Case study: Calico Enterprise empowers Aldagi to achieve EU GDPR compliance
Founded in 1990, Aldagi is Georgia’s first and biggest private insurance firm. With a 32% market share in Georgia’s insurance sector, Aldagi provides a broad range of services to corporate and retail clients.
With the onset of the pandemic in 2019, Aldagi wanted to make its services available to customers online. To this end, the company adopted an Agile methodology for software development and re-architected its traditional VM-based applications into cloud-native applications. Aldagi then began using containers and Kubernetes as a part of this process. Using self-managed clusters on Rancher Kubernetes Engine (RKE), Aldagi created distributed, multi-tenant applications to serve its broad EU customer base.
In collaboration with Tigera, Aldagi details its journey using Calico to achieve EU GDPR compliance, in order to share its experience with the rest of the Kubernetes community.

Case study highlights
Because Aldagi’s applications are distributed and multi-tenanted, the company faced three major challenges when it came to achieving EU GDPR compliance:
- Granular access control
- Visibility and security controls for workloads with sensitive data
- Continuous compliance reporting and auditing
By deploying Calico, Aldagi solved these challenges and achieved EU GDPR compliance, Continue reading
Kubernetes network security foundations: Get started on building your Kubernetes network security policies with Calico!
The adoption of cloud native applications has become a necessity for organizations to run their businesses efficiently. As per Gartner, more than 85% of organizations will embrace a cloud-first principle by 2025, which will rely on adopting cloud native applications for complete execution. The massive increase in adoption of cloud native applications has given rise to more security challenges such as container image vulnerabilities, configuration errors and a larger runtime attack surface. Kubernetes has become the de facto standard platform to host and run cloud native applications. However, as Kubernetes adoption gains momentum, so does the security risk associated with business-critical applications that communicate with multiple external and internal systems. Kubernetes network security is a critical aspect of securing cloud native applications and the Kubernetes platform itself. This multi-part blog series aims to explore the network security challenges of the Kubernetes environment and provide insights into mitigating them using Calico security controls. The series will cover various aspects of network security, including security policies, application layer security, host network security, Pod traffic encryption, and the importance of a defense-in-depth security approach. Let’s dive into the world of Kubernetes network security and learn how to protect your organization’s valuable assets.
Detect malicious activity and protect your containerized workloads in Amazon EKS or AWS
As containerized applications become increasingly complex, it can be challenging to design and execute an effective container security strategy. With the growing trend towards cloud-based applications and services, cyber criminals are also evolving their attack techniques, making container security solutions more critical than ever. Calico provides robust detection capabilities to detect known and zero-day container and network-based attacks. In this blog, we will look at Calico’s capabilities to detect network-based attacks.
Calico offers comprehensive protection against both known and zero-day network-based attacks. Using a combination of workload-based IDS/IPS, Calio can detect and block connections to known malicious IPs identified with AlienVault and custom threat intelligence feeds. Calico also uses heuristics-based learning to identify anomalous network activity and prevent zero-day attacks. To further protect against OWASP Top 10 attacks, Calico provides a web application firewall (WAF) that can intercept attacks and prevent them from reaching your applications. Additionally, Calico can also block requests from malicious IPs to prevent DDoS attacks from overwhelming your system.
Malicious attack on cloud-native application and how to prevent it
In this blog, we will go through a scenario where an attacker compromises a public-facing application and gains a foothold in the AWS EC2 or EKS network Continue reading
How to integrate Calico Image Scanner with Argo CI/CD
In today’s fast-paced software development environment, developers often use common public libraries and modules to quickly build applications. However, this presents a significant challenge for DevOps teams who must ensure that these applications are safe to use. As organizations move towards dynamic models of software development that rely on Continuous Integration and Continuous Deployment, the responsibility for deploying secure applications has shifted from traditional security teams to development teams.
To address this challenge, I will provide general guidelines on how to integrate the Calico Image Scanning feature into a CI/CD pipeline, using Argo. This will help ensure that images are built safely and free from Common Vulnerabilities and Exposures (CVEs). In this blog post, we will use a Kubernetes validating webhook configuration to attach a Calico Cloud admission controller that can accept or reject certain actions on resources, such as the creation of pods. This will prevent the deployment of images that contain known CVEs, thus strengthening the overall security of your software development process.
Overall Architecture
The building blocks to use Argo as an example of this integration are below:
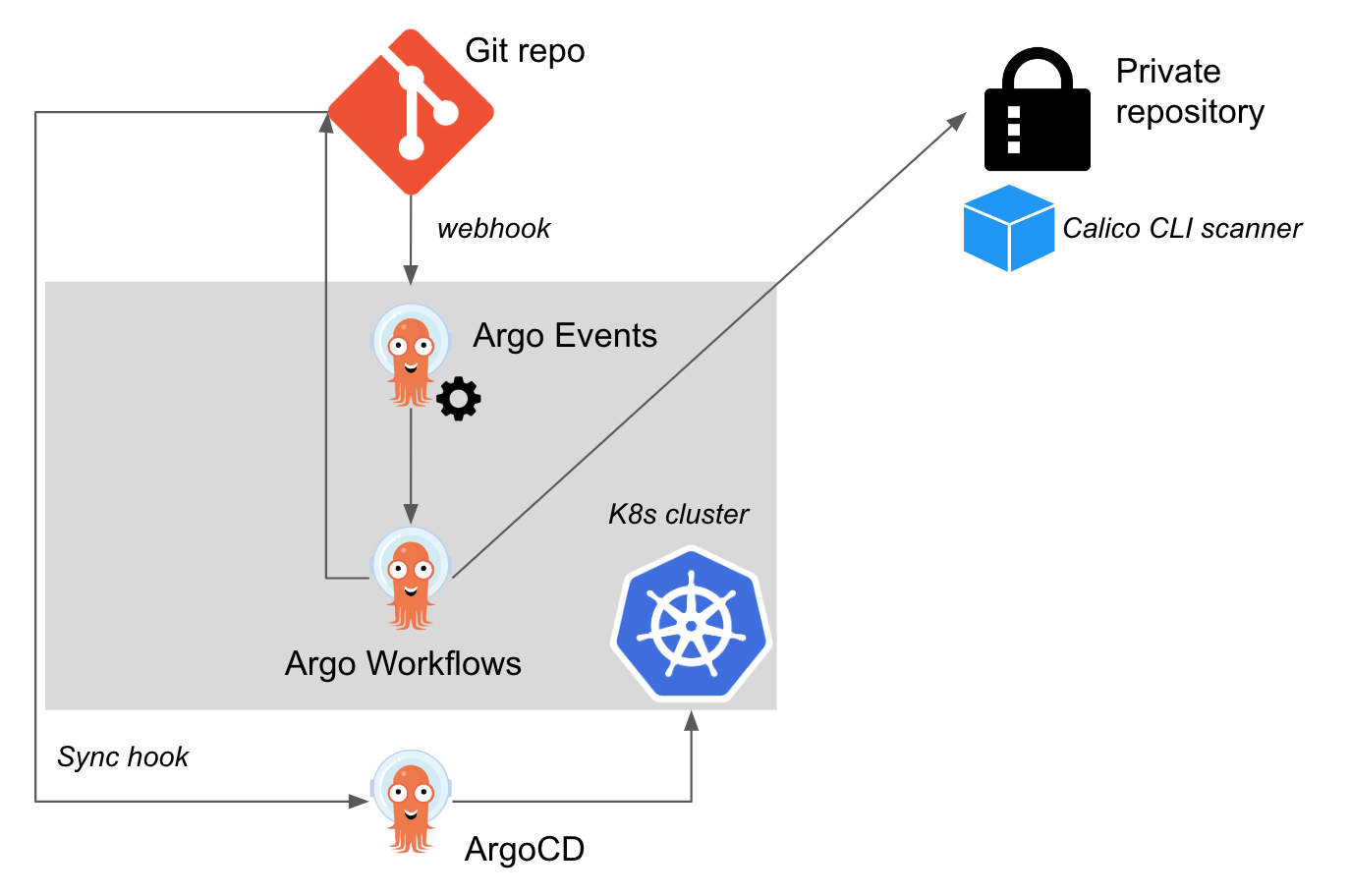
Relevant Calico configuration
Before even committing changes to our application, we must setup the Calico Admission Controller within our Continue reading
Tigera named as one of Forbes America’s Best Startup Employers in 2023
We are proud to announce that we have been named one of America’s Best Startup Employers 2023 by Forbes!
The Forbes list of America’s Best Startup Employers 2023 was compiled by evaluating 2,600 companies with at least 50 employees in the United States. All of the companies considered were founded between 2013 and 2020, from the ground up, and were not spin-offs of existing businesses. Just like other Forbes lists, businesses cannot pay to be considered. Evaluation was based on three criteria: employer reputation, employee satisfaction, and growth.
Great Place to Work 2022
2022

Inclusion in Forbes’ list comes after we were proudly certified as a Great Place to Work in 2022.
in 2022.
The Great Place to Work Certification recognizes employers that create an exceptional employee experience. The certification process involves surveying employees and the employer, and rankings are based on employee feedback and independent analysis. This means job searchers can rely on the certification to help them determine whether an organization is truly a great place to work.
Go Tigers!
Our core values are the foundation of everything we do. Tigera believes in a collaborative, flexible work environment built on mutual respect and commitment. We are delighted to hear that our Continue reading
Overcoming Security Gaps with Active Vulnerability Management
Organizations can reduce security risks in containerized applications by actively managing vulnerabilities through scanning, automated image deployment, tracking runtime risk and deploying mitigating controls to reduce risk
Kubernetes and containers have become de facto standards for cloud-native application development due to their ability to accelerate the pace of innovation and codify best practices for production deployments, but such acceleration can introduce risk if not operationalized properly.
In the architecture of containerized applications, it is important to understand that there are highly dynamic containers distributed across cloud environments. Some are ephemeral and short-lived, while others are more long-term. Traditional approaches to securing applications do not apply to cloud-native workloads because most deployments of containers occur automatically with an orchestrator that removes the manual step in the process. This automatic deployment requires that the images be continuously scanned to identify any vulnerabilities at the time of development in order to mitigate the risk of exploit during runtime.
In addition to these challenges, software supply chain adds complexity to vulnerability scanning and remediation. Applications increasingly depend on containers and components from third-party vendors and projects. As a result, it can take weeks or longer to patch the affected components and release new software Continue reading
Monitoring Kubernetes clusters activity with Azure Managed Grafana and Calico
Cloud computing revolutionized how a business can establish its digital presence. Nowadays, by leveraging cloud features such as scalability, elasticity, and convenience, businesses can deploy, grow, or test an environment in every corner of the world without worrying about building the required infrastructure.
Unlike the traditional model, which was based on notifying the service provider to set up the resources for customers in advance, in an on-demand model, cloud providers implement application programming interfaces (API) that can be used by customers to deploy resources on demand. This allows the customer to access an unlimited amount of resources on-demand and only pay for the resources they use without worrying about the infrastructure setup and deployment complexities.
For example, a load balancer service resource is usually used to expose an endpoint to your clients. Since a cloud provider’s bandwidth might be higher than what your cluster of choice can handle, a huge spike or unplanned growth might cause some issues for your cluster and render your services unresponsive.
To solve this issue, you can utilize the power of proactive monitoring and metrics to find usage patterns and get insight into your system’s overall health and performance.
In this hands-on tutorial, I will Continue reading
Community Spotlight series: Calico Open Source user insights from Saurabh Mishra
In this issue of the Calico Community Spotlight series, I’ve asked Saurabh Mishra from Vodafone to share his experience with Kubernetes and Calico Open Source. Let’s take a look at how Saurabh started his Kubernetes journey and the insights he gained from Calico Open Source.
Q: Please tell us a little bit about yourself, including where you currently work and what you do there.
I am working as a DevOps Manager with Vodafone Group. I am responsible for managing Kubernetes and cloud-based environments. I’m particularly interested in all things related to cloud, automation, machine learning, and DevOps.
Q: What orchestrator(s) have you been using?
Kubernetes.
Q: What cloud infrastructure(s) has been a part of your projects?
Amazon Elastic Kubernetes Service (EKS) and Google Kubernetes Engine (GKE).
Q: There are many people who are just getting started with Kubernetes and might have a lot of questions. Could you please talk a little bit about your own journey?
Kubernetes is a fully open-source project. It’s purposely designed this way so it can work with other open-source tools to create continuous improvements and innovations. In our team, we are using Kubernetes in non-production and production environments to run and manage critical Continue reading
RSAC 2023 interview: Tigera talks cloud-native security on theCUBE
During RSA Conference 2023, Utpal Bhatt sat down with SiliconANGLE & theCUBE host, John Furrier, to talk cloud-native security. Watch the full interview below.
Here’s a sneak peak of what’s inside…
“Cloud-native applications have fundamentally changed how security gets done. There are a lot of challenges that cloud-native applications bring to the table, given their large attack surface. You have attack vectors in your coding, CI/CD pipeline, deployment, and runtime. And I think that’s what organizations are realizing, that hey, this is fundamentally a different kind of architecture and we need to look at it differently.” —Utpal Bhatt, CMO at Tigera
“Cloud-native applications have fundamentally changed how security gets done. And there are a lot of challenges that cloud-native applications bring to the table, which is what organizations are realizing. If you think about organizations moving into the cloud, the majority have traditionally done a lift and shift. But now they’re recognizing that in order to get the economics right, they need to start developing cloud-native technologies, which are highly distributed, ephemeral, and transient. So all your standard security tools just really don’t work in that environment because you have a really large Continue reading
What you can’t do with Kubernetes network policies (unless you use Calico)
Kubernetes documentation clearly defines what use cases you can achieve using Kubernetes network policies and what you can’t. You are probably familiar with the scope of network policies and how to use them to secure your workload from undesirable connections. Although it is possible to cover the basics with Kubernetes native network policies, there is a list of use cases that you cannot implement by just using these policies.
You can refer to the Kubernetes documentation to review the list of “What you can’t do with network policies (at least, not yet)”.
Here are some of the use cases that you cannot implement using only the native network policy API (transcribed from the Kubernetes documentation):
- Forcing internal cluster traffic to go through a common gateway.
- Anything TLS related.
- Node specific policies.
- Creation or management of “Policy requests” that are fulfilled by a third party.
- Default policies which are applied to all namespaces or pods.
- Advanced policy querying and reachability tooling.
- The ability to log network security events.
- The ability to explicitly deny policies.
- The ability to prevent loopback or incoming host traffic (Pods cannot currently block localhost access, nor do they have the ability to block access from Continue reading
Using Calico Egress gateway and access controls to secure traffic
As more organizations embrace containerization and adopt Kubernetes, they reap the benefits of platform scalability, application portability, and optimized infrastructure utilization. However, with this shift comes a new set of security challenges related to enabling connectivity for applications in heterogeneous environments.
In this blog post, we’ll explore a real-life scenario of security exposure resulting from egress traffic leaving the Kubernetes cluster. We’ll examine how the Calico Egress Gateway can help mitigate these issues by providing robust access control. By using Calico Egress Gateway, enterprises can secure communication from their Kubernetes workloads to the internet, 3rd party applications and networks while maintaining a high level of security.
The Calico Egress Gateway enforces security policies to regulate traffic flowing out of the Kubernetes cluster, providing granular control over egress traffic. This ensures that only authorized traffic is allowed to leave the cluster, mitigating the risks associated with unauthorized outbound traffic.
Egress security challenges
For enterprises developing cloud-native applications with containers and Kubernetes, a frequent requirement is to connect to a database server hosted either on-prem or in the cloud, which is safeguarded by a network-based firewall. Since workloads with Kubernetes are dynamic without a fixed IP address, enabling such connectivity from workloads Continue reading
Calico’s 3.26.0 update unlocks high density vertical scaling in Kubernetes
Kubernetes is a highly popular and widely used container orchestration platform designed to deploy and manage containerized applications at a scale, with strong horizontal scaling capabilities that can support up to 5,000 nodes; the only limit in adding nodes to your cluster is your budget. However, its vertical scaling is restricted by its default configurations, with a cap of 110 pods per node. To maximize the use of hardware resources and minimize the need for costly horizontal scaling, users can adjust the kubelet maximum pod configuration to increase this limit allowing more pods to run concurrently on a single node.
To avoid network performance issues and achieve efficient horizontal scaling in a Kubernetes cluster that is tasked to run a large number of pods, high-speed links and switches are essential. A reliable and flexible Software Defined Networking (SDN) solution, such as Calico, is also important for managing network traffic efficiently. Calico has been tested and proven by numerous companies for horizontal scaling, but in this post, we will discuss recent improvements made to help vertical scaling of containerized applications to just work.
For example, the following chart illustrates the efficiency achieved with the improvements of vertical scaling in Calico 3. Continue reading
Tigera Named Winner of the Esteemed Global InfoSec Awards during RSA Conference 2023
The annual Global InfoSec Awards from Cyber Defense Magazine (CDM) have been announced, and we are excited to unveil that Tigera has won the ‘Hot Company: Container Security’ category! This award recognizes the value of the work Tigera does as a security company, and we wouldn’t be where we are without the support of our teams, customers, and community.
“We are honored to be recognized as one of the best in container security by Cyber Defense Magazine. As this is one of the most esteemed awards in cybersecurity, we are so grateful to have been selected amongst a pool of qualified applicants and are eager to continue to innovate and provide better container security for organizations,” said Amit Gupta, Chief Product Officer, Tigera.
Tigera’s transformative approach to container security helps prevent, detect, and mitigate threats in containers and Kubernetes environments across build, deploy and runtime stages. Calico Cloud provides a unique solution that gives users a single container security solution to improve security posture, reduce the attack surface with fine-grained security controls, and provide threat defense from network and host based threats.
Cyber Defense Magazine is the Continue reading
Leveraging security policy recommender to tighten your cluster’s security posture
We’ve noticed that many of our customers are currently undergoing a significant transformation in their application architecture, transitioning from legacy vertical applications to distributed microservices running on Kubernetes. This shift brings along a range of benefits, such as improved scalability, resilience, and agility. However, it also creates a larger attack surface that needs to be managed effectively.
To minimize the attack surface, it is crucial to have a clear understanding of how each microservice communicates microservices within, and outside, the cluster to implement robust network configuration and security policies. This can be challenging, especially when dealing with re-architected applications that can consist of hundreds of microservices.
To make the life of the security and DevOps teams easier, there are a few things that can be done. Firstly, providing them with access to detailed information on how microservices communicate within and outside the cluster. Secondly, having automated policy recommendations to improve their configuration and security. Finally, providing visibility and audit reports to help identify vulnerabilities in the system and prevent potential breaches.
In this blog, we will discuss how to leverage the security policy recommender to rapidly create security policies to minimize the attack surface and improve the security posture.
Gathering Continue reading
Hands-on guide: How to scan and block container images to mitigate SBOM attacks
According to OpenLogic’s Open Source Adoption and Expansion in 2022 Report, the adoption of Open Source Software (OSS) across all sizes of organizations is rising with 40% of respondents stating an increase of OSS software over the previous year and 36% reporting a significant increase in OSS software usage. The increase in OSS adoption can be attributed to a number of factors including access to the latest innovations, reduction in costs and frequent product updates. However, leveraging community contribution introduces the potential for malicious code to be attached. For example, a series of 2022 case studies conducted by the Package Analysis project, part of the Open Source Security Foundation (OpenSSF), details a number of malicious packages from widely used repositories such as PyPi and NPM. Therefore, it is essential to determine the vulnerabilities in any container image before its deployment into the environment. Calico Cloud’s Image Assurance capabilities enables Vulnerability Assessment for any image. We often hear this referred to as Image Scanning.
Looking for vulnerabilities in images
In order to assess the posture of container images the components that make up an image must be broken down. We refer to this inventory as the Software Bill of Materials Continue reading
White paper: Addressing the MITRE ATT&CK framework for containers using Calico
Be it chess, poker, or everyday driving, you must predict your opponent’s (or other drivers’) movement to win (or keep yourself safe!). Container security is the same, and many organizations look to the MITRE Adversarial Tactics, Techniques, and Common Knowledge (ATT&CK) framework to understand an attacker’s mindset and how to prevent attacks. The MITRE ATT&CK framework released a matrix for containers, giving organizations that use Kubernetes and containers a chance to analyze an attacker’s M.O. and assess the organization’s attack vectors.
To help organizations stay ahead of attackers, Tigera recently released a white paper based on the MITRE ATT&CK containers matrix. Drawing from Tigera’s experience as a cybersecurity provider, the white paper offers an in-depth analysis of the containers matrix. It also details how Tigera’s active security platform, Calico Cloud, a fully-managed SaaS, and its self-managed counterpart, Calico Enterprise, can detect and mitigate every tactic outlined in the matrix.
White paper highlights
Tigera’s white paper dives deep into the MITRE framework for containers to help organizations understand the risks they face and how they can mitigate these vulnerabilities using Calico. Here’s what you will learn from the white paper and the questions it’ll answer:
- Attack vectors of Continue reading
What is SOC 2 and how do you achieve SOC 2 compliance for containers and Kubernetes?
SOC 2 is a compliance standard for service organizations, developed by the American Institute of CPAs (AICPA), which specifies how organizations should manage customer data. SOC 2 is based on five overarching Trust Services Criteria (TSC): security, availability, processing integrity, confidentiality, and privacy. Specifically, the security criteria are broken down into nine sections called common criteria (CC):
- CC1: Control Environment
- CC2: Communication and Information
- CC3: Risk Assessment
- CC4: Monitoring Activities
- CC5: Control Activities
- CC6: Logical and Physical Access Controls
- CC7: System Operations
- CC8: Change Management
- CC9: Risk Mitigation
How does SOC 2 compliance apply to containers and Kubernetes?
Running Kubernetes clusters often presents challenges for CC6 (logical and physical access), CC7 (systems operations), and CC8 (change management) when trying to comply with SOC 2 standards.
In this technical blog, we will dive into how Calico can help you achieve full compliance in achieving all the requirements of CC6. To understand how to achieve compliance with CC7 and CC8, you can review our SOC 2 white paper.
| Control # | Compliance requirements | Calico controls |
| CC 6.1, 6.6, 6.7, 6.8
|
Implement logical access security measures to authorized systems only, implement controls to prevent or detect and act upon Continue reading |
Project Calico wants to hear from you! The 2023 Calico Open Source Adoption Survey
Project Calico is made possible thanks to you—thank you for your ongoing support of Project Calico, and for being an essential part of our growing open-source community. To improve Calico, we want to hear from you.
That’s why we’ve created the 2023 Calico Open Source Adoption Survey, a 16-question survey designed specifically to help us gather your feedback and insights.
Why take this survey?
Not only will this be a chance to share extensive feedback, your input will actually help us prioritize future development efforts and ensure that we are addressing the most pressing needs of the community. We want to make sure that Project Calico continues to be the best possible solution for networking and security in Kubernetes and container environments.
We know that your time is valuable, but we believe that your feedback is essential to our success. We hope that you will take a few moments to complete the survey and share your thoughts with us.
Thank you again for your continued support, and we look forward to hearing from you soon.
The post Project Calico wants to hear from you! The 2023 Calico Open Source Adoption Survey appeared first on Tigera.
Introducing Calico Runtime Threat Defense—The most extensive security coverage for containers and Kubernetes
Containerized applications are complex, which is why an effective container security strategy is difficult to design and execute. As digitalization continues to push applications and services to the cloud, bad actors’ attack techniques have also become more sophisticated, which further challenges container security solutions available on the market.
Despite the discussion around agent vs agentless in the cloud security landscape and which type of solution is better, the most valuable solution is one that provides a wide breadth of coverage. Calico is unique as it is already installed as part of the underlying platform and provides the dataplane for a Kubernetes cluster. When Calico Cloud or Calico Enterprise is deployed, security and observability capabilities can be enabled on top of these core components. We provide a simple plug-and-play active security solution that focuses on securing workloads and the Kubernetes platform with the least amount of complexity and configuration.
Runtime attack vectors
Cloud-native applications are susceptible to many attack vectors. We have broken them down to eight, as seen in the following illustration:
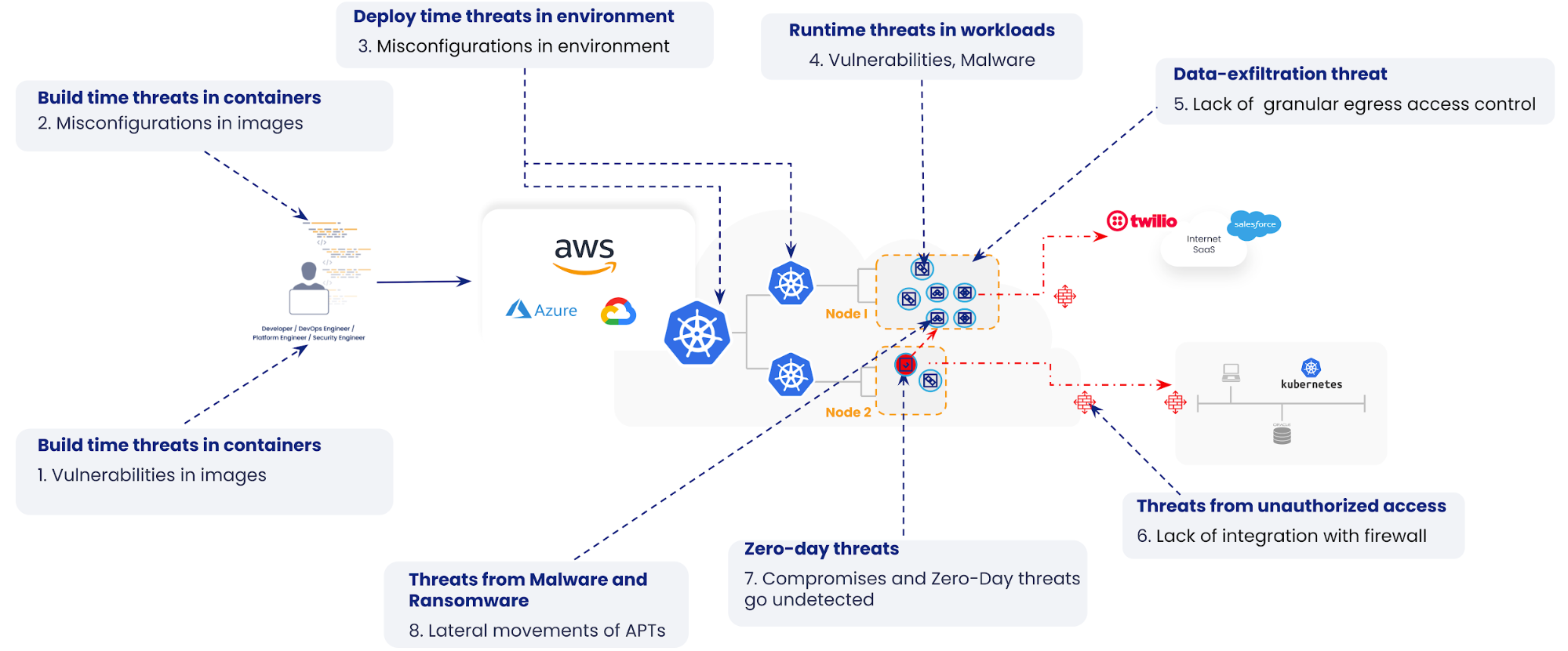
In previous blogs, we have explained how the use of vulnerability management, zero-trust workload security, and microsegmentation can help reduce the Continue reading
Introducing Calico Runtime Threat Defense—The most extensive security coverage for containers and Kubernetes
Containerized applications are complex, which is why an effective container security strategy is difficult to design and execute. As digitalization continues to push applications and services to the cloud, bad actors’ attack techniques have also become more sophisticated, which further challenges container security solutions available on the market.
Despite the discussion around agent vs agentless in the cloud security landscape and which type of solution is better, the most valuable solution is one that provides a wide breadth of coverage. Calico is unique as it is already installed as part of the underlying platform and provides the dataplane for a Kubernetes cluster. When Calico Cloud or Calico Enterprise is deployed, security and observability capabilities can be enabled on top of these core components. We provide a simple plug-and-play active security solution that focuses on securing workloads and the Kubernetes platform with the least amount of complexity and configuration.
Runtime attack vectors
Cloud-native applications are susceptible to many attack vectors. We have broken them down to eight, as seen in the following illustration:

In previous blogs, we have explained how the use of vulnerability management, zero-trust workload security, and microsegmentation can help reduce the Continue reading