When We Come Together, We Are Richer for It

These are unsettling and unprecedented times.
The speed at which coronavirus has taken hold around the world, and the dramatic changes to our lives that it has brought, would have been difficult for many of us to contemplate just a few short weeks ago.
Social (and physical) distancing measures that were merely a suggestion then have suddenly become a strange reality for millions of people, with entire countries going into complete lockdown, borders and schools closing, planes no longer flying, and normal social activity placed on hold.
The vital role the Internet is playing is clear for all to see. It allows us to work together while we are socially apart, quietly and quickly providing many of us with a way to continue our lives. It has allowed us to maintain at least some sense of the ordinary during an extraordinary time.
We are asking a lot of the Internet, but it is ready for the challenge. It is enabling companies to keep working, schoolchildren to continue learning, and families and friends to stay connected. Even virtual birthday parties and weddings have become a hit!
The Internet means that self-isolation may be a physical reality, but it need not be Continue reading
Can We Trust BGP Next Hops (Part 1)?
Aldrin sent me an interesting question as a comment to one of my EVPN blog posts:
How does the network know that a VTEP is actually alive? (1) from the point of view of the control plane and (2) from the point of view of the data plane? And how do you ensure that control and data plane liveness monitoring has the same view? BFD for BGP is a possible solution for (1) but it’s not meant for 3rd party next hops, i.e. it doesn’t address (2).
Let’s stop right there (or you’ll stop reading in the next 10 milliseconds). I will also try to rephrase the question in more generic terms, hoping Aldrin won’t mind a slight detour… we’ll get back to the original question in another blog post.
Network Break 278: Palo Alto Buys SD-WAN Maker CloudGenix; Zoom Gets Called On Security, Privacy Problems
Our weekly installment of tech news analysis includes Palo Alto's $420 million purchase of CloudGenix, Zoom's very bad week for security and privacy, Cisco Live going virtual, updates on professional development opportunities, and more on Network Break from the Packet Pushers.
The post Network Break 278: Palo Alto Buys SD-WAN Maker CloudGenix; Zoom Gets Called On Security, Privacy Problems appeared first on Packet Pushers.
Network Break 278: Palo Alto Buys SD-WAN Maker CloudGenix; Zoom Gets Called On Security, Privacy Problems
Our weekly installment of tech news analysis includes Palo Alto's $420 million purchase of CloudGenix, Zoom's very bad week for security and privacy, Cisco Live going virtual, updates on professional development opportunities, and more on Network Break from the Packet Pushers.The Wrong Certificate
I'm constantly impressed by the rather complex intricacies that are associated with running your own web server these days. A recent source of these complexities has been the PKI, the security infrastructure used to maintain secure connections over the network, and I'd like to recount my experience here, in case any others encounter the same seemingly inexplicable behaviours in their secure web service configurations.Will the Pandemic Propel DevSecOps? Snyk Says Yes
This is also a great time to start a bug bounty program, says Guy Podjarny, founder and president...
Daily Roundup: Cisco Buys Backhaul Vendor
Cisco secured a deal to buy Fluidmesh Networks; IBM CEO threw down a hybrid-cloud challenge; and DT...
Automating Scale-out IP Fabrics Part 2: Simplifying Underlays with BGP Unnumbered
Happy Birthday to Pluribus! It gives me great pleasure to post this blog on Pluribus Networks’ 10th anniversary. Since its...VCSA, 503 Service Unavailable – possible fix
My ESXi hosting the VCSA crashed for whatever reason and after reboot the VCSA was displaying a “503 Service Unavailable” error. What I was seeing actually was a blabbering long line: The ESXi hosting my VCSA is not the fastest in the world, so I’ve waited a while, but the error was still there. Searching … Continue reading VCSA, 503 Service Unavailable – possible fixNvidia Joins the Fight Against COVID-19
A task force made up of computer scientists at Nvidia has joined the COVID-19 High Performance...
Cisco Snatches Fluidmesh for On-the-Move IoT Backhaul
The terms of the deal were not disclosed, but Cisco said it expects the acquisition to close before...
IBM CEO Throws Down Hybrid-Cloud Challenge
That challenge will rely heavily on IBM’s Red Hat business unit, which also received a new leader.
Unfortunate Natural Experiment Shows the Internet Works

For many weeks now, as the pandemic caused by the coronavirus has spread around the world, people have been isolating themselves to reduce the spread of infection. Businesses and schools have closed, and whole cities have been ordered to stay indoors. People’s livelihoods have disappeared, and of course, far too many people have been critically ill or have died. It is a calamity. Yet it would be much worse, if it were not for the Internet.
It’s enabling life go on. Businesses and schools are able to continue their core activity online. People are able to order food and medicine delivery to lower the risk of contagion. Families are video conferencing to catch up, worship, and even attend weddings. Creators are streaming music and stories from their homes. Clinicians and researchers are sharing crucial medical data worldwide. Everyday citizens, remarkably informed, are trying to flatten the curve.
This is what the Internet is for: a force for good in society.
Resilient by Design
The Internet is working well under this sudden demand because of how it is designed. Nearly magic, the Internet is designed to be a reliable system built of unreliable parts. This might sound awful, as though it Continue reading
How to Easily Secure Virtual Desktops for your Remote Employees
The COVID-19 pandemic has forced many organizations to shift their business online and their employees to work from home. As a result, business had to quickly adjust and scale up their infrastructure, sometimes with security as an afterthought.
Malicious actors are already taking advantage of this new reality by targeting the vulnerabilities commonly associated with employees connecting to corporate resources from their home environment. This includes social engineering and phishing campaigns, denial of service attacks, and exploiting vulnerabilities in home routers.
Secure VDI Environments with NSX
Providing employees working from home with secure and reliable access to their corporate resources and applications by the use of Virtual Desktop Infrastructure (VDI) helps our customers to reduce the impact on productivity and continuity as well as the risk associated with remote access to internal data.
In this blog post, I will cover a couple of use cases on how NSX can provide security for End User Compute and share some resources to help customers who are scaling up their VDI / remote desktop session host (RDSH) infrastructure to adapt to this new world in which vast numbers of employees are now working from home.
Protect Your Desktop Pools
The initial target of Continue reading
Tech Bytes: Gain Application Fluency Across Multiple Clouds With Oracle SD-WAN (Sponsored)
Today's Tech Bytes podcast tackles SD-WAN with sponsor Oracle. We examine how SD-WAN supports multi-cloud management, fail-safe network automation, more secure connections, and application fluency. Our guest is Doug Tait, Director of Product Marketing.Tech Bytes: Gain Application Fluency Across Multiple Clouds With Oracle SD-WAN (Sponsored)
Today's Tech Bytes podcast tackles SD-WAN with sponsor Oracle. We examine how SD-WAN supports multi-cloud management, fail-safe network automation, more secure connections, and application fluency. Our guest is Doug Tait, Director of Product Marketing.
The post Tech Bytes: Gain Application Fluency Across Multiple Clouds With Oracle SD-WAN (Sponsored) appeared first on Packet Pushers.
The Week in Internet News: Stay-at-Home Orders Highlight Need for Internet Access

More important than ever: With most people in the U.S. and many other countries ordered to stay at home to prevent the spread of the coronavirus, a lack of Internet access in rural and poor areas is making people feel more disconnected than ever, according to an Associated Press story at NWAonline.com. Stella Ashcraft “lives from check to check and can’t afford internet. Her senior-citizen center, where she plays bingo, does puzzles and gets lunch five days a week, is closed. So is her church and the library where she checks email. ‘I feel very withdrawn, isolated, alone,’ she said.
Spotlight on Zoom’s privacy: With many people working from home, web-conferencing app Zoom has become a crucial service for many. However, with the increased use of Zoom is also coming increasing scrutiny. While the company has marketed its service as offering end-to-end encryption, that’s not really the case, The Intercept reports. Zoom Video Communications, the company behind Zoom, has been hit with a class-action lawsuit for allegedly sharing user data with Facebook, CBS News adds. Finally, Zoom has pledged to focus on privacy and security issues, TechXplore reports.
Homework hotspots: As most students in the U.S. and Continue reading
Conntrack tales – one thousand and one flows
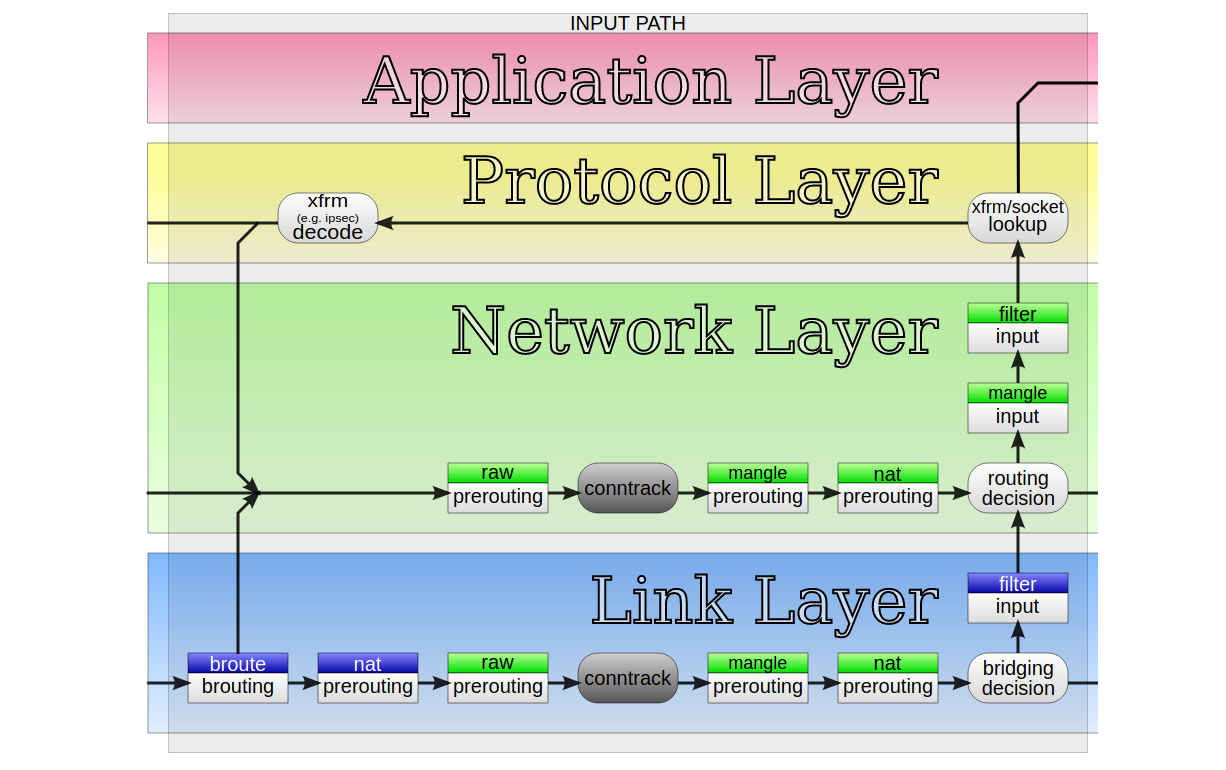
At Cloudflare we develop new products at a great pace. Their needs often challenge the architectural assumptions we made in the past. For example, years ago we decided to avoid using Linux's "conntrack" - stateful firewall facility. This brought great benefits - it simplified our iptables firewall setup, sped up the system a bit and made the inbound packet path easier to understand.
But eventually our needs changed. One of our new products had a reasonable need for it. But we weren't confident - can we just enable conntrack and move on? How does it actually work? I volunteered to help the team understand the dark corners of the "conntrack" subsystem.
What is conntrack?
"Conntrack" is a part of Linux network stack, specifically part of the firewall subsystem. To put that into perspective: early firewalls were entirely stateless. They could express only basic logic, like: allow SYN packets to port 80 and 443, and block everything else.
The stateless design gave some basic network security, but was quickly deemed insufficient. You see, there are certain things that can't be expressed in a stateless way. The canonical example is assessment of ACK packets - it's impossible to say if an ACK Continue reading