Day Two Cloud 052: Moving Back Home From The Cloud
Today's Day Two Cloud episode is a frank conversation about cloud migration, multicloud, cloud repatriation, and more. If you're here for rainbows and unicorns, prepare for disappointment. We talk about what's real, how expensive it can be to move to cloud, why people bring workloads back on premises, and more. Our guest is Bobby Allen, CTO at CloudGenera.
The post Day Two Cloud 052: Moving Back Home From The Cloud appeared first on Packet Pushers.
Day Two Cloud 052: Moving Back Home From The Cloud
Today's Day Two Cloud episode is a frank conversation about cloud migration, multicloud, cloud repatriation, and more. If you're here for rainbows and unicorns, prepare for disappointment. We talk about what's real, how expensive it can be to move to cloud, why people bring workloads back on premises, and more. Our guest is Bobby Allen, CTO at CloudGenera.NTC – Security and Networking
The increased rate of change in networking isn’t just impacting the operational models used to run networks. Network security posture, infrastructure, and operations are having to adapt quickly as well. In this episode we sit down with Henry Jiang, CISO of Diligent Corporation, to talk about how security is adapting to current infrastructure trends.
Outro Music:
Danger Storm Kevin MacLeod (incompetech.com)
Licensed under Creative Commons: By Attribution 3.0 License
http://creativecommons.org/licenses/by/3.0/
The post NTC – Security and Networking appeared first on Network Collective.
High Availability Load Balancers with Maglev

Background

We run many backend services that power our customer dashboard, APIs, and features available at our edge. We own and operate physical infrastructure for our backend services. We need an effective way to route arbitrary TCP and UDP traffic between services and also from outside these data centers.
Previously, all traffic for these backend services would pass through several layers of stateful TCP proxies and NATs before reaching an available instance. This solution worked for several years, but as we grew it caused our service and operations teams many issues. Our service teams needed to deal with drops of availability, and our operations teams had much toil when needing to do maintenance on load balancer servers.
Goals
With the experience with our stateful TCP proxy and NAT solutions in mind, we had several goals for a replacement load balancing service, while remaining on our own infrastructure:
- Preserve source IPs through routing decisions to destination servers. This allows us to support servers that require client IP addresses as part of their operation, without workarounds such as X-Forwarded-For headers or the PROXY TCP extension.
- Support an architecture where backends are located across many racks and subnets. This prevents solutions that cannot Continue reading
How Should Network Architects Deal with Network Automation
A network architect friend of mine sent me a series of questions trying to figure out how he should approach network automation, and how deep he should go.
There is so much focus right now on network automation, but it’s difficult for me to know how to apply it, and how it all makes sense from an Architect’s PoV.
A network architect should be the bridge between the customer requirements and the underlying technologies, which (in my opinion) means he has to have a good grasp of both as opposed to fluffy opinions glanced from vendor white papers, or brushed off so-called thought leaders.
MANRS Fellowship Program Now Open

The first-ever MANRS (Mutually Agreed Norms for Routing Security) Fellowship Program is now accepting applications. If you are an emerging leader eager to improve the well-being of the Internet’s global routing system, apply now.
The program gives highly motivated individuals the chance to work alongside MANRS ambassadors, who are industry leaders participating in the Ambassador Program. Together, they will train diverse communities on good routing practices, analyze routing incidents, research into ways to secure routing, and survey the global policy landscape.
Fellows will improve their skills and bring new perspectives and ideas to MANRS. They will also gain valuable insights and networking opportunities from well-respected professionals called MANRS Ambassadors under the MANRS Ambassadors Program. The selection process for this program is currently underway.
The Internet Society supports this program as part of its work to reduce common routing threats and establish norms for network operations.
You can apply for a fellowship in three different areas: training, research, and policy. Each fellow will receive a stipend of $750 a month. There is no age requirement and you can apply for more than one category but will only be selected for one of them.
Online training
Responsible for: Conducting MANRS online tutorial Continue reading
Aruba Assembles SDN Tech for Edge Services Platform
Aruba Edge Services Platform is comprised of 35 services, including a dozen new insights that were...
Daily Roundup: IBM Quits Facial Recognition Biz
IBM quit the facial recognition business; A10, Dell teamed up on application delivery; and Alibaba...
7 Layers: IoT Part 2 — IoT Devices are Dangerously Insecure
This week is the second in a two-part series on the Internet of Things. We cover IoT security...
The History of Networking: Ivan Pepelnjak and the Internet Behind the Iron Curtain
Ivan Pepelnjak was a founding member of the first IX in Slovenia twenty-five years ago. He joins us to describe the origins of the Internet, from the first dial-up circuits to the founding of the first IX and local DNS services here on the History of Networking. Ivan is an independent consultant and trainer; his work can be found at https://ipspace.net.
TSMC Secures US Subsidies for Arizona Fab
The announcement comes weeks after the Taiwanese chipmaker announced plans to build the facility.
IBM Stops Facial Recognition Support for Surveillance Activity
CEO Arvind Krishna made the pledge in a letter to the U.S. Congress. It’s one of three policy...
A10 Bundles App Delivery, Security on Dell Hardware
Both bundles can use A10’s Harmony Controller for application management and integration into...
Alibaba Cloud Kicks Off Hiring Surge
The company is recruiting IT professionals with expertise in networking, database management,...
Heavy Networking 522: How CIOs Prioritize Security – Cisco’s CIO Perspectives 2020 Survey (Sponsored)
Today's Heavy Networking, sponsored by Cisco, examines results and insights from 1,300 global CIOs in Cisco's CIO Perspectives 2020 survey. Guest Jo Peterson, VP of Cloud & Security for Clarify360, shares highlights and learnings on CIO priorities, security, digital transformation, empowering teams, and more.
The post Heavy Networking 522: How CIOs Prioritize Security – Cisco’s CIO Perspectives 2020 Survey (Sponsored) appeared first on Packet Pushers.
Heavy Networking 522: How CIOs Prioritize Security – Cisco’s CIO Perspectives 2020 Survey (Sponsored)
Today's Heavy Networking, sponsored by Cisco, examines results and insights from 1,300 global CIOs in Cisco's CIO Perspectives 2020 survey. Guest Jo Peterson, VP of Cloud & Security for Clarify360, shares highlights and learnings on CIO priorities, security, digital transformation, empowering teams, and more.Strengthening Communities, Improving Lives and Livelihoods: The Internet Society Foundation Launches SCILLS

When people connect to the Internet, they can change the world for the better. And so many people have done just that, using this transformative technology to make strides in education, economic opportunity, and health outcomes. But Internet access is only part of the equation. There’s now a different kind of divide: the gap between those who have the knowledge and skills to use the Internet to empower themselves and their communities – and those who don’t.
To address this gap, the Internet Society Foundation is launching SCILLS: Strengthening Communities, Improving Lives and Livelihoods. The program aims to expand economic growth, improve health outcomes, and increase educational opportunities – by supporting communities to more knowledgeably and skillfully use the Internet.
Are you working to close this gap? The Internet Society Foundation wants to hear from you!
In its pilot year, the program is open to eligible organizations in Bangladesh, Colombia, and Senegal, with expansion to additional countries planned in coming years. It provides grants of up to $150,000 USD for projects lasting up to 24 months. Applications are open between 9 June and 3 July, and grantees will be announced in early September.
The Internet is for everyone – a critical lifeline that can Continue reading
UtahFS: Encrypted File Storage
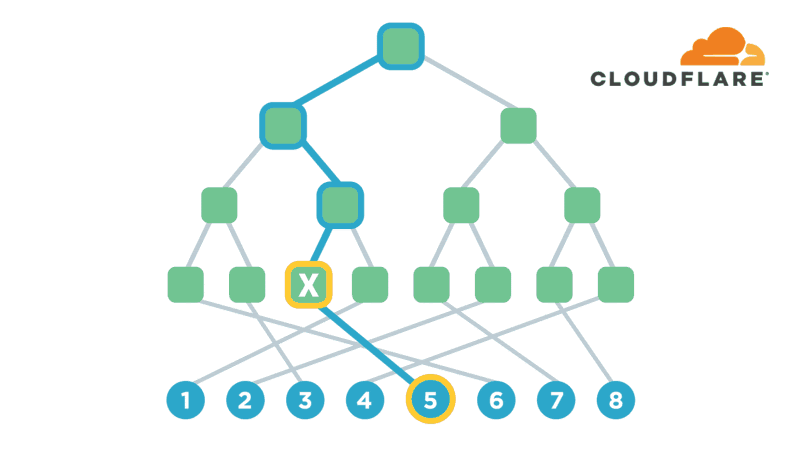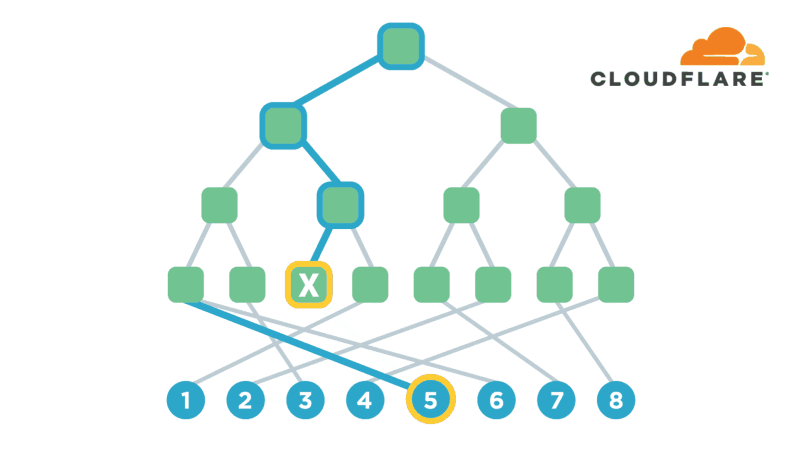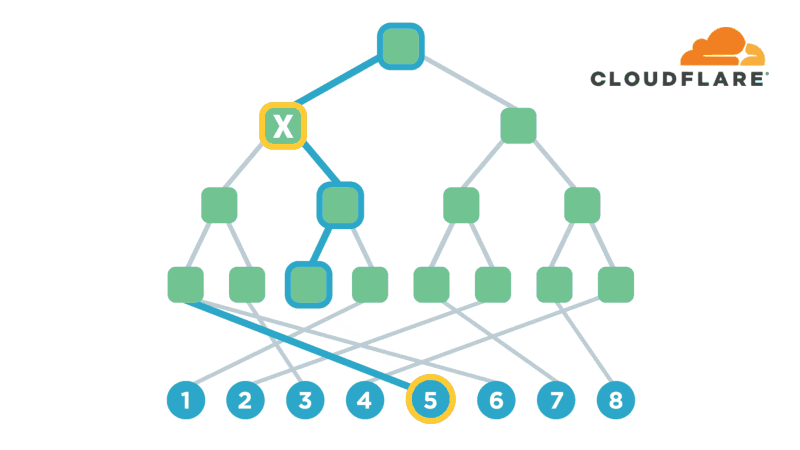
Encryption is one of the most powerful technologies that everyone uses on a daily basis without realizing it. Transport-layer encryption, which protects data as it’s sent across the Internet to its intended destination, is now ubiquitous because it’s a fundamental tool for creating a trustworthy Internet. Disk encryption, which protects data while it’s sitting idly on your phone or laptop’s hard drive, is also becoming ubiquitous because it prevents anybody who steals your device from also being able to see what’s on your desktop or read your email.
The next improvement on this technology that’s starting to gain popularity is end-to-end encryption, which refers to a system where only the end-users are able to access their data -- not any intermediate service providers. Some of the most popular examples of this type of encryption are chat apps like WhatsApp and Signal. End-to-end encryption significantly reduces the likelihood of a user’s data being maliciously stolen from, or otherwise mishandled by a service provider. This is because even if the service provider loses the data, nobody will have the keys to decrypt it!
Several months ago, I realized that I had a lot of sensitive files on my computer (my diary, if Continue reading
Cloud Networking Architectures
There’s one thing no cloud vendor ever managed to change: virtual machines running on top of cloud infrastructure expect to have Ethernet interfaces.
It doesn’t matter if the virtual Ethernet Network Interface Cards (NICs) are implemented with software emulation of actual hardware (VMware emulated the ancient Novell NE1000 NIC) or with paravirtual drivers - the virtual machines expect to send and receive Ethernet frames. What happens beyond the Ethernet NIC depends on the cloud implementation details.
Real-Time Monitoring Critical to Service Assurance
As service providers adopt virtualization and SDN capabilities, they are being held back by...