The Week in Internet News: Australian Lawmakers Push for ‘Fix’ to Encryption Law

An encryption fix: The Australian Labor Party says it will push for changes to an encryption law, passed in late 2018, that requires tech comp anies to give law enforcement agencies access to encrypted communications, ZDNet reports. Labor Party lawmakers have raised concerns about the law’s effect on the country’s tech industry, but it appears they don’t have the votes to make changes.
Telemedicine needs access: The use of telemedicine is growing, but low speeds in rural Internet are delaying its benefits to parts of Indiana, according to a story from the Kokomo Tribune, posted at Govtech.com. Some Internet-based diagnosis services need interactive videoconferencing technology with fast broadband speeds that aren’t available in parts of the state.
The future of IoT security: IoT World Today has six predictions for Internet of Things security in 2020. Among them: Facilities managers will become more concerned about smart building security, with buildings becoming a new avenue of attack. The security of 5G networks will also become an issue with new attacks on the way.
Goodbye WhatsApp: WhatsApp has begun automatically removing Kashmiri residents from WhatsApp, due to a long-running Internet shutdown in the region controlled by India, The Verge reports. WhatsApp’s Continue reading
Ericsson Corruption Probe Takes $1B Bite
“Through slush funds, bribes, gifts, and graft, Ericsson conducted telecom business with the...
Adlink Tackles Industrial IoT as Latest 5G-Drive Member
The 5G-Drive consortium has its sights set on the development of 5G autonomous drone scouts and...
Network Break 264: Broadcom’s New Tomahawk 4 Hits 25.6Tbps; Juniper Announces SD-LAN For EX Switches
Take a Network Break! Broadcom ships its fastest ASIC yet, the 15.6Tbps Tomahawk 4; Juniper Networks gets a new CTO, enables cloud control of its EX switches; and rolls out new CPE; Palo Alto Networks reports its latest quarterly financials, and we cover lots of listener follow-up.
The post Network Break 264: Broadcom’s New Tomahawk 4 Hits 25.6Tbps; Juniper Announces SD-LAN For EX Switches appeared first on Packet Pushers.
Network Break 264: Broadcom’s New Tomahawk 4 Hits 25.6Tbps; Juniper Announces SD-LAN For EX Switches
Take a Network Break! Broadcom ships its fastest ASIC yet, the 15.6Tbps Tomahawk 4; Juniper Networks gets a new CTO, enables cloud control of its EX switches; and rolls out new CPE; Palo Alto Networks reports its latest quarterly financials, and we cover lots of listener follow-up.Tech Bytes: Vitec Group Transforms Its WAN With Silver Peak’s SD-WAN (Sponsored)
Vitec Group has transformed its global WAN with an SD-WAN rollout from Silver Peak. The company has boosted the performance of critical business applications, reduced backup latency by 70%, and decommissioned expensive MPLS circuits in favor of DIA. Find out how in this sponsored Tech Bytes podcast. Our guest is Ben Skinner, head of corporate networks and infrastructure at Vitec Group.Tech Bytes: Vitec Group Transforms Its WAN With Silver Peak’s SD-WAN (Sponsored)
Vitec Group has transformed its global WAN with an SD-WAN rollout from Silver Peak. The company has boosted the performance of critical business applications, reduced backup latency by 70%, and decommissioned expensive MPLS circuits in favor of DIA. Find out how in this sponsored Tech Bytes podcast. Our guest is Ben Skinner, head of corporate networks and infrastructure at Vitec Group.
The post Tech Bytes: Vitec Group Transforms Its WAN With Silver Peak’s SD-WAN (Sponsored) appeared first on Packet Pushers.
Money Moves: November 2019
Google buys CloudSimple, challenges VMware Cloud on AWS; Palo Alto Networks announced plans to...
Segment Routing (SR) – What You Need To Know
This blog will provide you insights to help you on your journey on Segment Routing (SR) by...
Firewall Analytics: Now available to all paid plans
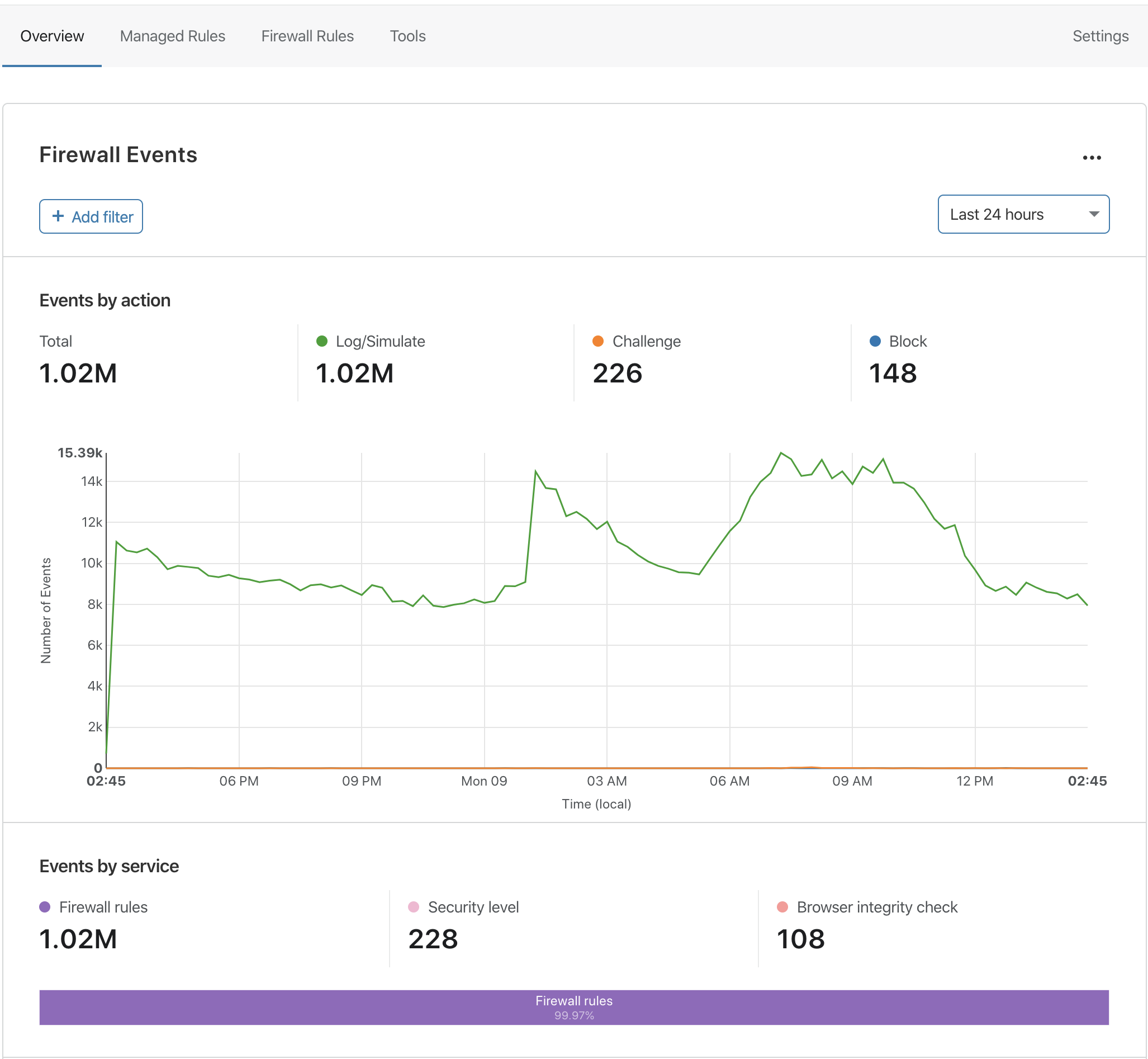
Our Firewall Analytics tool enables customers to quickly identify and investigate security threats using an intuitive interface. Until now, this tool had only been available to our Enterprise customers, who have been using it to get detailed insights into their traffic and better tailor their security configurations. Today, we are excited to make Firewall Analytics available to all paid plans and share details on several recent improvements we have made.
All paid plans are now able to take advantage of these capabilities, along with several important enhancements we’ve made to improve our customers’ workflow and productivity.
Increased Data Retention and Adaptive Sampling
Previously, Enterprise customers could view 14 days of Firewall Analytics for their domains. Today we’re increasing that retention to 30 days, and again to 90 days in the coming months. Business and Professional plan zones will get 30 and 3 days of retention, respectively.
In addition to the extended retention, we are introducing adaptive sampling to guarantee that Firewall Analytics results are displayed in the Cloudflare Dashboard quickly and reliably, even when you are under a massive attack or otherwise receiving a large volume of requests.
Adaptive sampling works similar to Netflix: when your internet connection runs low Continue reading
Announcing deeper insights and new monitoring capabilities from Cloudflare Analytics


This week we’re excited to announce a number of new products and features that provide deeper security and reliability insights, “proactive” analytics when there’s a problem, and more powerful ways to explore your data.
If you’ve been a user or follower of Cloudflare for a little while, you might have noticed that we take pride in turning technical challenges into easy solutions. Flip a switch or run a few API commands, and the attack you’re facing is now under control or your site is now 20% faster. However, this ease of use is even more helpful if it’s complemented by analytics. Before you make a change, you want to be sure that you understand your current situation. After the change, you want to confirm that it worked as intended, ideally as fast as possible.
Because of the front-line position of Cloudflare’s network, we can provide comprehensive metrics regarding both your traffic and the security and performance of your Internet property. And best of all, there’s nothing to set up or enable. Cloudflare Analytics is automatically available to all Cloudflare users and doesn’t rely on Javascript trackers, meaning that our metrics include traffic from APIs and bots and are not skewed Continue reading
Brief Briefing: Public Clouds Are Aggressively Proprietary

Packet Pushers has a podcast channel, Briefings in Brief, dedicated to shorter shows that focus on a single topic. It struck me that I haven’t mentioned it here. In this Brief I’m highlighting the lack of interoperability between clouds. When thinking more deeply, I realised that there is an aggressive lack of co-operation between cloud […]
The post Brief Briefing: Public Clouds Are Aggressively Proprietary appeared first on EtherealMind.
BGP- and Car Safety
The Facts and Fiction: BGP Is a Hot Mess blog post generated tons of responses, including a thoughtful tweet from Laura Alonso:
Is your argument that the technology works as designed and any issues with it are a people problem?
A polite question like that deserves more than 280-character reply, but I tried to do my best:
BGP definitely works even better than designed. Is that good enough? Probably, and we could politely argue about that… but the root cause of most of the problems we see today (and people love to yammer about) is not the protocol or how it was designed but how sloppily it’s used.
Laura somewhat disagreed with my way of handling the issue:
Read more ...