What’s New in Calico – Fall 2025 Release
Simplify, Secure, and Scale Your Infrastructure
As organizations scale Kubernetes and hybrid infrastructures, many are realizing that more tools don’t mean better security. A recent Microsoft report found that organizations with 16+ point solutions see 2.8x more data security incidents than those with fewer tools. Yet platform teams are still expected to deliver resilience and performance across containers, VMs, and bare metal, often while juggling fragmented tools that introduce risk, downtime, and complexity.
The Fall 2025 release of Calico Enterprise and Calico Cloud cuts through that complexity. Its new features are designed to make your infrastructure more resilient, performant, and observable—right out of the box. From disaster recovery automation to modern data plane support and application traffic handling, these updates empower platform engineers to simplify operations while meeting strict reliability requirements.
The new features in this release can be grouped into two main categories:
1. Resilient, High-Performance Networking and Improved Quality of Service:
-
- High availability (HA) management planes for VM and bare metal hosts – Increases resiliency and helps reduce downtime.
- The official release (GA) of the nftables dataplane -Delivers faster and more scalable rule-processing than iptables.
- Maglev-Based Session Affinity – Maintain stable network traffic flow during failures Continue reading
Zero-Trust with Zero-Friction eBPF in Calico v3.31
Calico eBPF by default*
*some conditions may apply
 Calico has used eBPF as one of its dataplanes since version 3.13, released more than five years ago. At the time, this was an exciting step forward, introducing a new, innovative data plane that quickly gained traction within the Calico community. Since then, there have been many changes and continued evolution, all thanks to the many adopters of the then-new data plane.
Calico has used eBPF as one of its dataplanes since version 3.13, released more than five years ago. At the time, this was an exciting step forward, introducing a new, innovative data plane that quickly gained traction within the Calico community. Since then, there have been many changes and continued evolution, all thanks to the many adopters of the then-new data plane.
However, there has been one persistent challenge in the installation process since day one: bootstrapping the eBPF data plane required a manual setup step. This extra friction point often frustrated operators and slowed adoption.
With the launch of Calico v3.31, that hurdle to using the eBPF data plane has finally been removed. For many environments (see Limitations section below), you can now install Calico with eBPF enabled right out of the box with no manual setup required.
Simply use the provided installation manifest (custom-resources-bpf.yaml), which comes preconfigured with the data plane option set to eBPF.
To get started, follow the instructions in Install Calico networking and network policy for on-premises deployments to enjoy a much smoother installation experience.
See Calico eBPF in action with Continue reading
Calico Whisker in Action: Reading and Understanding Policy Traces
Kubernetes adoption is growing, and managing secure and efficient network communication is becoming increasingly complex. With this growth, organizations need to enforce network policies with greater precision and care. However, implementing these policies without disrupting operations can be challenging.
That’s where Calico Whisker comes in. It helps teams implement network policies that follow the principle of least privilege, ensuring workloads communicate only as intended. Since most organizations introduce network policies after applications are already running, safe and incremental rollout is essential.
To support this, Calico Whisker offers staged network policies, which allow teams to preview a policy’s effect in a live environment before enforcing it. Alongside this, policy traces in Calico Whisker provide deep visibility into how both enforced and pending policies impact traffic. This makes it easier to understand policy behaviour, validate intent, and troubleshoot issues in real time. In this post, we’ll walk through real-world policy trace outputs and show how they help teams confidently deploy and refine network policies in production Kubernetes clusters.
Kubernetes Network Policy Behaviour
It’s important to reiterate the network policy behaviour in Kubernetes, as understanding this foundation is key to effectively interpreting policy traces and ensuring the right traffic flow decisions are Continue reading
5 Essential Steps to Strengthen Kubernetes Egress Security
Securing what comes into your Kubernetes cluster often gets top billing. But what leaves your cluster, outbound or egress traffic, can be just as risky. A single compromised pod can exfiltrate data, connect to malicious servers, or propagate threats across your network. Without proper egress controls, workloads can reach untrusted destinations, creating serious security and compliance risks. This guide breaks down five practical steps to strengthen Kubernetes egress security, helping teams protect data, enforce policies, and maintain visibility across clusters.
Why Egress Controls Matter
|
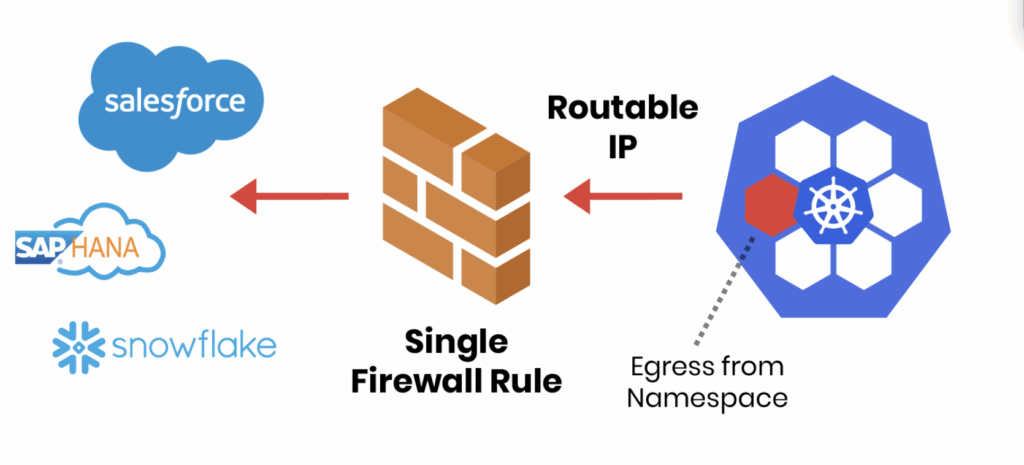
Your Kubernetes Egress Security Checklist
To help teams tackle this challenge, we’ve put together a Kubernetes Egress Security Checklist, based on best practices from real-world Continue reading
What’s New in Calico v3.31: eBPF, NFTables, and More
We’re excited to announce the release of Calico v3.31,  which brings a wave of new features and improvements.
which brings a wave of new features and improvements.
For a quick look, here are the key updates and improvements in this release:
- Calico NFTables Dataplane is now Generally Available
- Calico eBPF Dataplane Enhancements
- Simplified installation: new template defaults to
eBPF, automatically disableskube-proxyviakubeProxyManagementfield, and addsbpfNetworkBootstrapfor auto API endpoint detection. - Configurable cgroupv2 path: support for immutable OSes (e.g., Talos).
- >>Learn More: See how Calico v3.31 makes eBPF installation frictionless and simplifies setup in our Zero-Trust with Zero-Friction eBPF in Calico v3.31 blog
- Simplified installation: new template defaults to
- Calico Whisker (Observability Stack)
- Improved UI and performance in Calico v3.31.
- New policy trace categories: Enforced vs Pending.
- Lower memory use, IPv6 fixes, and more efficient flow streaming.
- Networking & QoS
- New bandwidth and packet rate QoS controls across all dataplanes.
- DiffServ (
DSCP) support: prioritize traffic by marking packets (e.g.,EFfor VoIP). - Introduces new
QoSPolicyAPI for declarative traffic control.
- Encapsulation & Routing
- Tech Preview: Felix now handles encapsulation routes (
IP-in-IP,no-encap) directly — no BIRD required!
- Tech Preview: Felix now handles encapsulation routes (
- NAT Control
- New
natOutgoingExclusionsconfig for granular NAT management. - Choose between
Continue reading
- New
When to Use BGP, VXLAN, or IP-in-IP: A Practical Guide for Kubernetes Networking
When deploying a Kubernetes cluster, a critical architectural decision is how pods on different nodes communicate. The choice of networking mode directly impacts performance, scalability, and operational overhead. Selecting the wrong mode for your environment can lead to persistent performance issues, troubleshooting complexity, and scalability bottlenecks.
The core problem is that pod IPs are virtual. The underlying physical or cloud network has no native awareness of how to route traffic to a pod’s IP address, like 10.244.1.5 It only knows how to route traffic between the nodes themselves. This gap is precisely what the Container Network Interface (CNI) must bridge.
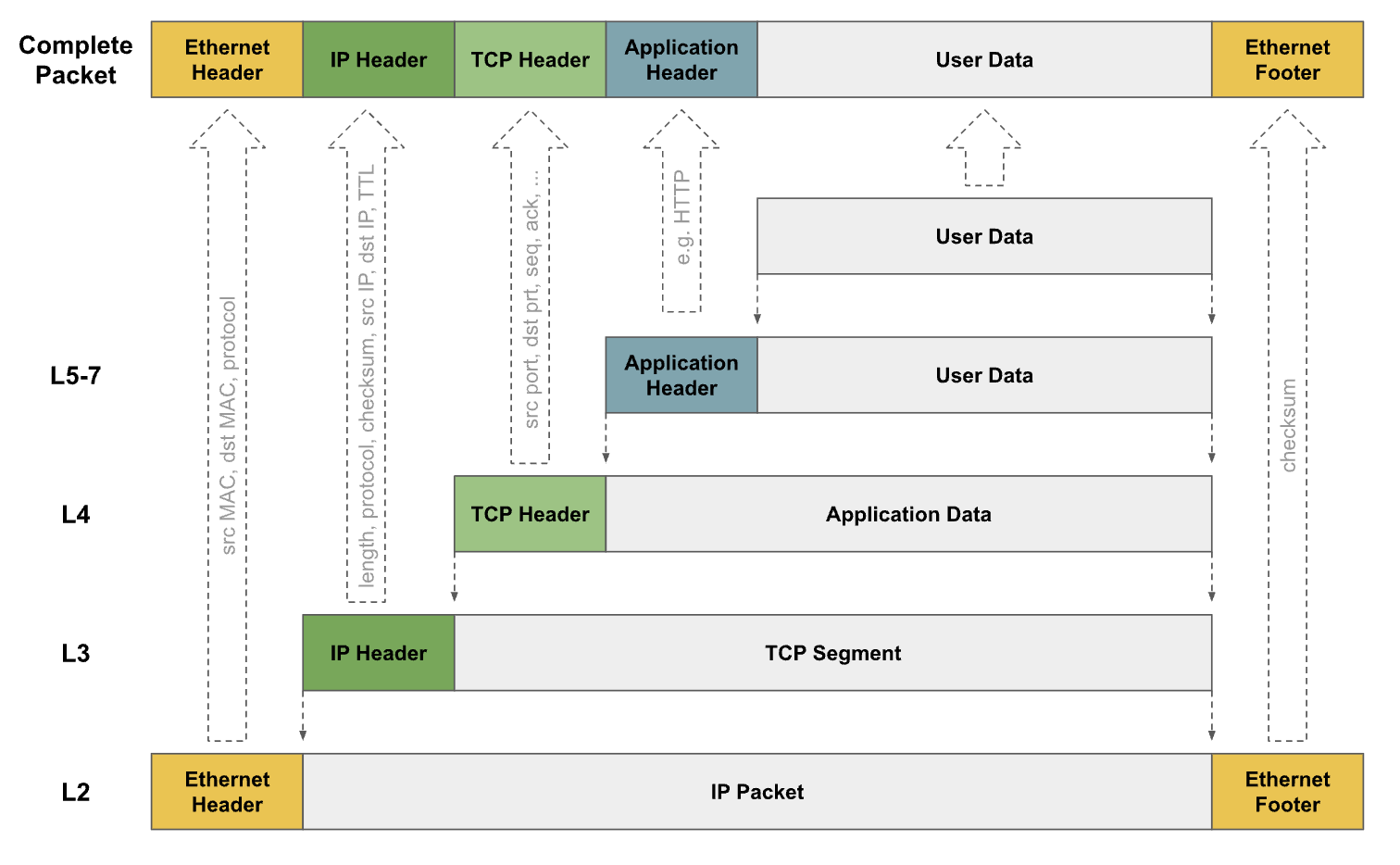
The CNI employs two primary methods to solve this problem:
- Overlay Networking (Encapsulation): This method wraps a pod’s packet inside another packet that the underlying network understands. The outer packet is addressed between nodes, effectively creating a tunnel. VXLAN and IP-in-IP are common encapsulation protocols.
- Underlay Networking (Routing): This method teaches the network fabric itself how to route traffic directly to pods. It uses a routing protocol like BGP to advertise pod IP routes to the physical Continue reading
How NRP Scales Global Scientific Research with Calico

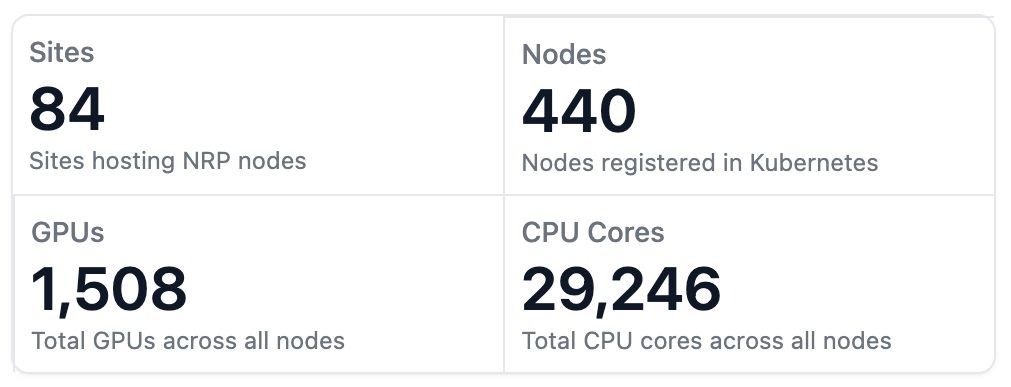
The National Research Platform (NRP) operates a globally distributed, high-performance computing and networking environment, with an average of 15,000 pods across 450 nodes supporting more than 3,000 scientific project namespaces. With its head node in San Diego, NRP connects research institutions and data centers worldwide via links ranging from 10 to 400 Gbps, serving more than 5,000 users in 70+ locations.
- Non-profit company
- Uses Calico Open Source
NRP is a partnership of more than 50 institutions, led by researchers at UC San Diego, University of Nebraska-Lincoln, and Massachusetts Green High Performance Computing Center and includes contributions by the National Science Foundation, the Department of Energy, the Department of Defense, and many research universities and R&E networking organizations in the US and around the world.
Challenges
Complex Network Visibility and Debugging
NRP needed a way to diagnose connectivity problems across globally distributed storage nodes. Frequent changes to edge network configurations, ACLs, firewalls, and static routes caused blocked ports, forcing manual troubleshooting with tools such as nmap and iperf. This process slowed down root-cause analysis and problem resolution.
Balancing Performance with Granular Security at Scale
Scientific workflows demanded maximum throughput over 100/400 Gbps links and jumbo frames. Traditional host firewalls introduced unacceptable Continue reading
How to Deploy Whisker and Goldmane in Manifest Only Calico Setups
Your Step-by-Step to Observability Without the Operator
If you’re running Calico using manifests, you may have found that enabling the observability features introduced in version 3.30, including Whisker and Goldmane, requires a more hands-on approach. Earlier documentation focused on the Tigera operator, which automates key tasks such as certificate management and secure service configuration. In a manifest-based setup, these responsibilities shift to the user. While the process involves more manual steps, it provides greater transparency and control over each component. With the right guidance, setting up these observability tools is entirely achievable and offers valuable insight into the internal behavior of your Calico deployment.
We’ve heard from many of you in the Calico Slack community: you’re eager to try out Whisker and Goldmane but aren’t sure how to set them up without Helm or the operator. For anyone who’s up for a challenge, this blog post provides a step-by-step guide on how to get everything wired up the hard way.
However, even if you already use the operator, keep reading! We’re going to pull back the curtain on the magic it performs behind the scenes. Understanding these mechanics will help you troubleshoot, customize, and better appreciate a managed Continue reading
SUSE and Tigera: Empowering Secure, Scalable Kubernetes with Calico Enterprise
Modern Workloads Demand Modern Kubernetes Infrastructure
As organizations expand Kubernetes adoption—modernizing legacy applications on VMs and bare metal, running next-generation AI workloads, and deploying intelligence at the edge—the demand for infrastructure that is scalable, flexible, resilient, secure, and performant has never been greater. At the same time, compliance, consistent visibility, and efficient management without overburdening teams remain critical.
The combination of Calico Enterprise from Tigera and SUSE Rancher Prime delivers a resilient and scalable platform that combines high-performance networking, robust network security, and operational simplicity in one stack.
Comprehensive Security Without Compromise
Calico Enterprise provides a unified platform for Kubernetes networking, security, and observability:
- eBPF-powered networking for high performance without sidecar overhead
- One platform for all Kubernetes traffic: ingress, egress, in-cluster, and multi-cluster
- Security for every workload type: containers, VMs, and bare metal
- Seamless scaling with built-in multi-cluster networking and security
- Zero-trust security with identity-aware policies and workload-based microsegmentation
- Integrated observability for policy enforcement and troubleshooting
- Compliance features that simplify audits (PCI-DSS, HIPAA, SOC 2, FedRAMP)
Deployed with Rancher Prime, these capabilities extend directly into every cluster, enabling security-conscious industries such as finance, healthcare, and government to confidently run Kubernetes for any use case—from application modernization to AI and edge Continue reading
How to Connect Nested KubeVirt Clusters with Calico and BGP Peering
Running Kubernetes inside Kubernetes isn’t just a fun experiment anymore – it’s becoming a key pattern for delivering multi-environment platforms at scale. With KubeVirt, a virtualization add-on for Kubernetes that uses QEMU (an open-source machine emulator and virtualizer), you can run full-featured Kubernetes clusters as virtual machines (VMs) inside a parent Kubernetes cluster. This nested architecture makes it possible to unify containerized and virtualized workloads, and opens the door to new platform engineering use cases.
But here’s the challenge: how can you ensure that these nested clusters, and the workloads within, can reach, and be reached by, your physical network and are treated the same way as any other cluster?
That’s where Calico’s Advanced BGP (Border Gateway Protocol) peering with workloads comes into play. By enabling BGP route exchange between the parent cluster and nested KubeVirt VMs, Calico extends dynamic routing directly to virtualized workloads. This allows nested clusters to participate in the broader network topology and advertise their pod and service IPs just like any other node. Thus eliminating the need for tunnels or overlays to achieve true layer 3 connectivity.
In this blog, we’ll walk through the big picture, prerequisites, and step-by-step configuration for setting up BGP Continue reading
Calico Whisker vs. Traditional Observability: Why Context Matters in Kubernetes Networking
Are you tired of digging through cryptic logs to understand your Kubernetes network? In today’s fast-paced cloud environments, clear, real-time visibility isn’t a luxury, it’s a necessity. Traditional logging and metrics often fall short, leaving you without the context needed to troubleshoot effectively.
That’s precisely what Calico Whisker’s recent launch (with Calico v3.30) aims to solve. This tool provides clarity where logs alone fall short. In the sections below, you’ll get a practical overview of how it works and how it fits into modern Kubernetes networking and security workflows.
If you’re relying on logs for network observability, you’re not alone. While this approach can provide some insights, it’s often a manual, resource-intensive process that puts significant load on your distributed systems. It’s simply not a cloud-native solution for real-time insights.
So are we doomed? No. Calico Whisker transforms network observability from a chore into a superpower.
What is Calico Whisker?
Calico Whisker is a free, lightweight, Kubernetes-native observability user interface (UI) created by Tigera and introduced with Calico Open Source v3.30. It’s designed to give you a simple yet powerful window into your cluster’s network traffic, helping you understand network flows and evaluate policy behavior in real-time.
Securing AI Workloads in Kubernetes: Why Traditional Network Security Isn’t Enough
The AI revolution is here, and it’s running on Kubernetes. From fraud detection systems to generative AI platforms, AI-powered applications are no longer experimental projects; they’re mission-critical infrastructure. But with great power comes great responsibility, and for Kubernetes platform teams, that means rethinking security.
But this rapid adoption comes with a challenge: 13% of organizations have already reported breaches of AI models or applications, while another 8% don’t even know if they’ve been compromised. Even more concerning, 97% of breached organizations reported that they lacked proper AI access controls. To address this, we must recognize that AI architectures introduce entirely new attack vectors that traditional security models aren’t equipped to handle.
AI Architectures Introduce New Attack Vectors
AI workloads running in Kubernetes environments introduce a new set of security challenges. Traditional security models often fall short in addressing the unique complexities of AI pipelines, specifically related to The Multi-Cluster Problem, The East-West Traffic Dilemma, and Egress Control Complexity. Let’s explore each of these critical attack vectors in detail.
The Multi-Cluster Problem
Most enterprise AI deployments don’t run in a single cluster. Instead, they typically follow this pattern:
Training Infrastructure (GPU-Heavy)
- Dedicated clusters with high-memory GPU nodes
- Batch job Continue reading
Navigating DORA with Calico: Strengthening Kubernetes Operational Resilience in Financial Services
A single cyberattack or system outage can threaten not just one financial institution, but the stability of a vast portion of the entire financial sector. For today’s financial enterprises, securing dynamic infrastructure like Kubernetes is a core operational and regulatory challenge. The solution lies in achieving DORA compliance for Kubernetes, which transforms your cloud-native infrastructure into a resilient, compliant, and secure backbone for critical financial services.
The Challenge DORA Seeks to Solve
Before DORA (Digital Operational Resilience Act), rules for financial companies primarily focused on making sure they had enough financial capital to cover losses. But what if a cyberattack or tech failure brought a large part of the financial system down? Even with plenty of financial capital, a major outage could stop most operations and cause big problems for the whole financial market. DORA steps in to fix this. It’s all about making sure financial firms can withstand, respond to, and recover quickly from cyberattacks and other digital disruptions.
What is DORA?
The Digital Operational Resilience Act (DORA) is a European Union (EU) regulation that came into effect on January 17, 2025 and is designed to strengthen the security of financial entities. It establishes uniform requirements across the financial Continue reading
Calico Egress Gateway: A Cost-Effective NAT for Kubernetes
The Need for a Kubernetes NAT Gateway
When Kubernetes workloads need to connect to the outside world, whether to access external APIs, integrate with external systems, or connect to partner networks, they often face a unique challenge. The problem? Pod IP addresses inside Kubernetes clusters are dynamic and non-routable. For external systems to recognize and trust this traffic, workloads need a consistent, dependable identity. This means outbound connections require fixed, routable IP addresses that external services can rely on. This is where Network Address Translation (NAT) becomes essential. It assigns Kubernetes pods with a static, consistent IP for all outbound traffic, ensuring those connections work properly.
If you’re running Kubernetes in the cloud, a common solution is to use your cloud provider’s managed NAT gateway service. These are easy to use, but they can come at a cost. In AWS, Azure, and Google Cloud, cloud-managed NAT gateways charge both an hourly fee and a per-gigabyte data processing fee. For high-traffic deployments, those charges can quickly add up, sometimes even exceeding your compute costs.
The good news: with Calico, you can handle NAT from inside your Kubernetes cluster, avoiding cloud NAT gateway fees and giving you more control over how egress Continue reading
What’s New in Calico – Summer 2025
As Kubernetes adoption scales across enterprise architectures, platform architects face mounting pressure to implement consistent security guardrails across distributed, multi-cluster environments while maintaining operational velocity. Modern infrastructure demands a security architecture that can adapt without introducing complexity or performance penalties. Traditional approaches force architects to cobble together separate solutions for ingress protection, network policies, and application-layer security, creating operational friction and increasing attack surface.
Today, we’re announcing significant enhancements to Calico that eliminate this architectural complexity. This release introduces native Web Application Firewall (WAF) capabilities integrated directly into Calico’s Ingress Gateway, enabling platform architects to deploy a single technology stack for both ingress management and HTTP-layer threat protection. Combined with enhanced Role-Based Access Controls (RBAC) controls, and centralized observability across heterogeneous workloads, platform architects can now design and implement comprehensive security all within a unified platform.
The new features in this release can be grouped under two main categories:
- Security at Scale with a Unified Platform: This release introduces critical security features that make it easier to secure and scale Kubernetes workloads.
- Simplified Operations for Kubernetes, VM, and bare metal workloads: Reducing complexity is key to scaling Kubernetes, VM, and bare metal workloads, and this release introduces features that make Continue reading
Calico at CalicoCon, KubeCon + CloudNativeCon North America 2025!
The Calico team was thrilled to participate in KubeCon + CloudNativeCon North America 2025, where we’ll be showcasing the latest advancements in Kubernetes networking, network security, and observability. We’re excited to connect with the vibrant cloud-native community, share insights, and demonstrate how Calico Open Source continues to empower organizations worldwide.
Quick Links
- CalicoCon North America 2025
- Happy Hour with Calico
- KubeCon + CloudNativeCon North America 2025
 Go Deeper: Calico Silent Disco Schedule at Booth #521
Go Deeper: Calico Silent Disco Schedule at Booth #521
Nov 10: CalicoCon North America 2025
CalicoCon North America 2025, your go-to event for the latest in Kubernetes networking, network security, and observability.
Hosted by the Calico team, this hybrid event is your chance to hear directly from Calico engineers and leadership, get hands-on with new features, and take an in-depth look at the state of Project Calico.
We’ll dive into Calico 3.30, Calico eBPF, and Calico Whisker: open source observability for Kubernetes.
To view the full agenda & register, see below or click here:
Event Details
Date: November 10, 2025
Time: 1:00pm to 5:00pm EST
Location: Virtual | The Westin Peachtree Plaza Atlanta
Nov 10: Happy Hour with Calico
After a day of deep dives and technical Continue reading
How 1&1 Mail & Media Scaled Kubernetes Networking with eBPF and Calico
“We started in 2017 with Calico and never regretted it!”
—Stefan Fudeus, Product Owner/Lead Architect, 1&1 Mail & Media
Challenge
1&1 Mail & Media, part of the IONOS group, powers popular European internet brands including GMX and Web.de, serving more than 50% of Germany’s population with critical identity and email infrastructure. With roughly 45 to 50 million users, network reliability is non-negotiable. Any downtime could affect millions.
By 2022, the company had containerized 80% of its workloads on Kubernetes across three self-managed data centers. While the platform, backed by bare metal nodes and custom network layers, was highly scalable, network throughput bottlenecks began to emerge. Pods were limited to 2.5 Gbps of bandwidth due to IP encapsulation overhead, despite 10 Gbps network interfaces.
The team needed a solution that:
- Improved pod-to-pod network performance
- Maintained strong network policy isolation across up to 40 tenants per cluster
- Scaled to millions of network connections and 1.4 million HTTP requests per second
Solution
1&1 Mail & Media had adopted Calico back in 2017, largely for its unique Kubernetes NetworkPolicy standard support. As their Kubernetes platform evolved, with clusters scaling to 300 bare metal nodes, 16,000 pods, and over 4 million Continue reading
Top 5 Kubernetes Network Issues You Can Catch Early with Calico Whisker
Kubernetes networking is deceptively simple on the surface, until it breaks, silently leaks data, or opens the door to a full-cluster compromise. As modern workloads become more distributed and ephemeral, traditional logging and metrics just can’t keep up with the complexity of cloud-native traffic flows.
That’s where Calico Whisker comes in. Whisker is a lightweight Kubernetes-native observability tool created by Tigera. It offers deep insights into real-time traffic flow patterns, without requiring you to deploy heavyweight service meshes or packet sniffer. And here’s something you won’t get anywhere else: Whisker is data plane-agnostic. Whether you run Calico eBPF data plane, nftables, or iptables, you’ll get the same high-fidelity flow logs with consistent fields, format, and visibility. You don’t have to change your data plane, Whisker fits right in and shows you the truth, everywhere.
Let’s walk through 5 network issues Whisker helps you catch early, before they turn into outages or security incidents.
1. Policy Misconfigurations
Traditional observability tools often show whether a packet was forwarded, accepted or dropped, but not why. They lack visibility into which Kubernetes network policy was responsible or if one was even applied.
With Whisker, each network flow is paired with:
- The enforced policy name Continue reading
Kubernetes Is Powerful, But Not Secure (at least not by default)
Kubernetes has transformed how we deploy and manage applications. It gives us the ability to spin up a virtual data center in minutes, scaling infrastructure with ease. But with great power comes great complexities, and in the case of Kubernetes, that complexity is security.
By default, Kubernetes permits all traffic between workloads in a cluster. This “allow by default” stance is convenient during development, and testing but it’s dangerous in production. It’s up to DevOps, DevSecOps, and cloud platform teams to lock things down.
To improve the security posture of a Kubernetes cluster, we can use microsegmentation, a practice that limits each workload’s network reach so it can only talk to the specific resources it needs. This is an essential security method in today’s cloud-native environments.
Why Is Microsegmentation So Hard?
We all understand that network policies can achieve microsegmentation; or in other words, it can divide our Kubernetes network model into isolated pieces. This is important since Kubernetes is usually used to provide multiple teams with their infrastructural needs or host multiple workloads for different tenants. With that, you would think network policies are first citizens of clusters. However, when we dig into implementing them, three operational challenges Continue reading

 Go Deeper: Calico Silent Disco Schedule at Booth #521
Go Deeper: Calico Silent Disco Schedule at Booth #521