5 years with home NAS/RAID
I have lots of data-sets (packet-caps, internet-scans), so I need a large RAID system to hole it all. As I described in 2012, I bought a home "NAS" system. I thought I'd give the 5 year perspective.Reliability. I had two drives fail, which is about to be expected. Buying a new drive, swapping it in, and rebuilding the RAID went painless, though that's because I used RAID6 (two drive redundancy). RAID5 (one drive redundancy) is for chumps.
Speed. I've been unhappy with the speed, but there's not much I can do about it. Mechanical drives access times are slow, and I don't see any way of fixing that.
Cost. It's been $3000 over 5 years (including the two replacement drives). That comes out to $50/month. Amazon's "Glacier" service is $108/month. Since we all have the same hardware costs, it's unlikely that any online cloud storage can do better than doing it yourself.
Moore's Law. For the same price as I spent 5 years ago, I can now get three times the storage, including faster processors in the NAS box. From that perspective, I've only spent $33/month on storage, as the remaining third still has value.
Ease-of-use: The Continue reading
5 Reasons Why Attending the Transform Security Track at vForum Online is a Must
If you’ve been working in IT for the past few years, you know how much the security landscape has changed recently. Application infrastructures — once hosted in on-premises data centers — now sit in highly dynamic public and private multicloud environments. With the rise of mobile devices, bring-your-own-device (BYOD) policies, and Internet of Things (IoT), end-user environments are no longer primarily about corporately managed desktops. And attackers are growing more sophisticated by the day.
In such an atmosphere, traditional network perimeter security ceases to provide adequate protection.
That’s where the VMware solutions come in. At the heart of the solutions is a ubiquitous software layer across application infrastructure and endpoints that’s independent of the underlying physical infrastructure or location. To really understand how it works, you need to experience it for yourself. And the Transform Security track at vForum Online Fall 2017 on October 18th is the perfect opportunity. As our largest virtual conference, vForum Online gives IT professionals like yourself the chance to take a deep dive into VMware products with breakout sessions, chats with experts, and hands-on labs — all from the comfort of your own desk.
With this free half-day event just weeks away, it’s time to Continue reading
Geo Key Manager: How It Works
Today we announced Geo Key Manager, a feature that gives customers unprecedented control over where their private keys are stored when uploaded to Cloudflare. This feature builds on a previous Cloudflare innovation called Keyless SSL and a novel cryptographic access control mechanism based on both identity-based encryption and broadcast encryption. In this post we’ll explain the technical details of this feature, the first of its kind in the industry, and how Cloudflare leveraged its existing network and technologies to build it.
Keys in different area codes
Cloudflare launched Keyless SSL three years ago to wide acclaim. With Keyless SSL, customers are able to take advantage of the full benefits of Cloudflare’s network while keeping their HTTPS private keys inside their own infrastructure. Keyless SSL has been popular with customers in industries with regulations around the control of access to private keys, such as the financial industry. Keyless SSL adoption has been slower outside these regulated industries, partly because it requires customers to run custom software (the key server) inside their infrastructure.
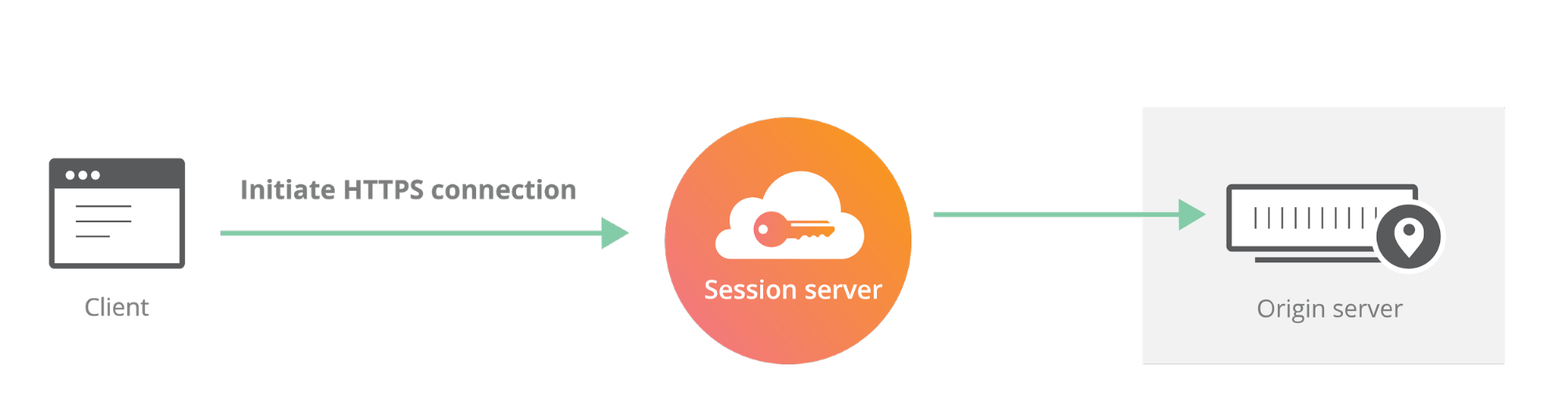
One of the motivating use cases for Keyless SSL was the expectation that customers may not trust a third party like Cloudflare with their Continue reading
Introducing the Cloudflare Geo Key Manager
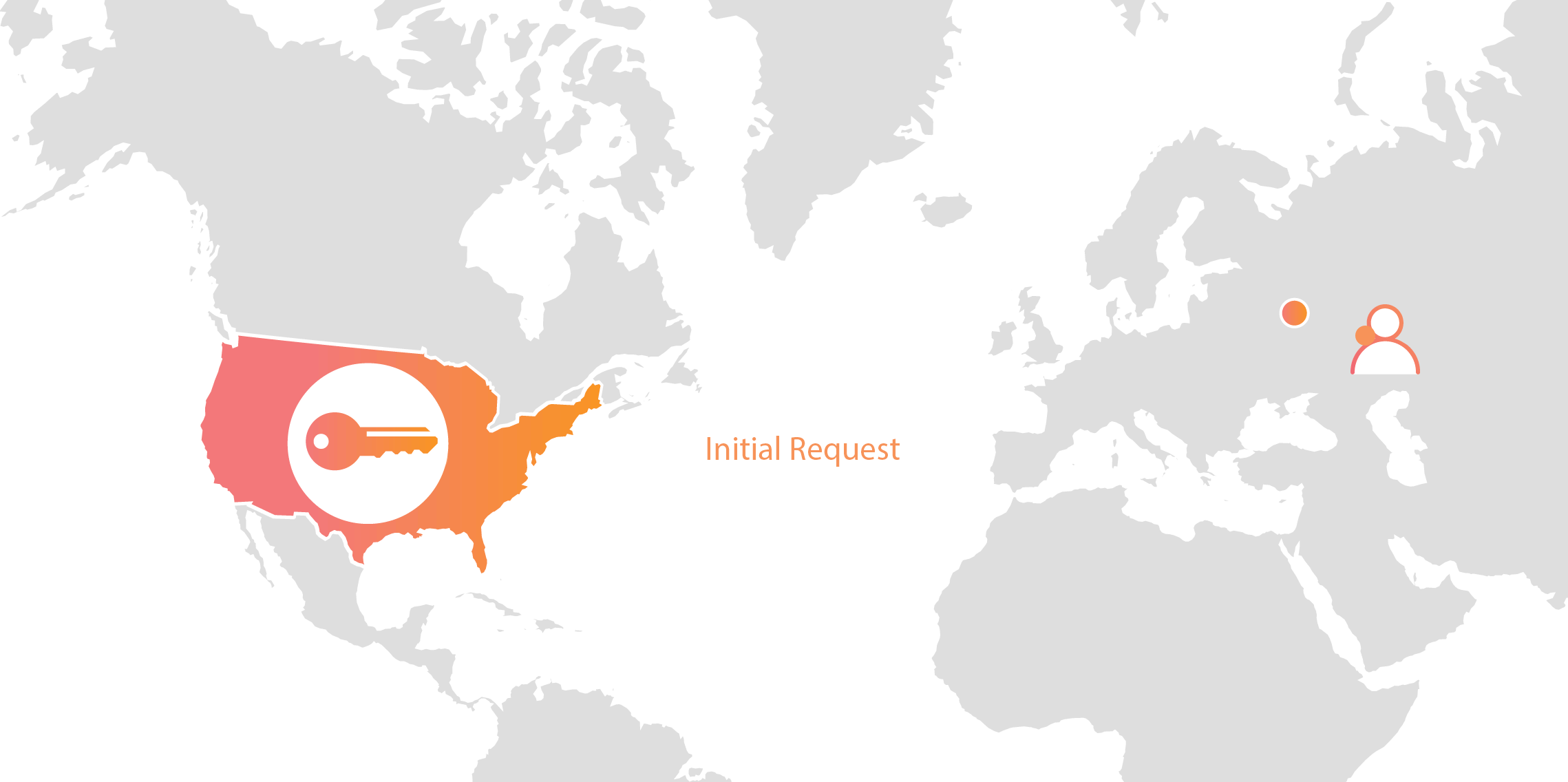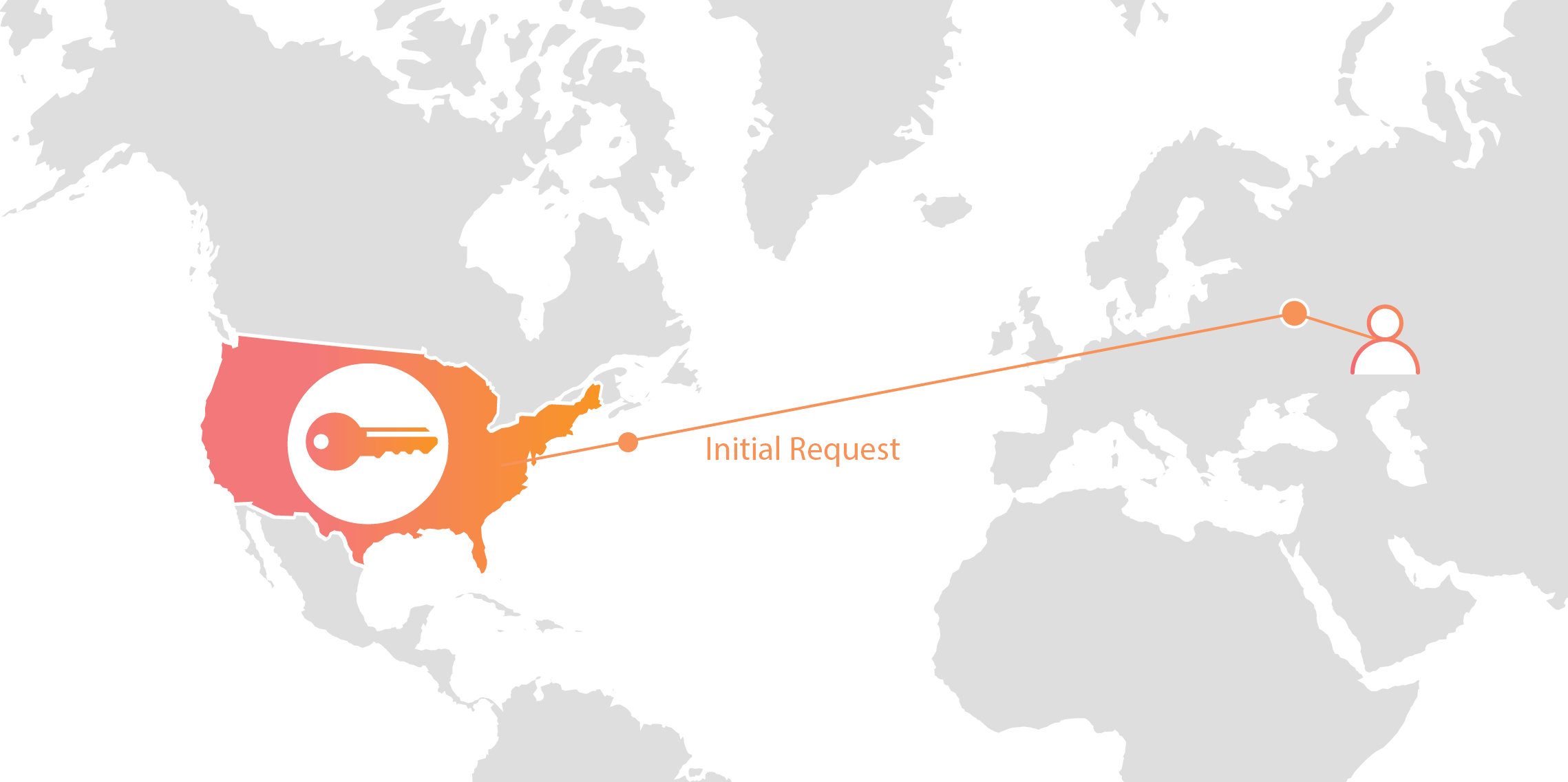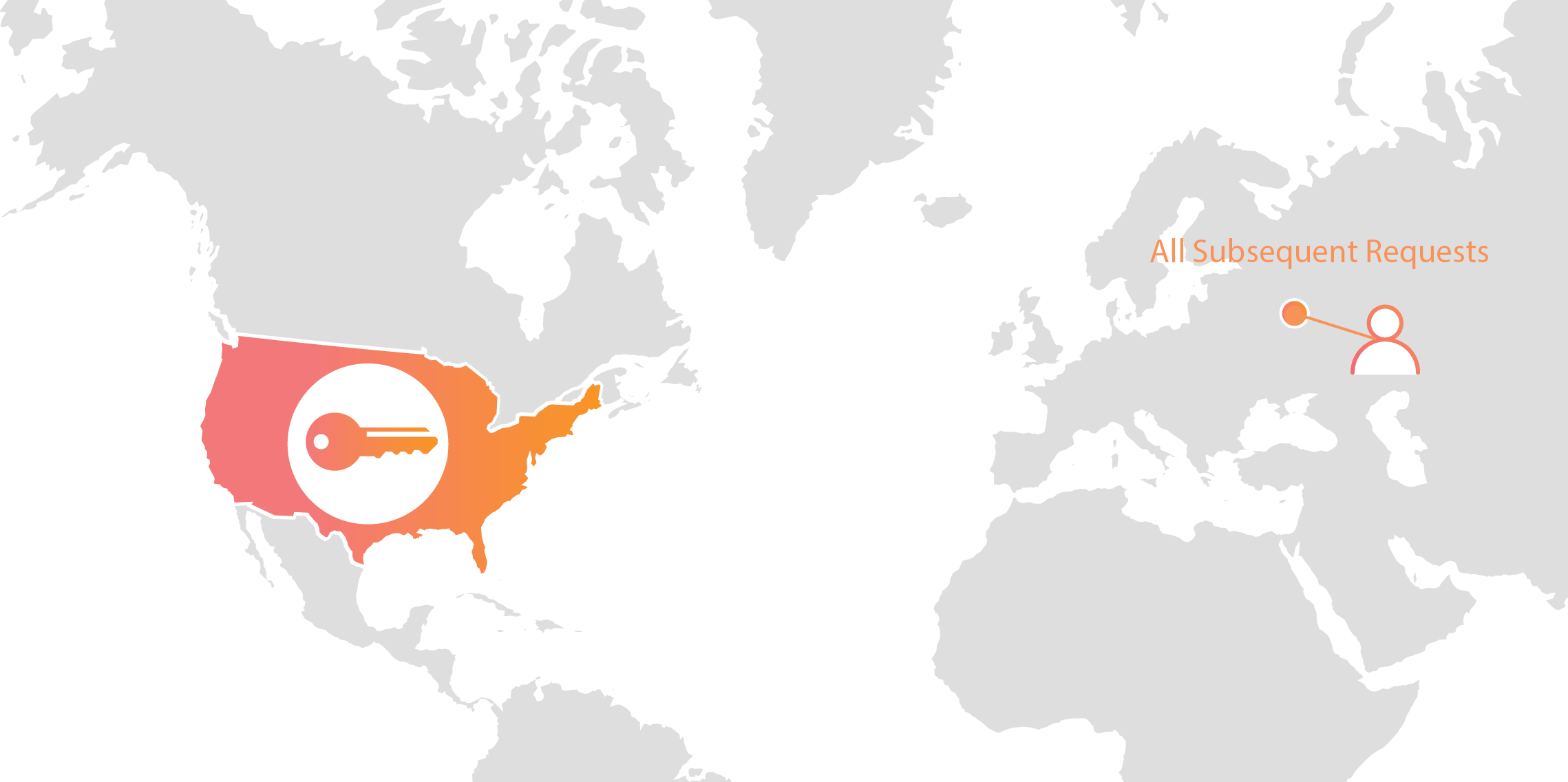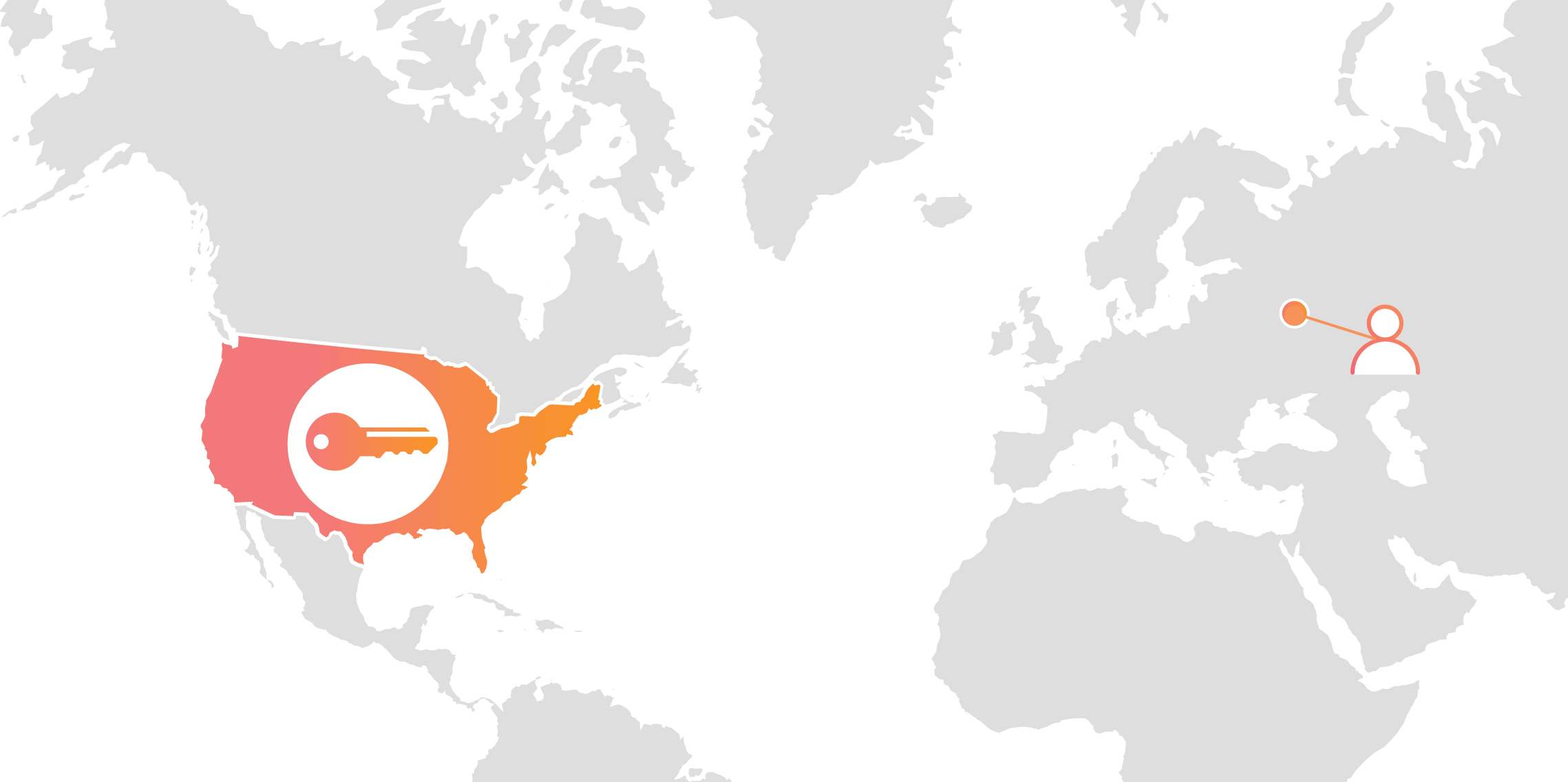
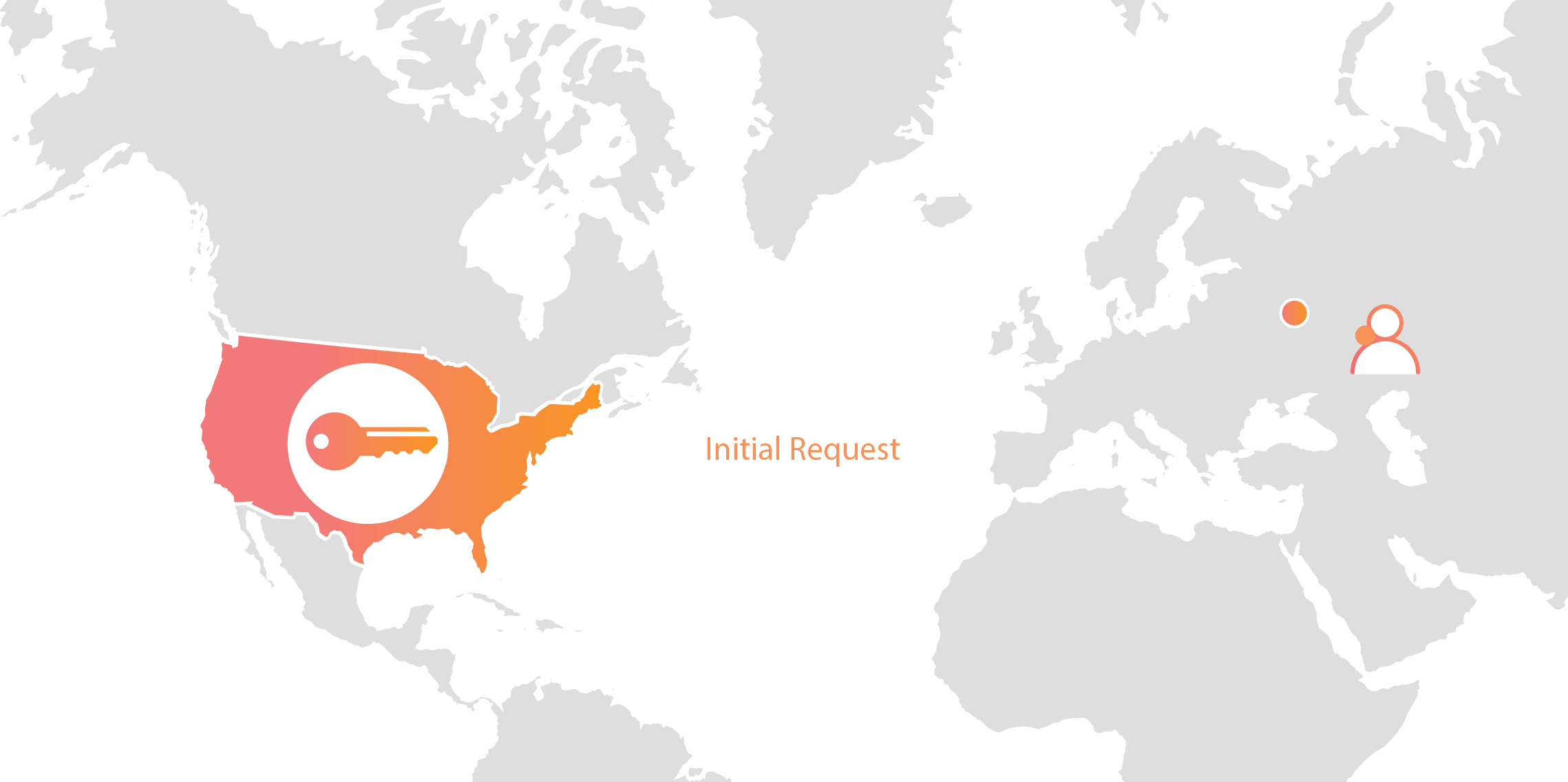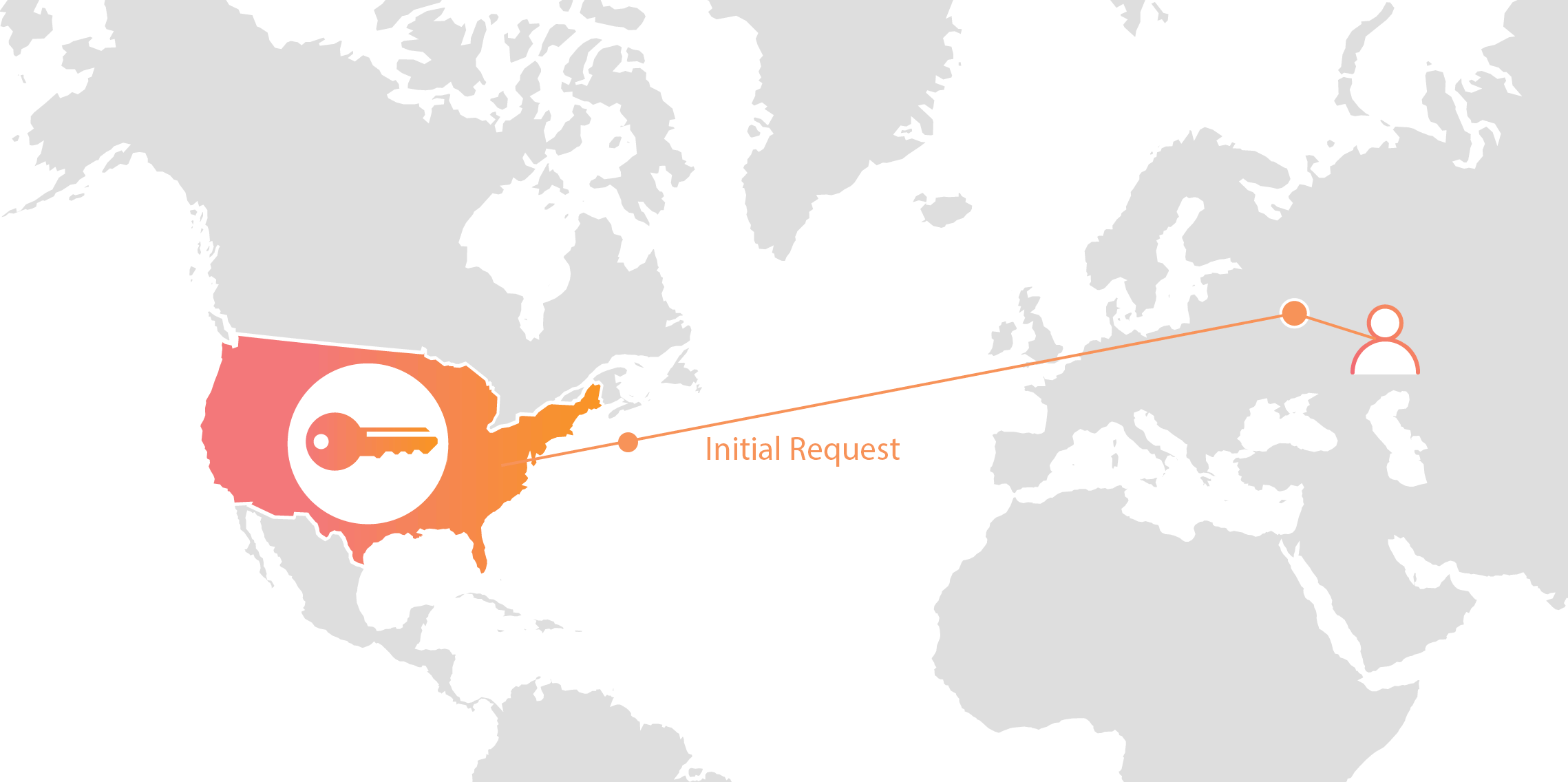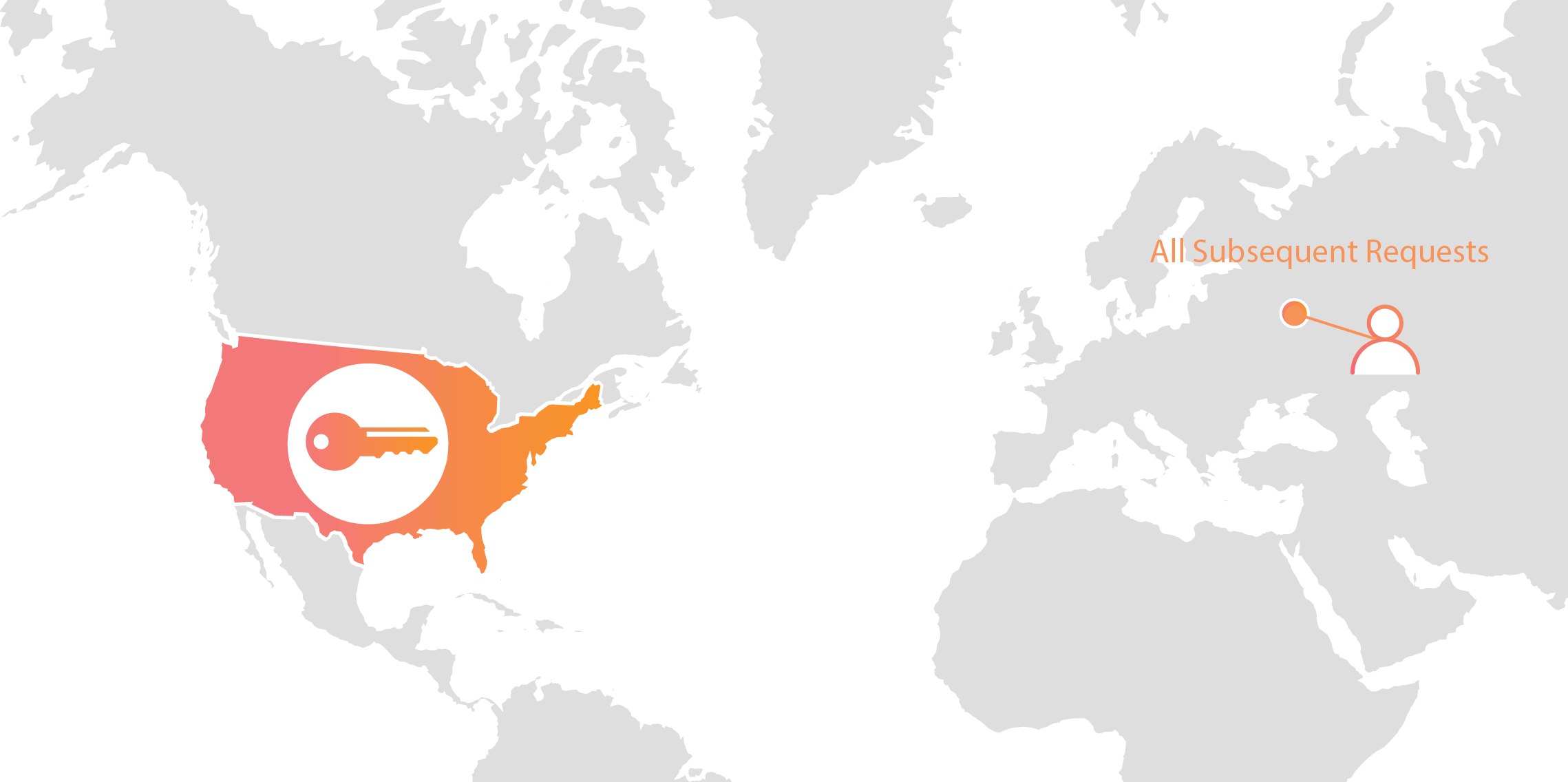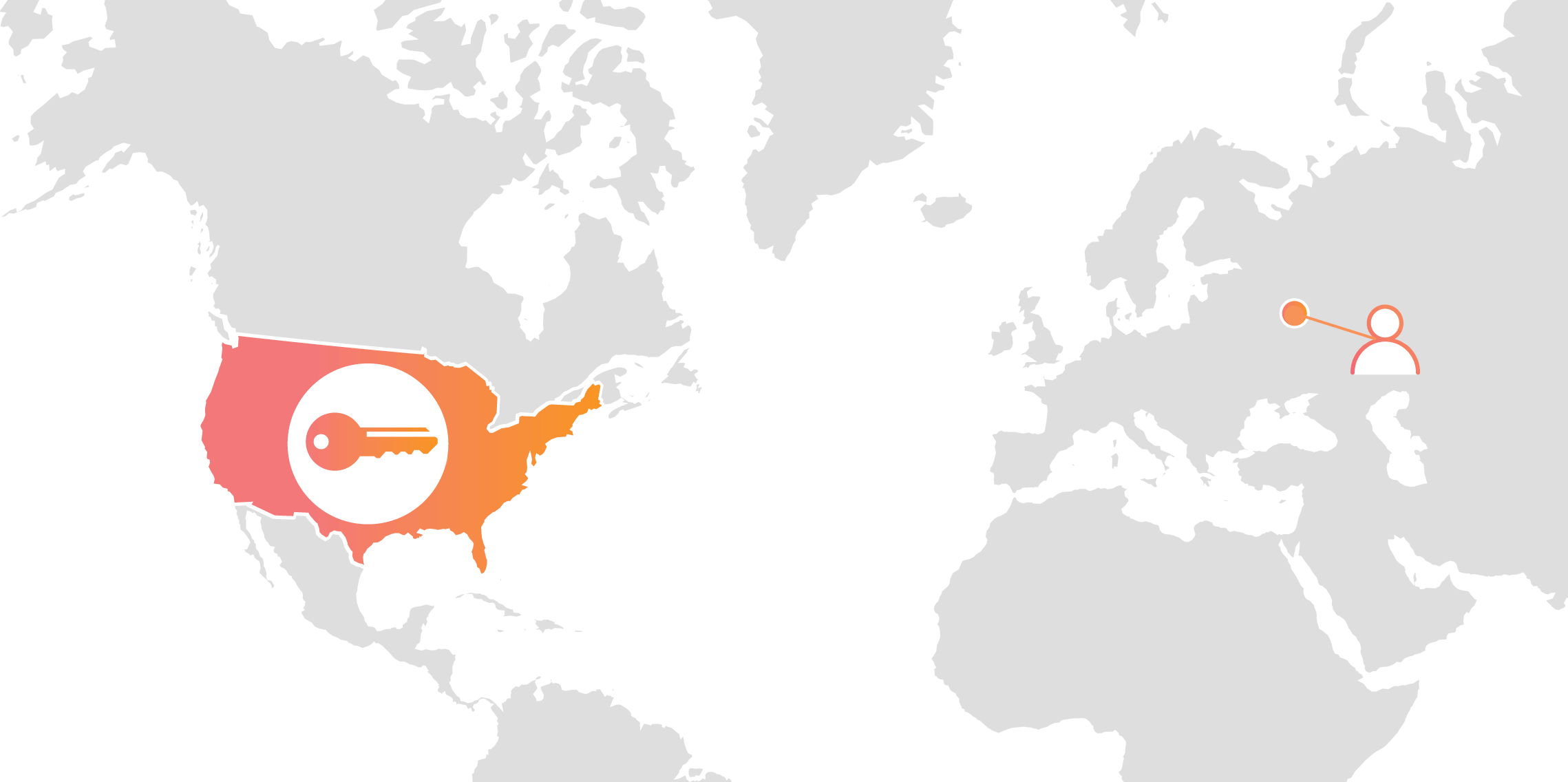
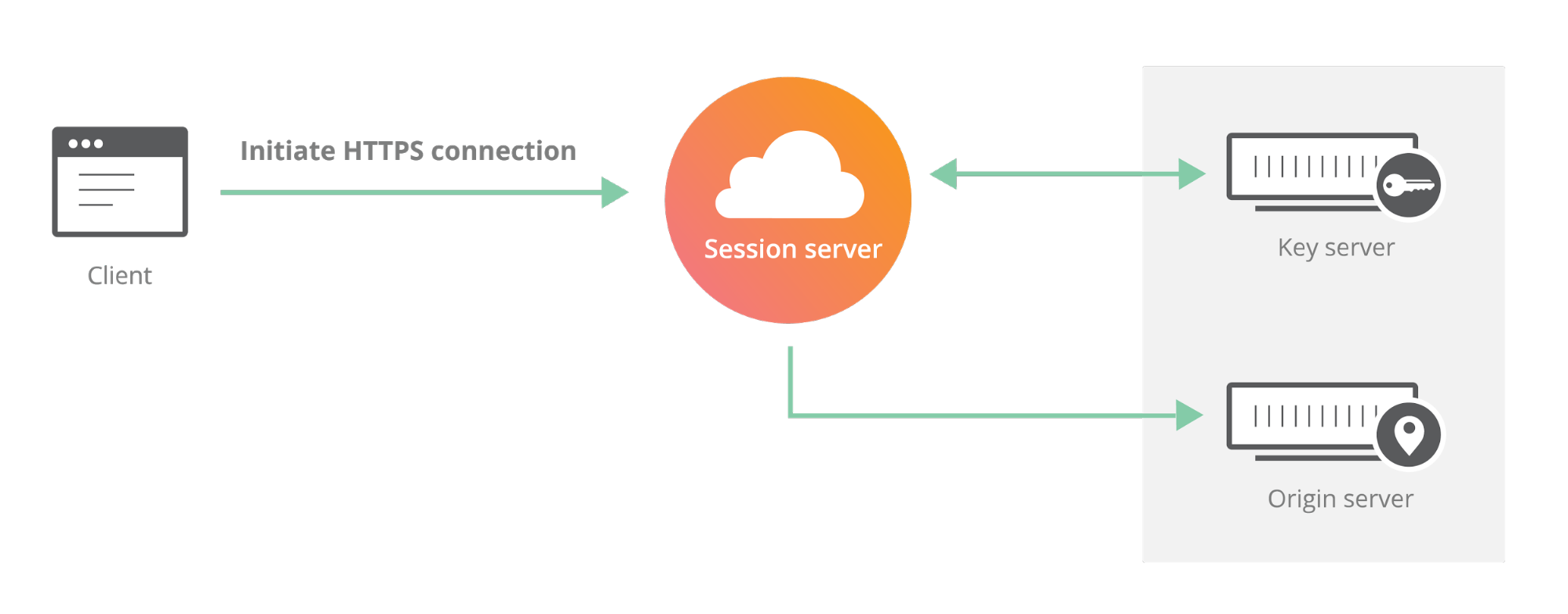
Cloudflare’s customers recognize that they need to protect the confidentiality and integrity of communications with their web visitors. The widely accepted solution to this problem is to use the SSL/TLS protocol to establish an encrypted HTTPS session, over which secure requests can then be sent. Eavesdropping is protected against as only those who have access to the “private key” can legitimately identify themselves to browsers and decrypt encrypted requests.
Today, more than half of all traffic on the web uses HTTPS—but this was not always the case. In the early days of SSL, the protocol was viewed as slow as each encrypted request required two round trips between the user’s browser and web server. Companies like Cloudflare solved this problem by putting web servers close to end users and utilizing session resumption to eliminate those round trips for all but the very first request.
Expanding footprint meets geopolitical concerns
As Internet adoption grew around the world, with companies increasingly serving global and more remote audiences, providers like Cloudflare had to continue expanding their physical footprint to keep up with demand. As of the date this blog post was published, Cloudflare has data centers in over 55 countries, and we continue Continue reading
A Day in the Life of a Docker Admin
About two months ago, we celebrated SysAdmin Day and kicked off our learning series for IT professionals. So far we’ve gone through the basics of containers and how containers are delivering value back to the company through cost savings. Now we begin the next stage of the journey by introducing how to deploy and operate containerized applications.
For the next few weeks, we are going to relate typical IT administrative tasks that many of you are familiar with to the tasks of a Docker admin. In the end, containerized applications are still applications and it is still primarily the responsibility of IT to secure and manage them. That is the same regardless of if the application runs in a container or not.
In this “A Day in the LIfe of a Docker Admin” series, we will discuss how common IT tasks translate to the world of Docker, such as:
- Managing .NET apps and migrating them off Windows Server 2008
- How networking with containers work and how to build an agile and secure network for containers
- How to achieve a secure and compliant application environment for any industry
- Integrating Docker with monitoring and logging tools
As a first step, let’s make Continue reading
Level 3 Tackles Optical Transport Data Encryption
 The platform supports encryption into Google Cloud and AWS but not into Microsoft Azure.
The platform supports encryption into Google Cloud and AWS but not into Microsoft Azure.
HPE Aruba 360 Secure Fabric Stretches Protection from Edge to Cloud
 The open architecture integrates with 120 other vendors' security products.
The open architecture integrates with 120 other vendors' security products.
Verizon Adds Software-Defined Perimeter Security from Vidder
 It isolates communications between cloud apps and devices.
It isolates communications between cloud apps and devices.
People can’t read (Equifax edition)
One of these days I'm going to write a guide for journalists reporting on the cyber. One of the items I'd stress is that they often fail to read the text of what is being said, but instead read some sort of subtext that wasn't explicitly said. This is valid sometimes -- as the subtext is what the writer intended all along, even if they didn't explicitly write it. Other times, though the imagined subtext is not what the writer intended at all.A good example is the recent Equifax breach. The original statement says:
Equifax Inc. (NYSE: EFX) today announced a cybersecurity incident potentially impacting approximately 143 million U.S. consumers.The word consumers was widely translated to customers, as in this Bloomberg story:
Equifax Inc. said its systems were struck by a cyberattack that may have affected about 143 million U.S. customers of the credit reporting agencyBut these aren't the same thing. Equifax is a credit rating agency, keeping data on people who are not its own customers. It's an important difference.
Another good example is yesterday's quote "confirming" that Equifax is confirming the "Apache Struts" vulnerability was to blame:
Equifax has been intensely Continue reading
Telefónica, Palo Alto Networks Launch Cloud-Based Security Software
 The two companies also collaborate on the Cyber Threat Alliance.
The two companies also collaborate on the Cyber Threat Alliance.
Microsoft Azure Cloud Security Encrypts In-Use Data
 Microsoft is using its Coco Framework technology to encrypt data in use for Azure SQL Database.
Microsoft is using its Coco Framework technology to encrypt data in use for Azure SQL Database.
New BlueBorne Vulnerability to Bluetooth Devices – What happened and what to do about it
Billions of Bluetooth-enabled devices may be exposed to a new remote attack called “BlueBorne”, even without user interaction or pairing. Affected systems include Windows, iOS (older than iOS 10), the Linux kernel, and Android. What should you do about it?
Bluetooth is ubiquitous, commonly connecting accessories like headsets and keyboards, but is also used throughout the brave new Internet of Things (IoT) world. An attacker exploiting these BlueBorne vulnerabilities can mount a man-in-the-middle attack, or even take control of a device without the user even noticing it.
The vulnerabilities were discovered by a security company called Armis earlier this year. Researchers reached out to the companies responsible for vulnerable implementations that lead to the coordinated disclosure (and patches) on September 12. (You can read more about our views on responsible disclosure and collaborative security in Olaf Kolkman’s blog post here.)
This case once again highlights how crucial it is that software update mechanisms are available to fix vulnerabilities, update configuration settings, and add new functionality to devices. There are challenges, both technological and economic, in having update capabilities ubiquitously deployed, as discussed in the recently published Report from the Internet of Things Software Update (IoTSU) Workshop 2016.
Vulnerabilities Continue reading
2017 SDx Infrastructure Security Report Available Now
 Download now to learn the latest on the SDx infrastructure security market.
Download now to learn the latest on the SDx infrastructure security market.
Making the World Better by Breaking Things
Ben Sadeghipour, Technical Account Manager, HackerOne, and Katie Moussouris, Founder & CEO, Luta Security
Moderator: John Graham-Cumming, CTO, Cloudflare
 Photo by Cloudflare Staff
Photo by Cloudflare Staff
JGC: We’re going to talk about hacking
Katie Moussouris helps people how to work around security vulnerabilities.
Ben Sadeghipour is a technical account manager at HackerOne, and a hacker at night
JGC: Ben, you say you’re a hacker by night. Tell us about this.
BS: It depends who you ask: if they encourage it; or, we do it for a good reason. “Ethical hacker” - we do it for a good reason. Hacking can be illegal if you’re hacking without permission; but that’s not what we do.
JGC: You stay up all night
BS: I lock myself in the basement
JGC: Tell us about your company.
KM: I was invited to brief Pentagon when I worked at Microsoft; The pentagon was interested in the implementation of this idea in a large corporation like Microsoft.
“Hacking the pentagon”
The adoption of Bug Bounty has been slow. We were interested in working with a very large company like Microsoft. There was interest in implementing ideas from private sector at Pentagon. I helped the internal team at Continue reading
Cisco’s David Goeckeler Talks Network Security at Deutsche Bank
 Encrypted traffic analytics finds malware in encrypted traffic.
Encrypted traffic analytics finds malware in encrypted traffic.
Extreme Networks Launches Automated Campus with Avaya Assets
 The system will support customizable signature sets for more than 7,000 applications.
The system will support customizable signature sets for more than 7,000 applications.
The View from Washington: The State of Cybersecurity
Avril Haines, Former Deputy National Security Advisor, Obama Administration
Moderator: Doug Kramer, General Counsel, Cloudflare
 Photo by Cloudflare Staff
Photo by Cloudflare Staff
Avril began her career on the National Security Council, and went on to become the first female deputy at the CIA.
DK: How will cyber will play a role in military operations?
AH: We look at it from the perspective of “asymmetric threats”; state actors (those who have high-value assets that they can hold at risk with no threat to them). The US is more technologically advanced and relies on cyber more and more; we are as a consequence more vulnerable to cyber threats. Asymmetric threats thus hold at risk those things that are most important to us.
In the cyber realm we can’t quite define what constitutes a use of force, and saying so can be used against us. So this is an area that is crucial to continue working in; in many respects the US has the most to lose from using a framework that doesn’t work.
“The private sector is utterly critical in creating a framework that is going to work.”
We want to have widely-accepted norms and rules so that we can ask other countries Continue reading
Veriflow Brings Intent-Based Networking Verification to the Cloud
 The updated platform can infer business goals with no input from the user.
The updated platform can infer business goals with no input from the user.
Domo BYOK Generates New Data Encryption Keys Every Hour
 The SaaS includes a built-in kill switch.
The SaaS includes a built-in kill switch.
IBM LinuxONE Gains Proprietary Container Focus
 IBM views commodity solutions as put together with "tape and bailing wire."
IBM views commodity solutions as put together with "tape and bailing wire."