Cloudflare named a Strong Performer in Email Security by Forrester
Today, we are excited to announce that Forrester has recognized Cloudflare Email Security as a Strong Performer and among the top three providers in the ‘current offering’ category in “The Forrester Wave™: Email, Messaging, And Collaboration Security Solutions, Q2 2025” report. Get a complimentary copy of the report here. According to Forrester:
“Cloudflare is a solid choice for organizations looking to augment current email, messaging, and collaboration security tooling with deep content analysis and processing and malware detection capabilities.”
In this evaluation, Forrester analyzed 10 Email Security vendors across 27 different criteria. Cloudflare received the highest scores possible in nine key evaluation criteria, and also scored among the top three in the current offering category. We believe this recognition is due to our ability to deliver stronger security outcomes across email and collaboration tools. These highlights showcase the strength and maturity of our Email Security solution:
Antimalware & sandboxing
Cloudflare’s advanced sandboxing engine analyzes files, whether directly attached or linked via cloud storage, using both static and dynamic analysis. Our AI-powered detectors evaluate attachment structure and behavior in real time, enabling protection not only against known malware but also emerging threats.
Malicious URL detection & web Continue reading
TNO031: Attracting New Talent to Networking, Pairing Dev With NetOps, and More With Justin Ryburn
Total Networks Operations sits down with Justin Ryburn for a wide-ranging discussion on the state of the networking industry. Topics including how to attract new talent to network engineering and network operations; getting literate in DevOps/infrastructure tools such as GitHub, Terraform, and Python; pairing Dev and NetOps to maximize domain expertise; integrating tools and trying... Read more »Multi-Layer Switching and Tunneling
When deep-diving into the confusing terminology of switching, routing, and bridging, I mentioned you could perform packet forwarding at different layers of a networking stack. In this blog post, we’ll explore what happens when we combine packet forwarding on multiple layers within a single network, resulting in multi-layer switching, where edge devices perform Layer n forwarding (usually Layer 3), and core devices perform Layer n-1 forwarding (typically Layer 2).
Each layer can use any forwarding paradigm you choose. However, since we generally use IP at Layer 3, edge devices typically perform hop-by-hop destination-based forwarding, while core devices can use alternative methods.
IPB176: How to Number Point-to-Point Links
Let’s chat about point-to-point links. On today’s episode we cover what should and shouldn’t be done, and discuss why following RFC’s doesn’t always get you to the right place. We dig into questions including: Don’t we just use link-local addresses for point-to-points? Shouldn’t we assign a /127, just like we do a /31 in IPv4?... Read more »Hedge 269: Web 3.0
Yes, we took an (unintentional) three-week break for medical reasons … but we’re back with a new episode.
What is Web 3.0, and how is it different from Web 2.0? What about XR, AI, and Quantum, and their relationship to Web 3.0? Jamie Schwartz joins Tom Ammon and Russ White to try to get to a solid definition of what Web 3.0 and how it impacts the future of the Internet.
Let’s DO this: detecting Workers Builds errors across 1 million Durable Objects
Cloudflare Workers Builds is our CI/CD product that makes it easy to build and deploy Workers applications every time code is pushed to GitHub or GitLab. What makes Workers Builds special is that projects can be built and deployed with minimal configuration. Just hook up your project and let us take care of the rest!
But what happens when things go wrong, such as failing to install tools or dependencies? What usually happens is that we don’t fix the problem until a customer contacts us about it, at which point many other customers have likely faced the same issue. This can be a frustrating experience for both us and our customers because of the lag time between issues occurring and us fixing them.
We want Workers Builds to be reliable, fast, and easy to use so that developers can focus on building, not dealing with our bugs. That’s why we recently started building an error detection system that can detect, categorize, and surface all build issues occurring on Workers Builds, enabling us to proactively fix issues and add missing features.
It’s also no secret that we’re big fans of being “Customer Zero” at Cloudflare, and Workers Builds is itself a Continue reading
BGP and MTU Deep Dive
A long long time ago, BGP implementations would use a Maximum Segment Size (MSS) of 536 bytes for BGP peerings. Why 536? Because in RFC 791, the original IP RFC, the maximum length of a datagram is defined as follows:
Total Length: 16 bits
Total Length is the length of the datagram, measured in octets,
including internet header and data. This field allows the length of
a datagram to be up to 65,535 octets. Such long datagrams are
impractical for most hosts and networks. All hosts must be prepared
to accept datagrams of up to 576 octets (whether they arrive whole
or in fragments). It is recommended that hosts only send datagrams
larger than 576 octets if they have assurance that the destination
is prepared to accept the larger datagrams.
The number 576 is selected to allow a reasonable sized data block to
be transmitted in addition to the required header information. For
example, this size allows a data block of 512 octets plus 64 header
octets to fit in a datagram. The maximal internet header is 60
octets, and a typical internet header is 20 octets, allowing a
margin for headers of higher level protocols.
The idea was to Continue reading
N4N028: The Wide World of WANs
We wanted to do an episode on SD-WAN, but realized we needed to set the stage for how wide-area networking developed. That’s why today’s episode is a history lesson of the Wide Area Network (WAN). We talk about how WANs emerged, public and private WANs, how WANs connect to LANs and data centers, the care... Read more »Dear ArubaCX, VXLAN VNI Has 24 Bits
I thought I’ve seen it all, but the networking vendors (and their lack of testing) never cease to amaze me. Today’s special: ArubaCX software VXLAN implementation.
We decided it’s a good idea to rewrite the VXLAN integration tests to use one target device and one FRR container to test inter-vendor VXLAN interoperability. After all, what could possibly go wrong with a simple encapsulation format that could be described on a single page?
Everything worked fine (as expected), except for the ArubaCX VM (running release Virtual.10.15.1005, build ID AOS-CX:Virtual.10.15.1005:9d92f5caa6b6:202502181604), which failed every single test.
HW053: Ubiquiti in the Enterprise
Ubiquiti is known primarily for wireless equipment for residential and small business use, but it can be a player in the enterprise world. On today’s show, we talk with Darrell DeRosia, Sr. Director, Network & Infrastructure Services with the Memphis Grizzlies, about how he provides that connectivity for the FedExForum, home to the Memphis Grizzlies... Read more »D2DO273: Azure VNets Don’t Exist
Cloud networks aren’t like traditional data center networks, so applying a traditional network design to the cloud probably isn’t the best idea. On today’s Day Two Cloud, guest Aidan Finn guides us through significant differences between Microsoft Azure networking and on-prem data center networks. For instance, subnets don’t segment hosts, network security groups do; every... Read more »Worth Reading: Practical Advice for Engineers
Sean Goedecke published an interesting compilation of practical advice for engineers. Not surprisingly, they include things like “focus on fundamentals” and “spend your working time doing things that are valuable to the company and your career” (OMG, does that really have to be said?).
Bonus point: a link to an article by Patrick McKenzie (of the Bits About Money fame) explaining why you SHOULD NOT call yourself a programmer (there goes the everyone should be a programmer gospel 😜).
Understanding Shortest Path First
Link state protocols like OSPF and IS-IS use the Shortest Path First (SPF) algorithm developed by Edsger Dijkstra. Edsger was a Dutch computer scientist, programmer, software engineer, mathematician, and science essayist. He wanted to solve the problem of finding the shortest distance between two cities such as Rotterdam and Groningen. The solution came to him when sitting in a café and the rest is history. SPF is used in many applications, such as GPS, but also in routing protocols, which I’ll cover today.
To explain SPF, I’ll be working with the following topology:
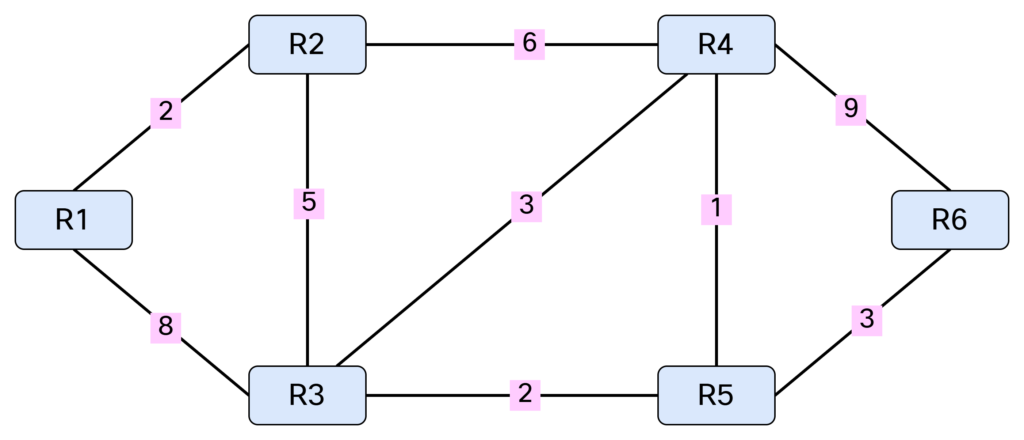
Note that SPF only works with a weighted graph where we have positive weights. I’m using symmetrical costs, although you could have different costs in each direction. Before running SPF, we need to build our Link State Database (LSDB) and I’ll be using IS-IS in my lab for this purpose. Based on the topology above, we can build a table showing the cost between the nodes:
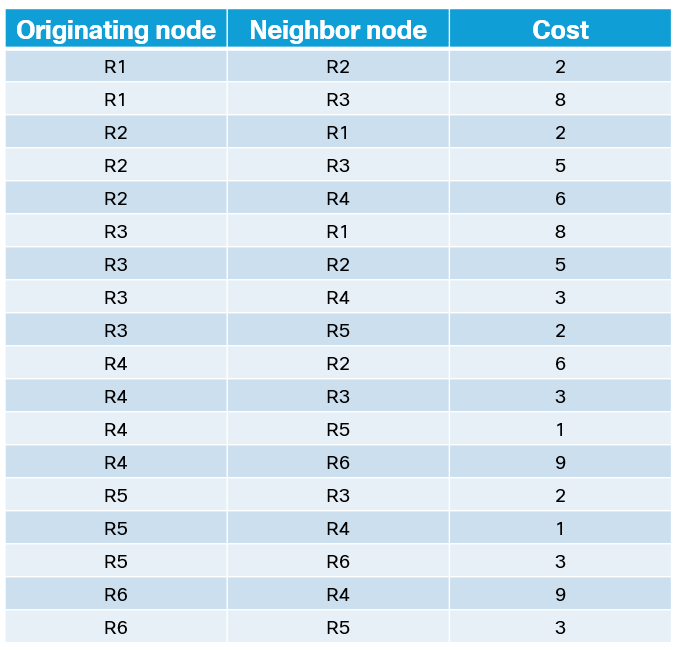
This triplet of information consists of originating node, neighbor node, and cost. It can also be represented as [R1, R2, 2], [R1, R3, 8], [R2, R1, 2], [R2, R3, 5], [R2, R4, 6], [R3, R1, 8], [R3, R2, 5], [R3, R4, Continue reading
BGP handling bug causes widespread internet routing instability
BGP handling bug causes widespread internet routing instability
At 7AM (UTC) on Wednesday May 20th 2025 a BGP message was propagated that triggered surprising (to many) behaviours with two major B
PP064: How Aviatrix Tackles Multi-Cloud Security Challenges (Sponsored)
Aviatrix is a cloud network security company that helps you secure connectivity to and among public and private clouds. On today’s Packet Protector, sponsored by Aviatrix, we get details on how Aviatrix works, and dive into a new feature called the Secure Network Supervisor Agent. This tool uses AI to help you monitor and troubleshoot... Read more »NB528: IP Fabric Adds Firewall Rule Simulation; Extreme Networks Debuts Agentic AI in Platform ONE
Take a Network Break! We begin with a Red Alert for critical vulnerabilities Kubernetes Gardener. Up next, a threat actor has been squatting on unused CNAME records to distribute malware and spam, and IP Fabric rolls out a new firewall rule simulation capability to let administrators test the effect of firewall rules on traffic patterns.... Read more »ChatGPT Strikes Again: IS-IS on Unnumbered Interfaces 🤦♂️
In the last few days, I decided to check out how much better ChatGPT has gotten in the last year or two. I tried to be positive and was rewarded with some surprisingly good results. I even figured out I can use it to summarize my blog posts using prompts like this one:
Using solely the information from blog.ipspace.net, what can you tell me about running ospf over unnumbered interfaces
And then I asked it about unnumbered interfaces and IS-IS, and it all went sideways:
Why we need a unified approach to Kubernetes environments
Today, organizations struggle managing disparate technologies for their Kubernetes networking and network security needs. Leveraging multiple technologies for networking and security for in-cluster, ingress, egress, and traffic across clusters creates challenges, including operational complexities and increased costs. For example, to manage ingress traffic for Kubernetes clusters, users cobble together multiple solutions from different providers such as ingress controllers or gateways and load balancers for routing traffic, as well as Web Application Firewalls (WAFs) for enhanced security.
Despite the challenges it brings, deploying disparate technologies has been a “necessary evil” for organizations to get all the capabilities needed for holistic Kubernetes networking. Here, we’ll explore challenges this proliferation of tooling introduces, and provide actionable tips for today’s platform and security teams to overcome these issues.
Challenges Managing Multiple Technologies
The fragmented approach to networking and network security in Kubernetes leads to challenges and inefficiencies, including:
- Operational overhead: Each technology comes with its own learning curve, setup, configuration, integration, and maintenance requirements. This leads to a challenging user experience.
- Increased costs: Licensing and operational costs accumulate as more tools are deployed.
- Scaling challenges: As clusters grow or spread across diverse environments, ensuring consistent and secure networking becomes harder.
- Security gaps: Disjointed solutions Continue reading
Repost: On the Advantages of XML
Continuing the discussion started by my Breaking APIs or Data Models Is a Cardinal Sin and Screen Scraping in 2025 blog posts, Dr. Tony Przygienda left another thoughtful comment worth reposting as a publicly visible blog post:
Having read your newest rant around my rant ;-} I can attest that you hit the nail on the very head in basically all you say:
- XML output big? yeah.
- JSON squishy syntax? yeah.
- SSH prioritization? You didn’t live it until you had a customer where a runaway python script generated 800+ XML netconf sessions pumping data ;-)
What is an EVPN Type 5 Route for (EVPN/VXLAN)
For EVPN/VXLAN, Type 5 routes are used for two purposes: Internally and Externally
Internally it’s used to communicate which VTEPs have a given subnet instantiated on it.
Here’s an example of the output of the command show ip bgp route-type ip-prefix ipv4 on an Arista cEOS spine running EVPN/VXLAN.
It’s showing you that 10.1.10.0/24 (VLAN 10/VNI 10010) is only available on leaf1 and leaf2 (10.1.255.1-2) and 10.1.20.0/24 (VLAN 20/VNI 10020) is only available on leaf3 and leaf4 (10.1.255.3-4). It’s eBGP so each leaf has its own ASN (you see in the path field). The next hop shows the VTEP IP (10.1.254.1-4). I checked on the spine as the spine receives all the EVPN routes from the leafs and propagates them as a route server. The spines don’t install any of these routes, they just propagates them.
Network Next Hop Metric LocPref Weight Path
* > RD: 10.1.255.1:10000 ip-prefix 10.1.10.0/24
10.1.254.1 - 100 0 65101 i
* > RD: 10.1.255.2:10000 ip-prefix 10.1.10.0/24
10.1.254.2 - 100 0 65102 i
Continue reading