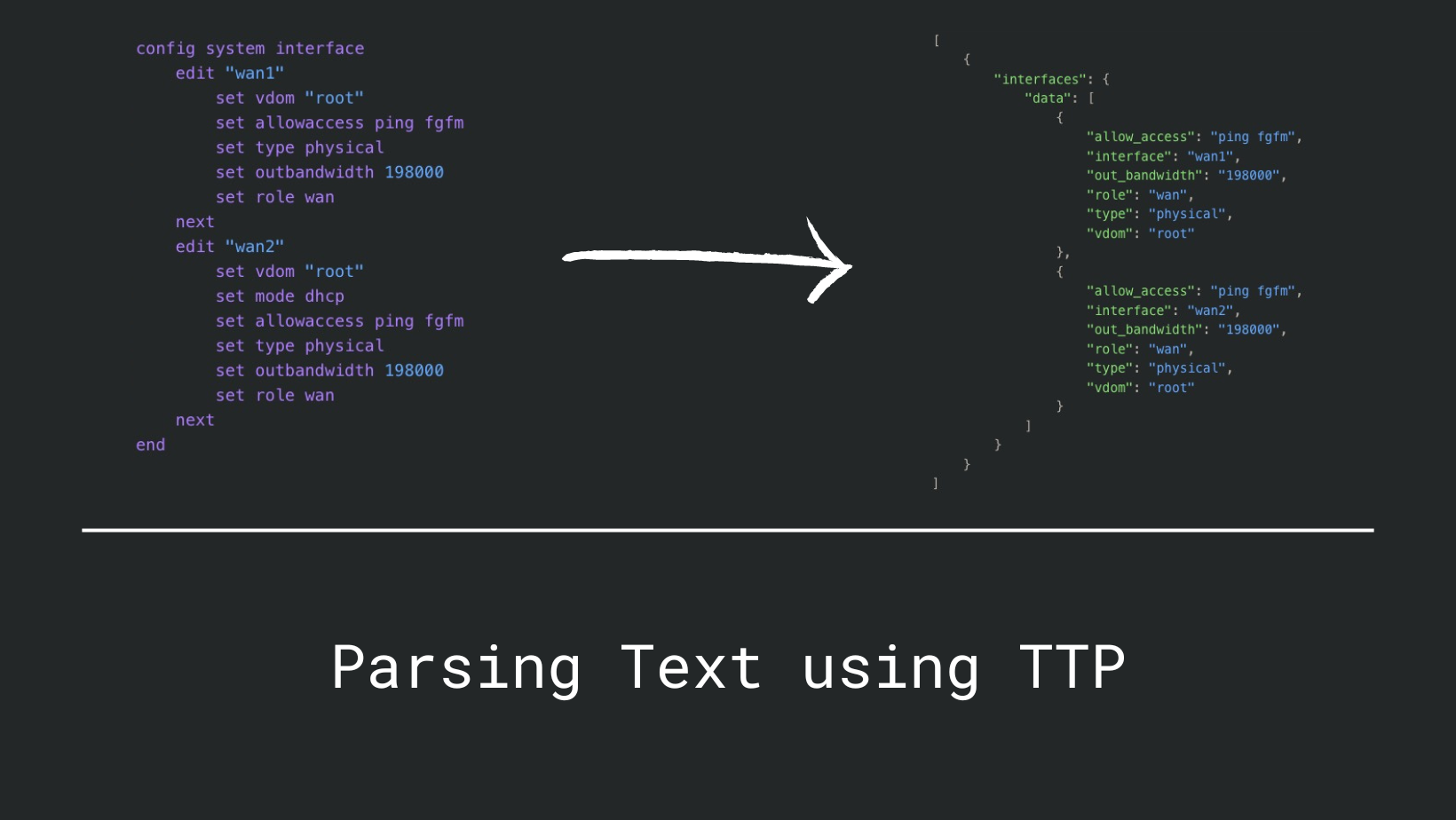
Before we dive into TTP (Template Text Parser), let us first address why we need a text scraping tool in the modern world of APIs and structured data. Here is my opinion:
- Many organisations still use legacy devices that do not have APIs or structured data formats embedded in their CLI.
- Network devices are still evolving and not all devices have APIs that are easy to work with.
- There is more information in the output of a command than what is available through the API.
- Network Engineers are used to working with CLI and screen scraping is a natural extension of this workflow.
- Sometimes you just need to get some data quickly and writing a full-fledged API client is not worth the effort.
You would be surprised to know that many commercial tools that do network observability use screen scraping under the hood. So, it is not a bad idea to learn how to do it yourself.
What are our options?
From a network engineer's perspective, there are two popular tools that can be used for screen scraping:
- TextFSM - TextFSM is a mature tool that has been around for a long time with huge community support and a large Continue reading
Walking the Policy Tightrope
In policy work nothing is ever truly simply black and white. The means to achieve one outcome may well act to impair the work to achieve different outcomes, and the resultant effort often requires some difficult decisions to balance what appears to be some fundamental tensions between various policy objectives. Even a topic like online safety, which should be very straightforward, has some challenges.Total TLS: one-click TLS for every hostname you have
Today, we’re excited to announce Total TLS — a one-click feature that will issue individual TLS certificates for every subdomain in our customer’s domains.
By default, all Cloudflare customers get a free, TLS certificate that covers the apex and wildcard (example.com, *.example.com) of their domain. Now, with Total TLS, customers can get additional coverage for all of their subdomains with just one-click! Once enabled, customers will no longer have to worry about insecure connection errors to subdomains not covered by their default TLS certificate because Total TLS will keep all the traffic bound to the subdomains encrypted.
A primer on Cloudflare’s TLS certificate offerings
Universal SSL — the “easy” option
In 2014, we announced Universal SSL — a free TLS certificate for every Cloudflare customer. Universal SSL was built to be a simple “one-size-fits-all” solution. For customers that use Cloudflare as their authoritative DNS provider, this certificate covers the apex and a wildcard e.g. example.com and *.example.com. While a Universal SSL certificate provides sufficient coverage for most, some customers have deeper subdomains like a.b.example.com for which they’d like TLS coverage. For those customers, we built Advanced Certificate Manager — a Continue reading