Tech Field Day Changed My Life

It’s amazing to me that it’s been ten years since I attended by first Tech Field Day event. I remember being excited to be invited to Tech Field Day 5 and then having to rush out of town a day early to beat a blizzard to be able to attend. Given that we just went through another blizzard here I thought the timing was appropriate.
How did attending an industry event change my life? How could something with only a dozen people over a couple of days change the way I looked at my career? I know I’ve mentioned parts of this to people in the past but I feel like it’s important to talk about how each piece of the puzzle built on the rest to get me to where I am today.
Voices Carry
The first thing Tech Field Day did to change my life was to show me that I mattered. I grew up in a very small town and spent most of my formative school years being bored. The Internet didn’t exist in a usable form for me. I devoured information wherever I could find it. And I languished as I realized that I needed more Continue reading
Using HPKE to Encrypt Request Payloads
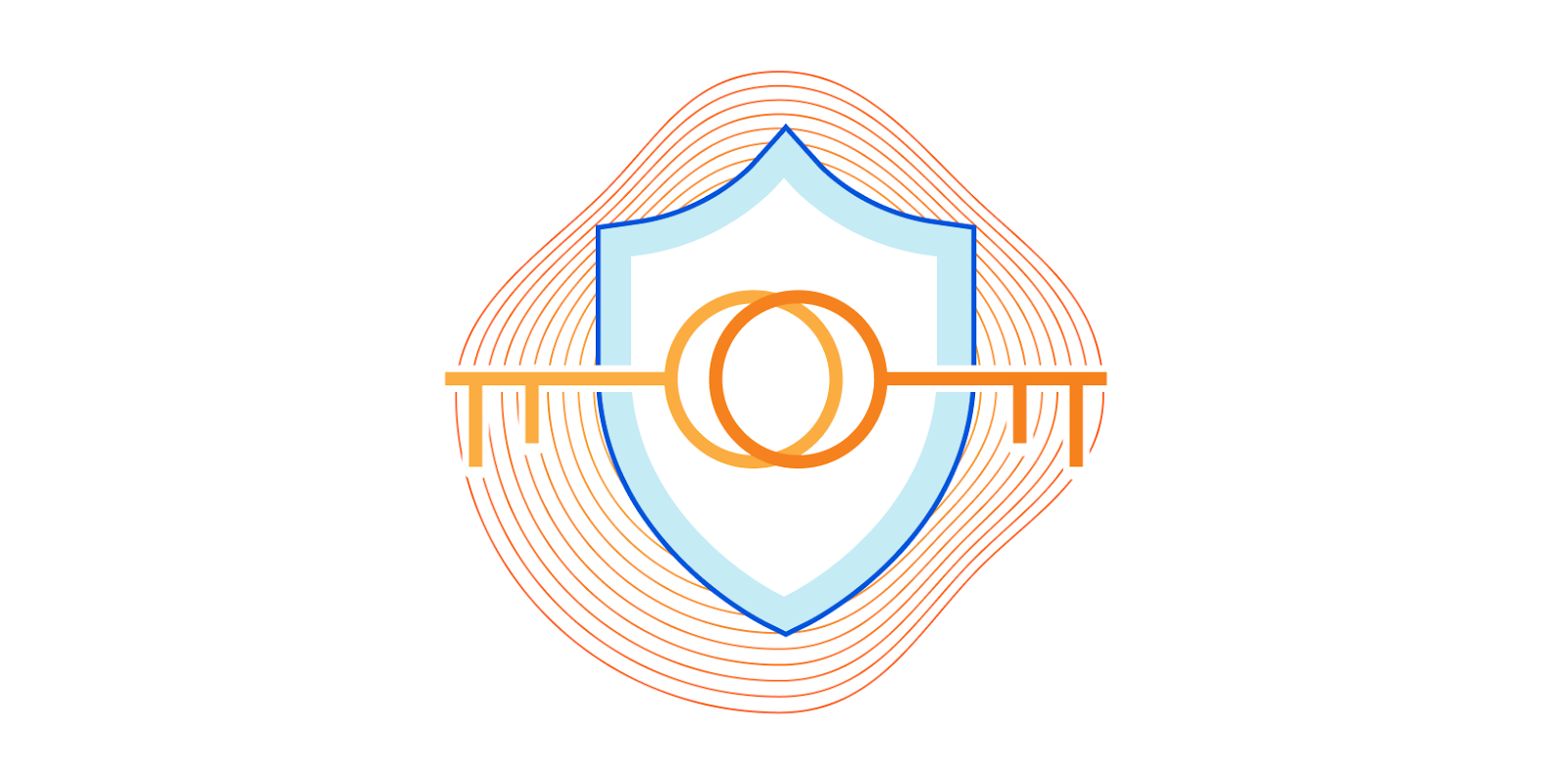
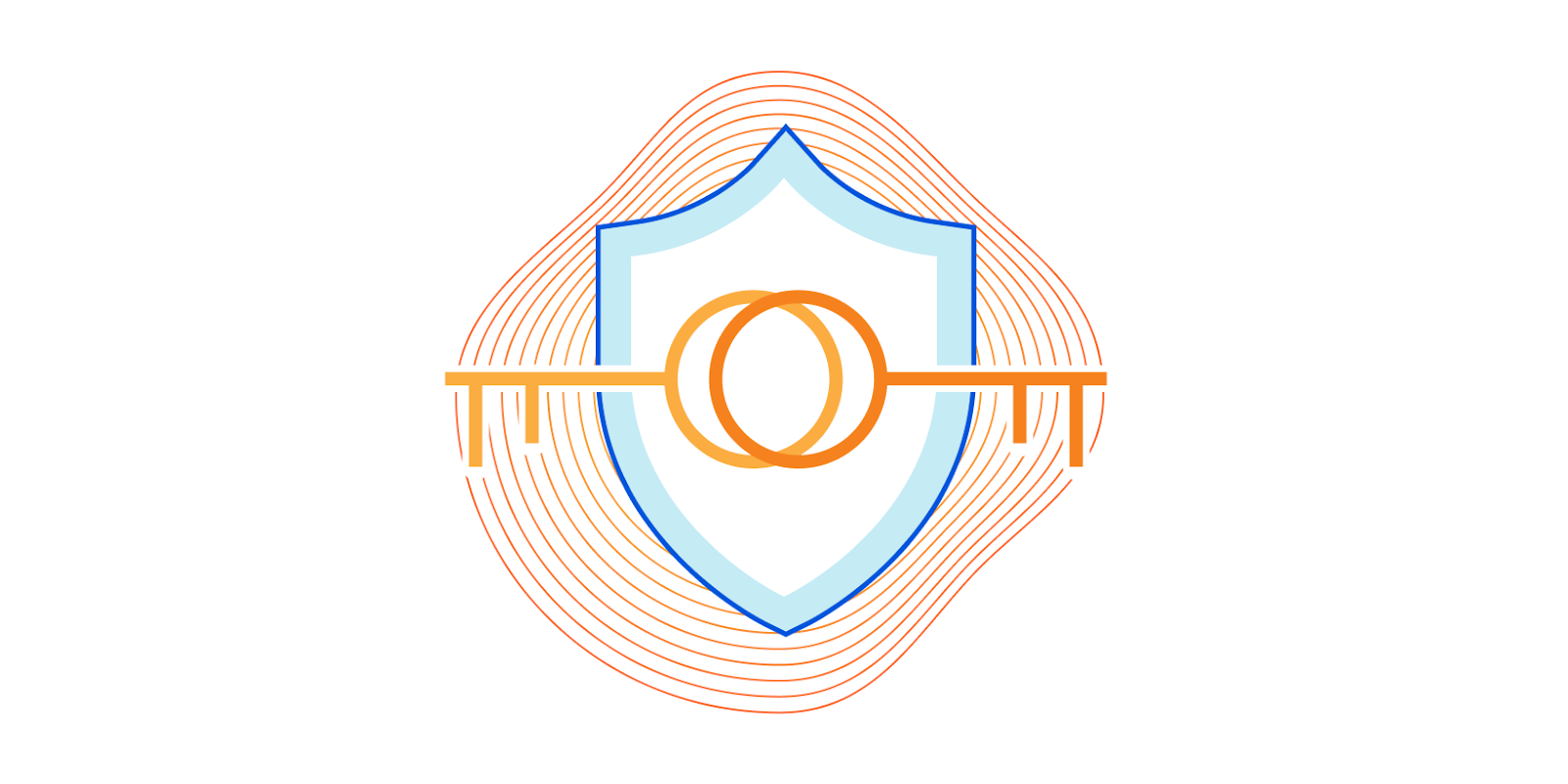
The Managed Rules team was recently given the task of allowing Enterprise users to debug Firewall Rules by viewing the part of a request that matched the rule. This makes it easier to determine what specific attacks a rule is stopping or why a request was a false positive, and what possible refinements of a rule could improve it.
The fundamental problem, though, was how to securely store this debugging data as it may contain sensitive data such as personally identifiable information from submissions, cookies, and other parts of the request. We needed to store this data in such a way that only the user who is allowed to access it can do so. Even Cloudflare shouldn't be able to see the data, following our philosophy that any personally identifiable information that passes through our network is a toxic asset.
This means we needed to encrypt the data in such a way that we can allow the user to decrypt it, but not Cloudflare. This means public key encryption.
Now we needed to decide on which encryption algorithm to use. We came up with some questions to help us evaluate which one to use:
- What requirements do we have for Continue reading
How Software Defined Packet Brokers Can Improve Network Observability
Network Packet Brokers (NPBs) can be valuable in improving network visibility and observability for both network operations (NetOps) and security...
The post How Software Defined Packet Brokers Can Improve Network Observability appeared first on Pluribus Networks.
Podcast: State of Networking (Early 2021)
In January, Jason Edelman kindly invited me for a chat about the state of (software defined) networking and network automation in particular. The recording was recently published on Network Collective.
Podcast: State of Networking (Early 2021)
In January, Jason Edelman kindly invited me for a chat about the state of (software defined) networking and network automation in particular. The recording was recently published on Network Collective.
Introducing: Smarter Tiered Cache Topology Generation
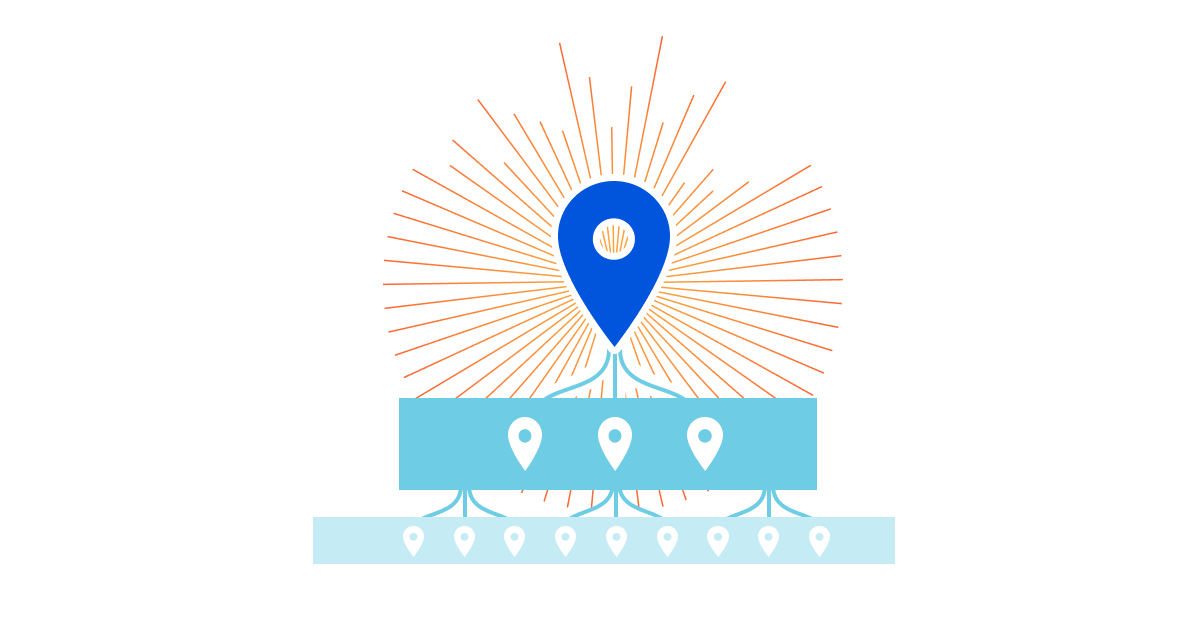
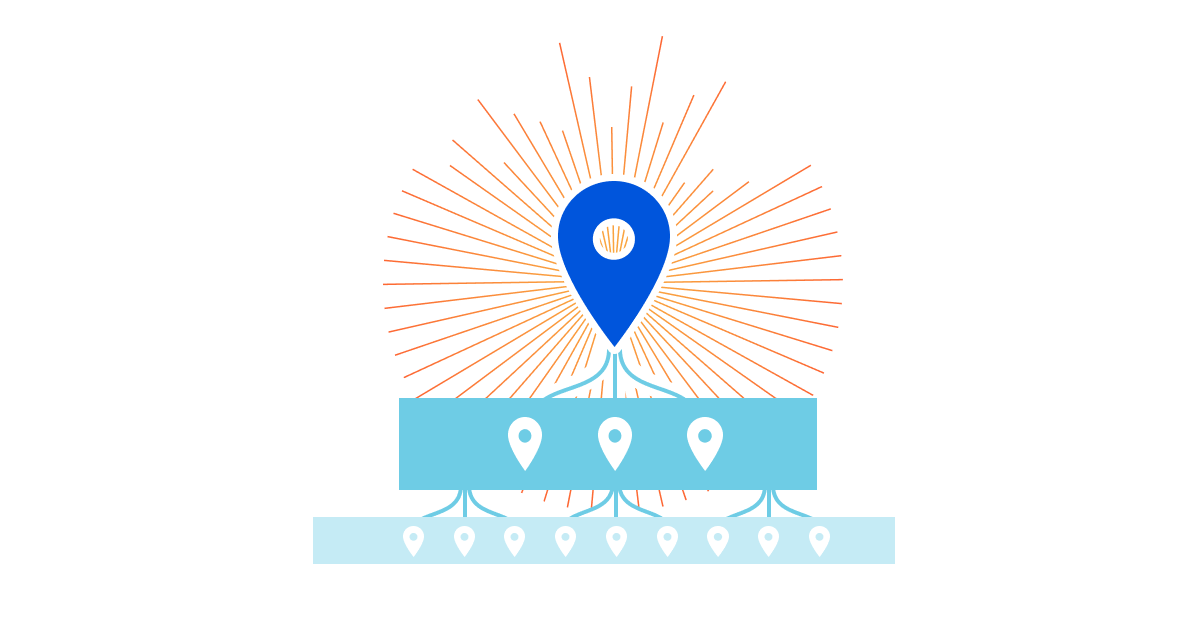
Caching is a magic trick. Instead of a customer’s origin responding to every request, Cloudflare’s 200+ data centers around the world respond with content that is cached geographically close to visitors. This dramatically improves the load performance for web pages while decreasing the bandwidth costs by having Cloudflare respond to a request with cached content.
However, if content is not in cache, Cloudflare data centers must contact the origin server to receive the content. This isn’t as fast as delivering content from cache. It also places load on an origin server, and is more costly compared to serving directly from cache. These issues can be amplified depending on the geographic distribution of a website’s visitors, the number of data centers contacting the origin, and the available origin resources for responding to requests.
To decrease the number of times our network of data centers communicate with an origin, we organize data centers into tiers so that only upper-tier data centers can request content from an origin and then they spread content to lower tiers. This means content that loads faster for visitors, is cheaper to serve, and reduces origin resource consumption.
Today, I’m thrilled to announce a fundamental improvement to Argo Continue reading
Tiered Cache Smart Topology
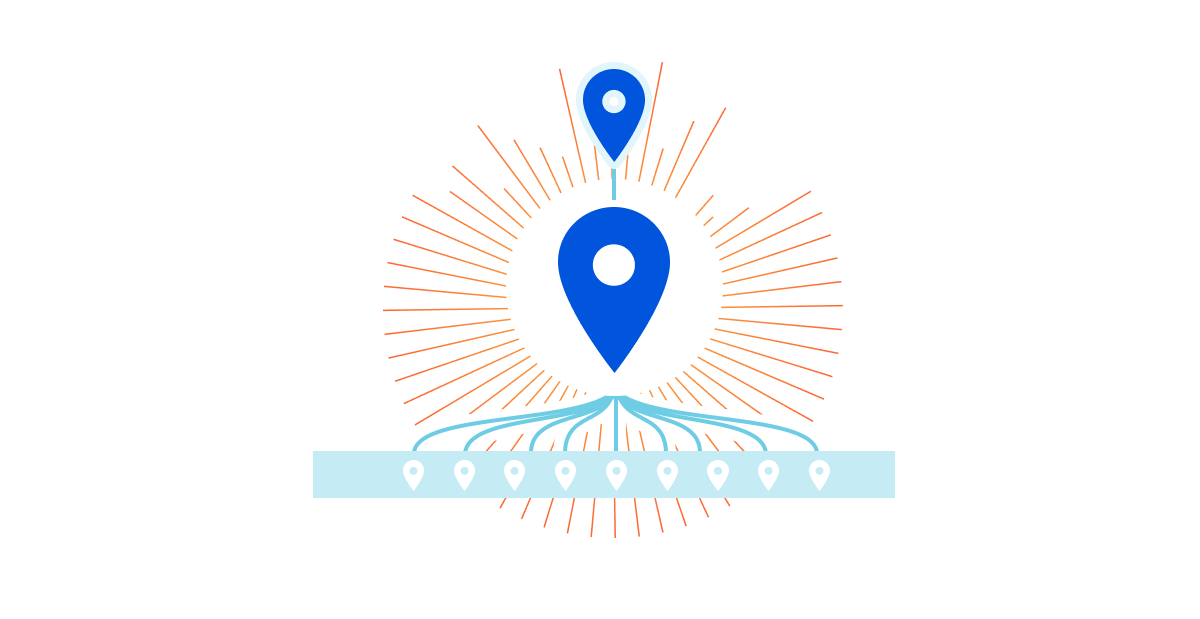
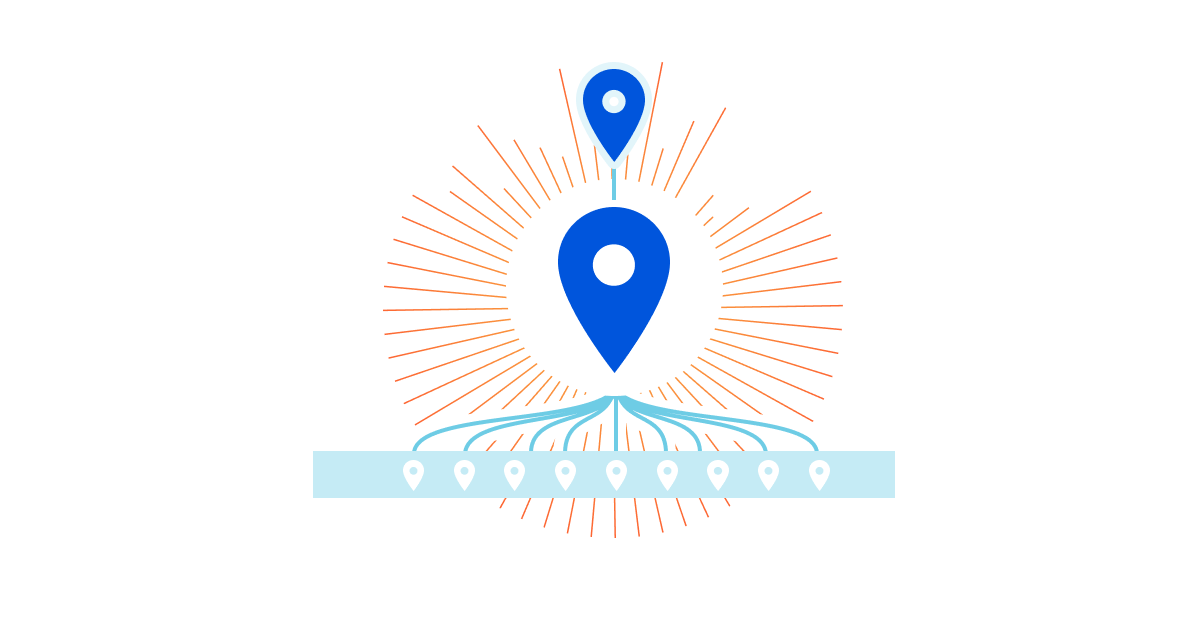
A few years ago, we released Argo to help make the Internet faster and more efficient. Argo observes network conditions and finds the optimal route across the Internet for origin server requests, avoiding congestion along the way.
Tiered Cache is an Argo feature that reduces the number of data centers responsible for requesting assets from the origin. With Tiered Cache active, a request in South Africa won’t go directly to an origin in North America, but, instead, look in a large, nearby data center to see if the data requested is cached there first. The number and location of the data centers used by Tiered Cache is controlled by a piece of configuration called the topology. By default, we use a generic topology for every customer that strikes a balance between cache hit ratios and latency that is suitable for most users.
Today we’re introducing Smart Topology, which maximizes cache hit ratios by building on Argo’s internal infrastructure to identify the single best data center for making requests to the origin.
Standard Cache
The standard method for caching assets is to let each data center be a reverse proxy for the origin server. In this scheme, a miss in any Continue reading
How to fix Wi-Fi interference
Since Wi-Fi transmits over the airwaves, it’s of course much more susceptible to interference than the wired network. There can be interference from your own network or neighbor's, non-Wi-Fi wireless devices, microwaves, and even radar systems. Because there are so many possibilities, tracking down or fixing the interference can be quite a task, but knowing where to start can help.
The symptoms of interference issues can easily be mistaken for symptoms of other, more apparent problems such as poor Wi-Fi coverage. If so, maybe you blindly add more access points (AP) and, not knowing that you already had interference, that can actually cause more interference. So, try to find the root causes of any symptoms and be very intentional about the changes you make.
How to fix Wi-Fi interference
Since Wi-Fi transmits over the airwaves, it’s of course much more susceptible to interference than the wired network. There can be interference from your own network or neighbor's, non-Wi-Fi wireless devices, microwaves, and even radar systems. Because there are so many possibilities, tracking down or fixing the interference can be quite a task, but knowing where to start can help.
The symptoms of interference issues can easily be mistaken for symptoms of other, more apparent problems such as poor Wi-Fi coverage. If so, maybe you blindly add more access points (AP) and, not knowing that you already had interference, that can actually cause more interference. So, try to find the root causes of any symptoms and be very intentional about the changes you make.
How to fix Wi-Fi interference
Since Wi-Fi transmits over the airwaves, it’s of course much more susceptible to interference than the wired network. There can be interference from your own network or neighbor's, non-Wi-Fi wireless devices, microwaves, and even radar systems. Because there are so many possibilities, tracking down or fixing the interference can be quite a task, but knowing where to start can help.
The symptoms of interference issues can easily be mistaken for symptoms of other, more apparent problems such as poor Wi-Fi coverage. If so, maybe you blindly add more access points (AP) and, not knowing that you already had interference, that can actually cause more interference. So, try to find the root causes of any symptoms and be very intentional about the changes you make.
Book Updates 0221
Someone recently asked me to suggest a list of books on thinking skills; I figured others might be interested in the list, as well, so … I decided to post it here. Further, I’ve added a few books to my “recommended book list” here on rule11; I thought I’d point those out, as well. My first suggestion, of course, is that if you want to improve your thinking skills, read. I don’t just mean technical stuff, I mean all over the place, in the form of books, and a lot.
So, forthwith, some more things to read.
Thinking Books
- Algorithms in a Nutshell
- The Inquiring Mind
- What Tech Calls Thinking
- Unintended Features
- The Elements of Reasoning
- Deep Work
- Being Logical
Recently Added Books
- From Counterculture to Cyberculture
- Escape from Reason
- The Rise and Triumph of the Modern Self
- Death in the City
- Rational Cybersecurity
- The Age of Access
- Curing Mad Truths
- Called to Freedom
You can find my list of recommended books here, and my goodreads profile, which lists a lot of the books I’ve read, I’m currently reading, and plan to read, here.
The Hedge #71: Nick Russo and Automating Productivity
When we think of automation—and more broadly tooling—we tend to think of automating the configuration, monitoring, and (possibly) the monitoring of a network. On the other hand, a friend once observed that when interviewing coders, the first thing he asked was about the tools they had developed and used for making themselves more efficient. This “self-tooling” process turns out to be important not just to be more efficient at work, but to use time more effectively in general. Join Nick Russo, Eyvonne Sharp, Tom Ammon, and Russ White as we discuss self-tooling.
Zodiac FX Gets a 3D Printed Case
Not content with having dug the Northbound Networks Zodiac FX out of a pile of overlooked technology in my office, I thought that the poor thing desperately needed to have a case to sit in. When I originally received the switch, I did not have a 3D printer and had no idea what it would take to make a case; now though, I do have a 3D printer … and no idea what it would take to make a case. Sounds like a plan to me!
Measuring the Zodiac FX
The most important tool I bought to go with my 3D printer (a Creality CR6-SE) was some digital calipers. I discovered early on how important it was to ensure that if I was going to screw up, I should be able to screw up accurately.

These calipers are made by RexBeti, and if you’ve never heard of that company that’s ok, because before I purchased this I hadn’t either. The calipers claim to be accurate to 0.01mm, but I don’t have any way to validate that claim, so let’s just assume that they are. I do know that it beats using a ruler. A few minutes of careful Continue reading
Response: Global Internet Map Map 2021
 Bandwidth map of global internet
Bandwidth map of global internet