A Safety Inquiry on 5G Deployments at U.S. Airports Balloons
The DOT, wireless carriers, the FAA, the aviation industry, and Biden Administration are all now involved in resolving a complex situation that airline CEOs claim could worsen air travel operations chaos beyond continuing Covid cancellations level.Day Two Cloud 130: Getting Started With OpenShift For Kubernetes Orchestration
On today's Day Two Cloud we have a career conversation with Angela Andrews, a Solution Architect at Red Hat. Angela provides an introduction to OpenShift, a cloud-based offering for running and orchestrating Kubernetes containers in public clouds and on premises from Red Hat. We also discuss how to integrate communication skills with technical knowledge, the role of a Solution Architect, how to stay on top of new and changing technologies, and more.
The post Day Two Cloud 130: Getting Started With OpenShift For Kubernetes Orchestration appeared first on Packet Pushers.
Day Two Cloud 130: Getting Started With OpenShift For Kubernetes Orchestration
On today's Day Two Cloud we have a career conversation with Angela Andrews, a Solution Architect at Red Hat. Angela provides an introduction to OpenShift, a cloud-based offering for running and orchestrating Kubernetes containers in public clouds and on premises from Red Hat. We also discuss how to integrate communication skills with technical knowledge, the role of a Solution Architect, how to stay on top of new and changing technologies, and more.VMware Network Automation with NSX-T 3.2 and vRealize Automation
VMware Network Automation combines the modern microservices architecture of vRealize with VMware NSX network virtualization to enable rapid application rollout. The solution automates VMware NSX via VMware vRealize Automation to deliver complete workload lifecycle automation through networking, compute, and security services that make it simple to template, provision, and update complete environments. That, in turn, enables businesses to accelerate application delivery and drive overall agility.

The latest iterations of vRealize Automation native integration with NSX-T features include multiple new capabilities, such as support for NSX-T Federation, distributed firewall configurations from NSX-T, a shared gateway across on-demand networks, and many others.
In this post, we will provide an overview of the feature-set available with this native integration. The post doesn’t aim to be exhaustive, so don’t hesitate to look at the vRealize Automation documentation for more details.
Setting up the Environment
The native integration allows for consumption of NSX-T constructs from vRealize Automation after a simple configuration.
The goal is for the cloud admin to be able to offer users a self-service catalog, through Service Broker that enables the deployment of complex topologies with consistent governance policies across the cloud — all while abstracting the underlying infrastructure and its complexity from Continue reading
Tonga’s likely lengthy Internet outage

2022 only has 19 days of existence but so far this January, there have already been four significant Internet disruptions:
1. An Internet outage in The Gambia because of a cable problem.
2. An Internet shutdown in Kazakhstan because of unrest.
3. A mobile Internet shutdown in Burkina Faso because of a coup plot.
4. An Internet outage in Tonga because of a volcanic eruption.
The latest Internet outage, in the South Pacific country of Tonga (with 169 islands), is still ongoing. It started with the large eruption of Hunga Tonga–Hunga Haʻapai, an uninhabited volcanic island of the Tongan archipelago on Friday, January 14, 2022. The next day, Cloudflare Radar shows that the Internet outage started at around 03:00 UTC (16:00 local time) — Saturday, January 15, 2022 — and is ongoing for more than four days. Tonga’s 105,000 residents are almost entirely unreachable, according to the BBC.
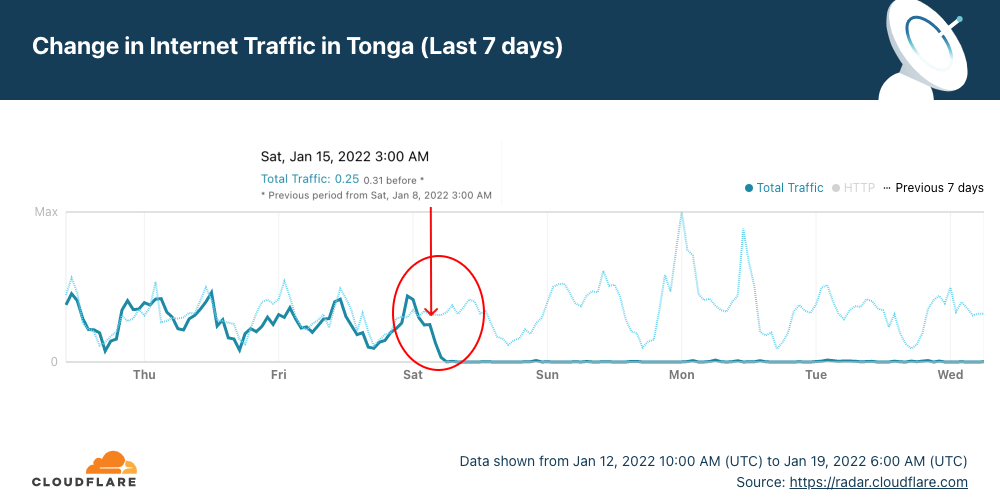
When we focus on the number of requests by ASN, the country’s main ISPs Digicel and Kalianet started to lose traffic after 03:00 UTC and by 05:30 UTC January 15, 2022, Cloudflare saw close to no traffic at all from them, as shown in the graph below.
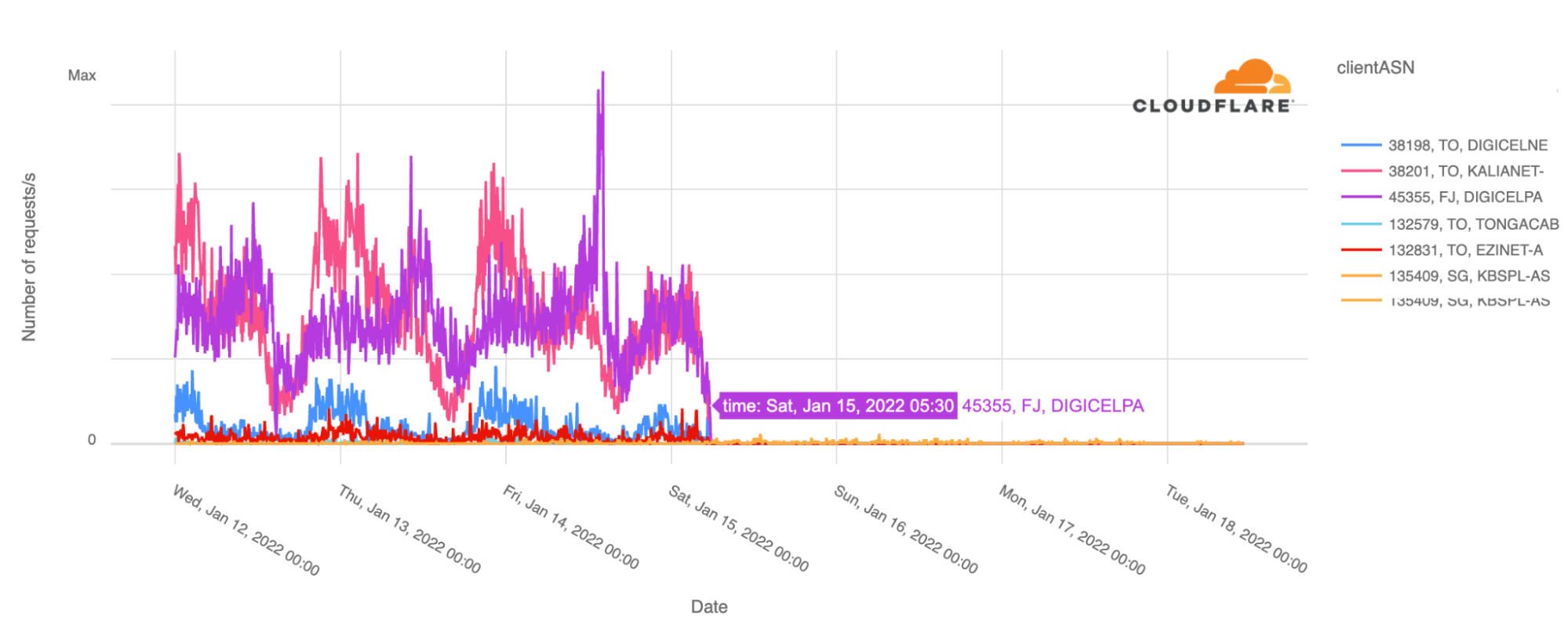
Looking at the BGP Continue reading
Introducing netsim-tools Plugins
Remember the BGP anycast lab I described in December 2021? In that blog post I briefly mentioned a problem of extraneous IBGP sessions and promised to address it at a later date. Let’s see how we can fix that with netsim-tools plugin.
We always knew that it’s impossible to implement every nerd knob someone would like to have when building their labs, and extending the tool with Python plugins seemed like the only sane way to go. We added custom plugins to netsim-tools release 1.0.6, but I didn’t want to write about them because we had to optimize the internal data structures first.
Introducing netlab Plugins
Remember the BGP anycast lab I described in December 2021? In that blog post I briefly mentioned a problem of extraneous IBGP sessions and promised to address it at a later date. Let’s see how we can fix that with a netlab plugin.
We always knew that it’s impossible to implement every nerd knob someone would like to have when building their labs, and extending the tool with Python plugins seemed like the only sane way to go. We added custom plugins to netlab in late 2021, but I didn’t want to write about them because we had to optimize the internal data structures first.
Beau Williamson: The Man Who Lived His Bucket List
Stream 1 October 2013: CCIE#1346 didn’t like it. In fact, he despised it so much that even after the edits he never posted the recommendation on his LinkedIn profile. The endorsement passage was strong and to the point; after having had his book, Developing IP Multicast Networks, for years and using it constantly, I […]
The post Beau Williamson: The Man Who Lived His Bucket List appeared first on Packet Pushers.
Tomonari Sato: Why I joined Cloudflare and why I’m helping Cloudflare grow in Japan

This post is also available in 日本語.

I’m excited to announce that I recently joined Cloudflare in Japan as Vice-President and Managing Director, to help build and expand our customer, partner base, and presence in Japan. Cloudflare expanded its network in Japan in 2010, just months after launching. Now, 12 years later, Cloudflare is continuing its mission to help build a better Internet in Japan and across the globe, and I’m looking forward to being able to contribute to that mission!

A little about me
In my 35-year career in the IT industry, I have been fortunate enough to work with some of the biggest technology companies in the world, working in various roles in both sales and technical sides of the business. I consider this one of my biggest strengths. In addition, working in the IT industry has allowed me to acquire industry knowledge across a number of different solutions such as custom development, packaged systems (ERP, CRM), MS Office products, and cloud solutions.
Most recently, I was director of the Enterprise Business Group for Japan at AWS, where I was responsible for all commercial industries such as Manufacturing, Process, Distribution, Retail, Telecommunications, Utility, Media, Service, Pharmaceuticals, among others. Continue reading
IP Addressing through 2021
Time for another annual roundup from the world of IP addresses. Let's see what has changed in the past 12 months in addressing the Internet and look at how IP address allocation information can inform us of the changing nature of the network itself.Infrastructure Bill Presents a Broadband Access Opportunity of a Generation
Given government austerity, tight budgets, and political polarization, it’s safe to say the broadband opportunities presented by the infrastructure bill will not likely come around again for a while.How to Monitor Calico’s eBPF Data Plane for Proactive Cluster Management
Monitoring is a critical part of any computer system that has been brought in to a production-ready state. No IT system exists in true isolation, and even the simplest systems interact in interesting ways with the systems “surrounding” them. Since compute time, memory, and long-term storage are all finite, it’s necessary at the very least to understand how these things are being allocated.
Why Does the Calico eBPF Data Plane Support Metrics?
Perhaps this question seems contrived. However, it’s always worth spending a moment thinking about reasons before adding any technical complexity to a distributed system! After all, they are already quite complicated! So why does the Calico eBPF data plane support metrics through Prometheus and Grafana?
Well, the Calico eBPF data plane is production ready and widely deployed, so a well-configured Kubernetes cluster with the Calico eBPF data plane correctly enabled will be stable and reliable. However, distributed systems are inherently complex and when dealing with them, it is generally good practice to instrument and baseline metrics wherever they are available. Doing so provides many benefits, especially for capacity planning, change management, and as an early-warning or smoke-testing system.
Additionally, seeing a running distributed system fully instrumented can be Continue reading
Full Stack Journey 062: Advice And Recommendations For Tech Learners
The Full Stack Journey is back for 2022, and kicking off the year Scott shares recommendations for learning new technologies based on his own career experiences and the technology transitions he's lived through, including virtualization to networking and networking to containers. Scott also shares four key takeaways for learners in the tech industry.
The post Full Stack Journey 062: Advice And Recommendations For Tech Learners appeared first on Packet Pushers.
Full Stack Journey 062: Advice And Recommendations For Tech Learners
The Full Stack Journey is back for 2022, and kicking off the year Scott shares recommendations for learning new technologies based on his own career experiences and the technology transitions he's lived through, including virtualization to networking and networking to containers. Scott also shares four key takeaways for learners in the tech industry.VaporIO Brings Infrastructure, Networking On-Demand For Dynamic Edge Services, And VMware Is Interested
This article was originally posted on the Packet Pushers Ignition site on June 15, 2021. There’s a growing need at the provider edge to let customers provision services closer to users and data sources. What do I mean by the ‘provider edge’? In the case of application infrastructure with low-latency connectivity for mobile, industrial, and […]
The post VaporIO Brings Infrastructure, Networking On-Demand For Dynamic Edge Services, And VMware Is Interested appeared first on Packet Pushers.
Layer-3 Carrier Ethernet
One of ipSpace.net subscribers asked for my opinion about Adaptive IP, a concept promoted by one of the optical connectivity vendors. As he put it:
My interest in Carrier Ethernet moving up to Layer 3 is to see if it would be something to account for in the future.
A quick search resulted in a marketecture using Segment Routing (of course) and an SDN controller (what else could one be using today) using Path Computation Element Protocol (PCEP) to program the network devices… and then I hit a regwall. They wanted to collect my personal details to grace me with their whitepaper, and I couldn’t find even a link to the product documentation.
Layer-3 Carrier Ethernet
One of ipSpace.net subscribers asked for my opinion about Adaptive IP, a concept promoted by one of the optical connectivity vendors. As he put it:
My interest in Carrier Ethernet moving up to Layer 3 is to see if it would be something to account for in the future.
A quick search resulted in a marketecture using Segment Routing (of course) and an SDN controller (what else could one be using today) using Path Computation Element Protocol (PCEP) to program the network devices… and then I hit a regwall. They wanted to collect my personal details to grace me with their whitepaper, and I couldn’t find even a link to the product documentation.