Private 5G Networks Sector Surges with New Services, Investments, and User Trials
Enterprises face a fast-expanding array of 5G private network offerings as AWS, Cisco, HPE, and others have joined the fray since December.Hedge 122: The Internet Architecture Board

What is the Internet Architecture Board (IAB) of the IETF? What role does the IAB play in the larger ecosystem of building and deploying standard protocols? In this episode of the Hedge, Tom and Ethan “flip roles” with Russ to ask these questions.
10 Reasons to Implement Network Automation – Low Effort, High Impact
In 2022, nearly 77% of technology professionals see the need for improvement in their data center network automation strategies. Despite years of predictions about applications and data migrating to the public cloud, a consensus has been that data centers remain the indispensable core of any digital infrastructure. While the public cloud has a vital role to play and it continues to grow, enterprises and service providers continue to rely on data centers to power their operations. To remain relevant in a cloud-centric world, data centers must modernize – needing scalable, efficient, and agile operations. Highly manual processes do not scale gracefully, therefore calling for organizations and their data centers to adopt network automation or be left behind.
VMware is proud to have an opportunity to sponsor Enterprise Management Associates (EMA) in producing The Future of Data Center Network Automation research report. This report analyzes cutting-edge technology of data center automation – drawing on quantitative and qualitative research done by EMA analysts – focusing on how tech orgs are planning, implementing, and using data center network automation solutions, the specific technologies they’re using, and the benefits and challenges associated with data center network automation. Using real-time VMware customers Continue reading
Containerlab DDoS testbed
Real-time telemetry from a 5 stage Clos fabric describes lightweight emulation of realistic data center switch topologies using Containerlab. This article extends the testbed to experiment with distributed denial of service (DDoS) detection and mitigation techniques described in Real-time DDoS mitigation using BGP RTBH and FlowSpec.docker run --rm -it --privileged --network host --pid="host" \Start Containerlab.
-v /var/run/docker.sock:/var/run/docker.sock -v /run/netns:/run/netns \
-v ~/clab:/home/clab -w /home/clab \
ghcr.io/srl-labs/clab bash
curl -O https://raw.githubusercontent.com/sflow-rt/containerlab/master/ddos.ymlDownload the Containerlab topology file.
containerlab deploy -t ddos.ymlFinally, deploy the topology. Connect to the web interface, http://localhost:8008. The sFlow-RT dashboard verifies that telemetry is being received from 1 agent (the Customer Network, ce-router, in the diagram above). See the sFlow-RT Quickstart guide for more information. Now access the DDoS Protect application at http://localhost:8008/app/ddos-protect/html/. The BGP chart at the bottom right verifies that BGP connection has been established so that controls can be sent to the Customer Router, ce-router.
docker exec -it clab-ddos-attacker hping3 --flood --udp -k -s 53 192.0.2.129Start a simulated DNS amplification attack using hping3. The udp_amplification chart shows that traffic matching the attack signature has crossed the threshold. The Controls chart shows Continue reading
Day Two Cloud 138: Rethinking Logs And Analysis With vRealize Log Insight Cloud (Sponsored)
VMware is our sponsor today for a Day Two Cloud episode about logging. Specifically, we're talking about vRealize Log Insight Cloud. It’s not just about collecting logs and events, and it's not just for VMware products. What do you get out of the data being logged? That’s what’s interesting. This is much more than a pile of syslogs with a search engine dropped on top.Announcing the Cloudflare API Gateway


Over the past decade, the Internet has experienced a tectonic shift. It used to be composed of static websites: with text, images, and the occasional embedded movie. But the Internet has grown enormously. We now rely on API-driven applications to help with almost every aspect of life. Rather than just download files, we are able to engage with apps by exchanging rich data. We track workouts and send the results to the cloud. We use smart locks and all kinds of IoT devices. And we interact with our friends online.
This is all wonderful, but it comes with an explosion of complexity on the back end. Why? Developers need to manage APIs in order to support this functionality. They need to monitor and authenticate every single request. And because these tasks are so difficult, they’re usually outsourced to an API gateway provider.
Unfortunately, today’s gateways leave a lot to be desired. First: they’re not cheap. Then there’s the performance impact. And finally, there’s a data and privacy risk, since more than 50% of traffic reaches APIs (and is presumably sent through a third party gateway). What a mess.
Today we’re announcing the Cloudflare API Gateway. We’re going to completely replace Continue reading
Envoy Media: using Cloudflare’s Bot Management & ML

This is a guest post by Ryan Marlow, CTO, and Michael Taggart, Co-founder of Envoy Media Group.

My name is Ryan Marlow, and I’m the CTO of Envoy Media Group. I’m excited to share a story with you about Envoy, Cloudflare, and how we use Bot Management to monitor automated traffic.
Background
Envoy Media Group is a digital marketing and lead generation company. The aim of our work is simple: we use marketing to connect customers with financial services. For people who are experiencing a particular financial challenge, Envoy provides informative videos, money management tools, and other resources. Along the way, we bring customers through an online experience, so we can better understand their needs and educate them on their options. With that information, we check our database of highly vetted partners to see which programs may be useful, and then match them up with the best company to serve them.
As you can imagine, it’s important for us to responsibly match engaged customers to the right financial services. Envoy develops its own brands that guide customers throughout the process. We spend our own advertising dollars, work purely on a performance basis, and choose partners we know will do right Continue reading
Announcing Friendly Bots


When someone mentions bots on the Internet, what’s your first reaction?
It’s probably negative. Most of us conjure up memories of CAPTCHAs, stolen passwords, or some other pain caused by bad bots.
But the truth is, there are plenty of well-behaved bots on the Internet. These include Google’s search crawler and Stripe’s payment bot. At Cloudflare, we manually “verify” good bots, so they don’t get blocked. Our customers can choose to allowlist any bot that is verified. Unfortunately, new bots are popping up faster than we can verify them. So today we’re announcing a solution: Friendly Bots.
Let’s begin with some background.
How does a bot get verified?
We often find good bots via our public form. Anyone can submit a bot, but we prefer that bot operators complete the form to provide us with the information we need. We ask for some standard bits of information: your bot’s name, its public documentation, and its user agent (or regex). Then, we ask for information that will help us validate your bot. There are four common methods:
IP list
Send us a list of IP addresses used by your bot. This doesn’t have to be a static list — you can Continue reading
Introducing Advanced Rate Limiting


Still relying solely on IP firewalling? It’s time to change that.
While the IP address might still be one of the core technologies allowing networks to function, its value for security is long gone. IPs are rarely static; nowadays, mobile operators use carrier-grade network address translation (CGNAT) to share the same IP amongst thousands of individual devices or users. Bots then carry out distributed attacks with low request volume from different IPs to elude throttling. Furthermore, many countries consider IP addresses to be personal data, and it would be a great advancement for privacy if a replacement could be found for elements of security that currently rely on IP addresses to function. A product that is affected by this trend is rate limiting.
Rate limiting is designed to stop requests from overloading a server. It relies on rules. A rate limiting rule is defined by a filter (which typically is a path, like /login) and the maximum number of requests allowed from each user over a period of time. When this threshold is exceeded, an action is triggered (usually a block) for subsequent requests from the same user for a period of time (known as a timeout). Traditional throttling Continue reading
BGP Anycast Best Practices & Configurations
The post BGP Anycast Best Practices & Configurations appeared first on Noction.
Hub-and-Spoke VPLS: Revenge of LDP
In the Segment Routing vs LDP in Hub-and-Spoke Networks blog post I explained why you could get into interesting scaling issues when running MPLS with LDP in a large hub-and-spoke network, and how you can use Segment Routing (MPLS edition) to simplify your design.
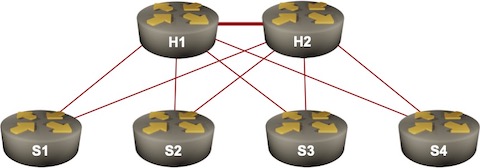
Sample hub-and-spoke network
Now imagine you’d like to offer VPLS services between hubs and spokes, and happen to be using equipment that uses targeted LDP sessions to signal pseudowires. Guess what happens next…
Hub-and-Spoke VPLS: Revenge of LDP
In the Segment Routing vs LDP in Hub-and-Spoke Networks blog post I explained why you could get into interesting scaling issues when running MPLS with LDP in a large hub-and-spoke network, and how you can use Segment Routing (MPLS edition) to simplify your design.

Sample hub-and-spoke network
Now imagine you’d like to offer VPLS services between hubs and spokes, and happen to be using equipment that uses targeted LDP sessions to signal pseudowires. Guess what happens next…
On findingballoons in data center networks micro-detection using adaptive ➰ feedback loops ♻
Using #SRLinux for flexible decentralized DDoS attack detection #SecDevOps
Distributed Denial of Service (DDoS) attacks continue to be a major problem for many network operators and their customers. As in most networking problems, the key issue is scale: Attackers are able to mount an amplified attack using many (N) sources to send large (M) payloads to a single (1) target server, causing link and CPU saturation and system overload
N*M >> 1 ~> overloaded system(s) and unhappy customers
Much like security in general, solving DDoS attacks is a continuous process, not a one-time product or solution deployment. While most operators have deployed DDoS mitigation solutions, there will — unfortunately — always come a time where the current solution falls short, and something else or more is needed.
#DevSecOps: Shortening feedback loops

Back in 2011 Peter Phaal wrote a blog about “Delay and stability”. Even though more than a decade has passed since, one can easily see how triggers like AWS outages haven’t changed — these points remain relevant and valid today:
✅ Measurement(observability) plays a critical role in data centers; it is the
foundation for automation (more on this Continue reading



