IPv6 Buzz 099: Why You Need An IPv6 Proof Of Concept Lab
In this episode of IPv6 Buzz we talk about what a Proof of Concept (PoC) lab is and why you probably need one as part of your IPv6 initiative. We discuss technical challenges and considerations, how much of your production network you need to model, learning opportunities that come with a lab, and more.Legal and Ethical Aspects of Privacy
My second post on privacy for network engineers is up over at Packet Pushers—
Meet The New WPA3 Wi-Fi Security Suite
WPA3, the latest Wi-Fi security suite, is finally making its way into products around the world. Here’s what you need to know for using it at home and in enterprise networks. What Is WPA? Wi-Fi Protected Access (WPA) is the suite of standards that define security for both WPA-Personal (passphrase) and WPA-Enterprise (802.1X) based wireless […]
The post Meet The New WPA3 Wi-Fi Security Suite appeared first on Packet Pushers.
netsim-tools Release 1.2.1: More MPLS and VRFs, Dell OS10, Cumulus 5.0 on Containerlab
I already mentioned the netsim-tools Easter Egg, here are the other cool features shipping in release 1.2.1:
- Dell OS10 on libvirt (including BGP, OSPFv2, OSPFv3 and VRF Lite) by Stefano Sasso
- VRFs, MPLS, and MPLS/VPN support on Mikrotik RouterOS and VyOS by Stefano Sasso
- Containerlab support for Cumulus 5.0 with NVUE including Simple VRF-Lite by Julien Dhaille
To upgrade netsim-tools, use pip3 install --upgrade netsim-tools; if you’re starting from scratch, read the installation instructions.
New in netlab: More MPLS and VRFs, Dell OS10, Cumulus 5.0 on Containerlab
I already mentioned the netsim-tools Easter Egg, here are the other cool features shipping in release 1.2.1:
- Dell OS10 on libvirt (including BGP, OSPFv2, OSPFv3 and VRF Lite) by Stefano Sasso
- VRFs, MPLS, and MPLS/VPN support on Mikrotik RouterOS and VyOS by Stefano Sasso
- Containerlab support for Cumulus 5.0 with NVUE including Simple VRF-Lite by Julien Dhaille
EVPN-VXLAN Explainer 1 – Static VXLAN
In this series of blog posts I'm going to break down how to configure Aruba AOS-CX switches for VXLAN and EVPN, plus explain how to read the EVPN table and various 'show' commands.
In this first post I will look at VXLAN, its configuration and operation.
A note about EVPN-VXLAN
VXLAN: encapsulation type of 8 bytes, works at the data plane, concerned with the forwarding of packets.
Ethernet VPN (EVPN): Extension to BGP, works that the control plane, concerned with learning and advertising MAC/IP addresses.
Static VXLAN - Start Here
VXLAN configuration is one of the basic building blocks of a EVPN-VXLAN network, it is worth familiarising yourself with static VXLAN configuration, even if you are never going to use it.
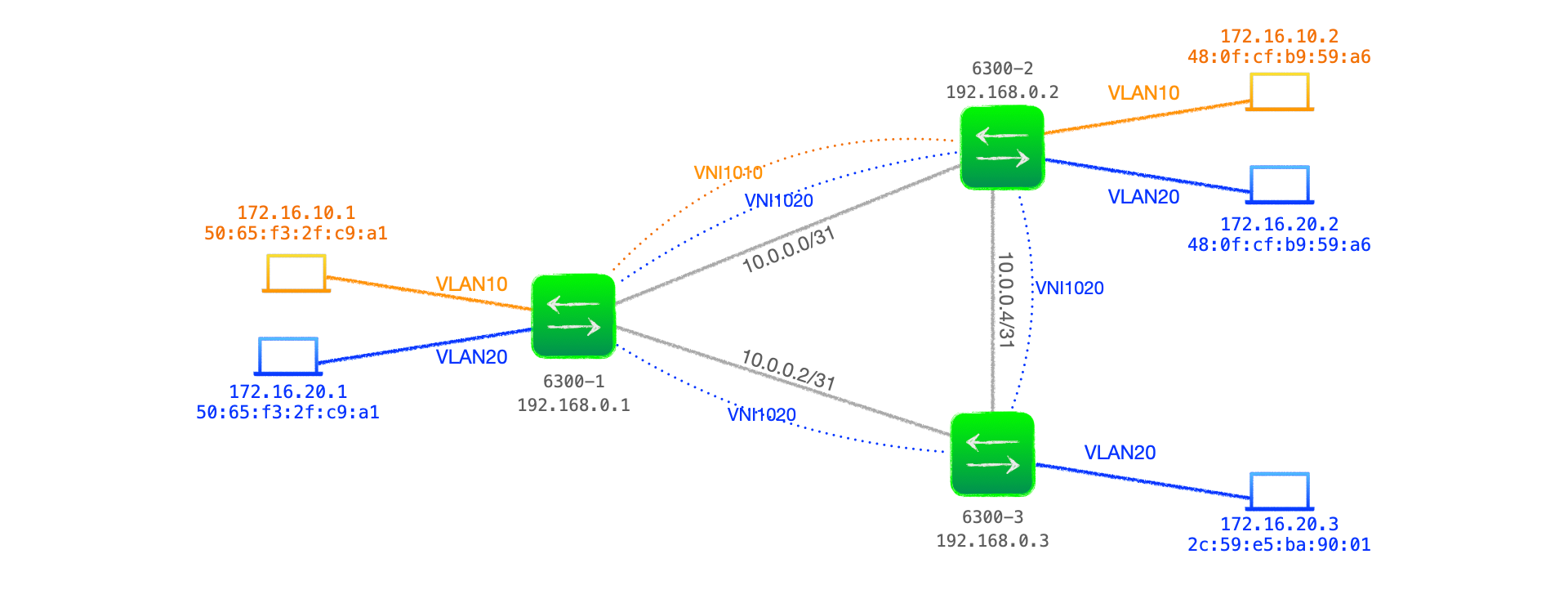
Example Network
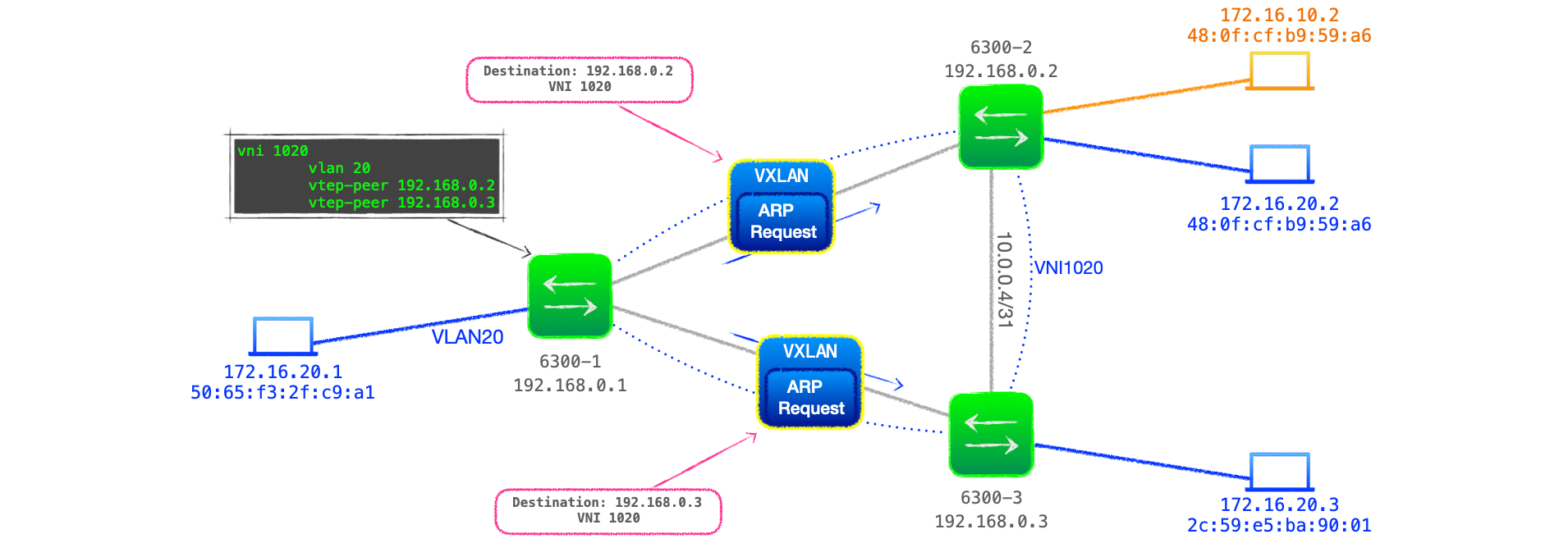
Figure 1 below shows a network comprised of three Aruba 6300 switches acting as VTEPs, with two customer VLANs, VLAN10 and VLAN 20, that are bound with VNI 1010 and VNI 1020 respectively across the VXLAN network.
VXLAN Configuration
Component parts of the configuration:
- Customer-side VLAN - carries the traffic to be encapsulated.
- An IP network between VTEPs (the underlay network)- there must be bi-directional connectivity between an IP address designated on the VTEP. Continue reading
Overcoming Technical Debt Requires Strategic Approach
Most companies are over-spending to meet cloud migration deadlines, and incurring technical debt in the process. What’s the impact of this down the line?Overcoming Technical Debt Requires Strategic Approach
Most companies are over-spending to meet cloud migration deadlines, and incurring technical debt in the process. What’s the impact of this down the line?Overcoming Technical Debt Requires Strategic Approach
Most companies are over-spending to meet cloud migration deadlines, and incurring technical debt in the process. What’s the impact of this down the line?Overcoming Technical Debt Requires Strategic Approach
Most companies are over-spending to meet cloud migration deadlines, and incurring technical debt in the process. What’s the impact of this down the line?Day Two Cloud 143: Application Security Isn’t Just For Developers
Today's Day Two Cloud gets into application security and working with developers to make sure code is sanitized and tested. Writing secure code at the outset can dramatically reduce risk and help simplify operations and security. Our guest is Tanya Janca, founder of We Hack Purple. We Hack Purple offers free training courses for people who want to get into security.How Small or Big is Off-Premises/Public Cloud, According to Gartner
 Is this number small or big ? I don't know
Is this number small or big ? I don't know
Why Asking for Help is Not a Sign of Weakness
Asking for help can be difficult. It can be hard to admit that we need assistance, and sometimes pride gets in the way of our better judgment. We may worry that asking for help will make us seem weak or incompetent. However, this could not be further from the truth. Asking for help is actually a sign of strength. It shows that we are willing to admit when we need assistance and that we are not afraid to ask for support.
Why is it hard to ask for help?
There can be many reasons why it is hard to ask for help. We may worry that we will seem weak or incompetent. We may also feel like we need to be able to handle everything on our own. However, it is important to remember that asking for help is not a sign of weakness. It takes a lot of strength and courage to reach out for assistance, and there are many people who are willing to support us through whatever challenge we may be facing.
Situations where it’s perfectly acceptable – and even necessary – to ask for help
There is nothing wrong with asking for help. In fact, it Continue reading