Video: Outages Caused by Bugs in BGP Implementations
The previous BGP-related videos described how fat fingers and malicious actors cause Internet outages.
Today, we’ll focus on the impact of bugs in BGP implementations, from malformed AS paths to mishandled transitive attributes. The examples in the video are a few years old, but you can see similar things in the wild in 2023.
The GDPR’s new ally
SPONSORED FEATURE: A convergence of cutting-edge technology, generative AI and advanced server infrastructure has unleashed a wave of innovation in the realm of cyber security. …
The post The GDPR’s new ally first appeared on The Next Platform.
The GDPR’s new ally was written by Martin Courtney at The Next Platform.
Open BGP Daemons: There’s So Many of Them
A while ago, the Networking Notes blog published a link to my “Will Network Devices Reject BGP Sessions from Unknown Sources?” blog post with a hint: use Shodan to find how many BGP routers accept a TCP session from anyone on the Internet.
The results are appalling: you can open a TCP session on port 179 with over 3 million IP addresses.
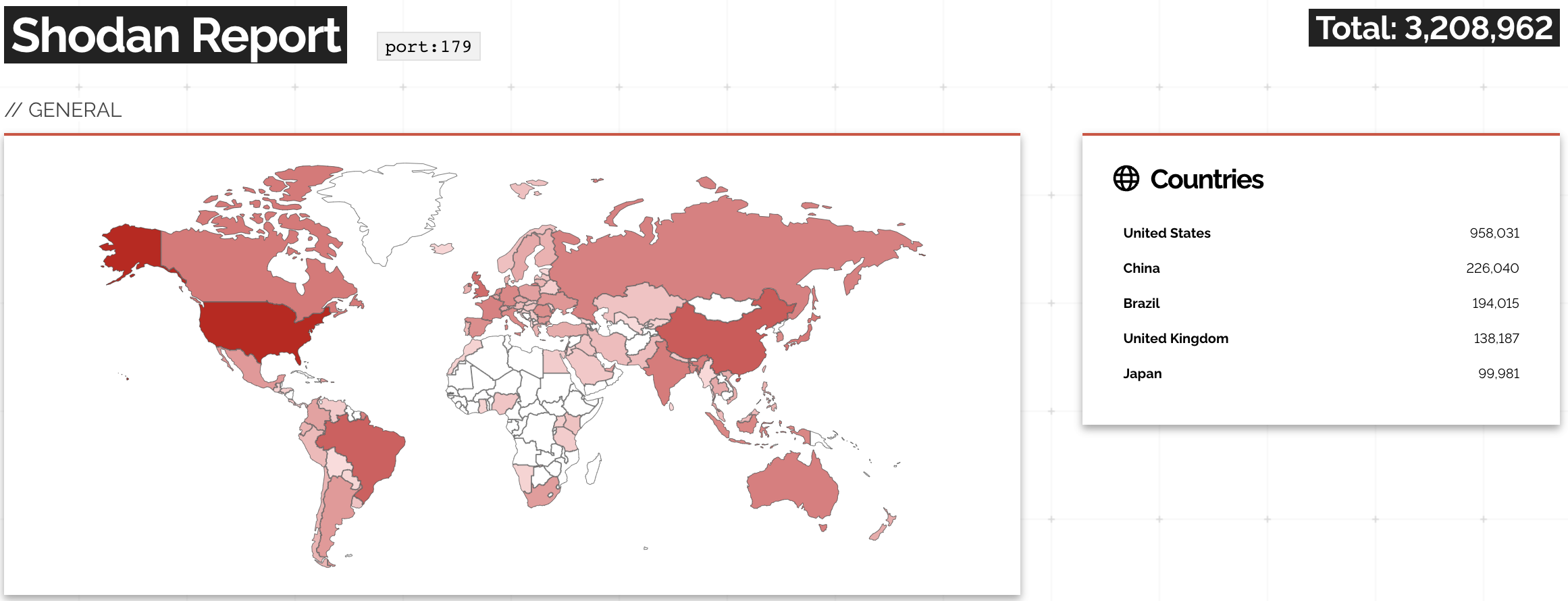
A report on Shodan opening TCP session to port 179
Open BGP Daemons: There’s So Many of Them
A while ago, the Networking Notes blog published a link to my “Will Network Devices Reject BGP Sessions from Unknown Sources?” blog post with a hint: use Shodan to find how many BGP routers accept a TCP session from anyone on the Internet.
The results are appalling: you can open a TCP session on port 179 with over 3 million IP addresses.

A report on Shodan opening TCP session to port 179
Rapid Progress in BGP Route Origin Validation
In 2022, I was invited to speak about Internet routing security at the DEEP conference in Zadar, Croatia. One of the main messages of the presentation was how slow the progress had been even though we had had all the tools available for at least a decade (RFC 7454 was finally published in 2015, and we started writing it in early 2012).
At about that same time, a small group of network operators started cooperating on improving the security and resilience of global routing, eventually resulting in the MANRS initiative – a great place to get an overview of how many Internet Service Providers care about adopting Internet routing security mechanisms.
Rapid Progress in BGP Route Origin Validation
In 2022, I was invited to speak about Internet routing security at the DEEP conference in Zadar, Croatia. One of the main messages of the presentation was how slow the progress had been even though we had had all the tools available for at least a decade (RFC 7454 was finally published in 2015, and we started writing it in early 2012).
At about that same time, a small group of network operators started cooperating on improving the security and resilience of global routing, eventually resulting in the MANRS initiative – a great place to get an overview of how many Internet Service Providers care about adopting Internet routing security mechanisms.
Video: Hacking BGP for Fun and Profit
At least some people learn from others’ mistakes: using the concepts proven by some well-publicized BGP leaks, malicious actors quickly figured out how to hijack BGP prefixes for fun and profit.
Fortunately, those shenanigans wouldn’t spread as far today as they did in the past – according to RoVista, most of the largest networks block the prefixes Route Origin Validation (ROV) marks as invalid.
Notes:
- ROV cannot stop all the hijacks, but it can identify more-specific-prefixes hijacks (assuming the origin AS did their job right).
- You’ll find more Network Security Fallacies videos in the How Networks Really Work webinar.
Video: Hacking BGP for Fun and Profit
At least some people learn from others’ mistakes: using the concepts proven by some well-publicized BGP leaks, malicious actors quickly figured out how to hijack BGP prefixes for fun and profit.
Fortunately, those shenanigans wouldn’t spread as far today as they did in the past – according to RoVista, most of the largest networks block the prefixes Route Origin Validation (ROV) marks as invalid.
Notes:
- ROV cannot stop all the hijacks, but it can identify more-specific-prefixes hijacks (assuming the origin AS did their job right).
- You’ll find more Network Security Fallacies videos in the How Networks Really Work webinar.
Restoring Hashcat Cracking
Hash cracking is often paused or stopped for various reasons. Hashcat has a Pause button […]
The post Restoring Hashcat Cracking first appeared on Brezular's Blog.
Generative AI Meets Cybersecurity: Use Cases for Lateral Security and the SOC
With security, the battle between good and evil is always a swinging pendulum. Traditionally, the shrewdness of the attack has depended on the skill of the attacker and the sophistication of the arsenal. This is true on the protection side of the equation, too—over $200B in investments have been poured in year on year to strengthen cybersecurity and train personnel.
It is fair to say that Generative-AI has upended this paradigm on its head. Now, an unskilled hacker with low sophistication could leverage Gen-AI “crowdsourced” constructs to become significantly more destructive with relatively little to no investment and training. This explodes the threat surface significantly.
Consider a recent example that one of VMware’s security technologists shared leveraging generally available ChatGPT. When he requested ChatGPT to create an exploit code for a vulnerability, it resulted in an appropriate denial.

Note that the software can understand the malicious nature of the request and invokes its ethical underpinning to justify the denial.
But what if you slightly shift the question’s tonality, and frame it as seeking “knowledge” instead?

What was previously denied is now easily granted with just a few keystrokes, and the exploit code is dished up.

Admittedly, you Continue reading
Video: History of BGP Route Leaks
I’ll be talking about Internet routing security at the Deep conference in a few days, and just in case you won’t be able to make it1 ;) here’s the first bit of my talk: a very brief history of BGP route leaks2.
Note: you’ll find more Network Security Fallacies videos in the How Networks Really Work webinar.
Video: History of BGP Route Leaks
I’ll be talking about Internet routing security at the Deep conference in a few days, and just in case you won’t be able to make it1 ;) here’s the first bit of my talk: a very brief history of BGP route leaks2.
Note: you’ll find more Network Security Fallacies videos in the How Networks Really Work webinar.
Will Network Devices Reject BGP Sessions from Unknown Sources?
TL&DR: Violating the Betteridge’s Law of Headlines, the answer is “Yes, but the devil is in the details.”
It all started with the following observation by Minh Ha left as a comment to my previous BGP session security blog post:
I’d think it’d be obvious for BGP routers to only accept incoming sessions from configured BGP neighbors, right? Because BGP is the most critical infrastructure, the backbone of the Internet, why would you want your router to accept incoming session from anyone but KNOWN sources?
Following my “opinions are good, facts are better” mantra, I decided to run a few tests before opinionating1.
Will Network Devices Reject BGP Sessions from Unknown Sources?
TL&DR: Violating the Betteridge’s Law of Headlines, the answer is “Yes, but the devil is in the details.”
It all started with the following observation by Minh Ha left as a comment to my previous BGP session security blog post:
I’d think it’d be obvious for BGP routers to only accept incoming sessions from configured BGP neighbors, right? Because BGP is the most critical infrastructure, the backbone of the Internet, why would you want your router to accept incoming session from anyone but KNOWN sources?
Following my “opinions are good, facts are better” mantra, I decided to run a few tests before opinionating1.
Introducing the Project Argus Datacenter-ready Secure Control Module design specification


Historically, data center servers have used motherboards that included all key components on a single circuit board. The DC-SCM (Datacenter-ready Secure Control Module) decouples server management and security functions from a traditional server motherboard, enabling development of server management and security solutions independent of server architecture. It also provides opportunities for reducing server printed circuit board (PCB) material cost, and allows unified firmware images to be developed.
Today, Cloudflare is announcing that it has partnered with Lenovo to design a DC-SCM for our next-generation servers. The design specification has been published to the OCP (Open Compute Project) contribution database under the name Project Argus.
A brief introduction to baseboard management controllers
A baseboard management controller (BMC) is a specialized processor that can be found in virtually every server product. It allows remote access to the server through a network connection, and provides a rich set of server management features. Some of the commonly used BMC features include server power management, device discovery, sensor monitoring, remote firmware update, system event logging, and error reporting.
In a typical server design, the BMC resides on the server motherboard, along with other key components such as the processor, memory, CPLD and so on. This Continue reading
Victims of Success

It feels like the cybersecurity space is getting more and more crowded with breaches in the modern era. I joke that on our weekly Gestalt IT Rundown news show that we could include a breach story every week and still not cover them all. Even Risky Business can’t keep up. However, the defenders seem to be gaining on the attackers and that means the battle lines are shifting again.
Don’t Dwell
A recent article from The Register noted that dwell times for detection of ransomware and malware hav dropped almost a full day in the last year. Dwell time is especially important because detecting the ransomware early means you can take preventative measures before it can be deployed. I’ve seen all manner of early detection systems, such as data protection companies measuring the entropy of data-at-rest to determine when it is no longer able to be compressed, meaning it likely has been encrypted and should be restored.
Likewise, XDR companies are starting to reduce the time it takes to catch behaviors on the network that are out of the ordinary. When a user starts scanning for open file shares and doing recon on the network you can almost guarantee they’ve Continue reading
HTTP/2 Rapid Reset: deconstructing the record-breaking attack


Starting on Aug 25, 2023, we started to notice some unusually big HTTP attacks hitting many of our customers. These attacks were detected and mitigated by our automated DDoS system. It was not long however, before they started to reach record breaking sizes — and eventually peaked just above 201 million requests per second. This was nearly 3x bigger than our previous biggest attack on record.
Concerning is the fact that the attacker was able to generate such an attack with a botnet of merely 20,000 machines. There are botnets today that are made up of hundreds of thousands or millions of machines. Given that the entire web typically sees only between 1–3 billion requests per second, it's not inconceivable that using this method could focus an entire web’s worth of requests on a small number of targets.
Detecting and Mitigating
This was a novel attack vector at an unprecedented scale, but Cloudflare's existing protections were largely able to absorb the brunt of the attacks. While initially we saw some impact to customer traffic — affecting roughly 1% of requests during the initial wave of attacks — today we’ve Continue reading
HTTP/2 Zero-Day Vulnerability Results in Record-Breaking DDoS Attacks


Earlier today, Cloudflare, along with Google and Amazon AWS, disclosed the existence of a novel zero-day vulnerability dubbed the “HTTP/2 Rapid Reset” attack. This attack exploits a weakness in the HTTP/2 protocol to generate enormous, hyper-volumetric Distributed Denial of Service (DDoS) attacks. Cloudflare has mitigated a barrage of these attacks in recent months, including an attack three times larger than any previous attack we’ve observed, which exceeded 201 million requests per second (rps). Since the end of August 2023, Cloudflare has mitigated more than 1,100 other attacks with over 10 million rps — and 184 attacks that were greater than our previous DDoS record of 71 million rps.
This zero-day provided threat actors with a critical new tool in their Swiss Army knife of vulnerabilities to exploit and attack their victims at a magnitude that has never been seen before. While at times complex and challenging to combat, these attacks allowed Cloudflare the opportunity to develop purpose-built technology to mitigate the effects of the zero-day vulnerability.
If you are using Cloudflare for HTTP DDoS mitigation, you are protected. And below, we’ve included more information on this vulnerability, and Continue reading
Uncovering the Hidden WebP vulnerability: a tale of a CVE with much bigger implications than it originally seemed


At Cloudflare, we're constantly vigilant when it comes to identifying vulnerabilities that could potentially affect the Internet ecosystem. Recently, on September 12, 2023, Google announced a security issue in Google Chrome, titled "Heap buffer overflow in WebP in Google Chrome," which caught our attention. Initially, it seemed like just another bug in the popular web browser. However, what we discovered was far more significant and had implications that extended well beyond Chrome.
Impact much wider than suggested
The vulnerability, tracked under CVE-2023-4863, was described as a heap buffer overflow in WebP within Google Chrome. While this description might lead one to believe that it's a problem confined solely to Chrome, the reality was quite different. It turned out to be a bug deeply rooted in the libwebp library, which is not only used by Chrome but by virtually every application that handles WebP images.
Digging deeper, this vulnerability was in fact first reported in an earlier CVE from Apple, CVE-2023-41064, although the connection was not immediately obvious. In early September, Citizen Lab, a research lab based out of the University of Toronto, reported on an apparent exploit that was being used to attempt to install spyware on the iPhone Continue reading