InfluxDB 2.0 released
InfluxData advances possibilities of time series data with general availability of InfluxDB 2.0 announced the production release of InfluxDB 2.0. This article demonstrates how to import sFlow data into InfluxDB 2.0 using sFlow-RT in order to provide visibility into network traffic.
Real-time network and system metrics as a service describes how to use Docker Desktop to replay previously captured sFlow data. Follow the instructions in the article to start an instance of sFlow-RT.
Create a directory for InfluxDB to use to store data and configuration settings:
mkdir dataNow start InfluxDB using the pre-built influxdb image:
docker run --rm --name=influxdb -p 8086:8086 \
-v $PWD/data:/var/lib/influxdb2 influxdb:alpine \
--nats-max-payload-bytes=10000000
Note: sFlow-RT is collecting metrics for all the sFlow agents embedded in switches, routers, and servers. The default value of nats-max-payload-bytes (1048576) may be too small to hold all the metrics returned when sFlow-RT is queried. The error, nats: maximum payload exceeded, in InfluxDB logs indicates that the limit needs to be increased. In this example, the value has been increased to 10000000.
Now access the InfluxDB web interface at http://localhost:8086/
The screen capture above shows three scrapers configured in InfluxDB 2.0:- sflow-analyzer
URL: http://host.docker.internal:8008/prometheus/analyzer/txt - sflow-metrics
Continue reading
App Modernization Goes Mainstream Again
The reality of modernization as a survival skill for business is seen in the way modernization has morphed from competitive advantage to mainstream initiative.Control web applications with two-clicks in Cloudflare Gateway

Nearly a year ago, we announced Cloudflare for Teams, Cloudflare’s platform for securing users, devices, and data. With Cloudflare for Teams, our global network becomes your team’s network, replacing on-premise appliances and security subscriptions with a single solution delivered closer to your users — wherever they work. Cloudflare for Teams centers around two core products: Cloudflare Access and Cloudflare Gateway.
Cloudflare Gateway protects employees from security threats on the Internet and enforces appropriate use policies. We built Gateway to help customers replace the pain of backhauling user traffic through centralized firewalls. With Gateway, users instead connect to one of Cloudflare’s data centers in 200 cities around the world where our network can apply consistent security policies for all of their Internet traffic.
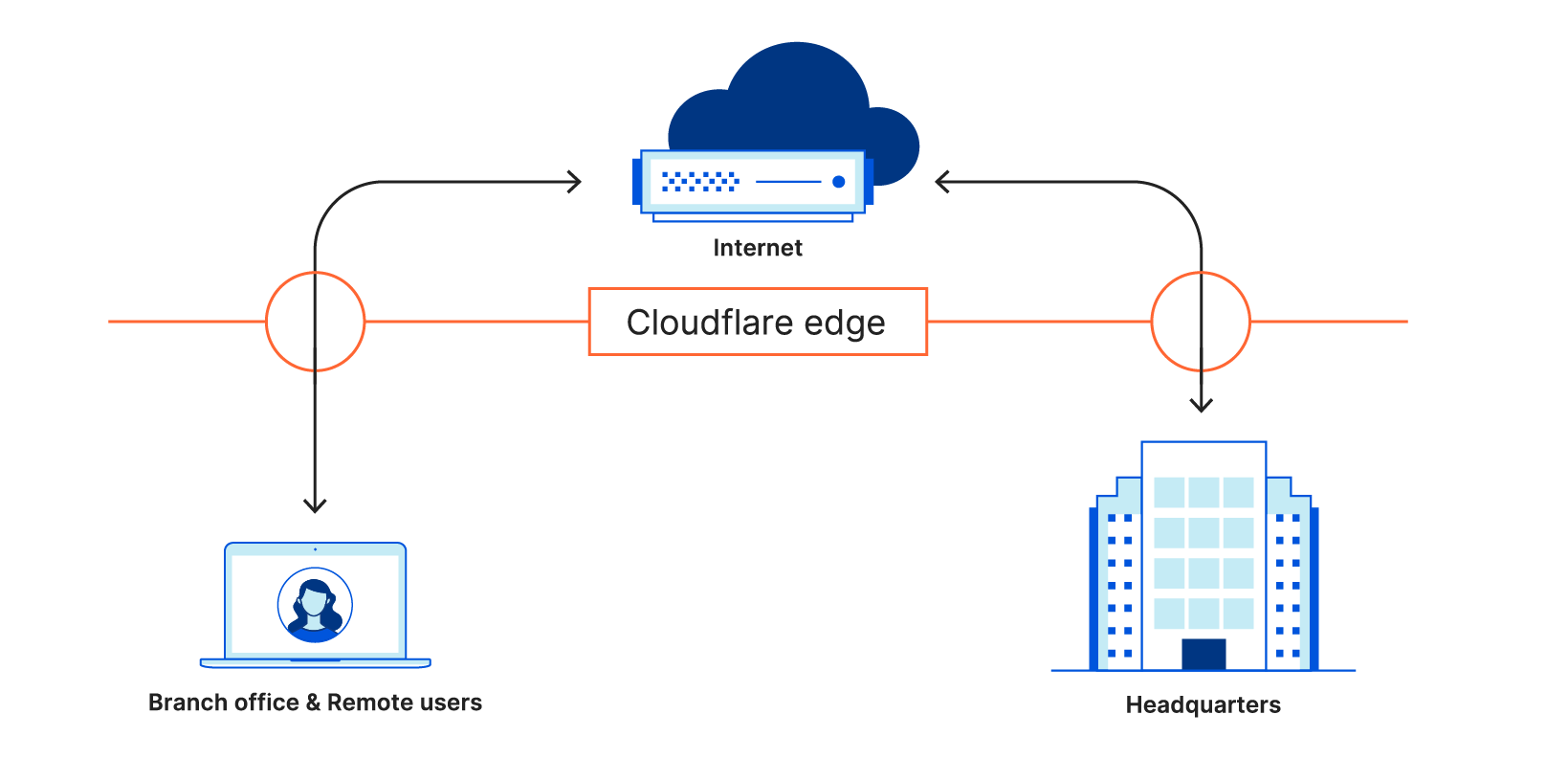
In March 2020, we launched Gateway’s first feature, a secure DNS filtering solution. With Gateway’s DNS filtering, administrators can click a single button to block known threats, like sources of malware or phishing sites. Policies can also be used to block specific risky categories, like gambling or social media. When users request a filtered site, Gateway stops the DNS query from resolving and prevents the device from connecting to a malicious destination or hostname with blocked material.
Tier 1 Carriers Performance Report: February, 2021
The post Tier 1 Carriers Performance Report: February, 2021 appeared first on Noction.
Interesting Tool: Schema Enforcer
It looks like JSON Schema is the new black. Last week I wrote about a new Ansible module using JSON Schema to validate data structures passed to it; a few weeks ago NetworkToCode released Schema Enforcer, a similar CLI tool (which means it’s easy to use it in any CI/CD pipeline).
Here are just a few things Schema Enforcer can do:
Interesting Tool: Schema Enforcer
It looks like JSON Schema is the new black. Last week I wrote about a new Ansible module using JSON Schema to validate data structures passed to it; a few weeks ago NetworkToCode released Schema Enforcer, a similar CLI tool (which means it’s easy to use it in any CI/CD pipeline).
Here are just a few things Schema Enforcer can do:
Tiling window manager
A couple of months ago it occurred to me that I’ve been manually tiling my windows. That is, I use all the screen real estate, and don’t have windows overlapping each other.
In various window manages (and on Windows) I have used Super+Left and Super+Right to divide the screen 50/50.
So why am I not running a tiling window manager? That’s literally what they do, and they allow more flexibility in how to tile, without wasting space.
Switching to tiling
A quick googling says that i3 is what I want. Fast, small, efficient. No bells and whistles.
I used it for a little while, but then because I wanted to make it even harder on myself, err… I mean to join the 21st century, I thought I’d switch from X11 to Wayland, too. Luckily there’s a Wayland Compositor that’s equilavent to the i3 Window Manager called Sway.
It’s great! I knew X11 and Gnome had issues, but I didn’t realize just how much better I feel when I don’t have to deal with their deficiencies.
Like:
- screen tearing when scrolling in terminal windows
- changing focus can take up to a second, sometimes
- X11 resets keyboard settings when it bloody feels Continue reading
Announcing the Final Candidate Slates for the 2021 Board of Trustees Elections

On behalf of the 2020-2021 Nominations Committee, I am pleased to announce the final slates of candidates for the 2021 Internet Society Board of Trustees elections.
Chapters Election
As announced to this community on March 1, we received the required number of signatures in support of Glenn McKnight’s petition to stand as a candidate in the Chapters election. No other petitions were filed for the Chapters election. Therefore, the final slate for the Chapters Election is as follows:
- Leiska Evanson
- Luis Martinez
- Glenn Carl McKnight
- Rao Naveed Bin Rais
- Muhammad Shabbir
- Niels ten Oever
Chapter voters will elect one trustee in the 2021 election.
Separately, the Board, acting pursuant to its authority under Article II, Section 1(d), of the Internet Society By-Laws, has announced its intention to offer the runner-up in the Chapters Election a one-year appointment as trustee. This will restore the board to its usual complement of 12 voting members comprised of equal numbers from all three communities: Chapters, Organizational Members and the IETF. The number of voting members fell to 11 when Olga Cavalli resigned with one year remaining in her term.
Organizational Members Election
There were no successful petitions in the Organizational Members election, so Continue reading
Tech Bytes: Manufacturer Taps Fortinet SD-WAN For IT/OT Convergence (Sponsored)
Dutch manufacturer Wavin wanted to securely connect offices and factories. The company turned to Fortinet SD-WAN to support its cloud-first strategy and converge its IT/OT security requirements. Fortinet is the sponsor for this Tech Byte episode, and our guest from Wavin is Gerben Bremmer, Manager Networking Services EMEA.
The post Tech Bytes: Manufacturer Taps Fortinet SD-WAN For IT/OT Convergence (Sponsored) appeared first on Packet Pushers.
Tech Bytes: Manufacturer Taps Fortinet SD-WAN For IT/OT Convergence (Sponsored)
Dutch manufacturer Wavin wanted to securely connect offices and factories. The company turned to Fortinet SD-WAN to support its cloud-first strategy and converge its IT/OT security requirements. Fortinet is the sponsor for this Tech Byte episode, and our guest from Wavin is Gerben Bremmer, Manager Networking Services EMEA.On Using the Right Word
A while back, I was sitting in a meeting where the presenter described switching from a “traditional, hierarchical data center fabric” to a spine-and-leaf (while drawing CLOS, in all capital letters, on the whiteboard). He pointed out that the spine-and-leaf design is simpler because it only has two tiers rather than three.
There is so much wrong with this I almost winced in physical pain. Traditional hierarchical designs are not fabrics. Spine-and-leaf fabrics are not CLOS, but Clos, fabrics. Clos fabrics have three stages, not two—even if we draw them “folded” so you only see two apparent levels to the fabric. In fact, all spine-and-leaf fabrics always have an odd number of stages, and they are stages, not tiers.
More recently, I heard someone talking about an operating system that was built using microservices. I thought—“that would be at neat trick.” To build something with microservices does not just mean a piece of software using modules—this would be modular application (or operating system) design. Microservices architectures break the application up into the most basic components possible and then scale each kind of component out (rather than up) by spinning new copies of each service as needed. I cannot imagine Continue reading
Not the Encryption Apocalypse…Yet

“This destroys the RSA cryptosystem.”
That is the last sentence in the abstract of a new, preliminary, dense mathematical paper published by renowned mathematician Claus Peter Schnorr. If this turns out to be true, it will mean bad news for anybody who relies on the underpinnings of encryption – which is everyone!
The paper, posted as a pre-print, meaning it is a draft paper that must undergo academic peer review, claims it has found an algorithm that significantly speeds up a particular kind of mathematical problem called factorization. Factorization is the process of finding two numbers that, when multiplied together, provide the given number. For example, calculating 23 x 29 is easy. (Try it yourself.) But factorizing 437 – finding the two numbers that multiply together to make 437 – will take anybody a bit of time. (It’s 19 x 23 by the way.)
Schnorr claims that he has found a way to significantly speed up the calculation needed to perform factorization – a claim that is currently widely disputed. Supposedly, his method will factor a number with roughly 260 digits about ten trillion times faster than previous methods.
Does Math Matter?
Factorization is the mathematical puzzle Continue reading
Network Break 323: Google To Swap 3rd-Party Cookies For Cohorts; Attackers Exploit On-Prem Exchange
This week's Network Break checks the fine print on a Google pledge to phase out third-party cookie tracking, examines a serious attack against Microsoft Exchange servers, dives into HPE's latest financial results, and analyzes more tech news.
The post Network Break 323: Google To Swap 3rd-Party Cookies For Cohorts; Attackers Exploit On-Prem Exchange appeared first on Packet Pushers.
Network Break 323: Google To Swap 3rd-Party Cookies For Cohorts; Attackers Exploit On-Prem Exchange
This week's Network Break checks the fine print on a Google pledge to phase out third-party cookie tracking, examines a serious attack against Microsoft Exchange servers, dives into HPE's latest financial results, and analyzes more tech news.The Week in Internet News: Lawmakers Point to ‘Extremist’ Content on YouTube

Extreme video: A group of Democratic lawmakers in the U.S. has demanded that YouTube explain its policies related to dealing with extremist content, Yahoo News reports. “Incendiary content that indoctrinates, radicalizes, and mobilizes extremists continues to flourish” on YouTube, the lawmakers wrote.
Blaming encryption: Meanwhile, a new government report on possible extremist attacks on the U.S. Capitol says information on future plans are becoming harder to find because militia groups have shifted to encryption tools, Axios reports. U.S. law enforcement authorities appear to be trying to resurrect their calls for encryption backdoors even as extremist groups post information on public websites like YouTube.
Blaming the website: The U.S. isn’t the only government looking to hold websites more responsible for user-generated content. India’s information technology ministry has finalized a set of rules intended to make online service providers more accountable for their users’ bad behavior, Brookings.edu notes. The Brookings blog post suggests that this effort, mirrored by a similar debate in the U.S., will be a grave threat to free speech and privacy rights.
Clamping down: Meanwhile basic rights in 10 African countries are threatened by a trend toward digital authoritarianism, according to a Continue reading
The benefits of serving stale DNS entries when using Consul
Introduction

We use Consul for service discovery, and we’ve deployed a cluster that spans several of our data centers. This cluster exposes HTTP and DNS interfaces so that clients can query the Consul catalog and search for a particular service and the majority of the clients use DNS. We were aware from the start that the DNS query latencies were not great from certain parts of the world that were furthest away from these data centers. This, together with the fact that we use DNS over TLS, results in some long latencies. The TTL of these names being low makes it even more impractical when resolving these names in the hot path.
The usual way to solve these issues is by caching values so that at least subsequent requests are resolved quickly, and this is exactly what our resolver of choice, Unbound, is configured to do. The problem remains when the cache expires. When it expires, the next client will have to wait while Unbound resolves the name using the network. To have a low recovery time in case some service needs to failover and clients need to use another address we use a small TTL (30 seconds) Continue reading
VoIP Packet Fight: Troubleshooting Phone Initialization Problems
Using a Profitap/ProfiShark tap to understand why VoIP phones got stuck on initializing, we could find a workaround to get things up and running.Happy International Women’s Day!
Here at Cloudflare, we’re thrilled to celebrate International Women’s Day today! We have tons of events planned throughout the month of March, which is our way of honoring Women’s Empowerment Month. We’ll be making sure we acknowledge women’s achievements, raise awareness about women’s equality, and lobby for accelerated gender parity — Cloudflare style.
We take the International Women’s Day initiatives and its calls to action seriously. Then again, how could we not? The latest 2020 Global Gender Gap Report from the World Economic Forum indicates that it’ll take another 257 years to close the gender gap, if we continue at our current pace of progress. It’s going to take all of us to make a positive impact and accelerate the reality of a gender equal world.
Introducing Womenflare
Before we dive further into how we’re planning to celebrate International Women’s Day and Women’s Empowerment Month, we’d like to introduce ourselves. We’re Womenflare — Cloudflare’s Employee Resource Group (ERG) for all who identify as and advocate for women (Talea and Angela are the global Womenflare leads and John is the Womenflare executive advocate). We launched Womenflare on International Women’s Day in 2020, and it was one of the last things we Continue reading

