Feedback: Mastering Cloud Networking
Most of the public cloud training seems focused on developers. No surprise there, they are the usual beachhead public cloud services need to get into large organizations. Unfortunately, once the production applications start getting deployed into public cloud infrastructure, someone has to take over operations, and that’s where the fun starts.
For whatever reason, there aren’t that many resources helping the infrastructure operations teams understand how to deal with this weird new world, at least according to the feedback Jawed left on Azure Networking webinar:
Feedback: Mastering Cloud Networking
Most of the public cloud training seems focused on developers. No surprise there, they are the usual beachhead public cloud services need to get into large organizations. Unfortunately, once the production applications start getting deployed into public cloud infrastructure, someone has to take over operations, and that’s where the fun starts.
For whatever reason, there aren’t that many resources helping the infrastructure operations teams understand how to deal with this weird new world, at least according to the feedback Jawed left on Azure Networking webinar:
The secret to Cloudflare’s pace of Innovation


We are 11! And we also may be a little bleary-eyed and giddy from a week of shipping.

Our Birthday Weeks are one of my favorite Cloudflare traditions — where we release innovations that help to build a better Internet. Just this week we tackled email security, expanded our network into office buildings, and entered into the Web3 world.

But these weeks also precipitate the most common questions I’m asked from my product and engineering peers across the industry: how do we do it? How do we get so much stuff out so quickly? That we are able to innovate — and innovate so quickly — is no happy accident. In fact, this capability has been very deliberately built into the DNA of Cloudflare. I want to touch on three of the reasons unique to us: one relates to our people, one relates to our technology, and one relates to our customers.
Cultivating curiosity
The seeds of innovative ideas start with our team. One of the core things we look for when hiring in every role at Cloudflare — be it engineering and product or sales or account — is curiosity. We seek people who approach a situation Continue reading
Nornir: Inventory Structure and Filtering
The inventory is at the core of Nornir holding all the hosts that tasks will be run against and the variables that will be used by those tasks. Before any tasks can be run by Nornir the inventory has to be initialised.
Two Weeks Later: Finding and Eliminating Long Tail Latencies


A little over two weeks ago, we shared extensive benchmarking results of edge networks all around the world. It showed that on a range of tests (TCP connection time, time to first byte, time to last byte), and on a range of measurements (p95, mean), that Cloudflare had some impressive network performance. But we weren't the fastest everywhere. So we made a commitment: we would improve in at least 10% of networks where we were not #1.
Today, we’re happy to tell you that we’ve delivered as promised. Of the networks where our average latency exceeded 100ms behind the leading provider during Speed Week, we’ve dramatically improved our performance. There were 61 networks; now, we’re the fastest in 29 of them. Of course, we’re not done yet — but we wanted to share with you the latest results, and explain how we did it.
Measuring What Matters
In the process of quantifying network performance, it became clear where we were not the fastest everywhere. There were 61 country/network pairs where we more than 100ms behind the leading provider:
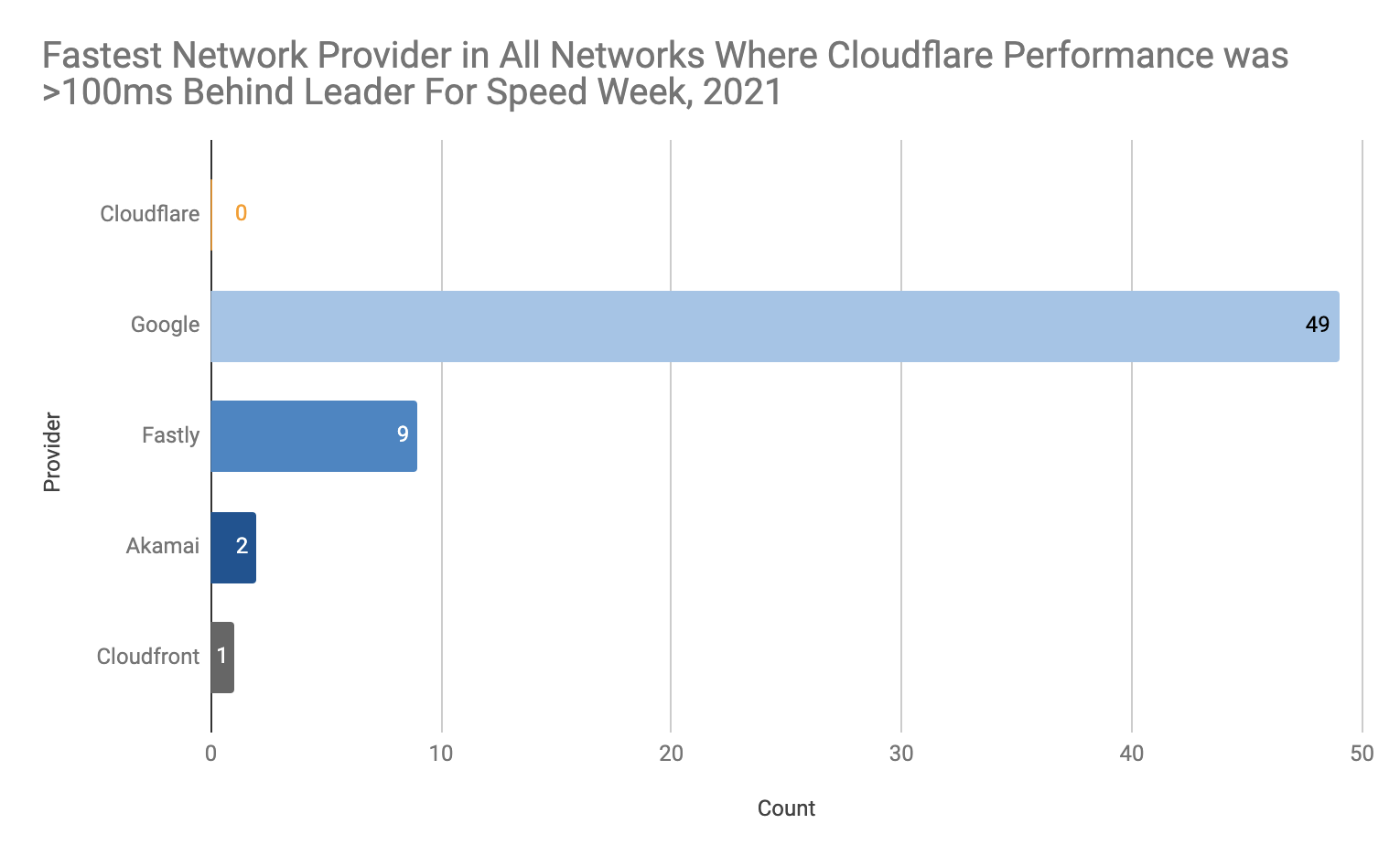
Once that was done, the fun began: we needed to go through the process of figuring out why we were slow — Continue reading
Heavy Networking 600: Inside A Non-Profit Internet Exchange
Internet exchange points are networks you can use to connect to some other exchange participant. Sounds like maybe that’s a service provider thing, and it can be. But IXPs are useful for businesses, too. In this episode of Heavy Networking, we’re going to learn about IXPs, and non-profit IXPs in particular.
The post Heavy Networking 600: Inside A Non-Profit Internet Exchange appeared first on Packet Pushers.
Heavy Networking 600: Inside A Non-Profit Internet Exchange
Internet exchange points are networks you can use to connect to some other exchange participant. Sounds like maybe that’s a service provider thing, and it can be. But IXPs are useful for businesses, too. In this episode of Heavy Networking, we’re going to learn about IXPs, and non-profit IXPs in particular.Seeking Service Mesh Sessions at VMworld
It’s that time of the year again, when all of VMware’s customers and the vCommunity at large assemble for the annual gathering of learning and shared knowledge that we call VMworld.
This year, like last year, VMworld will be held in a virtual format and, just like last year, it’s completely free! Last year’s VMworld was a big success, with many great sessions and a record number of attendees who joined from around the world.
As for Tanzu Service Mesh, I have good news for all you service mesh enthusiasts — and for those who are just starting to learn about service mesh. This year will see an exponential increase in the number of sessions that cover Tanzu Service Mesh. —
Service Mesh Sessions You Won’t Want to Miss:
- Solutions Keynote: DevSecOps Your Way to Any Cloud (And Delight Customers) [V13190]
This session, led by Ajay Patel, SVP and GM of the Modern Apps and Management Business Unit, will review VMware solutions that enable a DevSecOps practice for our customers — and that includes Tanzu Service Mesh. Pratik Roychowdhury a Tanzu Service Mesh director of product management, will talk about how Tanzu Service Mesh provides a way to observe and control API calls exchanged between micro-services. Pratik will also describe our PII Data Leakage protection Continue reading
Cloud PCs: From DIY to SaaS
A SaaS approach to DaaS can deliver maximum uptime at a fraction of the cost of DIY cloud desktops.How to Utilize Automation to Revolutionize Modern Networks
At VMworld 2021, we’re imagining what’s possible when it comes to the public cloud experience everywhere. IT enterprises are expected to keep up with increasing consumer demands, focusing on fast application roll out across multiple clouds. There’s an industry wide emphasis being placed on delivering immediate, secure, and strong end-user network experience to get the job done right. At this year’s conference, we’re looking at real customers and their experiences when it comes to optimizing automation in modern network environments.
Dankse Bank, a leader in the financial industry, learned what was necessary to achieve the most simplified self-service functionality possible. By starting with Day 0 deployment and all the way to Day 2 delivery, Dankse Bank secured sustainable service delivery and self-service modifications. VMworld 2021 session Network Operations: Intelligence and Automation from Day 0 to Day 2 takes a deeper look at this customer’s intelligence journey to show how you can achieve simplification within the public cloud, too.
Simplifying Day 0 and Day 2 ops are action steps IT can take to streamline business ops but understanding the modern enterprise – and the complexities involved – is evergreen. Learning the ins-and-outs of the modern network with end-to-end virtualization allows businesses like yours to succeed in even the most diverse environments. Tom Gillis, Business Group leader, NASBG, of VMware, takes us on a deep dive of why building out a better security posture within diverse infrastructure is crucial. You Continue reading
Chip Shortages Aren’t Sweet for Networking

Have you tried to order networking gear recently? You’re probably cursing because the lead times on most everything are getting long. It’s not uncommon to see lead times on wireless access points or switch gear reaching 180 days or more. Reports from the Internet say that some people are still waiting to get things they ordered this spring. The prospect of rapid delivery of equipment is fading like the summer sun.
Why are we here? What happened? And can we do anything about it?
Fewer Chips, More Air
The pandemic has obviously had the biggest impact for a number of reasons. When a fabrication facility shuts down it doesn’t just ramp back up. Even when all the workers are healthy and the city where it is located is open for business it takes weeks to bring everything back online to full capacity. Just like any manufacturing facility you can’t just snap your fingers and get back to churning out the widgets.
The pandemic has also strained supply chains around the world. Even if the fabs had stayed open this entire time you’d be looking at a shortage of materials to make the equipment. Global supply chains were running extremely lean Continue reading
FRnOG #34: how we deployed a datacenter in one click
Here are the slides I presented for FRnOG #34 in October 2021. They are about automating the deployment of Blade’s datacenters using Jerikan and Ansible. For more information, have a look at “Jerikan+Ansible: a configuration management system for network.”
The presentation, in French, was recorded. I have added English subtitles.1
-
Good thing if you don’t understand French as my diction was poor with a lot of fillers. ↩︎
Announcing The Cloudflare Distributed Web Gateways Private Beta: Unlocking the Web3 Metaverse and Decentralized Finance for Everyone


It’s cliché to say that the Internet has undergone massive changes in the last five years. New technologies like distributed ledgers, NFTs, and cross-platform metaverses have become all the rage. Unless you happen to hang out with the Web3 community in Hong Kong, San Francisco, and London, these technologies have a high barrier to entry for the average developer. You have to understand how to run distributed nodes, set up esoteric developer environments, and keep up with the latest chains just to get your app to run. That stops today. Today you can sign up for the private beta of our Web3 product suite starting with our Ethereum and IPFS gateway.

Before we go any further, a brief introduction to blockchain (Ethereum in our example) and the InterPlanetary FileSystem (IPFS). In a Web3 setting, you can think of Ethereum as the compute layer, and IPFS as the storage layer. By leveraging decentralised ledger technology, Ethereum provides verifiable decentralised computation. Publicly available binaries, called "smart contracts", can be instantiated by users to perform operations on an immutable set of records. This set of records is the state of the blockchain. It has to be maintained by every node on the Continue reading
Get started Building Web3 Apps with Cloudflare
For many developers, the term Web3 feels like a buzzword — it's the sort of thing you see on a popular "Things you need to learn in 2021" tweet. As a software developer, I've spent years feeling the same way. In the last few months, I’ve taken a closer look at the Web3 ecosystem, to better understand how it works, and why it matters.
Web3 can generally be described as a decentralized evolution of the Internet. Instead of a few providers acting as the mediators of how your interactions and daily life on the web should work, a Web3-based future would liberate your data from proprietary databases and operate without centralization via the incentive structure inherent in blockchains.
The Web3 space in 2021 looks and feels much different from what it did a few years ago. Blockchains like Ethereum are handling incredible amounts of traffic with relative ease — although some improvements are needed — and newer blockchains like Solana have entered the space as genuine alternatives that could alleviate some of the scaling issues we've seen in the past few years.
Cloudflare is incredibly well-suited to empower developers to build the future with Web3. The announcement of Continue reading
Web3 — A vision for a decentralized web


By reading this, you are a participant of the web. It's amazing that we can write this blog and have it appear to you without operating a server or writing a line of code. In general, the web of today empowers us to participate more than we could at any point in the past.
Last year, we mentioned the next phase of the Internet would be always on, always secure, always private. Today, we dig into a similar trend for the web, referred to as Web3. In this blog we'll start to explain Web3 in the context of the web's evolution, and how Cloudflare might help to support it.
Going from Web 1.0 to Web 2.0
When Sir Tim Berners-Lee wrote his seminal 1989 document “Information Management: A Proposal”, he outlined a vision of the “web” as a network of information systems interconnected via hypertext links. It is often assimilated to the Internet, which is the computer network it operates on. Key practical requirements for this web included being able to access the network in a decentralized manner through remote machines and allowing systems to be linked together without requiring any central control or coordination.
Video: Public Cloud Networking Is Different
Even though you need plenty of traditional networking constructs to deploy a complex application stack in a public cloud (packet filters, firewalls, load balancers, VPN, BGP…), once you start digging deep into the bowels of public cloud virtual networking, you’ll find out it’s significantly different from the traditional Ethernet+IP implementations common in enterprise data centers.
For an overview of the differences watch the Public Cloud Networking Is Different video (part of Introduction to Cloud Computing webinar), for more details start with AWS Networking 101 and Azure Networking 101 blog posts, and continue with corresponding cloud networking webinars.