Hedge 117: Mike Bushong and the Product Process
Continuing our series on how vendors build networking products, Mike Bushong joins this episode of the Hedge to discuss the overall process, the importance of the product manager, and the importance of managing and selling change. Join Tom Ammon, Eyvonne, and Russ White as we discuss how vendors build products.
Need to Keep Analytics Data in the EU? Cloudflare Zaraz Can Offer a Solution


A recent decision from the Austrian Data Protection Authority (the Datenschutzbehörde) has network engineers scratching their heads and EU companies that use Google Analytics scrambling. The Datenschutzbehörde found that an Austrian website’s use of Google Analytics violates the EU General Data Protection Regulation (GDPR) as interpreted by the “Schrems II” case because Google Analytics can involve sending full or truncated IP addresses to the United States.
While disabling such trackers might be one (extreme) solution, doing so would leave website operators blind to how users are engaging with their site. A better approach: find a way to use tools like Google Analytics, but do so with an approach that protects the privacy of personal information and keeps it in the EU, avoiding a data transfer altogether. Enter Cloudflare Zaraz.
But before we get into just how Cloudflare Zaraz can help, we need to explain a bit of the background for the Datenschutzbehörde’s ruling, and why it’s a big deal.
What are the privacy and data localization issues?
The GDPR is a comprehensive data privacy law that applies to EU residents’ personal data, regardless of where it is processed. The GDPR itself does not insist that personal data must Continue reading
Do a Cleanup Before Automating Your Network
Remington Loose sent me an interesting email describing his views on the right approach to network automation after reading my Network Reliability Engineering Should Be More than Software or Automation rant – he’s advocating standardizing network services and cleaning up your network before trying to deploy full-scale automation.
I think you are 100% right to start with a thorough cleanup before automation. Garbage in, garbage out. It is also the case that all that inconsistency and differentiation makes for complexity in automation (as well as general operations) that makes it harder to gain traction.
Do a Cleanup Before Automating Your Network
Remington Loose sent me an interesting email describing his views on the right approach to network automation after reading my Network Reliability Engineering Should Be More than Software or Automation rant – he’s advocating standardizing network services and cleaning up your network before trying to deploy full-scale automation.
I think you are 100% right to start with a thorough cleanup before automation. Garbage in, garbage out. It is also the case that all that inconsistency and differentiation makes for complexity in automation (as well as general operations) that makes it harder to gain traction.
DC Fabric Intelligence Panel at DCD
On the 10th of February (next week) I’m participating in a panel discussing—
A networking strategy involving disaggregation deployment, overlay network virtualization, automation, and visibility can remedy the complexities with better utilization and performance and ultimately enable network slicing and self-healing abilities. Cloudification of the network is here, but how far do we need to go, and what is the impact on the hardware?
Cloud Engineering For The Network Pro (Video)
The Packet Pushers are launching a new video series with Michael Levan on cloud engineering for network pros. The first video in the series gets into the basics of cloud networks. Michael covers AWS and Azure in particular. You can watch the video below, or click here to see it on YouTube. You can subscribe […]
The post Cloud Engineering For The Network Pro (Video) appeared first on Packet Pushers.
In Memoriam: Kurt Marko
We at Packet Pushers Interactive were saddened to learn of the death of Kurt Marko on January 12th, 2022. Kurt wrote numerous columns for this Web site and our Ignition site, as well as for other publications such as Diginomica. We respected his insights, analysis, and informed perspective. Kurt’s writing and analysis were informed by […]
The post In Memoriam: Kurt Marko appeared first on Packet Pushers.
Why Privacy?
I’ve kicked off a series over at Packet Pushers on the ; the first installment is up now.
There’s a chapter in my new book on the topic, as well.
Cato Networks Adds A Cloud Access Security Broker (CASB) For App Visibility And Control
Cato Networks is announcing the availability of a Cloud Access Security Broker (CASB) capability that will be integrated into Cato’s cloud-based security service, which already includes next-gen firewalls, anti-malware, and more. The CASB provides visibility into, and control over, SaaS, cloud, and on-premises applications. Visibility is a key feature of the CASB service. SaaS and […]
The post Cato Networks Adds A Cloud Access Security Broker (CASB) For App Visibility And Control appeared first on Packet Pushers.
Day Two Cloud 132: What Web3 Means For Infrastructure Engineers
Web3 is the term for an emerging technology movement that aims to create a more decentralized Internet and put more ownership in the hands of individual users and consumers. At present Web3 is associated with cryptocurrencies and NFTs, but it's worth understanding the technological underpinnings of Web3, particularly blockchain and its broader applications. Our guide to Web3 infrastructure is Josh Neuroth.
The post Day Two Cloud 132: What Web3 Means For Infrastructure Engineers appeared first on Packet Pushers.
Day Two Cloud 132: What Web3 Means For Infrastructure Engineers
Web3 is the term for an emerging technology movement that aims to create a more decentralized Internet and put more ownership in the hands of individual users and consumers. At present Web3 is associated with cryptocurrencies and NFTs, but it's worth understanding the technological underpinnings of Web3, particularly blockchain and its broader applications. Our guide to Web3 infrastructure is Josh Neuroth.Pluribus Netvisor ONE R7 Feature Spotlight: Kubernetes-aware Fabric with the KubeTracker™ Fabric Service
One of the most innovative features of Netvisor 7 is a new suite of monitoring and visibility tools, including FlowTracker and KubeTracker™ fabric services.
The post Pluribus Netvisor ONE R7 Feature Spotlight: Kubernetes-aware Fabric with the KubeTracker™ Fabric Service appeared first on Pluribus Networks.
Pluribus Netvisor ONE R7 Feature Spotlight: Kubernetes-aware Fabric with the KubeTracker™ Fabric Service
Today, Pluribus released Netvisor 7, which marks another major step forward in our mission to radically simplify deployment and operations for distributed cloud networking. One of the most innovative features of this release is a new suite of monitoring and visibility tools, including FlowTracker and KubeTracker fabric services.
fabric services.
In prior releases, Netvisor ONE OS and the Adaptive Cloud Fabric software could capture flow telemetry for TCP flows only. With the introduction of FlowTracker in R7, Pluribus now provides telemetry on every flow traversing the fabric, including TCP, UDP, ICMP and even infrastructure services flows like DCHP, DNS and more.
Amazingly, this comprehensive flow telemetry is achieved without the need for an expensive external TAP and TAP aggregation overlay infrastructure. The cost of procuring and deploying TAPS to capture packet flows for analysis can be daunting and often results in cost/benefit tradeoffs where TAPS are only installed at certain points in the network. With FlowTracker, that expense and those tradeoffs are eliminated, every flow in the fabric is captured, and flow metadata is exported to tools like our UNUM Insight Analytics platform.
The KubeTracker fabric service is a powerful new capability delivered by the Adaptive Cloud Fabric specifically for network operators Continue reading
How to stop running out of ephemeral ports and start to love long-lived connections
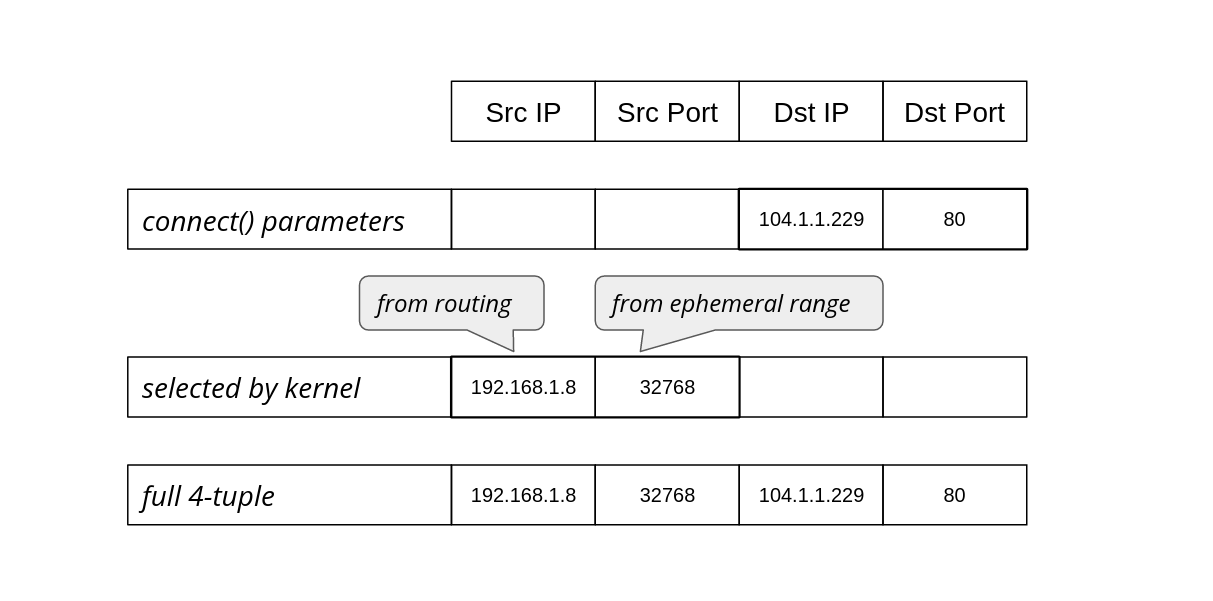
Often programmers have assumptions that turn out, to their surprise, to be invalid. From my experience this happens a lot. Every API, technology or system can be abused beyond its limits and break in a miserable way.
It's particularly interesting when basic things used everywhere fail. Recently we've reached such a breaking point in a ubiquitous part of Linux networking: establishing a network connection using the connect() system call.
Since we are not doing anything special, just establishing TCP and UDP connections, how could anything go wrong? Here's one example: we noticed alerts from a misbehaving server, logged in to check it out and saw:
marek@:~# ssh 127.0.0.1
ssh: connect to host 127.0.0.1 port 22: Cannot assign requested address
You can imagine the face of my colleague who saw that. SSH to localhost refuses to work, while she was already using SSH to connect to that server! On another occasion:
marek@:~# dig cloudflare.com @1.1.1.1
dig: isc_socket_bind: address in use
This time a basic DNS query failed with a weird networking error. Failing DNS is a bad sign!
In both cases the problem was Linux running out of ephemeral ports. When Continue reading
netsim-tools Release 1.1.2
Every time I’m writing netsim-tools release notes I’m amazed at the number of features we managed to put together in just a few weeks.
Here are the goodies from netsim-tools releases 1.1.1 and 1.1.2:
netsim-tools Release 1.1.2
Every time I’m writing netsim-tools release notes I’m amazed at the number of features we managed to put together in just a few weeks.

Here are the goodies from netsim-tools releases 1.1.1 and 1.1.2: