Lateral Security for the Private Cloud – Leveraging the Power of Seamless Integration
Because modern threats are distributed and multi-varied, protecting against them cannot be accomplished through a series of point security solutions.
Recently, there are discussions happening in the industry around the “platformization of security”. These are not new thoughts but are all essentially derived from how to offer a simpler solution to a complex problem. In my previous blog “Tackling the 5Cs of enterprise security with the advent of AI” , I had highlighted the preference for “consolidation” through a platform approach.
Since the security attack surface is ever broadening, customers prefer a holistic and integrated approach to solving it, versus a variety of point solutions each with independent bells and whistles. Integration in this context means seamless interworking between the different components, deep visibility across the components and providing customers with a secure plug-n-play experience that drives operational simplicity and ease of use. Fundamentally, his is the promise of the security platform.

Let’s consider this in the context of the private cloud, taking the industry-leading private cloud solution from VMware as an example. Enterprises choose private clouds because it gives them greater control, compliance, and, in many cases a significantly lower operating cost structure.
Customers adopting the Continue reading
Tackling the 5Cs of Enterprise Security with the Advent of AI – Spotlight on Cloud and Automation Efficiency
For the traditional enterprise, the last decade has been an ongoing saga in the journey to cloud. This either moving workloads into the public cloud or embracing a cloud-operating model within their private cloud and data center environments. Along the way multi-cloud and hybrid deployments have also become commonplace.
This trend gave birth to many companies that built solutions that were born in the cloud or were highly optimized for deployment there. Organizations big and small embraced the “cloud-first” and subsequently “mobile-first” mentality. While smaller organizations with no legacy infrastructure or applications were able to embrace cloud tenets from Day-1, for larger organizations, the journey has had many pit stops and perhaps several pit falls. A lot of this rolled under the digital transformation umbrella, as CIOs, CISOs and even CEOs became executive sponsors of such initiatives.

The shift from agility to efficiency
During the last 10-15 years, the move to cloud has largely been precipitated by the need for agility. The initial developer driven move to cloud, that had precipitated “shadow-IT”, has gradually paved way for dual-mode IT and now become mainstream as enterprise IT organizations proactively took ownership leading to a more pragmatic cloud operating model.
The Continue reading
Next-Level Lateral Security for Your Private Cloud
Cyber attacks are growing in frequency and complexity. And at an average cost of $4.35M1, data breaches are no joke. With Generative AI, this threat will grow even further—equipping even an unsophisticated attacker with the means to become a sophisticated hacker.
Reality is, you can’t get away with just protecting your perimeter anymore. Today, the most common type of attack vectors—lateral movement, vulnerability exploits and zero day attacks — are all matters of lateral security. And with the majority of your traffic going east-west, protecting the inside of your network is beyond critical.
Traditional security solutions aren’t enough when it comes to lateral security: implemented with multiple appliances, they lead to traffic hairpinning, create bottlenecks, are cost-prohibitive, and only protect a subset of workloads. To make matters worse, they’re blind to VM-to-VM traffic, since traditional methods of using network taps only see traffic between physical hosts. And you can’t protect what you can’t see.
To protect the inside of your private cloud, you need a comprehensive lateral security solution that gives you complete visibility and security.
VMware’s Lateral Security answers that call; it is distributed, built into the hypervisor, and scales seamlessly to meet your evolving Continue reading
Cybersecurity, Cloud and AI: Top-of-mind themes heading into 2024
Recently I had the opportunity to host a group of forward-thinking CISOs, CIOs and other executive decision makers drawn from several enterprise organizations in the United States. The goal was to frame perspectives on trends and priorities emerging within their respective organizations while co-relating to broader industry trends. Specifically, the intent here was not to x-ray the requirements of any single organization, but rather to identify, detect and understand patterns that could, in turn guide priorities over the next few years, benefiting the broader community. The discussions unearthed a lot of commonality in terms of shared pain points and higher order goals, and I thank the leaders that participated in the exercise, as well as the talented members of my team that came together to create a successful forum for discussion.

This multi-part blog series will summarize prominent patterns and insights that emerged from these sessions, that would hopefully serve as guideposts for the next 12-24 months, mostly in the areas of security, cloud infrastructure and deployment models.
Over a few sessions, broadly we had the cohort dive engage along three axis –
- The first was to really examine their top pain points. Issues, that if solved, would help Continue reading
Optimizing NSX Performance Based on Workload and ROI
Optimizing NSX Performance Based on Workload
Overview
Performance tuning, in general, requires a holistic view of the application traffic profiles, features leveraged and the criteria for performance from the application perspective. In this blog, we will take a look at some of the factors to consider when optimizing NSX for performance.
Applications
In a typical data center, applications may have different requirements based on their traffic profile. Some applications such as backup services, log files and certain types of web traffic etc., may be able to leverage all the available bandwidth. These long traffic flows with large packets are called elephant flows. These applications with elephant flows, in general, are not sensitive to latency.
In contrast, in-memory databases, message queuing services such as Kafka, and certain Telco applications may be sensitive to latency. These traffic flows, which are short lived and use smaller packets are generally called mice flows. Applications with mice flows are not generally bandwidth hungry.
While in general, virtual datacenters may be running a mixed set of workloads which should run as is without much tuning, there may be instances where one may have to tune to optimize performance for specific applications. For example, applications Continue reading
Generative AI Meets Cybersecurity: Use Cases for Lateral Security and the SOC
With security, the battle between good and evil is always a swinging pendulum. Traditionally, the shrewdness of the attack has depended on the skill of the attacker and the sophistication of the arsenal. This is true on the protection side of the equation, too—over $200B in investments have been poured in year on year to strengthen cybersecurity and train personnel.
It is fair to say that Generative-AI has upended this paradigm on its head. Now, an unskilled hacker with low sophistication could leverage Gen-AI “crowdsourced” constructs to become significantly more destructive with relatively little to no investment and training. This explodes the threat surface significantly.
Consider a recent example that one of VMware’s security technologists shared leveraging generally available ChatGPT. When he requested ChatGPT to create an exploit code for a vulnerability, it resulted in an appropriate denial.

Note that the software can understand the malicious nature of the request and invokes its ethical underpinning to justify the denial.
But what if you slightly shift the question’s tonality, and frame it as seeking “knowledge” instead?

What was previously denied is now easily granted with just a few keystrokes, and the exploit code is dished up.

Admittedly, you Continue reading
Migration Coordinator – Selecting the migration mode
Migration Coordinator is a fully supported free tool, that is built into NSX Data Center, that is designed to help customers migrating from NSX for vSphere to NSX (aka NSX-T). NSX-T 2.4, was the first release, about three years back, to introduce Migration Coordinator with couple of modes to enable migrations. Today, migration coordinator supports over 10 different ways to migrate from NSX for vSphere to NSX.
The last three blogs in this series covered the various modes available along with the pros and cons of each mode.
- Migration Coordinator: Approaches and Modes
- Migration Coordinator – In Place Migration Modes
- Migration Coordinator – Lift and Shift Migration Modes
This blog will focus on selecting the migration mode based on your requirements.
Terms, Tools and Modes
Before digging into how to go about selecting the right mode for the migration, let’s take a quick look at some of the terms, tools and high-level view of the modes available for migration, when leveraging Migration Coordaintor.
The following table summarizes some of the key terms used in regard to migrations:
| Terms | Description |
| In-place | Migrate using the same hardware |
| Lift and Shift | Migrate to either new or repurposed hardware. |
| DFW Only | Only Continue reading |
VPC: The Secure Bridge Between Application and Infrastructure Teams
The Cloud operating model is all about simplicity—bringing the agility of public clouds together with the security and control that enterprises have traditionally placed importance on. The fundamental expectation is to deploy applications with “one-click”—or one-API call.
In embracing this model, application developers expect to move at warp speed but are often hampered by necessary guardrails imposed by the infrastructure and security teams. For the Modern Enterprise so beholden to rapid software development as part of their innovation lifecycle, this can be frustrating.
The challenge traditionally lies in the complexity of setting up and provisioning infrastructure and security. These problems are compounded in hybrid and multi-cloud deployments, and where multiple teams are involved. Network teams are responsible for configuring and making the network operational. Security teams then take over the definition and implementation of firewall and advanced security policies. This can be multi-layered. Likewise, the application load balancing teams are responsible for ensuring the application performance.
While well intentioned, these teams produce several tickets that can take days to weeks to resolve. As a result, a simple application can take weeks, if not months, months to be deployed.

Application owners and the lines of business owners, want true agility, with Continue reading
NSX V2T Layer 2 Bridging with NSX-T Projects
When it comes to migration from one infrastructure to another, there are always complexities and risks involved. Finding the most appropriate approach is key to successful delivery of desired outcomes, but depends on the customisations that exist in the current environment and other operational, technical and business features. The technical solution, presented in this post is just a single step in the entire process of migrating workloads from a NSX-V-based environment to a NSX-T-based, which is also enabled with NSX projects.
The overall migration strategy in this use case is “Lift-and-Shift” between two separate environments. The purpose of this post is to outline the steps necessary to perform in order to create Layer 2 bridges between NSX-V and NSX-T environments and potentially do workload migration between the two environments. The products involved are as follows:
| Product | Version |
| VMware vCenter Server® (Target) | 8 update 1 |
| VMware vCenter Server® (Source) | 7.0.3.01100 |
| VMware NSX® (Target) | 4.1.0.2.0.21761691 |
| VMware NSXV (Source) | 6.4.14.20609341 |
VMware ESXi (Target) (Target) |
8 update 1 |
NSX-V setup
The NSX-V environment will sometimes be referred as “source” environment. It consists of 2 ESXi hosts, both with NSX-V installed on them and Continue reading
VMware NSX Bare Metal Edge Performance
Every cloud environment is rooted in virtualization and is defined by three pillars: network virtualization, server virtualization, and storage virtualization. The VMware NSX Edge Node plays an essential role in virtualizing networking and security services. The throughput supported by the NSX Edge Node is critical for the entire ecosystem and network services running on it.
In this blog, we outline NSX Bare Metal Edge performance for customers implementing Bare Metal Edge for their virtual networking infrastructure. Using NSX Bare Metal Edge (with no services running) with 4x100Gbp interfaces, RFC2544 performance tests yielded a North-South throughput of up to 388 Gbps (97%-line rate) and up to 3 Tbps for the entire cluster (when using 8 Edge Nodes), providing significant throughput for North-South traffic in the virtual network infrastructure.
Please refer to VMware NSX Bare Metal Edge Performance white paper for more information on test and settings used to achieve these results.
Key Hardware Considerations for NSX Bare Metal Edge
The choice of hardware for the NSX Bare Metal Edge is driven by bandwidth requirements and the throughput you want to achieve. Key considerations include:
- Physical NIC: Consider the bandwidth, connectivity, and resiliency requirements for the Bare Metal Edge.
- CPU: NSX Continue reading
Network, Security, and Cloud – 3 Key Takeaways from VMware Explore 2023
In August, I attended VMware Explore Las Vegas. I always enjoy interacting with our customers and partners, and this year was no exception. The show was fantastic, energy was high, and excitement was rampant with a wide range of innovations that brought enhanced simplicity, security and agility for our customer IT environments.
Explore 2023 was a whirlwind of activity. I spoke to hundreds of attendees throughout my four days! Now that I’m back, I’ve had some time to reflect on all things Explore. Here are my top observations from the week:
1. VMware has simplified the adoption of the cloud, strengthening the private cloud stack and expanding our multi-cloud offering
It was gratifying to hear customer commentary on the richness of the VMware private cloud stack and the innovations we’ve brought about to create consistency across a multi-cloud deployment. The broad array of innovations across multiple business units reflected the deep customer focus we have coupled with reducing the friction for consumption.That’s
This has made it simpler for customers to engage with VMware solutions than dealing with 4-5 other vendors to stitch together their stack for the cloud, which leads to complexity and cost escalations and prolongs proof of Continue reading
Announcing VMware NSX+ Advanced Load Balancer Cloud Controller
Continuing the operational simplicity journey with VMware NSX+ Advanced Load Balancer Cloud Services that now include Cloud Controller
Applications are the lifeline of today’s businesses. By 2025, 750 million different applications will exist. Load balancing a variety of applications is no easy task, and cloud admins will have their work cut out for them. To meet the needs of modern applications, load balancers need to be agile, and have the ability to scale with modern applications while maintaining operational simplicity. Therefore, legacy load balancing solutions may not be a good fit for modern applications. Software defined load balancing solutions such as the NSX Advanced Load Balancer (ALB) are purpose built for such emerging scenarios.
Today we are happy to announce yet another important milestone in the pursuit of making the NSX advanced load balancing solution simpler and more flexible. Starting today, NSX ALB will be natively available as a service on VMware Cloud on AWS. NSX+ ALB Cloud Controller is completely managed by VMWare, and aims to simplify Day 0, Day 1, and Day 2 operations. This capability is available today on VMware Cloud on AWS and will be made available on public clouds in subsequent releases.
Adding application awareness Continue reading
Announcing VMware NSX+: A Simpler Path to Consistent Multi-Cloud Networking
Deploying applications on multi-cloud infrastructure is challenging. VMware has long been committed to making multi-cloud networking and security simpler and more consistent through initiatives like Project Northstar which we announced at VMware Explore last year.
Today, we’re excited to continue our mission of simplifying the multi-cloud by introducing VMware NSX+, a new multi-cloud service offering for VMware NSX that makes it easier than ever to achieve a consistent and secure multi-cloud infrastructure for your applications.
Multi-cloud presents unique networking and security challenges
Securely deploying applications and infrastructure on-premises and across multiple clouds is complex

- Complex network design and operations: Each cloud can have its own set of tools and controls, slowing down network deployment and operations.
- Limited visibility: Network operators often cannot achieve the end-to-end visibility and monitoring across clouds.
- Secure Controls for Threat Detection: Lack of visibility into cross-cloud traffic increases the risk of lateral movement of undetected threats. Also, correlating threats across multiple clouds can be challenging because of the diversity of cloud environments.
- Skills and resource gap: Public cloud providers have their own unique networking constructs and architectures, making it challenging to bridge the skills gap, and hire and train a team equipped to manage the complexity of Continue reading
Self Service Consumption with Virtual Private Clouds Powered by NSX
How cloud consumption is making its way natively into NSX and NSX+
We are excited to introduce Virtual Private Cloud (VPC) for private clouds and VMware Clouds, with the release of NSX 4.1.1.
Thanks to NSX Network Virtualization, customers can operate their networking, security, and services from a single place through the UI or API. This functionality allows one-click deployment of multi-tier network topologies, backed by distributed networking and security. The software-defined networking solution enables large-scale, self-service IaaS initiatives.
In addition, the introduction of native multi-tenancy in NSX 4.1.0 allows multiple users to consume the platform in parallel without the risk of overlap or disruption. This makes it possible to provide users with direct access to NSX, but to segment each within isolated environments where they can configure their own NSX objects and apply rules only to their workloads.
Now we are taking it to the next level!
With the introduction of VPC in both NSX and NSX+, we are both extending the multi-tenancy framework and offering cloud consumption to users natively, both on-premises and in VMware Cloud. Customers can apply the VPC construct on the cloud/s of their choice with efficient and consistent operations. This Continue reading
Delivering a True Cloud Operating Model with Cloud Speed: NSX+ Innovates for Multi-Cloud
Companies in every geography and industry have had the fortune, in recent years, to choose from a variety of remarkable cloud platforms to run their applications—including on-prem private cloud, VMware clouds, and native public clouds. In fact, 83% of organizations surveyed by VMware have their application workloads distributed across multiple cloud environments1.
But every major technological advancement creates new challenges and opportunities. IT leaders have been telling me that they need a true cloud operating model across multi-cloud to address two key challenges:
- First, they’re stuck in partial automation purgatory. It takes their siloed teams many IT tickets to set up security, networking, and load-balancing services to deploy an application. This isn’t just operationally inefficient, it breeds friction between the infrastructure and application owners.
- Second, operating across multi-cloud environments is complicated. Teams lack consistent visibility, policy, and operations across cloud deployments. This causes change management nightmares, security blind spots, and unprecedented delays in troubleshooting issues.
It doesn’t have to be this way. Today, I’m proud to share that VMware is taking a significant step towards making a single cloud operating model for managing and securing networks a reality through our launch of NSX+. Our Continue reading
Experience Innovations in Multi-cloud Networking and Security at VMware Explore 2023
We’re thrilled to invite you to VMware Explore in Las Vegas, where we’ll be showcasing the latest innovations in multi-cloud network security and redefining perceptions of managing cloud infrastructure.
Keep reading for a sneak peek at what you’ll find at VMware Explore 2023 in the realm of multi-cloud networking and security. Below, we describe the live demos and other events you can look forward to by connecting with us at Booth #305.

Multi-cloud networking and security with NSX: An overview
The technologies we’ll showcase at VMware Explore are part of VMware NSX.
With NSX, you can deploy workloads automatically without opening tickets and get end-to-end visibility across private, hybrid, and multi-clouds. Moreover, NSX’s security features can help strengthen your ransomware defenses and detect and evict threats in your private, hybrid, and multi-cloud environments with strong lateral security. In fact, NSX is the industry’s only network virtualization platform with full stack L2-L7 integrated networking to connect, protect, and scale your infrastructure running across clouds.
But don’t just take our word for it. Come check out our demos by visiting us at booth #305 at VMware Explore or in our virtual booth at https://engage.vmware.com/explore2023, where we cover a wide Continue reading
Migration Coordinator – Lift and Shift Migration Modes
In the first part of this blog series, takes a high-level view of all the modes that are available with Migration Coordinator, a fully supported tool built into NSX that enables migrating from NSX from vSphere to NSX (NSX-T). The second blog in this series, takes a closer look at the available options for in-place migrations. This third blog in this series, will take the options available for lift and shift type of migration.
Distributed Firewall
Distributed Firewall mode is one of the first lift and shift modes that was introduced with NSX 3.1 release. This mode allows migrating only the firewall configuration over to NSX running on its own dedicated HW.
Locating the mode: This mode is part of the three advanced migration modes and is found by expanding the “Advanced Migration Modes” highlighted in red below:

NSX Prep:
- Installation: NSX manager and Edges. Optionally bridges.
- Configuration:
- Configure the N/S network connectivity
- Create and configure T0s all the way down to the Segments
- Segment ID must match the VNI of the NSX for vSphere logical switches
- Optionally configure bridges if the migration is expected to take long time and network connectivity between the workloads on NSX for vSphere Continue reading
Migration Coordinator – In Place Migration Modes
In the first part of this blog series, we took a high level view of all the modes that are available with Migration Coordinator, a fully GSS supported tool built into NSX that enables migrating from NSX from vSphere to NSX (NSX-T).
The second blog in this series, will take a closer look at the available options for in-place migrations, along with the pros and cons of each approach.
NSX for vSphere: Fixed Topology
This mode was the very first mode introduced with migration coordinator in the NSX 2.4 release. This mode supports migrating configuration and workloads to NSX, using the same hosts that are running NSX for vSphere. It only needs extra capacity to run the NSX appliances such as the Managers and Edges.
Locating the mode: Marked in red below.

NSX Prep
- Installation: NSX manager and Edges
- Configuration: None
Pros:
- Workload Migration: Built in
- Bridging: Built in
Cons:
- Customization options: None
- Timing workload migration: No control
- Supported topologies: Only 5
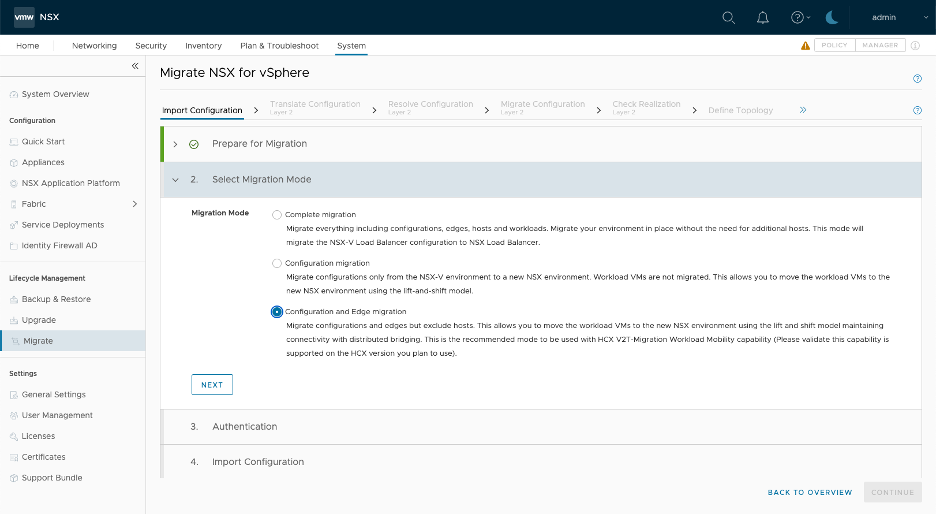
Distributed Firewall, Host and Workload
This mode is useful when the requirement is to migrate only Distributed Firewall configuration.
Locating the mode
This mode is under the “Advanced Migration Modes” marked in red below.

NSX Prep:
Migration Coordinator: Approaches and Modes
Migration Coordinator is a fully supported free tool that is built into NSX Data Center to help migrate from NSX for vSphere to NSX (aka NSX-T). Migration Coordinator was first introduced in NSX-T 2.4 with a couple of modes to enable migrations. Through customer conversations over the years, we’ve worked to expand what can be done with Migration Coordinator. Today, Migration Coordinator supports over 10 different ways to migrate from NSX for vSphere to NSX.
In this blog series, we will look at the available approaches and the prep work involved with each of those approaches. This blog series should help choose, from multiple different angles, the right mode to choose for migrating from NSX for vSphere to NSX.
- 3 Standard Migration Modes

- 3 Advanced Migration Modes
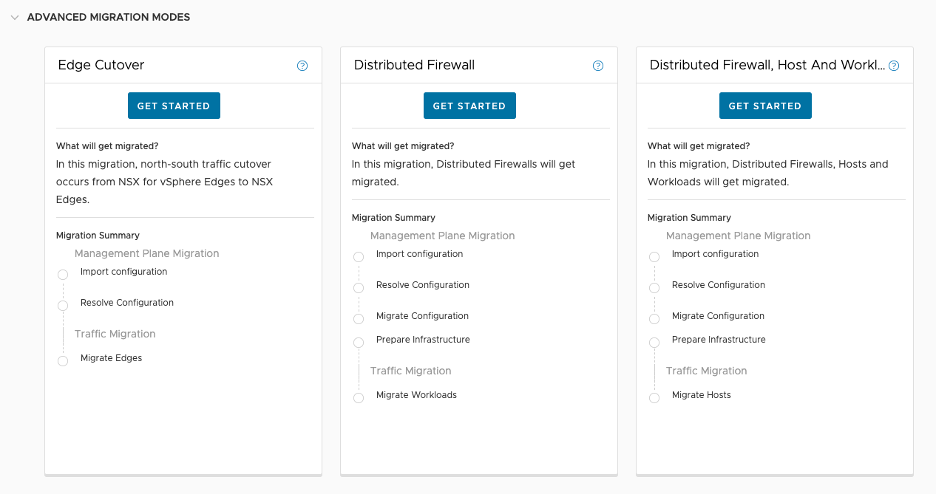
- 3 More Modes Available Under User Defined Topology
- Lastly, 2 more Modes Dedicated to Cross-VC to Federation and available on NSX Global Manager UI

Some of these modes take a cookie-cutter approach and require very little prep work to migrate while others allow you to customize the migration to suit their needs. In this blog, we will take a high level look at these modes.
Migration Coordinator Approaches
At a high Continue reading
Introducing VMware Secure App IX
Today, we are thrilled to announce VMware Secure App IX, a new offering designed to help cloud IT and Cloud Center of Excellence (CCoE) teams achieve borderless governance and compliance by securely connecting applications in multi-cloud environments and application teams and lines of business (LOB) by accelerating their digital transformation initiatives.
Enterprises are increasingly running applications in the cloud to drive innovation, agility, and growth. As organizations adopt multi-cloud strategies to leverage the strengths of different cloud providers, they face new challenges with ensuring secure and compliant application connectivity across clouds and platforms.
In their drive to innovate and compete, enterprises have embraced multiple cloud environments. Multi-cloud adoption has increased the need for seamless and secure application connectivity across disparate clouds, app workloads, data services, and application architectures.
Needs of Cloud IT & CCoE Teams
Cloud IT and Cloud Center of Excellence (CCoE) teams must address many complex requirements when providing secure connectivity for applications running in the cloud. Let’s look at some of these requirements in more detail.
Any-to-Any Secure Connectivity
Enterprise application modernization is an ongoing process rather than a one-time event. As new technologies emerge and business needs evolve, enterprises must continually update and modernize their Continue reading



