Day Two Cloud 066: Cloud Computing At The Edge(s)
Mark Thiele joins the Day Two Cloud podcast to school us on all things edge. He argues that edge is more than a buzzword, with a specific set of opportunities and challenges for IT operations and infrastructure.What Will the Internet Look Like in 2030? New Grants Program for Researchers Studying the Future of the Internet

From the environment to the economy, the Internet is reshaping and disrupting several sectors of our society. What might future patterns of disruption look like? How will these changes affect all of us, particularly those on the margins of society? What new solutions can we generate today, to address the challenges of tomorrow?
At the Internet Society Foundation, we believe the answers to these questions and many others lies in research. That’s why we’re thrilled to announce a new grants program supporting researchers worldwide who are studying the future and sustainability of the Internet. Grants of up to US$200,000 are available for research lasting up to two years and focused in one of two categories:
- Greening the Internet: How the Internet affects and is affected by the environment
- The Internet Economy: How digital technologies are transforming our economic landscape
Established in 2019 to support the positive difference the Internet can make to people everywhere, the Internet Society Foundation awards grants to Internet Society Chapters/Special Interest Groups (SIGs) as well as nonprofit organizations and individuals dedicated to providing meaningful access to an open, globally-connected, secure, and trustworthy Internet for everyone.
Learn more about future calls for Continue reading
Moobot vs. Gatebot: Cloudflare Automatically Blocks Botnet DDoS Attack Topping At 654 Gbps
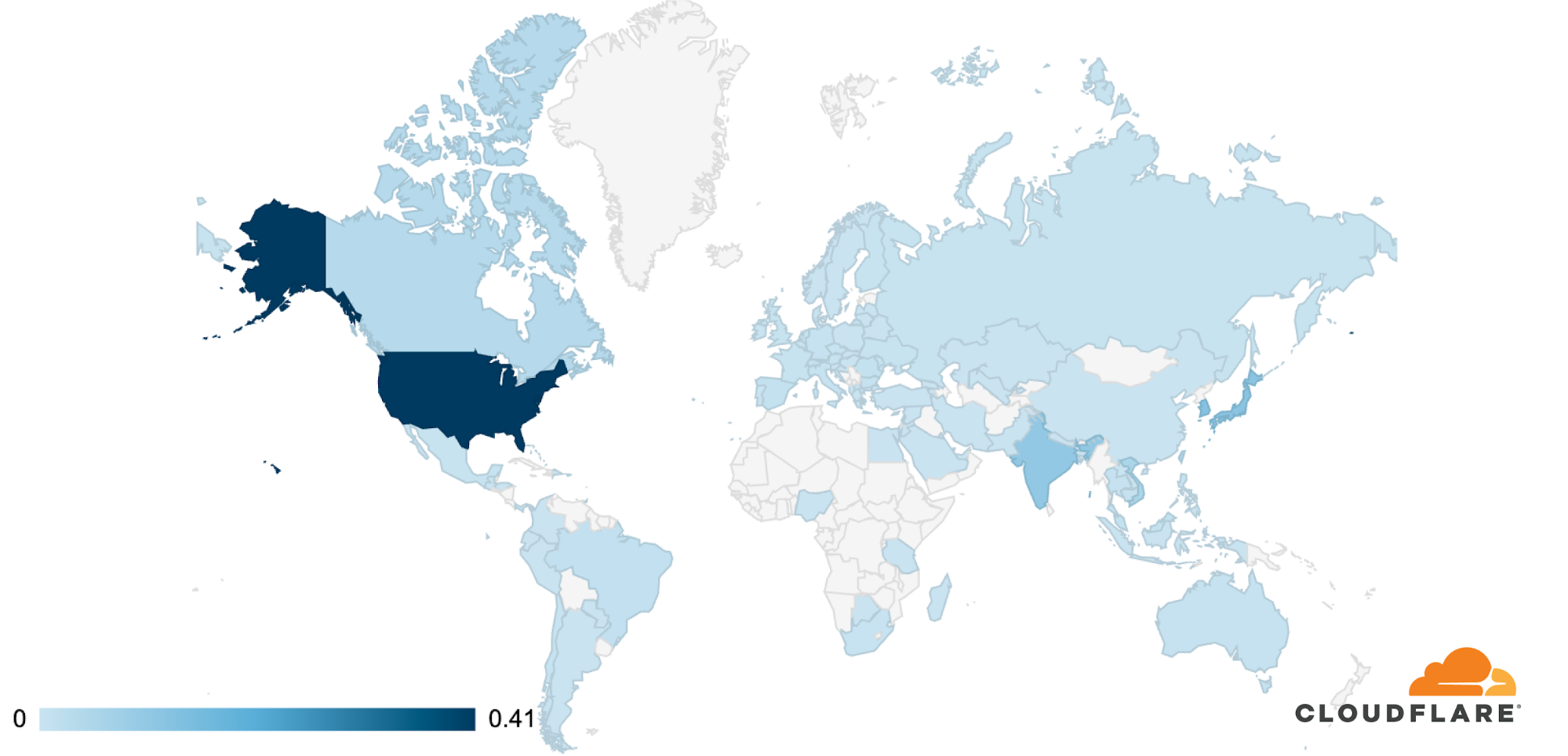
On July 3, Cloudflare’s global DDoS protection system, Gatebot, automatically detected and mitigated a UDP-based DDoS attack that peaked at 654 Gbps. The attack was part of a ten-day multi-vector DDoS campaign targeting a Magic Transit customer and was mitigated without any human intervention. The DDoS campaign is believed to have been generated by Moobot, a Mirai-based botnet. No downtime, service degradation, or false positives were reported by the customer.
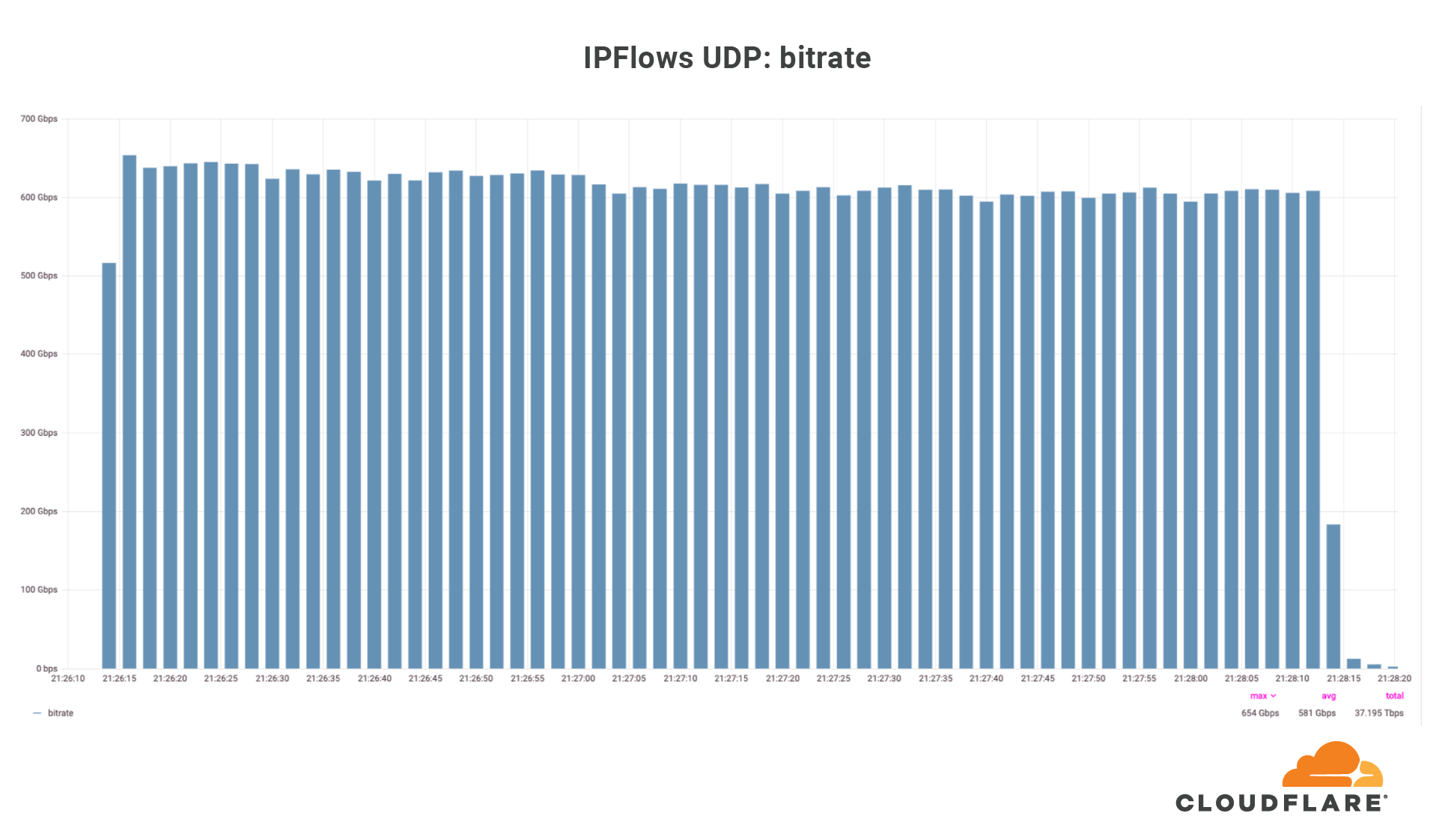
Over those ten days, our systems automatically detected and mitigated over 5,000 DDoS attacks against this one customer, mainly UDP floods, SYN floods, ACK floods, and GRE floods. The largest DDoS attack was a UDP flood and lasted a mere 2 minutes. This attack targeted only one IP address but hit multiple ports. The attack originated from 18,705 unique IP addresses, each believed to be a Moobot-infected IoT device.
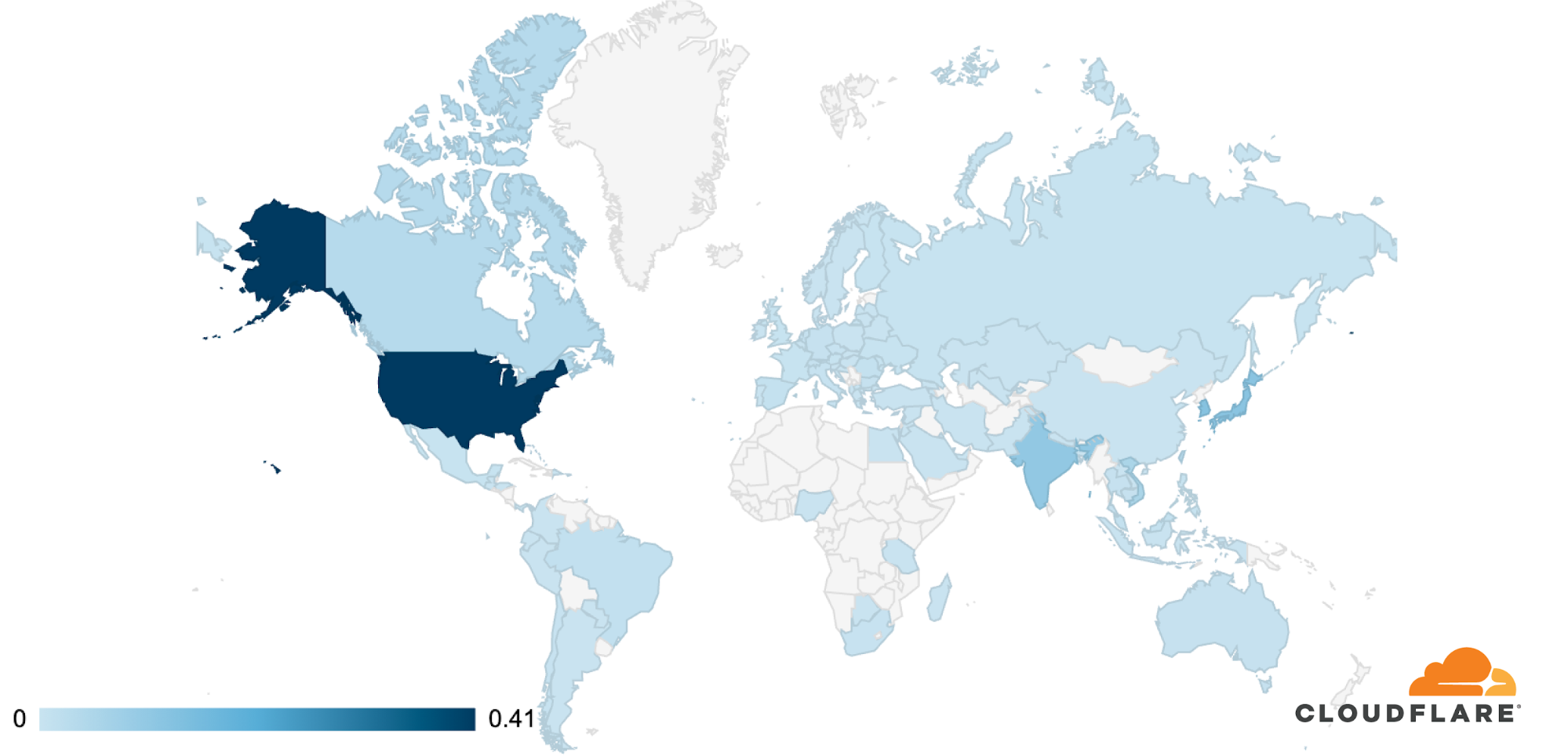
The attack was observed in Cloudflare’s data centers in 100 countries around the world. Approximately 89% of the attack traffic originated from just 10 countries with the US leading at 41%, followed by South Korea and Japan in second place (12% each), Continue reading
Restoring data to Netbox Docker
Having just shot myself in the foot by deleting docker and losing a container I had been working on, here is the command to restore data to netbox-docker’s Postgres database:
sudo docker exec -i netbox-docker_postgres_1 psql --username netbox netbox < /path/to/backup/file.sql
Phew…
Why Don’t We Have Dynamic Firewall Policies
One of the readers of the Considerations for Host-Based Firewalls blog post wrote this interesting comment:
Perhaps a paradigm shift is due for firewalls in general? I’m thinking quickly here but wondering if we perhaps just had a protocol by which a host could request upstream firewall(s) to open access inbound on their behalf dynamically, the hosts themselves would then automatically inform the security device what ports they need/want opened upstream.
Well, we have at least two protocols that could fit the bill: Universal Plug and Play and Port Control Protocol (RFC 6887).
Deloitte on Cloud, the Edge, and Enterprise Expectations
As technology matures to be cheaper, faster, and more powerful, it creates new possibilities with micro data centers and AI chips at the edge.A summary of High Speed Ethernet ASICs
There is a lot going on in the field of the highest speed network ASICs. These are focused on very high speed, less features, and lower buffers, driven by the hyperscalers and the Financial industry which desires the lowest latency switching. This is a rich area that I can’t cover...SD-LAN Helps Mitigate Smart Building Physical Cybersecurity Risks
The mitigation of smart building cyber security risk is shaping up to be one of the key driving factors that propels SD-LAN technologies into the mainstream.Member News: Kyrgyzstan Chapter Focuses on Online Resources for Schools

Library access: The Kyrgyzstan Chapter of the Internet Society has started work on version 2.0 of its ilimBox project, an online educational platform for teachers and students. The ilimBox device, now powered by the Raspberry Pi 4, will include new educational videos, audio, and text resources. IlimBox is a digital library for schools and public libraries, containing Wikipedia in Kyrgyz, Russian, and English, the Khan Academy electronic library in English, and thousands of video lessons, audio, and electronic books. All these digital training materials can be used offline, with users not needing immediate access to the Internet, although the library also connects to services through WiFi. As of last November, about 100 schools in Kyrgyzstan had installed ilimBox.
Building a better network: The Ghana Chapter has a post on efforts to improve the wireless network at Ho Technical University, and the author credited training from the Internet Society on community networks in helping him sort out problems with the network there. The campus network “had a lot of issues such rogue DHCP servers and IP address conflicts,” the author noted.
Algorithmic privacy: The Commission for the Protection of Privacy in Canada has given a grant to the Quebec Chapter Continue reading
The History of Comm Servers with Kevin Herbert
Communication Servers designed to support hundreds or thousands of users reached their peak capabilities just as dial-up service access began to recede in importance. In fact, many network engineers today have probably never managed a dial-up communications server, which were once used to connect everything from individual users to services like AOL and remote workers to entire sites (hence OSPF’s demand circuit capability). Kevin Herbert joins us to discuss the early work on communication servers, including some of the challenges of working with early networking hardware.
Three Ways Operationalizing NSX Will Transform Your IT Organization
By Kevin Lees and Devyani Pisolkar, authors of the ‘Operationalizing VMware NSX’ guide
Virtualized networking and security may appear to be a standard feature of today’s modern data center, but it wasn’t so long ago — what, seven years? — that network virtualization was a new concept, largely introduced and propelled by VMware. How time flies. Today, across industries, network virtualization, in the form of VMware NSX, is the go-to choice for delivery of software-based network and security services. Nowadays we spend less time discussing the novelty of the architecture and more time talking about how to maximize the value of NSX by fully operationalizing the platform to make it a critical driver in your digital transformation.
VMware NSX is utterly unlike legacy networking
VMware NSX delivers networking and security services entirely in software. That enables organizations to move myriad operational tasks into the software layer, but to leverage it fully requires a top-to-bottom rethink of network operation itself. Under NSX, the old paradigm of the network as a hardware silo is gone; instead, the virtualized NSX network is an integral component in the software-defined data center.
Which brings us to the key point: in order to fully realize Continue reading
Secondary DNS – Deep Dive
How Does Secondary DNS Work?
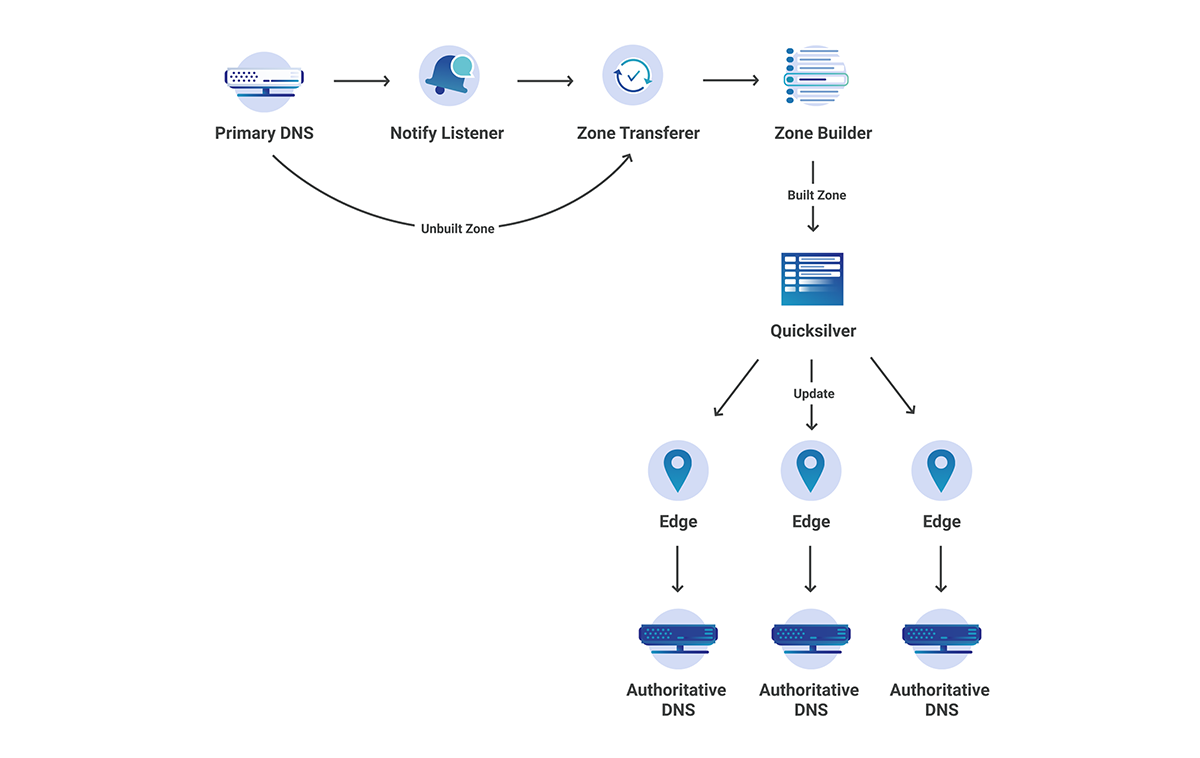
If you already understand how Secondary DNS works, please feel free to skip this section. It does not provide any Cloudflare-specific information.
Secondary DNS has many use cases across the Internet; however, traditionally, it was used as a synchronized backup for when the primary DNS server was unable to respond to queries. A more modern approach involves focusing on redundancy across many different nameservers, which in many cases broadcast the same anycasted IP address.
Secondary DNS involves the unidirectional transfer of DNS zones from the primary to the Secondary DNS server(s). One primary can have any number of Secondary DNS servers that it must communicate with in order to keep track of any zone updates. A zone update is considered a change in the contents of a zone, which ultimately leads to a Start of Authority (SOA) serial number increase. The zone’s SOA serial is one of the key elements of Secondary DNS; it is how primary and secondary servers synchronize zones. Below is an example of what an SOA record might look like during a dig query.
example.com 3600 IN SOA ashley.ns.cloudflare.com. dns.cloudflare.com.
2034097105 // Serial
10000 // Continue reading