HS. Part 7. Interoperability of Nokia SRLinux and Microsoft Azure SONiC
Hello my friend,
we continue the series of the blogpost dedicated to the overview of the Nokia SR Linux. Today we will speak about the interoperability and its joint operation with Microsoft Azure SONiC, another disaggregated OS, which is used in the hyper scale data centres.
2
3
4
5
retrieval system, or transmitted in any form or by any
means, electronic, mechanical or photocopying, recording,
or otherwise, for commercial purposes without the
prior permission of the author.
Automate your data centre infrastrcutre
The data centres and applications they host might be very static, if that is classical enterprise workloads. However, in the world of the clouds the frequency of the changes performed in the data centre network and servers can be very high. Effectively, it can be so high that doing them manually is impractical.
At our network automation training (either live or self-paced) you will learn the foundation of the automation for the small and big data centres, and clouds. You will lean how to structure the data using YANG modules, how to serialise it using JSON, XML, Protobuf depending on the application requirements Continue reading
The Hedge Podcast #46: The Value of a College Degree
While many network engineers think about getting a certification, not many think about going after a degree. Is there value in getting a degree for the network engineer? If so, what is it? What kinds of things do you learn in a degree program for network engineering? Eric Osterweil, a professor at George Mason University, joins Jeremy Filliben and Russ White on this episode of the Hedge to consider degrees for network engineers.
Workers Security


Hello, I'm an engineer on the Workers team, and today I want to talk to you about security.
Cloudflare is a security company, and the heart of Workers is, in my view, a security project. Running code written by third parties is always a scary proposition, and the primary concern of the Workers team is to make that safe.
For a project like this, it is not enough to pass a security review and say "ok, we're secure" and move on. It's not even enough to consider security at every stage of design and implementation. For Workers, security in and of itself is an ongoing project, and that work is never done. There are always things we can do to reduce the risk and impact of future vulnerabilities.
Today, I want to give you an overview of our security architecture, and then address two specific issues that we are frequently asked about: V8 bugs, and Spectre.
Architectural Overview
Let's start with a quick overview of the Workers Runtime architecture.
There are two fundamental parts of designing a code sandbox: secure isolation and API design.
Isolation
First, we need to create an execution environment where code can't access anything it's not Continue reading
Dictionary : feces barrier

Defining feces barrier
The post Dictionary : feces barrier appeared first on EtherealMind.
Dictionary : bugdoor

Whats is a bugdoor ?
The post Dictionary : bugdoor appeared first on EtherealMind.
OMG, Not Again: New Mobile Internet Protocol Vulnerabilities
Every now and then a security researcher “discovers” a tunneling protocol designed to be used over a protected transport core and “declares it vulnerable” assuming the attacker can connect to that transport network… even though the protocol was purposefully designed that way, and everyone with a bit of clue knew the whole story years ago (and/or it’s even documented in the RFC).
It was MPLS decades ago, then VXLAN a few years ago, and now someone “found” a “high-impact vulnerability” in GPRS Tunnel Protocol. Recommended countermeasures: whitelist-based IP filtering. Yeah, it’s amazing what a wonderful new tool they found.
Unfortunately (for the rest of us), common sense never generated headlines on Hacker News (or anywhere else).
Pluribus Networks Named a Strong Performer in Latest Forrester Wave™ for Open, Programmable Switches for a Businesswide SDN
Pluribus Networks has been named a Strong Performer in The Forrester Wave™: Open, Programmable Switches for Businesswide SDN, Q3, 2020.How Community Networks Are Helping during COVID-19

In July 2020, the Internet Society organized the webinar “How Community Networks are helping during COVID-19.”
We are halfway through this unprecedented year in which COVID-19 continues to cause disruptions and confusion in many areas of our lives. What is clear though, is the recognition of the Internet as a lifeline for us – for communicating with family members and health workers, accessing essential services, and participating in online learning and remote work.
But what about those who don’t have it?
The panel was an opportunity to show that there are solutions out there. To get to them will take strong communities driven by the understanding that everyone can make a difference.
The discussions of July’s webinar got to the heart of this.
The panelists shared stories and videos of the community networks they have helped to build in remote villages where underserved Indigenous tribes live. We heard the story of one Indigenous tribe located in the southern part of West Java in Indonesia, who set up a wireless network for their community. It helped them find jobs and increase their income, as well as access health information, learning resources, and government services.
In India, an Continue reading
Cloudflare Workers Announces Broad Language Support


We initially launched Cloudflare Workers with support for JavaScript and languages that compile to WebAssembly, such as Rust, C, and C++. Since then, Cloudflare and the community have improved the usability of Typescript on Workers. But we haven't talked much about the many other popular languages that compile to JavaScript. Today, we’re excited to announce support for Python, Scala, Kotlin, Reason and Dart.
You can build applications on Cloudflare Workers using your favorite language starting today.

Getting Started
Getting started is as simple as installing Wrangler, then running generate for the template for your chosen language: Python, Scala, Kotlin, Dart, or Reason. For Python, this looks like:
wrangler generate my-python-project https://github.com/cloudflare/python-worker-hello-world
Follow the installation instructions in the README inside the generated project directory, then run wrangler publish. You can see the output of your Worker at your workers.dev subdomain, e.g. https://my-python-project.cody.workers.dev/. You can sign up for a free Workers account if you don't have one yet.
That’s it. It is really easy to write in your favorite languages. But, this wouldn’t be a very compelling blog post if we left it at that. Now, I’ll shift the focus to Continue reading
The Migration of Legacy Applications to Workers


As Cloudflare Workers, and other Serverless platforms, continue to drive down costs while making it easier for developers to stand up globally scaled applications, the migration of legacy applications is becoming increasingly common. In this post, I want to show how easy it is to migrate such an application onto Workers. To demonstrate, I’m going to use a common migration scenario: moving a legacy application — on an old compute platform behind a VPN or in a private cloud — to a serverless compute platform behind zero-trust security.
Wait but why?
Before we dive further into the technical work, however, let me just address up front: why would someone want to do this? What benefits would they get from such a migration? In my experience, there are two sets of reasons: (1) factors that are “pushing” off legacy platforms, or the constraints and problems of the legacy approach; and (2) factors that are “pulling” onto serverless platforms like Workers, which speaks to the many benefits of this new approach. In terms of the push factors, we often see three core ones:
- Legacy compute resources are not flexible and must be constantly maintained, often leading to capacity constraints or excess cost;
- Continue reading
Solving Internet Challenges with LISP – Dino Farinacci, Founder @ lispers.net
In this episode Rick and Melchior discuss with Dino Farinacci how LISP can help solve internet challenges.
We touch on FIB scaling, mobility, IPv4 runout, COVID-19 and digital voting apps, blockchain and quantum internet.

Spectral Clustering
Motivation
Clustering is a way to make sense of the data by grouping similar values into a group. There are many ways to achieve that and in this post we will be looking at one of the way based on spectral method. Spectral clustering provides a starting point to understand graphs with many nodes by clustering them into 2 or more clusters. This clustering technique can also be applied for analyzing general data. This technique is based on Linear algebra and Graph theory.
We will start with a very brief introduction of the prerequisite for the sake of completeness and one can skip the prerequisite topics if they already have the familiarity.
Prerequisite Topic
Eigen Vectors and Eigen Values
One way to interpret when we multiply a vector a matrix is that a matrix transforms the vector. For example: below is a vector \(\begin{pmatrix} 2\\1 \end{pmatrix}\)
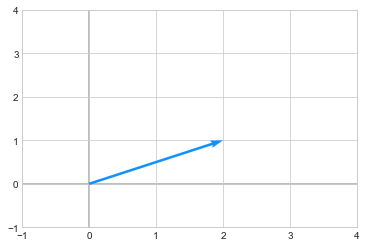
we apply a transformation by multiplying the above vector to a matrix
\[\begin{pmatrix} -1 & 3 \\ 2 & -2 \end{pmatrix}\]The resultant vector \(\begin{pmatrix} 1\\2 \end{pmatrix}\) is in orange after transformation.
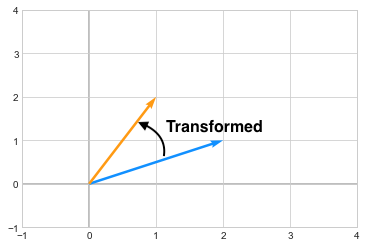
you can see how the vector changed its direction after the transformation. Now in case of Eigenvectors, which are special kinds of Continue reading
Your Automation Skills will Travel Well
In 2020 our automation skills may be the only thing that does travel! What I mean is that the automation skills being evangelized by so many in the networking community (Kirk Byers, David Bombal, Nick Russo, Jason Edelman and the Network to Code team, Hank Preston and Cisco DevNet and many more ....) will serve READ MORE
The post Your Automation Skills will Travel Well appeared first on The Gratuitous Arp.
Smart Network or Dumb?
Should the network be dumb or smart? Network vendors have recently focused on making the network as smart as possible because there is a definite feeling that dumb networks are quickly becoming a commodity—and it’s hard to see where and how steep profit margins can be maintained in a commodifying market. Software vendors, on the other hand, have been encroaching on the network space by “building in” overlay network capabilities, especially in virtualization products. VMWare and Docker come immediately to mind; both are either able to, or working towards, running on a plain IP fabric, reducing the number of services provided by the network to a minimum level (of course, I’d have a lot more confidence in these overlay systems if they were a lot smarter about routing … but I’ll leave that alone for the moment).
How can this question be answered? One way is to think through what sorts of things need to be done in processing packets, and then think through where it makes most sense to do those things. Another way is to measure the accuracy or speed at which some of these “packet processing things” can be done so you can decide in a more Continue reading