Network Break 326: Cloudflare Announces New WAN Services; Intel’s Turnaround Roadmap
Can Pat Gelsinger refloat the Intel container ship? Is Cloudflare's new magic WAN service all that new? What's behind the Fortinet/Linksys partnership? Is a tweet really worth $2.9 million? This week's Network Break podcast ponders these and other tech questions, plus listener FUs.
The post Network Break 326: Cloudflare Announces New WAN Services; Intel’s Turnaround Roadmap appeared first on Packet Pushers.
Network Break 326: Cloudflare Announces New WAN Services; Intel’s Turnaround Roadmap
Can Pat Gelsinger refloat the Intel container ship? Is Cloudflare's new magic WAN service all that new? What's behind the Fortinet/Linksys partnership? Is a tweet really worth $2.9 million? This week's Network Break podcast ponders these and other tech questions, plus listener FUs.The Week in Internet News: Facebook Calls for Changes in Legal Protections for User Content

Rewriting the rules: Facebook, during a hearing in the U.S. Congress, called on lawmakers to revamp Section 230 of the Communications Decency Act of 1996, which protects websites from lawsuits for content posted by users, NBC News reports. Websites should be protected if they adopt user moderation practices largely in line with Facebook’s own rules, ZDNet noted. The change could give Facebook an advantage while upending much of the rest of the Internet, The Verge suggested.
Competition in space: The competition among satellite-based broadband providers is heating up, with OneWeb launching 36 new satellites from eastern Russia, The BBC reports. The company, now primarily owned by Indian conglomerate Bharti Global and the U.K. government, now has 146 broadband satellites deployed. The company plans to offer broadband service later this year to northern latitudes, including the U.K., Northern Europe, Alaska, Canada, and other areas. Meanwhile, three rural counties in North Carolina are testing broadband service from SpaceX, another satellite provider, as a way to provide Internet service to students, GCN says.
Bad virus information: Facebook and Twitter have removed millions of posts containing misinformation about COVID-19 in recent months, The Straits Times reports. Since last year, Continue reading
A new Cloudflare Web Application Firewall
The Cloudflare Web Application Firewall (WAF) blocks more than 57 billion cyber threats per day. That is 650k blocked HTTP requests per second. The original code that filters this traffic was written by Cloudflare’s now CTO and the WAF has since received many accolades including the highest score for ability to execute in the 2020 Gartner Magic Quadrant for WAF.
Because we value replacing code when it is no longer as maintainable, performant, or scalable as it once was, we regularly rewrite key parts of the Cloudflare stack. That’s necessary as our enormous growth makes yesterday’s solutions unworkable. For some time, we have been working on replacing that original LuaJIT code John wrote with new code, written in Rust, along with an improved UI.
We are now excited to announce a new Cloudflare Web Application Firewall.
Starting today, 10% of newly created accounts on Cloudflare will be given access to the new WAF whenever a Pro plan zone or above is added. This percentage will increase to 100% of new accounts over the month of April, after which migration efforts will commence for existing customers. Enterprise customers may migrate early by contacting their account team.
What’s changing
The Web Application Continue reading
Playing games with Tensorflow
As a fun project, I recently built a web app to play checkers online against the computer. This post tries to outline the methodology I used. If you want to checkout the results, I would encourage you to try the web link above, change the difficulty level to ‘hard’ and play a round against the computer. You will be playing against a very simple neural network model that is, as far as I can tell, reasonably effective.
The standard approach to developing a game AI for something like board games is the “MiniMax” algorithm. Implementing “MiniMax” for a game like checkers is a relatively simple task; one needs to components:
- A method of generating valid moves for a play given a board position;
- A scorer function that evaluates the “goodness” of a given board position for a play;
There are multiple sets of possible rules for the game of checkers. I used the “Spanish draughts” rule set popular in Portugal: men move forward only; flying kings and mandatory moves on a 8×8 board. The minimax algorithm is independent of the particular rule-set used.
The scorer function must be able to look at a given player position and determine a score. Continue reading
Playing games with Tensorflow
As a fun project, I recently built a web app to play checkers online against the computer. This post tries to outline the methodology I used. If you want to checkout the results, I would encourage you to try the web link above, change the difficulty level to ‘hard’ and play a round against the computer. You will be playing against a very simple neural network model that is, as far as I can tell, reasonably effective.
The standard approach to developing a game AI for something like board games is the “MiniMax” algorithm. Implementing “MiniMax” for a game like checkers is a relatively simple task; one needs to components:
- A method of generating valid moves for a play given a board position;
- A scorer function that evaluates the “goodness” of a given board position for a play;
There are multiple sets of possible rules for the game of checkers. I used the “Spanish draughts” rule set popular in Portugal: men move forward only; flying kings and mandatory moves on a 8×8 board. The minimax algorithm is independent of the particular rule-set used.
The scorer function must be able to look at a given player position and determine a score. Continue reading
netsim-tools: Release 0.4 Is Out
TL&DR: The new release of netsim-tools includes unnumbered interfaces, configuration modules, and OSPF configuration.
In mid-March, we enjoyed another excellent presentation by Dinesh Dutt, this time focused on running OSPF in leaf-and-spine fabrics. He astonished me when he mentioned unnumbered Ethernet interfaces being available on all major network operating systems. It was time to test things out, and I wanted to use my networking simulation builder to build the test lab.
netsim-tools: Unnumbered Interfaces, Configuration Modules, OSPF
TL&DR: The new release of netsim-tools includes unnumbered interfaces, configuration modules, and OSPF configuration.
In mid-March, we enjoyed another excellent presentation by Dinesh Dutt, this time focused on running OSPF in leaf-and-spine fabrics. He astonished me when he mentioned unnumbered Ethernet interfaces being available on all major network operating systems. It was time to test things out, and I wanted to use my networking simulation builder to build the test lab.
TCP Congestion Control at IETF 110
IETF 110 was held virtually in March 2020. These are some notes I took on the topic of current research activities in the area of transport protocol flow control at the meeting of the Internet Congestion Control Research Group at that meeting.Don’t Be Complex When Simple Will Do
Let’s say you’re a consultant working on a couple of internet edge design projects.
In the first scenario, you are designing an internet connection for a factory.
- There are a few hundred workers who access AWS using the internet-as-WAN for critical apps related to factory operations.
- The factory is automated, and metrics related to production line health and performance are analyzed in AWS.
- There is an IoT network used for physical security that relies on an internet-based SaaS product to run reports and distribute alerts.
- A group of executives have offices at one end of the factory. Because of the pandemic, they don’t use them right now, but they do remotely access workstations with highly sensitive data that reside in those offices.
In the second scenario, you are designing an internet connection for an executive’s home.
- The executive has been working from home since the pandemic started, and finds the internet connection is unreliable for video calls. The video lags and gets pixelated. There are audio dropouts and audible jitter.
- The executive’s family members are also demanding internet users. The kids are in Zoom school. The spouse has a digital editing business and shares large files with clients.
Worth Reading: Learning without Burnout
We’re in an unfortunate industry where you can’t learn everything there’s to know in 3 years and keep doing the same stuff for the next 30 years… but how do you keep learning? Andrew Owen documented what works for him in Learning without Burnout.
Worth Reading: Learning without Burnout
We’re in an unfortunate industry where you can’t learn everything there’s to know in 3 years and keep doing the same stuff for the next 30 years… but how do you keep learning? Andrew Owen documented what works for him in Learning without Burnout.
Keyless SSL now supports FIPS 140-2 L3 hardware security module (HSM) offerings from all major cloud providers
Private encryption keys stored in hardware security module offerings from all major cloud providers can now be used to secure HTTPS connections at Cloudflare’s global edge.
Cloudflare generates, protects, and manages more SSL/TLS private keys than perhaps any organization in the world. Private keys must be carefully protected, as an attacker in possession of one can impersonate legitimate sites and decrypt HTTPS requests. To mitigate this risk, Cloudflare has strict key handling procedures and layers of isolation at the edge that are designed to safeguard keys at all costs. But for a small minority of customers with information security policies dictating where they can (or cannot) custody their keys, these protections do not meet their requirements.
It was for these customers that we first released Keyless SSL in 2014, a protocol we use extensively inside our network: all of the TLS handshakes per day established at the Cloudflare edge that take place in a process that has no access to our customers’ private keys. The data required to establish the session is instead sent to a separate system, where the necessary cryptographic signing operation is performed. For keys uploaded to or generated by Cloudflare, we manage this other system, Continue reading
Heartbleed Revisited


In 2014, a bug was found in OpenSSL, a popular encryption library used to secure the majority of servers on the Internet. This bug allowed attackers to abuse an obscure feature called TLS heartbeats to read memory from affected servers. Heartbleed was big news because it allowed attackers to extract the most important secret on a server: its TLS/SSL certificate private key. After confirming that the bug was easy to exploit, we revoked and reissued over 100,000 certificates, which highlighted some major issues with how the Internet is secured.
As much as Heartbleed and other key compromise events were painful for security and operations teams around the world, they also provided a learning opportunity for the industry. Over the past seven years, Cloudflare has taken the lessons of Heartbleed and applied them to improve the design of our systems and the resiliency of the Internet overall. Read on to learn how using Cloudflare reduces the risk of key compromise and reduces the cost of recovery if it happens.
Keeping keys safe
An important tenet of security system design is defense-in-depth. Important things should be protected with multiple layers of defense. This is why security-conscious people keep spare house Continue reading
Introducing: Advanced Certificate Manager
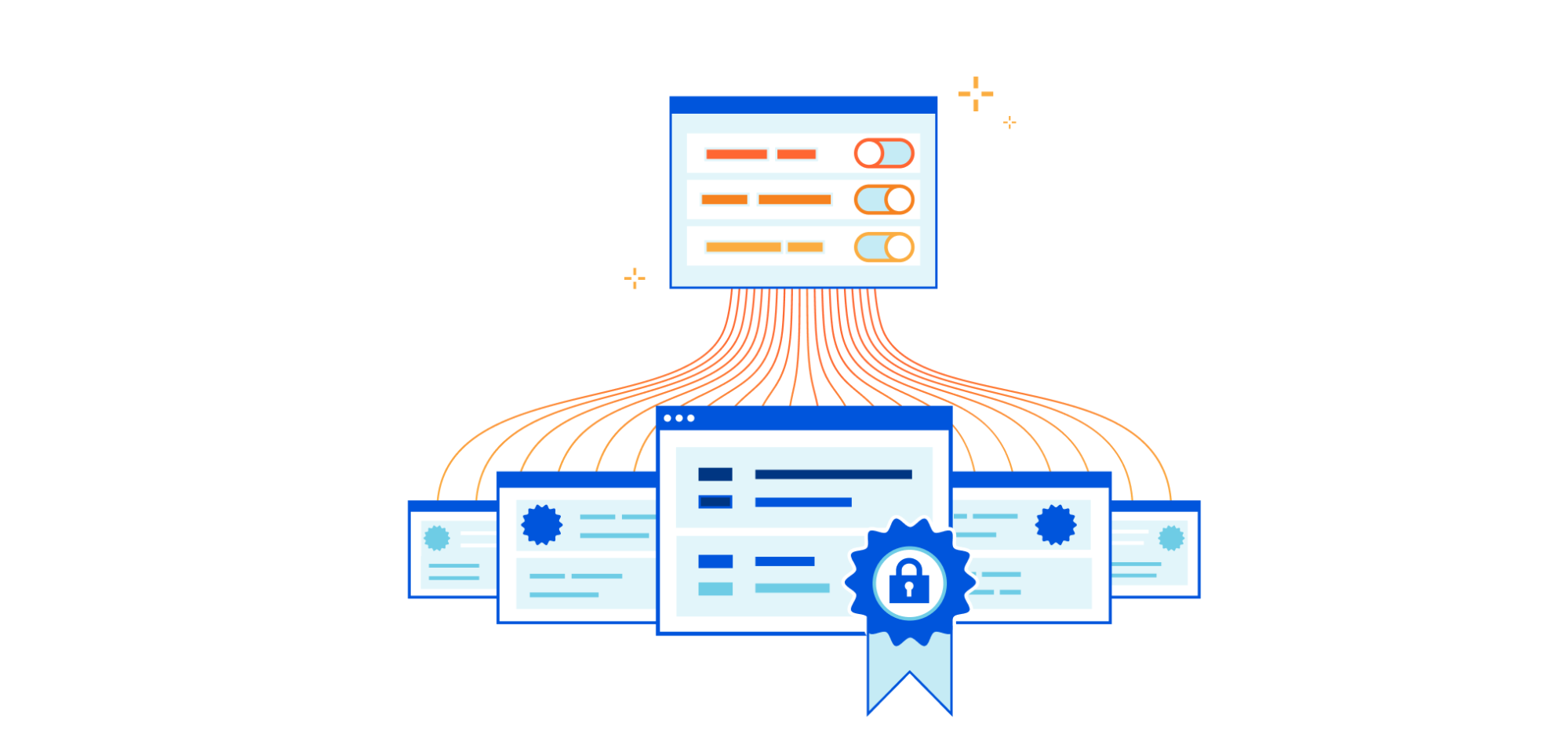
In 2016, we launched Dedicated Certificates. Today, we are excited to announce that dedicated certs are getting an upgrade… and a new name… introducing Advanced Certificate Manager! Advanced Certificate Manager is a flexible and customizable way to manage your certificates on Cloudflare.
Certificates
TLS Certificates are the reason you can safely browse the Internet, securely transfer money online, and keep your passwords private. They do that by encrypting your sensitive messages using public-key cryptography that is cryptographically linked to the certificate itself. But beyond that, TLS certificates are used to make an assertion about identity — verifying that the server is who they claim to be. Server Certificates — used by every website — include the website's name on the certificate and is issued by a third-party certificate authority (CA) who verifies that the certificate's information is correct and accurate.
Browsers only let you visit a website when it's encrypted using TLS after it has successfully validated the certificate presented by the server — much like how security checks your ID to board a plane.
We are focusing on securing the Internet now more than ever. We want to make it as easy as possible for any customer to be Continue reading
Worth Reading: Network Automation ChatBot with Discord
It’s amazing how easy it is to create a chatbot that will send messages to a Discord channel… just follow John Capobianco’s step by step tutorial.
Worth Reading: Network Automation ChatBot with Discord
It’s amazing how easy it is to create a chatbot that will send messages to a Discord channel… just follow John Capobianco’s step by step tutorial.