netsim-tools: Combining VLANs with VRFs
Last two weeks we focused on access VLANs and VLAN trunk implementation in netsim-tools. Can we combine them with VRFs? Of course.
The trick is very simple: attributes within a VLAN definition become attributes of VLAN interfaces. Add vrf attribute to a VLAN and you get all VLAN interfaces created for that VLAN in the corresponding VRF. Can’t get any easier, can it?
How about extending our VLAN trunk lab topology with VRFs? We’ll put red VLAN in red VRF and blue VLAN in blue VRF.
netlab: Combining VLANs with VRFs
Last two weeks we focused on access VLANs and VLAN trunk netlab implementation. Can we combine them with VRFs? Of course.
The trick is very simple: attributes within a VLAN definition become attributes of VLAN interfaces. Add vrf attribute to a VLAN and you get all VLAN interfaces created for that VLAN in the corresponding VRF. Can’t get any easier, can it?
How about extending our VLAN trunk lab topology with VRFs? We’ll put red VLAN in red VRF and blue VLAN in blue VRF.
Cloudflare is redefining employee well-being in Japan

This post is also available in 日本語

“You can accomplish anything if you do it. Nothing will be accomplished unless you do it. If nothing is not accomplished, that’s because no one did it.“
— Yozan Uesugi
Long hours and hard work. If you ask anyone in Japan what our work culture is like, chances are, these are the words that will come to mind. Different countries have their own cultures and also specific work habits and ways of having a work-life balance. The pandemic brought everyone (companies and their people) a new reality, new lessons, and new habits. Here at Cloudflare, our thinking around where and how we do our best work has evolved over the course of the pandemic. We care about addressing the diverse needs of our workforce and our policies and benefits are designed to optimize for their flexibility and needs. To that end, Cloudflare Japan is making a few important changes to our employee benefits:
- “take what you need” time off for all our employees
- 16-week gender-neutral paid parental leave
- flexible working hours
First, let’s try to understand a bit of the Japanese work culture. According to Japan’s labor laws, Japanese employed workers are Continue reading
BGP communities part 3: Customer BGP Traffic Engineering communities
If you’ve ever been asked to prioritize one internet connection over another for any variety of reasons, cost, latency, SLA, etc… this is for you.
Often I hear the same tactics to solve this problem:
- AS-PATH prepending
- conditional advertisements
- scripting
- some other manual process
However, most carriers offer customer BGP TE communities that you can use to influence traffic within their AS, with one notable exception Hurricane Electric. If you’re not sure what a BGP community take a quick look at this post on them first.
Lets explore how to utilize these, where to find them, and how they might give more deterministic path selection than the options laid out above.
BGP Topology
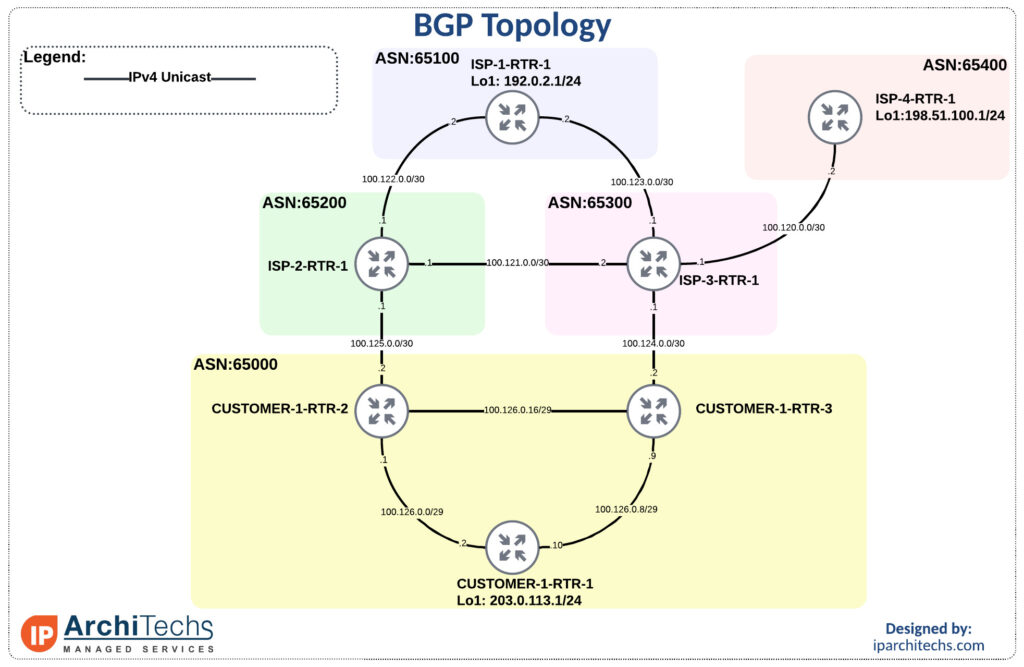
Default behavior with no modification
First to get familiar with the topology and show reachability we’ll leave all settings as “defaults” with no modifications.
ISP-1-RTR-1#traceroute 203.0.113.1 source 192.0.2.1
Type escape sequence to abort.
Tracing the route to 203.0.113.1
VRF info: (vrf in name/id, vrf out name/id)
1 100.123.0.1 1 msec 1 msec 1 msec
2 100.124.0.2 1 msec 0 msec 0 msec
3 100.126.0.10 2 msec * 1 Continue readingUsing OpenSSL with Ed Harmoush 3/6 Troubleshooting: Matching Keys To Certificates – Video
ED, HIS TLS COURSE, AND THE FREE OPENSSL CHEATSHEET Twitter @ed_pracnet https://practicalnetworking.net Practical TLS course: https://pracnet.net/tls OpenSSL Cheatsheet: https://pracnet.net/openssl FILES FOR THE CERT/KEY MATCHING EXERCISE: ZIP VERSION: packetpushers-pracnet-openssl.zip https://ln5.sync.com/dl/1f1f63d90/kqztwkp9-hkcz3yvq-tuzx79ke-aewxgaip TAR.GZ VERSION: packetpushers-pracnet-openssl.tar.gz https://ln5.sync.com/dl/0791b8d50/q973jpyb-qrmz3cpd-xeiar9zn-qu99gi5w FOR MORE INFO Hashing, Hashing Algorithms, and Collisions – Cryptography Symmetric Encryption vs Asymmetric Encryption Public & Private Keys – Signatures & […]
The post Using OpenSSL with Ed Harmoush 3/6 Troubleshooting: Matching Keys To Certificates – Video appeared first on Packet Pushers.
Segment Routing with MPLS (SR-MPLS)
In this lab we explore Segment Routing (SR) using Multiprotocol Label Switching as an encoding mechanism. Segment Routing, also known as “Source Packet Routing in Networking” (SPRING), is a method of routing in which ingress routers prepend instructions to traffic that cause actions to be performed by transit nodes as it travels across a network. This is sometimes as simple as a list of routers a packet must traverse to reach its destination.Heavy Networking 634: Why (Not) MikroTik?
Today's Heavy Networking gets into networking hardware from MikroTik, a vendor you may not have heard of. Our guest is Kevin Myers, a senior network architect and consultant who uses MikroTik with a variety of clients big and small. We'll find out what MikroTik is good for, and not good for, management and support, and more. This is a non-sponsored episode.
The post Heavy Networking 634: Why (Not) MikroTik? appeared first on Packet Pushers.
Heavy Networking 634: Why (Not) MikroTik?
Today's Heavy Networking gets into networking hardware from MikroTik, a vendor you may not have heard of. Our guest is Kevin Myers, a senior network architect and consultant who uses MikroTik with a variety of clients big and small. We'll find out what MikroTik is good for, and not good for, management and support, and more. This is a non-sponsored episode.How to Retain Talent in Uncertain Circumstances
Recruiters may be calling your top talent right now. Here's what you can do to make your employees more likely to let those calls go to voice mail.Using OpenSSL with Ed Harmoush 2/6 Generating Certificates – Video
ED, HIS TLS COURSE, AND THE FREE OPENSSL CHEATSHEET Twitter @ed_pracnet https://practicalnetworking.net Practical TLS course: https://pracnet.net/tls OpenSSL Cheatsheet: https://pracnet.net/openssl FILES FOR THE CERT/KEY MATCHING EXERCISE: ZIP VERSION: packetpushers-pracnet-openssl.zip https://ln5.sync.com/dl/1f1f63d90/kqztwkp9-hkcz3yvq-tuzx79ke-aewxgaip TAR.GZ VERSION: packetpushers-pracnet-openssl.tar.gz https://ln5.sync.com/dl/0791b8d50/q973jpyb-qrmz3cpd-xeiar9zn-qu99gi5w FOR MORE INFO Hashing, Hashing Algorithms, and Collisions – Cryptography Symmetric Encryption vs Asymmetric Encryption Public & Private Keys – Signatures & […]
The post Using OpenSSL with Ed Harmoush 2/6 Generating Certificates – Video appeared first on Packet Pushers.
Friday Thoughts Pre-Cisco Live

It’s weird to think that I’m headed out to Cisco Live for the first time since 2019. The in-person parts of Cisco Live have been sorely missed during the pandemic. I know it was necessary all around but I didn’t realize how much I enjoyed being around others and learning from the community until I wasn’t able to do it for an extended period of time.
Now we’re back in Las Vegas and ready to take part in something that has been missed. I’ve got a busy lineup of meetings with the CCIE Advisory Council and Tech Field Day Extra but that doesn’t mean I’m not going to try and have a little fun along the way. And yes, before you ask, I’m going to get the airbrush tattoo again if they brought the artist back. It’s a tradition as old as my CCIE at this point.
What else am I interested in?
- I’m curious to see how Cisco responds to their last disappointing quarter. Are they going to tell us that it was supply chain? Are they going to double down on the software transition? And how much of the purchasing that happened was pull through? Does that mean Continue reading
AAE-1 & SMW5 cable cuts impact millions of users across multiple countries


Just after 1200 UTC on Tuesday, June 7, the Africa-Asia-Europe-1 (AAE-1) and SEA-ME-WE-5 (SMW-5) submarine cables suffered cable cuts. The damage reportedly occurred in Egypt, and impacted Internet connectivity for millions of Internet users across multiple countries in the Middle East and Africa, as well as thousands of miles away in Asia. In addition, Google Cloud Platform and OVHcloud reported connectivity issues due to these cable cuts.
The impact
Data from Cloudflare Radar showed significant drops in traffic across the impacted countries as the cable damage occurred, recovering approximately four hours later as the cables were repaired.
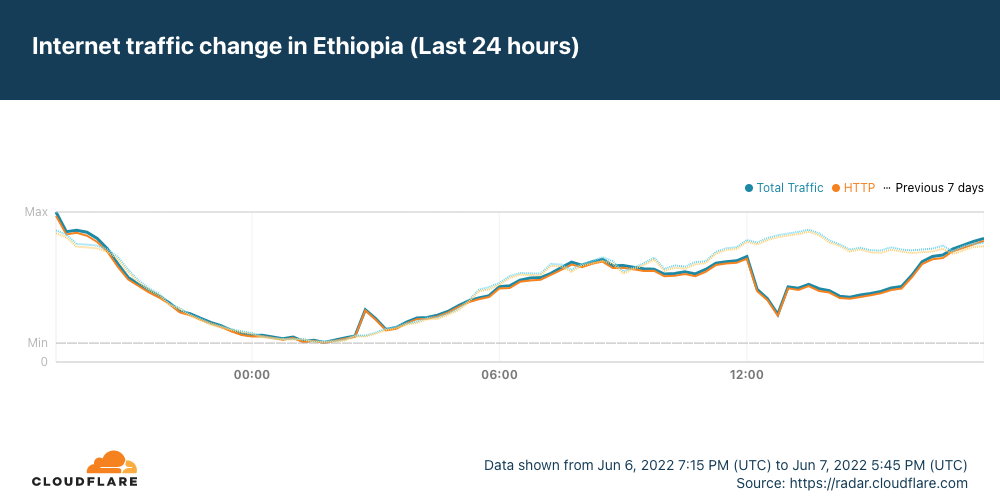
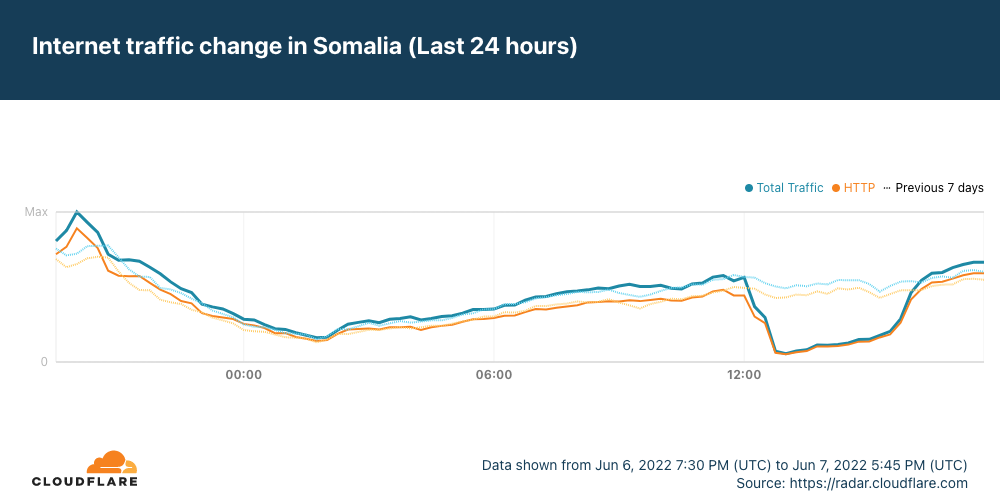
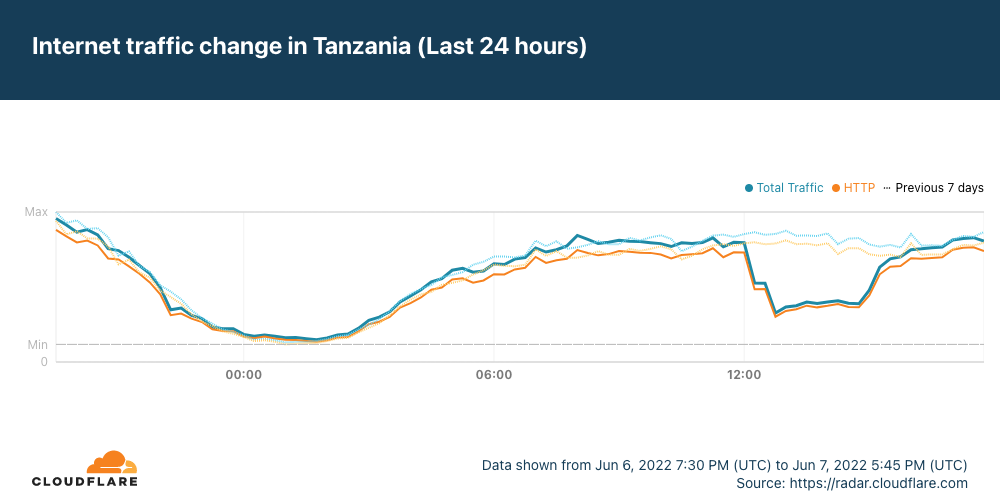
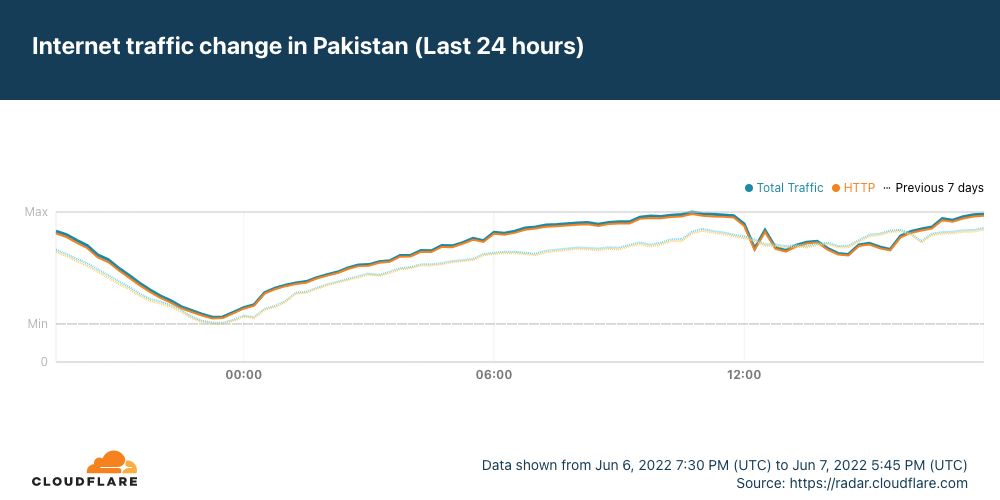
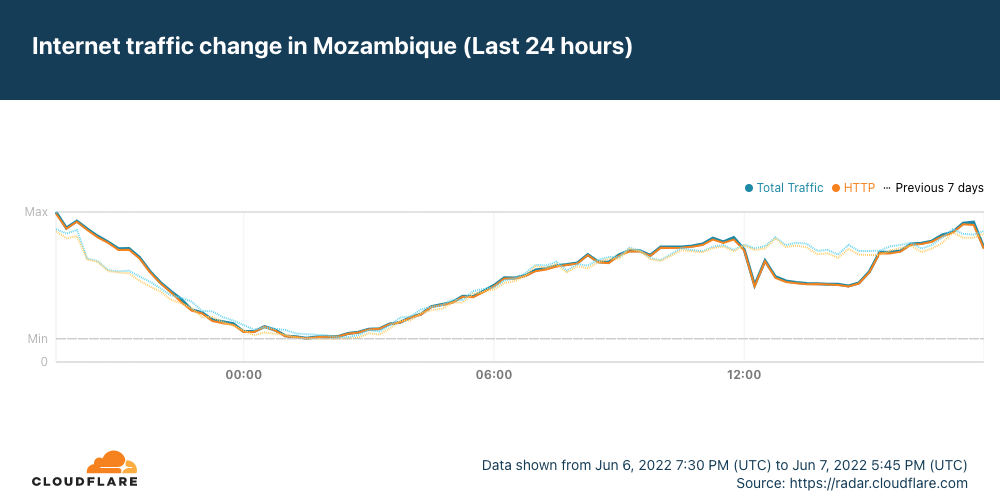
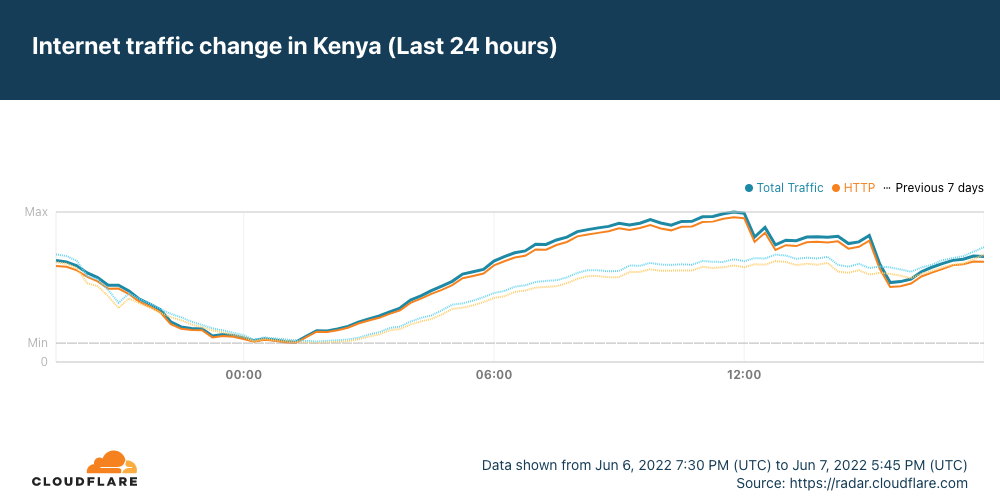
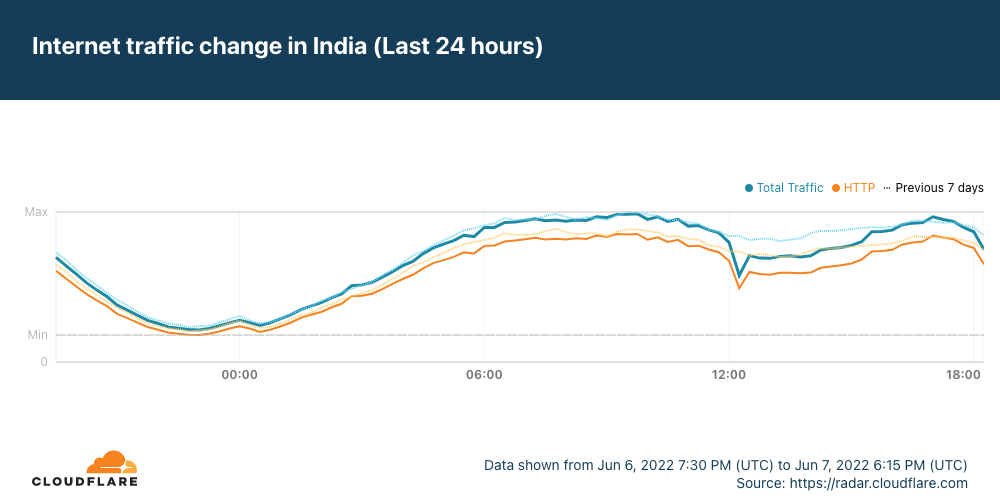
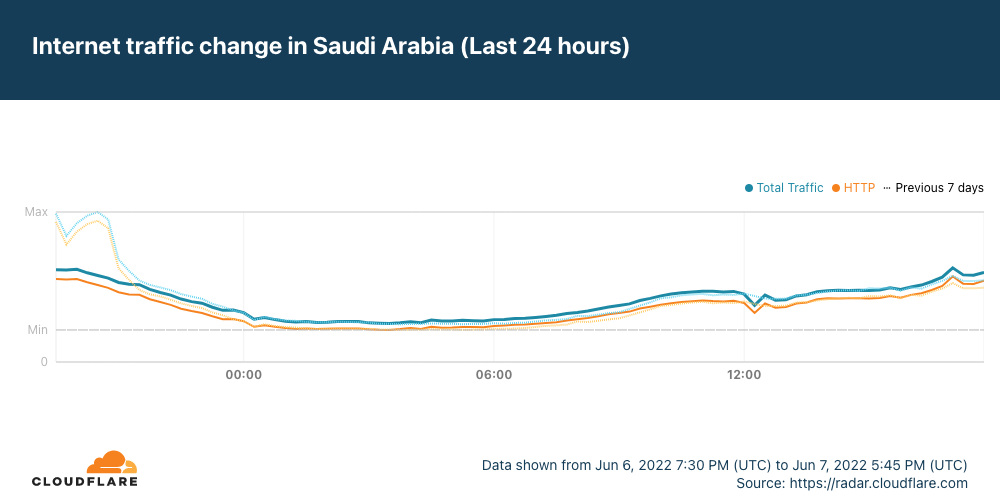
It appears that Saudi Arabia may have also been affected by the cable cut(s), but the impact was much less significant, and traffic recovered almost immediately.
In the graphs above, we show that Ethiopia was one of the impacted countries. However, as it is landlocked, there are obviously no submarine cable landing points within the country. The Afterfibre map from the Network Startup Resource Center (NSRC) shows that that fiber in Ethiopia connects to fiber in Somalia, which experienced an impact. In addition, Ethio Telecom also routes traffic through network providers in Kenya and Djibouti. Djibouti Telecom, one of these providers, in turn Continue reading
Video: Rogue IPv6 RA Challenges
IPv6 security-focused presentations were usually an awesome opportunity to lean back and enjoy another round of whack-a-mole, often starting with an attacker using IPv6 Router Advertisements to divert traffic (see also: getting bored at Brussels airport) .
Rogue IPv6 RA challenges and the corresponding countermeasures are thus a mandatory part of any IPv6 security training, and Christopher Werny did a great job describing them in IPv6 security webinar.
Video: Rogue IPv6 RA Challenges
IPv6 security-focused presentations were usually an awesome opportunity to lean back and enjoy another round of whack-a-mole, often starting with an attacker using IPv6 Router Advertisements to divert traffic (see also: getting bored at Brussels airport) .
Rogue IPv6 RA challenges and the corresponding countermeasures are thus a mandatory part of any IPv6 security training, and Christopher Werny did a great job describing them in IPv6 security webinar.
Key advantages of the Calico eBPF data plane
Project Calico and eBPF
Project Calico has offered a production-ready data plane based on eBPF since September 2020, and it’s been available for technical evaluation for even longer (since February 2020).


The pre-requisites and limitations are simple to review, it’s easy to enable, and it’s easy to validate your configuration. So, there’s never been a better time to start experiencing the benefits!
You do know what those are, don’t you? Don’t worry if not! That’s what this blog post is about. We’ve reached a point where the journey is easy to make, if you know why you want to get there.
Key advantages of using Calico with eBPF
Calico is already the most widely deployed Kubernetes network security solution. What can eBPF do to help our winning formula further? I’ll dive into the details, but let’s look at the highest possible level first.
These three key benefits apply across all supported environments:
- General performance
- Native Kubernetes service handling
- Source IP preservation and Direct Server Return, or DSR
- Each of these benefits is significant and worth discussing in more detail.
Performance
Calico’s eBPF data plane achieves high performance in several ways. Firstly, it achieves higher throughput and/or less CPU Continue reading