Another SD-WAN Security SNAFU: SQL Injections in Cisco SD-WAN Admin Interface
Christoph Jaggi sent me a link to an interesting article describing security vulnerabilities pentesters found in Cisco SD-WAN admin/management code.
I’m positive the bugs have been fixed in the meantime, but what riled me most was the root cause: Little Bobby Tables (aka SQL injection) dropped by. Come on, it’s 2021, SD-WAN is supposed to be about building secure replacements for MPLS/VPN networks, and they couldn’t get someone who could write SQL-injection-safe code (the top web application security risk)?
How to Simplify Your Journey to Zero Trust with NSX Workshops
At its core, Zero Trust is an operational framework that helps enterprises secure modern network environments. Zero Trust insists organizations strip away ambiguity from their security and focus on the basics: committing to a risk-based approach across end-users, networks, data, devices, and much more. If you’re ready to take the next step toward built-in, Zero Trust networking (ZTN), we can help. Learn how to successfully implement Zero Trust networking and segmentation strategies at one of our upcoming NSX Network Security Workshop Sessions on Tuesday, September 28, 2021 or on Wednesday, September 29, 2021.
During these live virtual events, Patricio Villar, Principal Network Architect and VMware Certified Expert/Network Virtualization, will cover Zero Trust foundational concepts, including:
- How to identify communication paths to segment and build policy to protect your data center
- How implementing NSX security supports ZTN framework
- How to easily implement stronger distributed security with VMware NSX
NSX Network Security Workshop topics include:
- Zero Trust Networking concepts
- Tools to implement ZTN
- Distributed Firewall
- Distributed IDS/IPS
- NSX Intelligence
- Live demos
- And much more
If you’re ready to simplify Zero Trust so you can have simply zero worries, grab your spot and register today.
See you there!
The post How to Simplify Your Journey to Zero Trust with NSX Workshops appeared first on Network and Security Virtualization.
How not to get caught in law-enforcement geofence requests
I thought I'd write up a response to this question from well-known 4th Amendment and CFAA lawyer Orin Kerr:
Question for tech people related to "geofence" warrants served on Google: How easy is it for a cell phone user, either of an Android or an iPhone, to stop Google from generating the detailed location info needed to be responsive to a geofence warrant? What do you need to do?
— Orin Kerr (@OrinKerr) September 15, 2021
(FWIW, I'm seeking info from people who actually know the answer based on their expertise, not from those who are just guessing, or are who are now googling around to figure out what the answer may be,)
— Orin Kerr (@OrinKerr) September 15, 2021
First, let me address the second part of his tweet, whether I'm technically qualified to answer this. I'm not sure, I have only 80% confidence that I am. Hence, I'm writing this answer as blogpost hoping people will correct me if I'm wrong.
There is a simple answer and it's this: just disable "Location" tracking in the settings on the phone. Both iPhone and Android have a one-click button to tap that disables everything.
The trick is knowing which thing Continue readingHow Cloudflare helped mitigate the Atlassian Confluence OGNL vulnerability before the PoC was released
On August 25, 2021, Atlassian released a security advisory for their Confluence Server and Data Center. The advisory highlighted an Object-Graph Navigation Language (OGNL) injection that would result in an unauthenticated attacker being able to execute arbitrary code.
A full proof of concept (PoC) of the attack was made available by a security researcher on August 31, 2021. Cloudflare immediately reviewed the PoC and prepared a mitigation rule via an emergency release. The rule, once tested, was deployed on September 1, 2021, at 15:32 UTC with a default action of BLOCK and the following IDs:
100400(for our legacy WAF)e8c550810618437c953cf3a969e0b97a(for our new WAF)
All customers using the Cloudflare WAF to protect their self-hosted Confluence applications have automatically been protected since the new rule was deployed last week. Additionally, the Cloudflare WAF started blocking a high number of potentially malicious requests to Confluence applications even before the rule was deployed.
And customers who had deployed Cloudflare Access in front of their Confluence applications were already protected even before the emergency release. Access checks every request made to a protected hostname for a JSON Web Token (JWT) containing a user’s identity. Any unauthenticated users attempting this exploit Continue reading
Getting Blasted by Backdoors

I wanted to take minute to talk about a story I’ve been following that’s had some new developments this week. You may have seen an article talking about a backdoor in Juniper equipment that caused some issues. The issue at hand is complicated at the linked article does a good job of explaining some of the nuance. Here’s the short version:
- The NSA develops a version of Dual EC random number generation that includes a pretty substantial flaw.
- That flaw? If you know the pseudorandom value used to start the process you can figure out the values, which means you can decrypt any traffic that uses the algorithm.
- NIST proposes the use of Dual EC and makes it a requirement for vendors to be included on future work. Don’t support this one? You don’t get to even be considered.
- Vendors adopt the standard per the requirement but don’t make it the default for some pretty obvious reasons.
- Netscreen, a part of Juniper, does use Dual EC as part of their default setup.
- The Chinese APT 5 hacking group figures out the vulnerability and breaks into Juniper to add code to Netscreen’s OS.
- They Continue reading
Marketing Wins
Off-topic post for today …
In the battle between marketing and security, marketing always wins. This topic came to mind after reading an article on using email aliases to control your email—
One of the most basic things you can do to increase your security against phishing attacks is to have two email addresses, one you give to financial institutions and another one you give to “everyone else.” It would be nice to have a third for newsletters and marketing, but this won’t work in the real world. Why?
Because it’s very rare to find a company that will keep two email addresses on file for you, one for “business” and another for “marketing.” To give specific examples—my mortgage company sends me both marketing messages in the form of a “newsletter” as well as information about mortgage activity. They only keep one email address on file, Continue reading
Making Magic Transit health checks faster and more responsive


Magic Transit advertises our customer’s IP prefixes directly from our edge network, applying DDoS mitigation and firewall policies to all traffic destined for the customer’s network. After the traffic is scrubbed, we deliver clean traffic to the customer over GRE tunnels (over the public Internet or Cloudflare Network Interconnect). But sometimes, we experience inclement weather on the Internet: network paths between Cloudflare and the customer can become unreliable or go down. Customers often configure multiple tunnels through different network paths and rely on Cloudflare to pick the best tunnel to use if, for example, some router on the Internet is having a stormy day and starts dropping traffic.
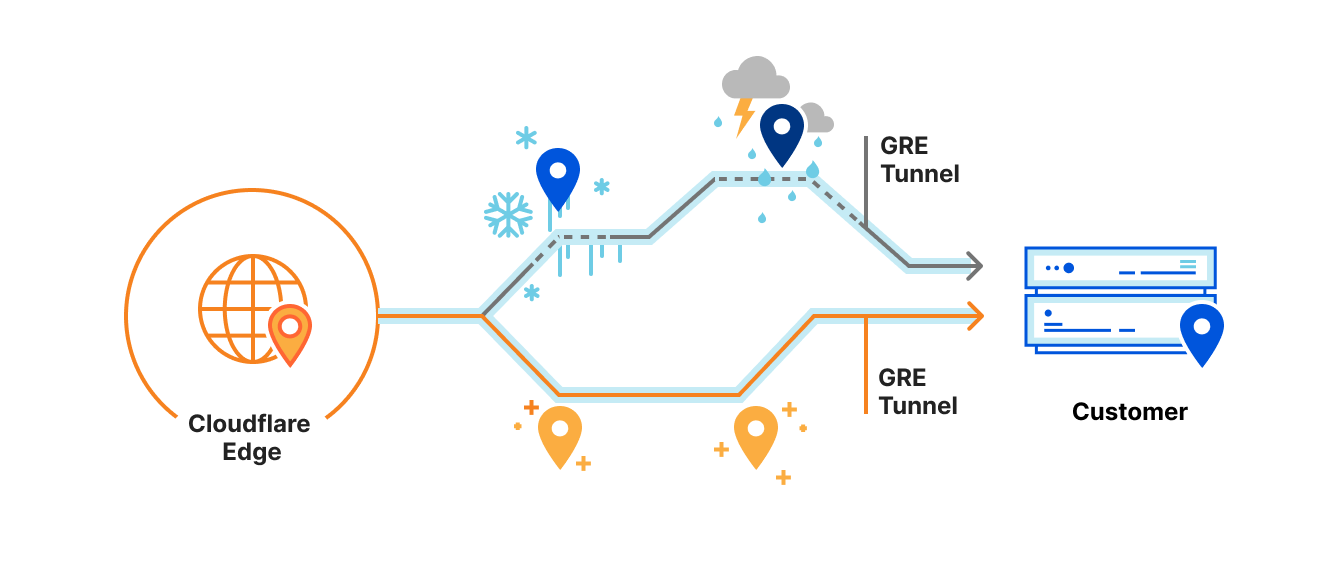
Because we use Anycast GRE, every server across Cloudflare’s 200+ locations globally can send GRE traffic to customers. Every server needs to know the status of every tunnel, and every location has completely different network routes to customers. Where to start?
In this post, I’ll break down my work to improve the Magic Transit GRE tunnel health check system, creating a more stable experience for customers and dramatically reducing CPU and memory usage at Cloudflare’s edge.
Everybody has their own weather station
To decide where to send traffic, Cloudflare edge servers Continue reading
MUST Read: Operational Security Considerations for IPv6 Networks (RFC 9099)
After almost a decade of bickering and haggling (trust me, I got my scars to prove how the consensus building works), the authors of Operational Security Considerations for IPv6 Networks (many of them dear old friends I haven’t seen for way too long) finally managed to turn a brilliant document into an Informational RFC.
Regardless of whether you already implemented IPv6 in your network or believe it will never be production-ready (alongside other crazy stuff like vaccines) I’d consider this RFC a mandatory reading.
MUST Read: Operational Security Considerations for IPv6 Networks (RFC 9099)
After almost a decade of bickering and haggling (trust me, I got my scars to prove how the consensus building works), the authors of Operational Security Considerations for IPv6 Networks (many of them dear old friends I haven’t seen for way too long) finally managed to turn a brilliant document into an Informational RFC.
Regardless of whether you already implemented IPv6 in your network or believe it will never be production-ready (alongside other crazy stuff like vaccines) I’d consider this RFC a mandatory reading.
More devices, fewer CAPTCHAs, happier users


Earlier this year we announced that we are committed to making online human verification easier for more users, all around the globe. We want to end the endless loops of selecting buses, traffic lights, and convoluted word diagrams. Not just because humanity wastes 500 years per day on solving other people's machine learning problems, but because we are dedicated to making an Internet that is fast, transparent, and private for everyone. CAPTCHAs are not very human-friendly, being hard to solve for even the most dedicated Internet users. They are extremely difficult to solve for people who don’t speak certain languages, and people who are on mobile devices (which is most users!).
Today, we are taking another step in helping to reduce the Internet’s reliance on CAPTCHAs to prove that you are not a robot. We are expanding the reach of our Cryptographic Attestation of Personhood experiment by adding support for a much wider range of devices. This includes biometric authenticators — like Apple's Face ID, Microsoft Hello, and Android Biometric Authentication. This will let you solve challenges in under five seconds with just a touch of your finger or a view of your face -- without sending this private Continue reading
Helping Keep Governments Safe and Secure

Today, we are excited to share that Cloudflare and Accenture Federal Services (AFS) have been selected by the Department of Homeland Security (DHS) to develop a joint solution to help the federal government defend itself against cyberattacks. The solution consists of Cloudflare’s protective DNS resolver which will filter DNS queries from offices and locations of the federal government and stream events directly to Accenture’s analysis platform.
Located within DHS, the Cybersecurity and Infrastructure Security Agency (CISA) operates as “the nation’s risk advisor.”1 CISA works with partners across the public and private sector to improve the security and reliability of critical infrastructure; a mission that spans across the federal government, State, Local, Tribal, and Territorial partnerships and the private sector to provide solutions to emerging and ever-changing threats.
Over the last few years, CISA has repeatedly flagged the cyber risk posed by malicious hostnames, phishing emails with malicious links, and untrustworthy upstream Domain Name System (DNS) resolvers.2 Attackers can compromise devices or accounts, and ultimately data, by tricking a user or system into sending a DNS query for a specific hostname. Once that query is resolved, those devices establish connections that can lead to malware downloads, phishing websites, Continue reading
Of course you can’t trust scientists on politics
Many people make the same claim as this tweet. It's obviously wrong. Yes,, the right-wing has a problem with science, but this isn't it.If you think you don't trust scientists, you're mistaken. You trust scientists in a million different ways every time you step on a plane, or for that matter turn on your tap or open a can of beans. The fact that you're unaware of this doesn't mean it's not so.
— Paul Graham (@paulg) July 26, 2021
First of all, people trust airplanes because of their long track record of safety, not because of any claims made by scientists. Secondly, people distrust "scientists" when politics is involved because of course scientists are human and can get corrupted by their political (or religious) beliefs.
And thirdly, the concept of "trusting scientific authority" is wrong, since the bedrock principle of science is distrusting authority. What defines sciences is how often prevailing scientific beliefs are challenged.
Carl Sagan has many quotes along these lines that eloquently expresses this:
A central lesson of science is that to understand complex issues (or even simple ones), we must try to free our minds of dogma and to guarantee the freedom to publish, Continue reading
Cloudflare’s Handling of an RCE Vulnerability in cdnjs


cdnjs provides JavaScript, CSS, images, and fonts assets for websites to reference with more than 4,000 libraries available. By utilizing cdnjs, websites can load faster with less strain on one’s own origin server as files are served directly from Cloudflare’s edge. Recently, a blog post detailed a vulnerability in the way cdnjs’ backend automatically keeps the libraries up to date.
This vulnerability allowed the researcher to execute arbitrary code, granting the ability to modify assets. This blog post details how Cloudflare responded to this report, including the steps we took to block exploitation, investigate potential abuse, and remediate the vulnerability.
This vulnerability is not related to Cloudflare CDN. The cdnjs project is a platform that leverages Cloudflare’s services, but the vulnerability described below relates to cdnjs’ platform only. To be clear, no existing libraries were modified using this exploit. The researcher published a new package which demonstrated the vulnerability and our investigation concluded that the integrity of all assets hosted on cdnjs remained intact.
Disclosure Timeline
As outlined in RyotaK’s blog post, the incident began on 2021-04-06. At around 1100 GMT, RyotaK published a package to npm exploiting the vulnerability. At 1129 GMT, cdnjs processed this package, resulting in Continue reading
Pegasus Pisses Me Off

In this week’s episode of the Gestalt IT Rundown, I jumped on my soapbox a bit regarding the latest Pegasus exploit. If you’re not familiar with Pegasus you should catch up with the latest news.
Pegasus is a toolkit designed by NSO Group from Israel. It’s designed for counterterrorism investigations. It’s essentially a piece of malware that can be dropped on a mobile phone through a series of unpatched exploits that allows you to create records of text messages, photos, and phone calls and send them to a location for analysis. On the surface it sounds like a tool that could be used to covertly gather intelligence on someone of interest and ensure that they’re known to law enforcement agencies so they can be stopped in the event of some kind of criminal activity.
Letting the Horses Out
If that’s where Pegasus stopped, I’d probably not care one way or the other. A tool used by law enforcement to figure out how to stop things that are tough to defend against. But because you’re reading this post you know that’s not where it stopped. Pegasus wasn’t merely a tool developed by intelligence agencies for targeted use. If I had to Continue reading
Risk analysis for DEF CON 2021
It's the second year of the pandemic and the DEF CON hacker conference wasn't canceled. However, the Delta variant is spreading. I thought I'd do a little bit of risk analysis. TL;DR: I'm not canceling my ticket, but changing my plans what I do in Vegas during the convention.
First, a note about risk analysis. For many people, "risk" means something to avoid. They work in a binary world, labeling things as either "risky" (to be avoided) or "not risky". But real risk analysis is about shades of gray, trying to quantify things.
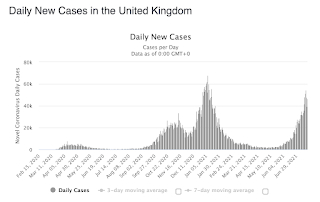
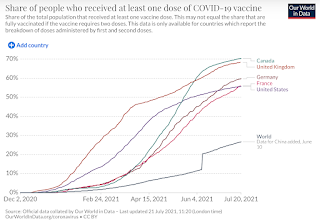
The Delta variant is a mutation out of India that, at the moment, is particularly affecting the UK. Cases are nearly up to their pre-vaccination peaks in that country.
Note that the UK has already vaccinated nearly 70% of their population -- more than the United States. In both the UK and US there are few preventive measures in place (no lockdowns, no masks) other than vaccines.
Thus, the UK graph is somewhat predictive of what will happen in the United States. If we time things from when the latest wave hit the same levels as peak of the first wave, then it looks like the Continue reading
DDoS attack trends for 2021 Q2


Recent weeks have witnessed massive ransomware and ransom DDoS (Distributed Denial of Service) attack campaigns that interrupted aspects of critical infrastructure around the world, including one of the largest petroleum pipeline system operators, and one of the world’s biggest meat processing companies. Earlier this quarter, more than 200 organizations across Belgium, including the government and parliament websites and other services, were also DDoS’d.
And when most of the United States were celebrating Independence Day on July 4, hundreds of US companies were hit by a ransomware attack demanding 70 million USD in Bitcoin. Attackers known to be affiliated with REvil, a Russian ransomware group, exploited multiple previously unknown vulnerabilities in IT management software. The targets included schools, small public-sector bodies, travel and leisure organizations, and credit unions, to name a few. While the threat of ransomware and ransom DDoS is not new (read our posts on ransomware and ransom DDoS from 2021 Q1), the latest attacks on Internet properties ranging from wineries, professional sports teams, ferry services and hospitals has brought them from just being background noise to front page headlines affecting our day-to-day lives. In fact, recent attacks have propelled ransomware and DDoS to the top of US Continue reading
Microsoft Misplaced Security Priorites
 Pays bug bounty pittance, spends big on speculative product
Pays bug bounty pittance, spends big on speculative product