AT&T Continues to Build 5G on the Nation’s Best Wireless Network
AT&T’s 5G network is now live for consumers in 137 additional markets across the country and...
Wipro Partners With Citrix and Microsoft to Drive Business Continuity for Customers
Wipro Limited, a leading global information technology, consulting, and business process services...
Daily Roundup: IBM Buys Cloud Security Startup
IBM bought cloud security startup Spanugo; Nokia added Broadcom 5G chips to its ReefShark...
4 years on air.
Hello my friend,
Traditionally in the beginning of June (5th of June to be accurate), we celebrate the anniversary of our blogging. And in this year it is already 4 years, since we started in 2016!
In terms of the absolute numbers, we have crossed the mark in 100 posted blogs! Hurray! And we were marked as Cisco Champion 2020 one more time! Also Hurray!
Let’s reflect what has happened global as well…
Live automation training
The biggest new introduction is the live online network automation training. Years of real practical experience of implementing and automating network solutions for service provider and data centres across Europe and North America are now available for you. Just join our network automation training in this run or in any next and learn:
- Why to automate?
- How to automate?
- What is the toolkit (YANG, XML, YAML, JSON, Protobuf, NETCONF, RESTCONF, gNMI/gRPC, VS Code, Atom, POSTman, Python, Ansible, Linux, Docker and many others)?
- How do different vendors behave (Cisco, Nokia, Arista, Cumulus)?

GitHub projects
There were multiple mini-series of the blogposts supported by the code at the GitHub:
Measuring the Core
This last week I was a guest on the TechSequences podcast with Leslie and Alexa discussing the centralization of the routed infrastructure in the ‘net. When that episode posts, I’ll cross post it here (but, of course, you should really just subscribe to their podcast, as they always have interesting guests—I’ll have Leslie and Alexa on the Hedge at some point, as well). The topic is related to this post on CircleID about the death of transit, which was a reaction to Geoff Huston’s article on the death of transit some time before.
All that to say… while reading through some research papers this week, I ran into a recent (2018) paper where Carisimo et al. try out different ways of measuring which autonomous systems belong to the “core” of the ‘net. They went about this by taking a set of AS’ “everyone” acknowledges to be “part of the core,” and then trying to find some measurement that successfully describes something all of them have in common.
The result is the k-metric, which measures the connectivity of an AS’ peers. If an AS has peers who are just as connected as they are, then k-metric is high. Otherwise, the k-metric Continue reading
GSMA Cancels MWC LA Event Due to COVID-19 Concerns
The trade group was forced to nix this year’s MWC Barcelona event just as the pandemic was...
Nokia Adds Broadcom ASICs to 5G ReefShark Portfolio
Earlier this year Nokia announced plans to use Intel and Marvell's base station chips in its...
IBM Buys Spanugo for Cloud Security, Compliance
Big Blue plans to integrate Spanugo’s software into its public cloud to help meet the security...
Tech Bytes: Improving IT Operations With Aruba’s AIOps (Sponsored)
Today's Tech Bytes Podcast, sponsored by Aruba, discusses the AI capabilities in Aruba’s new Edge Services Platform or ESP; in particular, we explore Aruba's AIOps offering, and how artificial intelligence can improve day-to-day IT operations. Our guest is Jose Tellado, Chief Technologist of AIOps and an HPE Fellow.
The post Tech Bytes: Improving IT Operations With Aruba’s AIOps (Sponsored) appeared first on Packet Pushers.
Tech Bytes: Improving IT Operations With Aruba’s AIOps (Sponsored)
Today's Tech Bytes Podcast, sponsored by Aruba, discusses the AI capabilities in Aruba’s new Edge Services Platform or ESP; in particular, we explore Aruba's AIOps offering, and how artificial intelligence can improve day-to-day IT operations. Our guest is Jose Tellado, Chief Technologist of AIOps and an HPE Fellow.Network Break 288: Aruba ESP Senses Opportunity At The Edge; Intel Wrestles With New Chip Attacks
Take a Network Break! Aruba targets the enterprise edge with Aruba ESP and AI, Intel grapples with new attacks against secure enclaves in its chips, and MIT walks away from negotiations with an academic publisher over open access to journals. Three tech companies rethink the sale of facial recognition technology to U.S. police forces, the Wi-Fi Alliance praises the FCC Chair, and more tech news and commentary.Network Break 288: Aruba ESP Senses Opportunity At The Edge; Intel Wrestles With New Chip Attacks
Take a Network Break! Aruba targets the enterprise edge with Aruba ESP and AI, Intel grapples with new attacks against secure enclaves in its chips, and MIT walks away from negotiations with an academic publisher over open access to journals. Three tech companies rethink the sale of facial recognition technology to U.S. police forces, the Wi-Fi Alliance praises the FCC Chair, and more tech news and commentary.
The post Network Break 288: Aruba ESP Senses Opportunity At The Edge; Intel Wrestles With New Chip Attacks appeared first on Packet Pushers.
SASE Is Here to Stay
SD-WAN and security alone may not be going anywhere soon, but you can bet on SASE becoming a much...
The Week in Internet News: Twitter Removes 170,000 Pro-China Accounts

No more tweets for you: Twitter has removed 170,000 accounts it says are tied to a coordinated pro-China campaign, BBC.com reports. A core network of nearly 24,000 accounts along with 150,000 “amplifier” accounts were among those removed, the company said. The accounts were pushing pro-communist messages while criticizing protestors in Hong Hong.
No more Zoom for you: Meanwhile, video conferencing giant Zoom has shut down the account of a pro-democracy activist on the request of the Chinese government, The Independent writes. The account was closed after Zhou Fengsuo and other activists held a digital event commemorating the 1989 Tienanmen Square Massacre. After criticism, Zoom reactivated the account.
Closing the gap: Sub-Saharan Africa is the Internet’s next frontier, writes Forbes contributor Miriam Tuerk. “Expanding network connectivity across sub-Saharan Africa will open up digital services that many of us now take for granted,” she says. “Mobile Banking, WhatsApp chatting and video, e-health, e-education are key services only possible with reliable internet connectivity.”
Where’s the WiFi? The state of Michigan has launched a map of free WiFi hotspots in an effort to aid residents without Internet access during the COVID-19 pandemic, WKZO.com reports. “While public Wi-Fi hot spots are not a Continue reading
Routing in Fat Trees – Tony Przygienda, Distinguished Engineer @ Juniper Networks
Why do we need another routing protocol in the datacenter? And why not use optimised BPG or ISIS?
Tony Przygienda introduced and explains a new routing protocol written with current DC needs in mind; Routing in Fat Trees or in short RIFT.

Using data science and machine learning for improved customer support
In this blog post we’ll explore three tricks that can be used for data science that helped us solve real problems for our customer support group and our customers. Two for natural language processing in a customer support context and one for identifying attack Internet attack traffic.
Through these examples, we hope to demonstrate how invaluable data processing tricks, visualisations and tools can be before putting data into a machine learning algorithm. By refining data prior to processing, we are able to achieve dramatically improved results without needing to change the underlying machine learning strategies which are used.
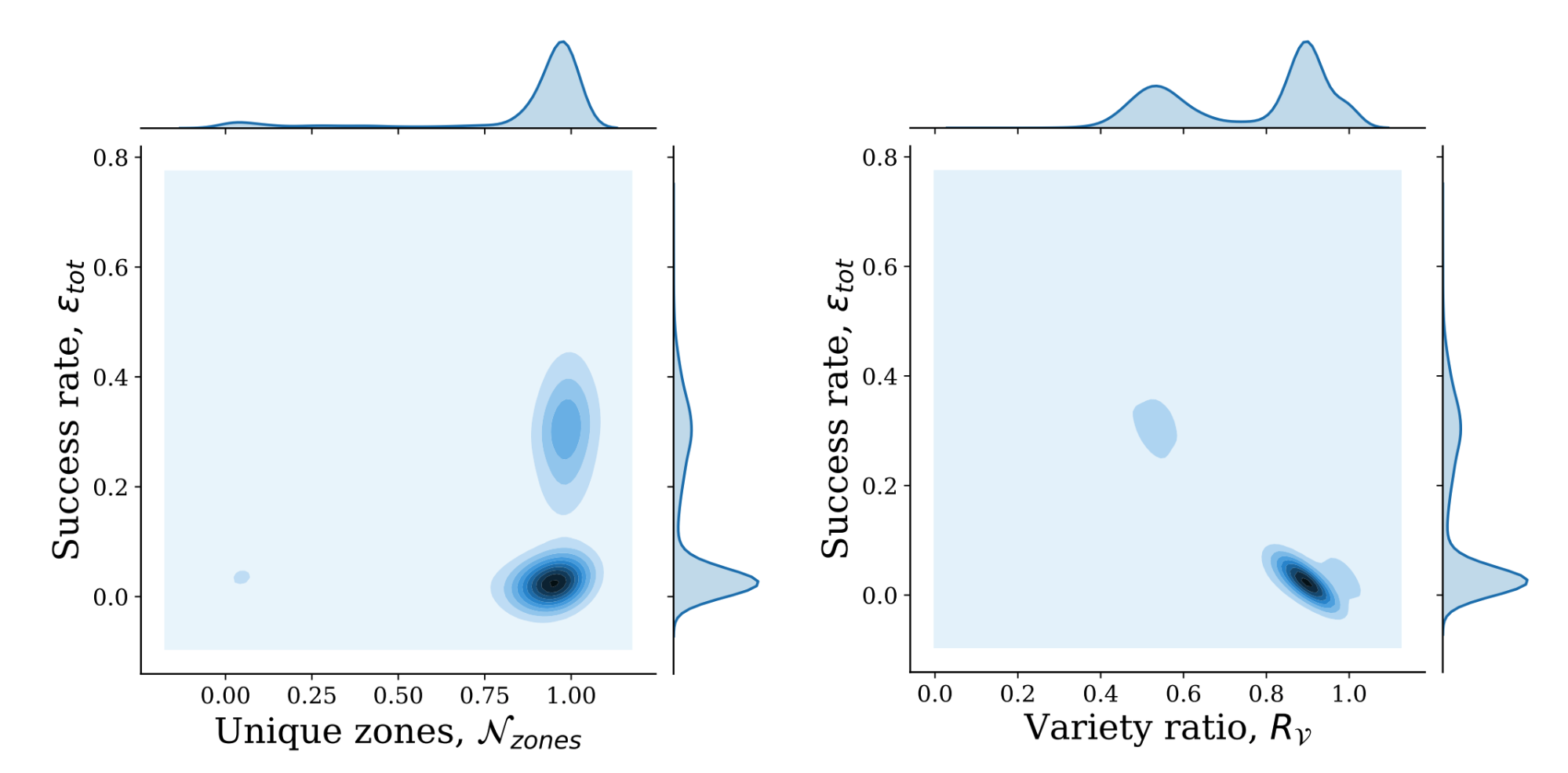
Know the Limits (Language Classification)
When browsing a social media site, you may find the site prompts you to translate a post even though it is in your language.
We recently came across a similar problem at Cloudflare when we were looking into language classification for chat support messages. Using an off-the-shelf classification algorithm, users with short messages often had their chats classified incorrectly and our analysis found there’s a correlation between the length of a message and the accuracy of the classification (based on the browser Accept-Language header and the languages of the country where the request was submitted):
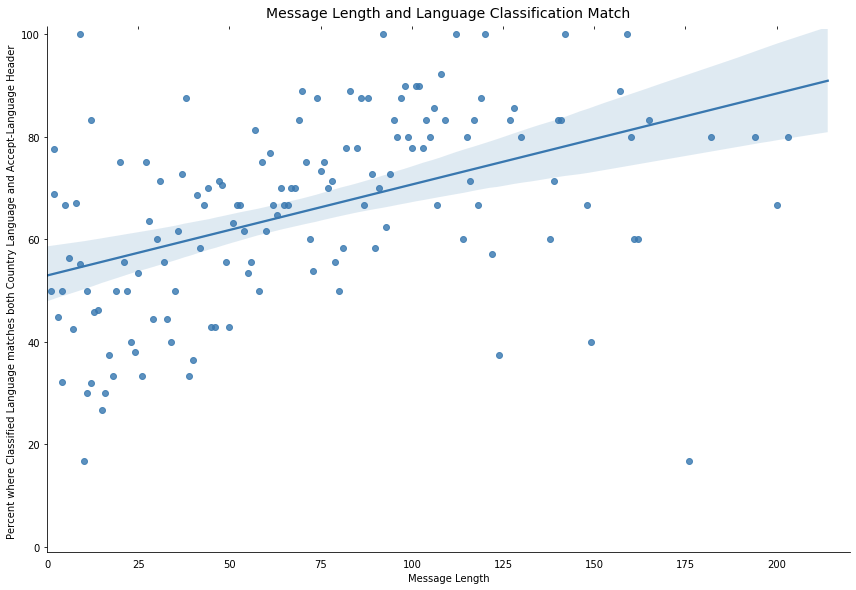
On a Continue reading
2020年第1四半期ネットワーク層DDoS攻撃の傾向


2020年第1四半期の締め括りにあたり、当社は、DDoS攻撃の傾向が、未曾有の世界的外出禁止令の中、変わったのかどうか、変わったのであればどのように変わったのかの把握に着手しました。それ以降、トラフィックレベルは多くの国で50%以上も増加していますが、DDoS攻撃も同様に増えているのでしょうか。
長期休暇の時期は、トラフィックの増加が見られます。この時期、世の中の人は、オンラインで買い物や食べ物を注文したり、オンラインゲームで遊んだり、その他オンラインでさまざまなことを楽しんでいるものです。使用量の増加は、種々多様なオンラインサービスを提供する企業にとって分刻みの収益増加につながります。
こうしたピーク時にダウンタイムやサービス低下が発生すると、あっという間にユーザーの解約や大規模な減収という事態になりかねません。ITICの見積もりでは、停止時の損失額は、1分あたり平均5,600ドルとなります。これは1時間あたり30万ドル以上の損失に相当します。したがって、長期休暇時期に攻撃者がDDoS攻撃の数を増やすことで、この機会を利用するのは驚くべきことではありません。
現在のコロナ禍は、同じような因果関係を持っています。多くの人が、家にいることを余儀なくされています。日々の仕事をこなすために、オンラインサービスへの依存度を高めている現状が、インターネットトラフィックとDDoS攻撃の急増を引き起こします。
小規模で短時間の攻撃の台頭
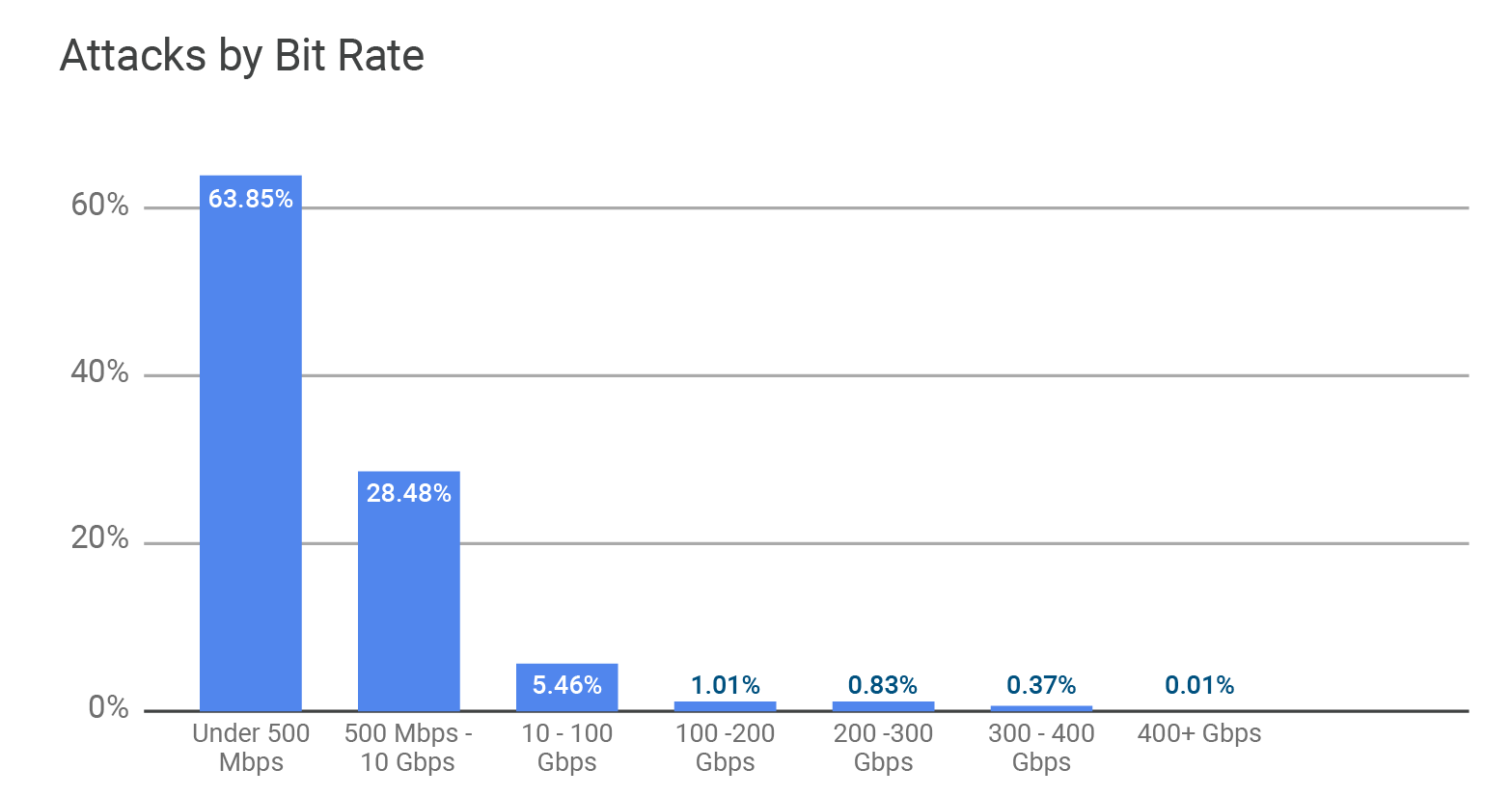
2020年の第1四半期に観測された攻撃のほとんどが、ビットレートで比較的小規模なものでした。次の図で示すように、10Gbps未満の攻撃が起きたのは、2020年第1四半期が92%、一方、2019年の第4四半期は、84%でした。
さらに深く掘り下げると、第1四半期の10Gbps未満の攻撃の分布には、前四半期と比較すると興味深い変化が見られます。前年第4四半期では、47%のネットワーク層DDoS攻撃の最大値は500Mbps以下であるのに対して、今年の第1四半期では、それが64%まで増加しています。
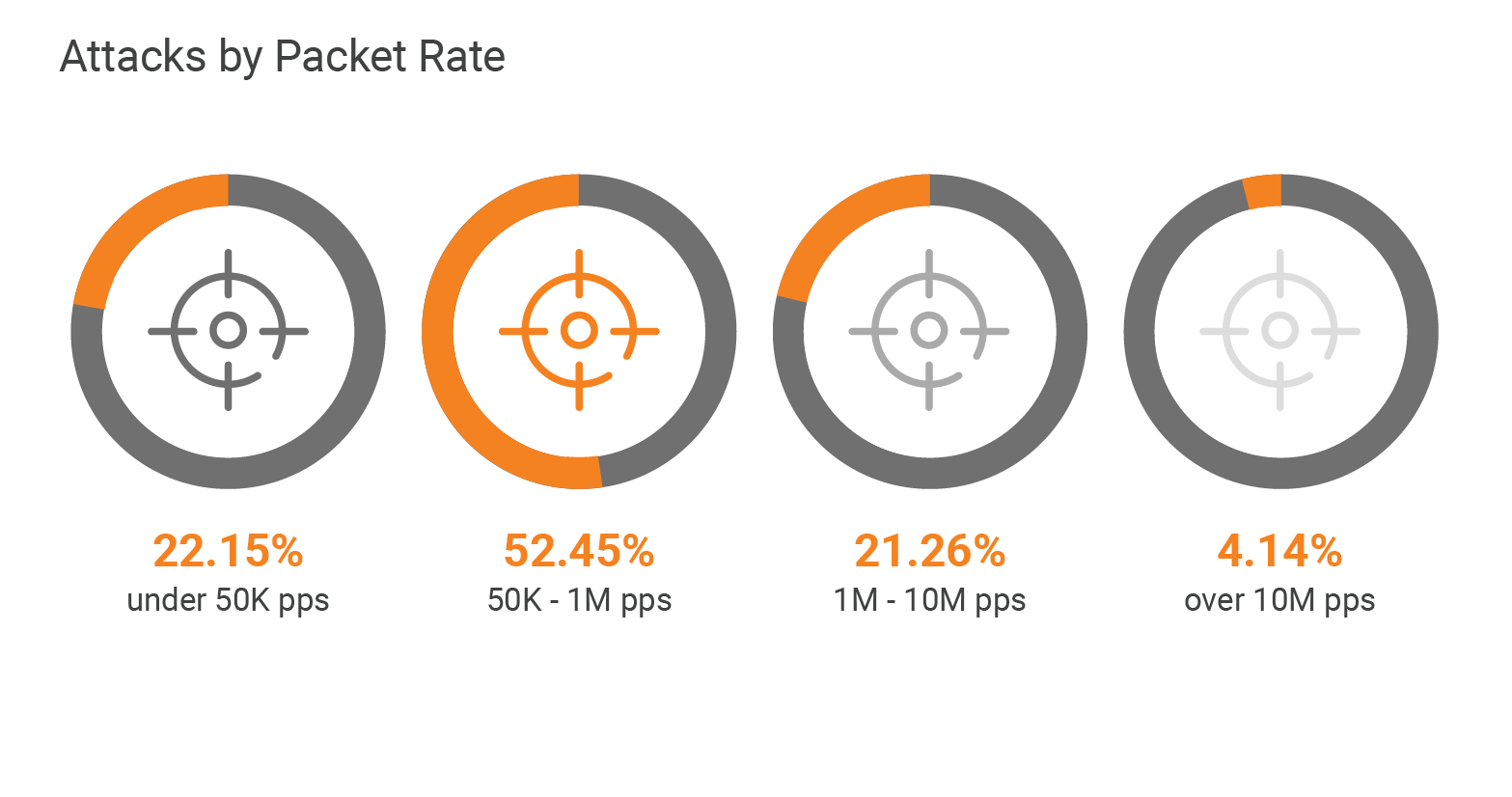
パケットレートの観点からは、攻撃の大部分で最大値は100万pps以下でした。ビットレートとともに、このレートは攻撃者が1秒あたり数ビットまたはパケットの高速フラッドを生成するために努力もリソースも集中させていないことを示しています。
ところが、減少しているのはパケットとビットレートだけでなく、攻撃持続時間も減少しています。下の図を見ると、第1四半期に30~60分間続いたDDoS攻撃は79%で、第4四半期の60%から19%増加したことがわかります。
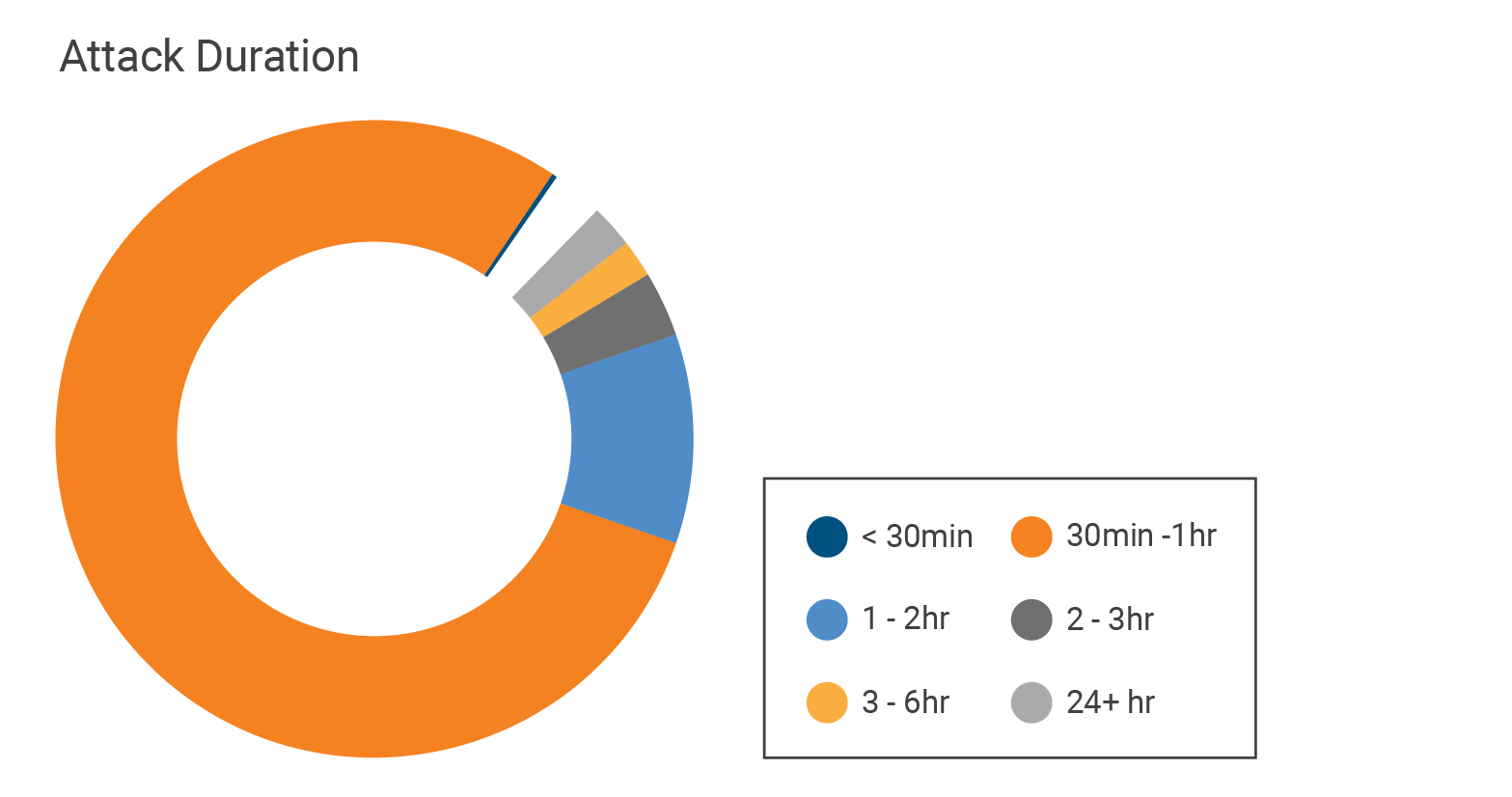
この3つの傾向は、次のように説明できます。
- DDoS攻撃を始めるのは安価で、技術的な知識はそれほど必要ではありません。DDoS-as-a-service(サービスとしてのDDoS攻撃)ツールは、専門知識を持たない悪者が費用対効果の高い方法で、帯域幅も多く使わずに迅速かつ簡単にDDoS攻撃を仕掛けることを可能にしました。Kaperskyによると、DDoS攻撃サービスは300秒間(5分間)の攻撃でわずか5ドルです。さらに、アマチュアの攻撃者でも簡単に無料ツールを使って、パケットのフラッドを引き起こすことができてしまいます。次のセクションで説明しますが、第1四半期の全DDoS攻撃のうち13.5%が一般に公開されているMiraiコードの変種を使って生成されていました。
- 10Gbps未満の攻撃は小さいように見えるかもしれませんが、未保護のインターネットプロパティに影響を与えるには十分な規模です。より小規模でより速い攻撃は、インターネットプロパティの可用性を妨害しない代わりに、攻撃者が企業から身代金を要求することのROIが高いということになるかもしれません。
大規模な攻撃は少数ながら依然として存在する
攻撃の大部分は10Gbps未満ですが、大規模な攻撃も依然として蔓延しています。以下のグラフでは、2019年第4四半期と2020年第1四半期にCloudflareが観測し、軽減したネットワーク層DDoS攻撃の最大ビットレートの傾向を示しています。今四半期に起きた最大の攻撃は3月に発生し、ピークは550Gbpsをわずかに上回りました。
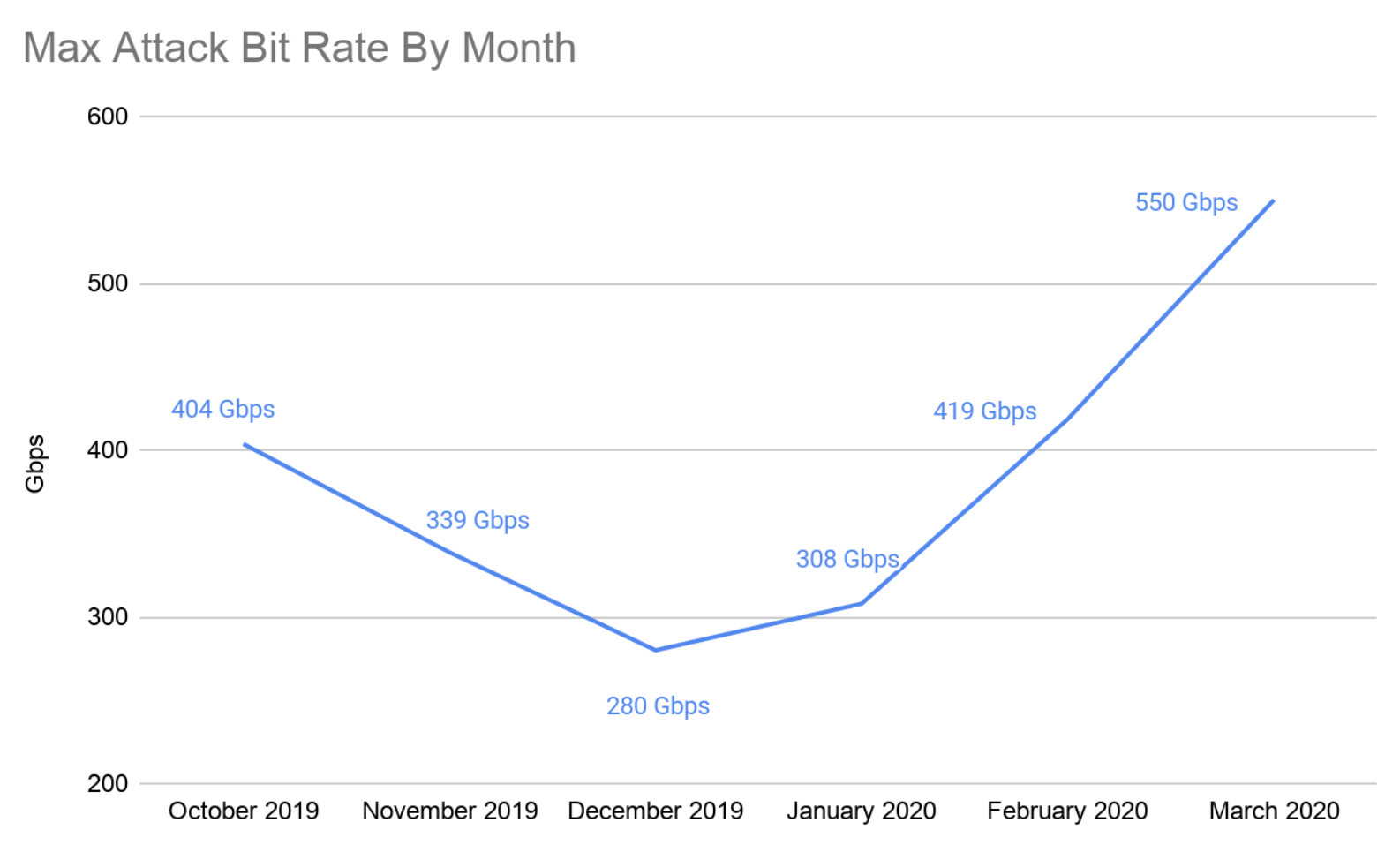
失敗しても諦めず、再試行を繰り返す
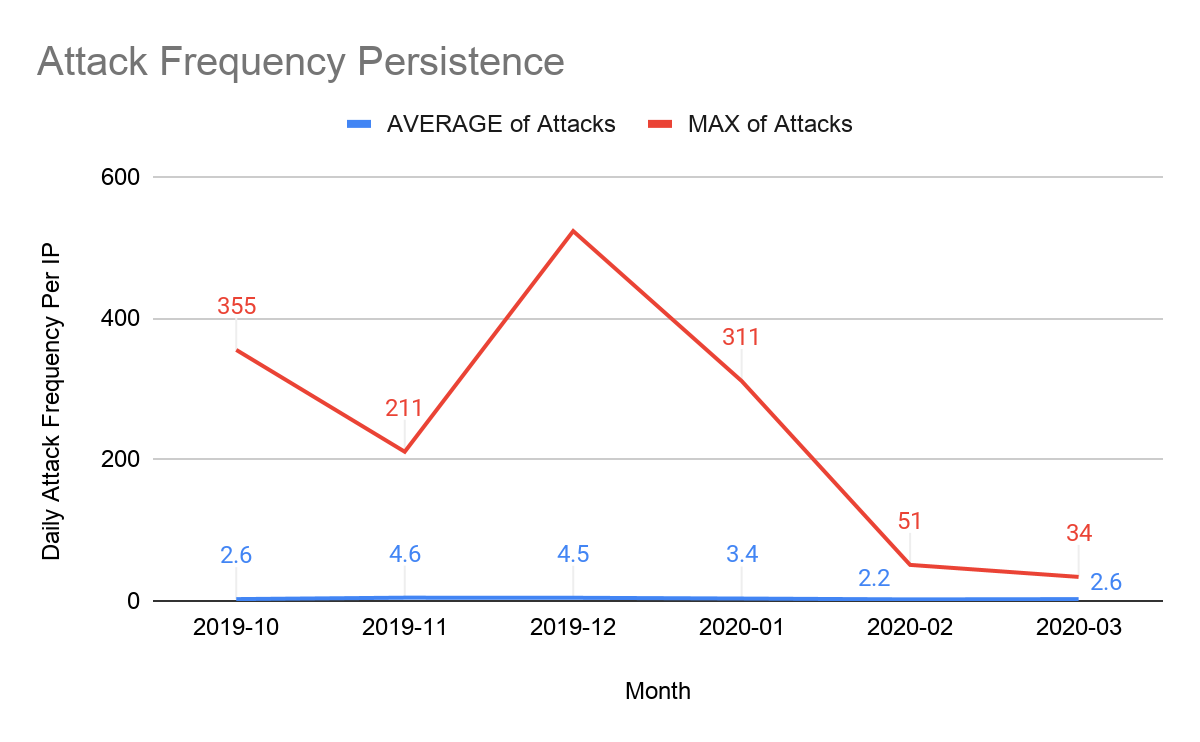
しつこい攻撃者は、攻撃に失敗しても諦めないタイプです。何度も仕掛けてきます。ターゲットに向けて複数の攻撃を仕掛け、攻撃ベクトルを複数利用することもあります。2019年第4四半期の年末期間中に、攻撃者は単一のCloudflare IPに対して1日に523件ものDDoS攻撃をしつこく仕掛けてきました。攻撃下にあったCloudflare IPそれぞれが、毎日平均4.6ものDDoS攻撃の標的となりました。
各国で新型コロナウイルスによる都市封鎖が始まった第1四半期中、例年の月間平均と比べると、攻撃数に大幅な増加が見られました。このような増加を目の当たりにしたのは、2019年の第4四半期以来です。ただし、そこには興味深い違いがあり、現在の攻撃は年末時期より持続性が低かったように見えました。2020年第1四半期、各Cloudflare IPアドレスへの1日あたりの攻撃の持続率は2.2件まで低下しており、単一IPアドレスへの攻撃の最大数は311件でした。これは前期の年末時期に比べ40%の削減でした。
過去2四半期にわたり、1日あたりIPごとのDDoS攻撃で使われた攻撃ベクトルの平均数はほぼ一定して約1.4で、最大数は10でした。

この四半期では、第3/4層で34種類の攻撃ベクトルが見られました。ACK攻撃は第1四半期の最大数(50.1%)を占め、次はSYN攻撃の16.6%でした。第3位はMiraiで、それでも攻撃の大きな割合(15.4%)を占めています。SYN攻撃とACK DDoS攻撃(TCP)を合わせると、第1四半期の第3/4層への全攻撃ベクトルの66%となります。
攻撃ベクトルのトップ
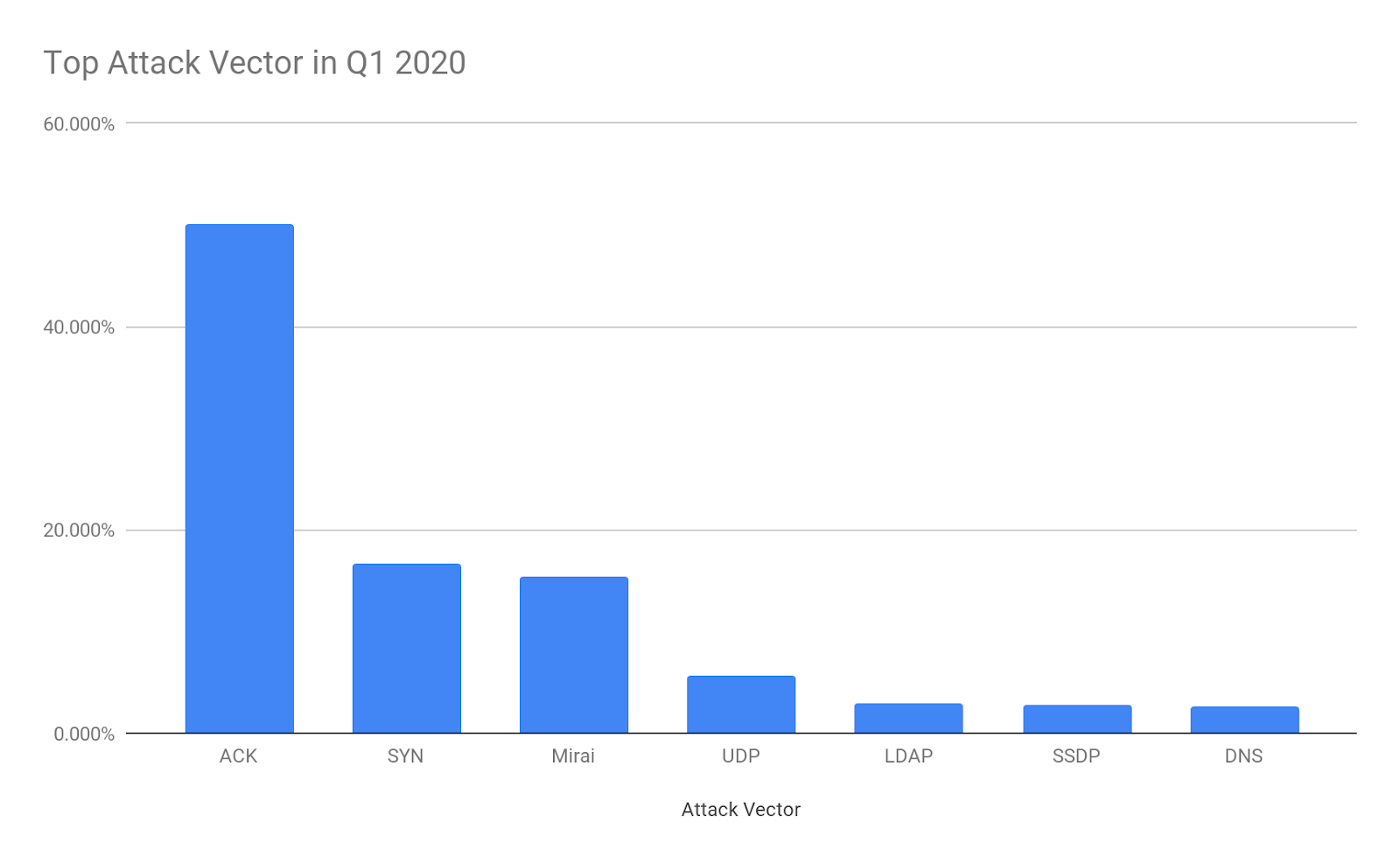
すべての攻撃ベクトル
| Attack Vector | Percent in Q1 |
|---|---|
| ACK | 50.121% |
| SYN | 16.636% |
| Mirai | 15.404% |
| UDP | 5.714% |
| LDAP | 2.898% |
| SSDP | 2.833% |
| DNS | 2.677% |
| Other | 0.876% |
| QUIC | 0.527% |
| NTP | 0.373% |
| RST | 0.353% |
| Memcached | 0.296% |
| ChargeGen | 0.236% |
| WS Discovery | 0.221% |
| ACK-PSH | 0.208% |
| SNMP | 0.159% |
| VSE | 0.081% |
| MSSQL | 0.079% |
| ICMP | 0.072% |
| Bittorrent | 0.056% |
| OpenVPN | 0.046% |
| Dahua | 0.032% |
| GRE | 0.022% |
| TFTP | 0.014% |
| LOIC | 0.014% |
| STUN | 0.011% |
| Lantronix | 0.009% |
| CoAP | 0.008% |
| Jenkins | 0.006% |
| VXWorks | 0.005% |
| Ubiquity | 0.005% |
| TeamSpeak | 0.004% |
| XMAS | 0.003% |
| SPSS | 0.001% |
残念なことに、危機的状況とは時に悪意の好機である
2020年3月のDDoS攻撃数は、1月と2月と比較して増加しました。以下に示されるように、この危機的時期を、攻撃者はDDoS攻撃を増やす絶好の機会であると考えました。

さらに、各国の政府当局が都市封鎖と一時待機の義務づけを始めたのに合わせて、攻撃者は3月下旬に大規模な攻撃を増加させに至りました。3月の後半(3月16~31日)には、前半(3月1~15日)に比べて検出された攻撃は55%も増加していました。さらに、300-400 Gbpsをピークとする攻撃の94%が3月中に発生したものでした。
規模に関わりなく、ソースにより近くでDDoS攻撃を阻止
DDoSの状況は常に変化しており、包括的で適応性の高いDDoS保護ソリューションを備えることが重要です。上記の攻撃への洞察の観点から、ここではCloudflareがお客様を保護するために、こうした変化に対して機先を制していく方法をご紹介しましょう。
- 攻撃の速度も持続時間も短縮を続け、今までのベンダーが提示してきたような、最大15分の軽減時間のSLAは、実用性がありません。Cloudflareは、多くの場合、ネットワーク層DDoS攻撃を10秒未満で軽減します。これはますます短くなる攻撃に対抗するために重要です。こちらで最新のDDoS攻撃検出と軽減システムについてお読みください。このシステムでは、DDoS攻撃の自動検出と軽減を迅速に、かつ大規模に行うことができます。
- 近年より多くのDDoS攻撃がローカライズされています。つまり、スクラビングセンターアプローチを採用する従来のDDoSソリューションは、グローバルなカバレッジに制限があると同時に、DDoSトラフィックをセンター経由で動かす必要があるためチョークポイントとなり、実用性が低いということになります。Cloudflare独自の分散型アーキテクチャは、世界200都市に広がり、完全なDDoS対策機能を提供して、データセンター全てを強化します。
- 大規模に分散された帯域幅消費型攻撃はまだ存在し、チャンスが増えたとき、高い処理能力を持った攻撃者に使われてしまいます。1Tbpsを超える攻撃が将来的に予想されるため、大規模なDDoS攻撃を軽減する能力は、今日のDDoSソリューションにとって大切です。Cloudflareは、最大規模のDDoS攻撃でさえも軽減することが可能となる35Tbpsを超える容量を持つ世界で最も相互接続しているネットワークの一つです。この大規模なネットワーク容量と世界的に分散されたアーキテクチャによって、Cloudflareはどのような規模でも、ソースに近いところで攻撃を軽減することができます。
CloudflareのDDoSソリューションの詳細は、こちらにお問い合わせいただくか、今すぐ始めましょう。
Technology Adoption in the Internet
How are new technologies adopted in the Internet? What drives adoption? What impedes adoption? These were the questions posed at a panel session at the recent EuroDiG workshop in June.IT Training and Running – Not So Different?
For those that follow me on Twitter, you probably know that I’m an avid runner and post some of my experiences there. My current goal is to become a sub 20 minute 5km runner, which is turning out to be an aggressive goal. I’m probably at around 22 minutes right now. As I always do, I try to learn from different areas of life and cross apply that, to also what I do in IT. When you think about it, it’s not that different! Things I’ve learned from trying to become a better runner, that you can apply in your IT training.
Plan – The saying “failing to plan is planning to fail” is quite accurate. Many runners don’t have a plan and end up just running around the same pace every training session. That leads to mediocre results. The same is true when trying to become better at something in IT. You don’t always need a super detailed plan, but you need a plan. A certification is one of the tools to help you build that plan.
Discipline – A plan is no good if you don’t materialize it. Sometimes it’s tough, and you don’t feel like living Continue reading
Network Reliability Engineering Should Be More than Software or Automation
This blog post was initially sent to the subscribers of my SDN and Network Automation mailing list. Subscribe here.
In late 2018 Juniper started aggressively promoting Network Reliability Engineering - the networking variant of concepts of software-driven operations derived from GIFEE SRE concept (because it must make perfect sense to mimic whatever Google is doing, right?).
There’s nothing wrong with promoting network automation, or infrastructure-as-code concepts, and Matt Oswalt and his team did an awesome job with NRE Labs (huge “Thank you!” to whoever is financing them), but is that really all NRE should be?