On Their Way Out: Proprietary Security Appliances in Branch Offices
 The attack landscape has broadened.
The attack landscape has broadened.
Cloud Native Security Paradigm Shift
 Exciting time is ahead for the cloud security industry.
Exciting time is ahead for the cloud security industry.
Technology Short Take #68
Welcome to Technology Short Take #68, my erratically-published collection of links, articles, and posts from around the web—all focused on today’s major data center technologies. I’ve been trying to stick to a schedule that has these posts published on a Friday, but given the pending holiday weekend I wanted to get this out a bit early. As always, I hope that something I’ve included here proves useful to you.
Networking
- Brent Salisbury retweeted a ton of MACVLAN- and IPVLAN-related posts right after I published the last Technology Short Take, so they had to get bumped to this one. First, we have this post on HiCube, which covers MACVLAN vs. IPVLAN. Next, we have a pair of articles by Sreenivas Makam; the first covers MACVLAN and IPVLAN basics, while the second tackles the Docker MACVLAN and IPVLAN network plugins. Both articles are useful, IMHO, especially considering that MACVLAN is no longer experimental as of the Docker 1.12 release.
- I recently came across this mention of in-band network telemetry (INT), which looks really powerful. I think this will be something worth watching.
- Oh, and while we’re discussing P4: Diego Dompe has an article talking about OpenSwitch and P4 that Continue reading
Split Tunnel Insecurities
I really dislike corporate VPNs that don’t allow split tunneling—disconnecting from the VPN to print on a local printer, or access a local network attached drive, puts a real crimp in productivity. In the case of services reachable over both IPv6 and IPv4, particularly if the IPv6 path is preferred, split tunneling can be quite dangerous, as explained in RFC7359. Let’s use the network below to illustrate.

In this network, host A is communicating with server B through a VPN, terminated by the VPN concentrator marked as “VPN.” Assume the host is reachable on both 192.0.2.1 and 2001:fb8:0:1::1. The host, the upstream router, the network in the cloud, and the server are all IPv6 reachable. When the host first connects, it will attempt both the IPv6 and IPv4 connections, and choose to use the IPv6 connection (this is what most current operating systems will do).
The problem is: the VPN connection doesn’t support IPv6 at all—it only supports IPv4. Because IPv6 is preferred, the traffic between the host and the server will take the local IPv6 connection, which is not encrypted—the blue dash/dot line—rather than the encrypted IPv4 tunnel—the red dashed line. The user, host, and Continue reading
Cisco Pays $293M for CloudLock, a Cloud Security Firm
 CloudLock uses an API-based technology.
CloudLock uses an API-based technology.
Nuage Networks Security Report Webinar Q&A: SDN & Security Policy Automation
 Check out the post-event Q&A from Nuage on SDN, Security & Policy!
Check out the post-event Q&A from Nuage on SDN, Security & Policy!
Accessing ASA CLI in Firepower Threat Defence
I’ve recently loaded Firepower Threat Defense on an ASA5525 for my home Internet firewall. For those unfamiliar with FTD, it is basically a combination of critical ASA features and all of the Cisco Firepower features in a single image and execution space. So unlike Firepower Services, which runs separately inside the same ASA sheet metal, FTD takes over the hardware. Once the image installed onto the hardware, the firewall is attached to and managed by a Firepower Management Console.
For those that still want to (or need to) get under the covers to understand the underpinnings or do some troubleshooting of the ASA features, it is still possible to access the familiar CLI. The process first requires an ssh connection to the management IP of the FTD instance, then access expert mode and enter the lina_cli command.
MacBook:~ paulste$ ssh [email protected] Password: Last login: Thu Jun 23 18:16:43 2016 from 192.168.1.48 Copyright 2004-2016, Cisco and/or its affiliates. All rights reserved. Cisco is a registered trademark of Cisco Systems, Inc. All other trademarks are property of their respective owners. Cisco Fire Linux OS v6.0.1 (build 37) Cisco ASA5525-X Threat Defense v6.0.1 Continue reading
Use the freakin’ debugger
This post is by a guy who does "not use a debugger". That's stupid. Using a friendly source-level debugger (Visual Studio, XCode, Eclipse) to step line-by-line through working code is what separates the 10x programmers from the wannabes. Yes, it's a bit of a learning hurdle, and creating "project" files for small projects is a bit of a burden, but do it. It'll vastly improve your coding skill.That post quotes people like Rob Pike saying that stepping line-by-line is a crutch, that instead you should be able to reason about code. And that's true, if you understand what you are doing completely.
But in the real world, you never do. Programmers are constantly forced to stretch and use unfamiliar languages. Worse yet, they are forced to use unfamiliar libraries. Documentation sucks, there's no possible way to understand APIs than to step through code -- either watching the returned values, or compiling their source and stepping into it.
As an experienced programmer, it's true I often don't step through every line. The lines I understand completely, the ones I can fully reason about, I don't bother. But the programmer spends only a small percentage of their time on things Continue reading
On differential privacy
Over the past several weeks, there’s been a lot of talk about something called “differential privacy.” What does this mean, how does it work, and… Is it really going to be effective? The basic concept is this: the reason people can identify you, personally, from data collected off your phone, searches, web browser configuration, computer configuration, etc., is you do things just different enough from other people to create a pattern through cyber space (or rather data exhaust). Someone looking hard enough can figure out who “you” are by figuring out patterns you don’t even think about—you always install the same sorts of software/plugins, you always take the same path to work, you always make the same typing mistake, etc.
The idea behind differential security, considered here by Bruce Schneier, here, and here, is that you can inject noise into the data collection process that doesn’t impact the quality of the data for the intended use, while it does prevent any particular individual from being identified. If this nut can be cracked, it would be a major boon for online privacy—and this is a nut that deserves some serious cracking.
But I doubt it can actually be cracked Continue reading
Reverse Turing testing tech support
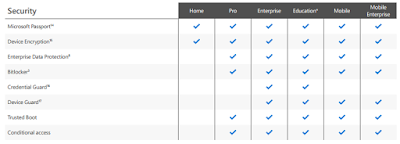
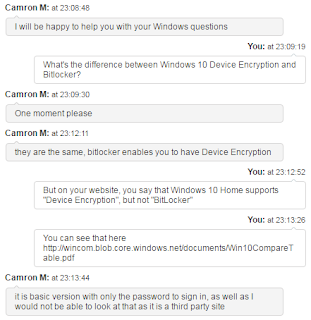
So I have to get a new Windows license for a new PC. Should I get Windows 10 Home or Windows 10 Professional? What's the difference?128 Technology Raises $36M to Simplify Virtual Routers
 Session-aware and deterministic routers are the key.
Session-aware and deterministic routers are the key.
DockerCon 2016 Vendor Meetings
While at DockerCon 2016 in Seattle today, I took some time on the expo floor to talk to a number of different vendors, mostly focused on networking solutions. Here are some notes from these discussions. I may follow up with additional posts on some of these technologies; it will largely depend on time and the ease by which the technologies/products may be consumed.
Plumgrid
My first stop was the Plumgrid booth. I’d heard of Plumgrid, but wanted to take this time to better understand their architecture. As it turns out, their architecture is quite interesting. Plumgrid is one of the primary commercial sponsors behind the IO Visor project, a Linux Foundation project, which leverages the extended Berkeley Packet Filter (eBPF) subsystem in the Linux kernel. Using eBPF, Plumgrid has created in-kernel virtual network functions (VNFs) that do things like bridging, routing, network address translation (NAT), and firewalling. Combined with a scale-out central control plane and leveraging the Linux kernel’s built-in support for VXLAN, this enables Plumgrid to create overlay networks and apply very granular security policies to attached workloads (which could be VMs or containers).
Project Calico
Next, I stopped by the Calico booth. Unlike many of the networking Continue reading
A Look at Key SDN Deployments
 While the SDN market isn’t taking off as much as everybody would like, it’s being implemented in many customer deployments for key data center use cases.
While the SDN market isn’t taking off as much as everybody would like, it’s being implemented in many customer deployments for key data center use cases.
Tesla review: What you need to know about charging
Before you buy an electric car, you need to understand charging. It’s a huge deal. You think it works almost like filling the gas tank. It doesn’t. Before going on long trips, you first need to do math and a bit of planning.The Math
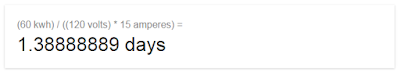
Like BMW model numbers indicate engine size, Tesla model numbers indicate the size of the battery, so my "Tesla S P90D" has a 90kwh (killowatt-hour) battery, with a 286mile range. Their lowest end model is the “Tesla S 60”, which has a 60kwh hour battery, or a 208mile advertised range.In the United States, a typical plug is a 120volt circuit with a maximum of 15amps. Doing the math, this is how long it’ll take for me to recharge the battery:
That’s right, 1.4 days (or 2.1 days for a 90kwh car). This is the absolute worse case scenario, mind you, but it demonstrates that you have to pay attention to charging. You can't simply drive up to a station, fill up the tank in a couple minutes, and drive away.
Let’s say you live in Austin, Texas, and you have a meeting in Dallas. You think that you can drive up to Continue reading
Ethereum/TheDAO hack simplified
The news in the Bitcoin world is the Ethereum/DAO hack. I thought I'd write up a simplified explanation.What is Bitcoin?
move these coins I received there, to this guy here
Big Chain Deep Dive on Software Gone Wild
A while ago Big Switch Networks engineers realized there’s a cool use case for their tap aggregation application (Big Tap Monitoring Fabric) – an intelligent patch panel traffic steering solution used as security tool chaining infrastructure in DMZ… and thus the Big Chain was born.
Curious how their solution works? Listen to Episode 58 of Software Gone Wild with Andy Shaw and Sandip Shah.
DNS Cookies and DDoS Attacks
DDoS attacks, particularly for ransom—essentially, “give me some bitcoin, or we’ll attack your server(s) and bring you down,” seem to be on the rise. While ransom attacks rarely actually materialize, the threat of DDoS overall is very large, and very large scale. Financial institutions, content providers, and others regularly consume tens of gigabits of attack traffic in the normal course of operation. What can be done about stopping, or at least slowing down, these attacks?
To answer, this question, we need to start with some better idea of some of the common mechanisms used to build a DDoS attack. It’s often not effective to simply take over a bunch of computers and send traffic from them at full speed; the users, and the user’s providers, will often notice machine sending large amounts of traffic in this way. Instead, what the attacker needs is some sort of public server that can (and will) act as an amplifier. Sending this intermediate server should cause the server to send an order of a magnitude more traffic towards the attack target. Ideally, the server, or set of servers, will have almost unlimited bandwidth, and bandwidth utilization characteristics that will make the attack appear Continue reading
Virtualized Networks Invite Cyber Espionage
 The cybersecurity and security solutions landscape is in constant flux.
The cybersecurity and security solutions landscape is in constant flux.
The Cost Of “Sales” Isn’t Free
Why should you care how much a company spends on sales? Because the actual cost of selling products is paid for by the customer in the price of the product.
The post The Cost Of “Sales” Isn’t Free appeared first on Packet Pushers.
Scanning for ClamAV 0day
Last week an 0day was released for ClamAV. Well, not really an 0day so much as somebody noticed idiotic features in ClamAV. So I scanned the Internet for the problem.The feature is that the daemon listens for commands that tell it to do things like scan files. Normally, it listens only locally for such commands, but can be reconfigured to listen remotely on TCP port 3310. Some packages that include ClamAV sometimes default to this.
It's a simple protocol that consists of sending a command in clear text, like "PING", "VERSION", "SHUTDOWN", or "SCAN
So I ran masscan with the following command:
masscan 0.0.0.0/0 -p3310 --banners --hello-string[3310] VkVSU0lPTg==Normally when you scan and address range (/0) and port (3310), you'd just see which ports are open/closed. That's not useful in this case, because it finds 2.7 million machines. Instead, you want to establish a full TCP connection. That's what the --banners option does, giving us only 38 thousand machines that successfully establish a connection. The remaining machines are large ranges on the Internet where firewalls are configured to respond with SYN-ACK, with the express purpose of frustrating port scanners.
But of those 38k machines, most are actually Continue reading