We Won’t Save the Internet by Breaking It

On the anniversary of the armistice ending the First World War, more than 40 countries stood together for security online by signing the Paris Call for Trust and Security in Cyberspace. The call, which sets out a list of challenges the world needs to tackle, seems to be promising on paper. From hacking to harming the public core – all of this needs to be addressed. And it needs to be addressed urgently.
Others signed the call too. The Internet Society signed because we believe it is a continuation of calls we have made before. It maintains that solutions to Internet issues must be developed together with other Internet stakeholders – each performing its role, and all working collaboratively.
This approach is what allows the Internet to thrive and is key to the ultimate success of this call. Open, decentralized, and distributed. It’s not the traditional multilateral way of doing things, but it is the Internet way – the only one that can work.
There are real and pressing Internet security concerns. It’s critical that signatories to the call do not imagine they can address the concerns alone. The Internet depends, as a technical fact, on cooperative voluntary action, so Continue reading
Michigan VC Firm Deploys Bigleaf SD-WAN to Its Car Dealerships
 As venture capital firm DP Fox began to migrate its business-critical applications to the cloud it needed a connectivity service that could keep up with its growing portfolio.
As venture capital firm DP Fox began to migrate its business-critical applications to the cloud it needed a connectivity service that could keep up with its growing portfolio.
The rise of multivector DDoS attacks
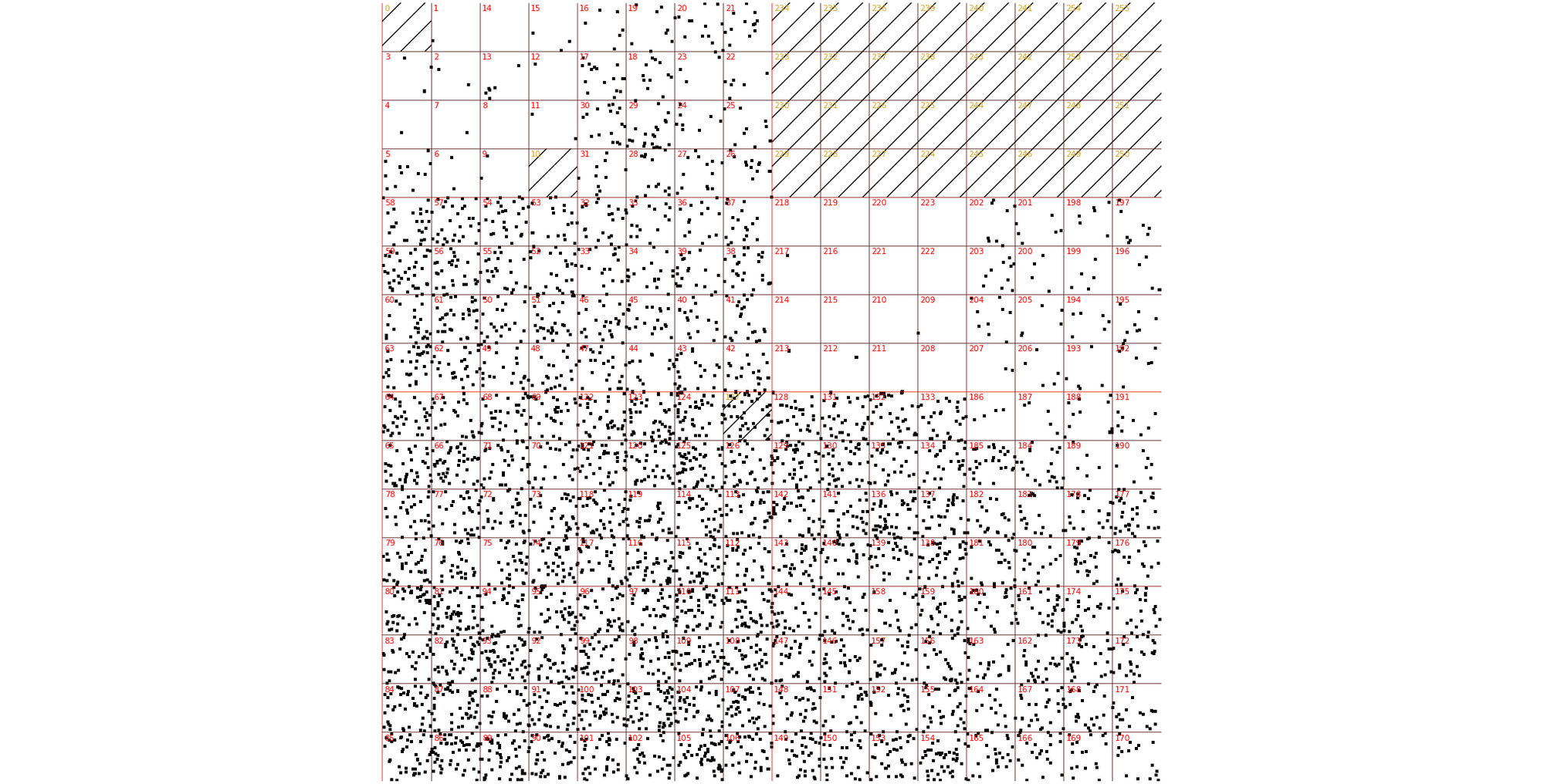
It's been a while since we last wrote about Layer 3/4 DDoS attacks on this blog. This is a good news - we've been quietly handling the daily onslaught of DDoS attacks. Since our last write-up, a handful of interesting L3/4 attacks have happened. Let's review them.
Gigantic SYN
In April, John tweeted about a gigantic 942Gbps SYN flood:
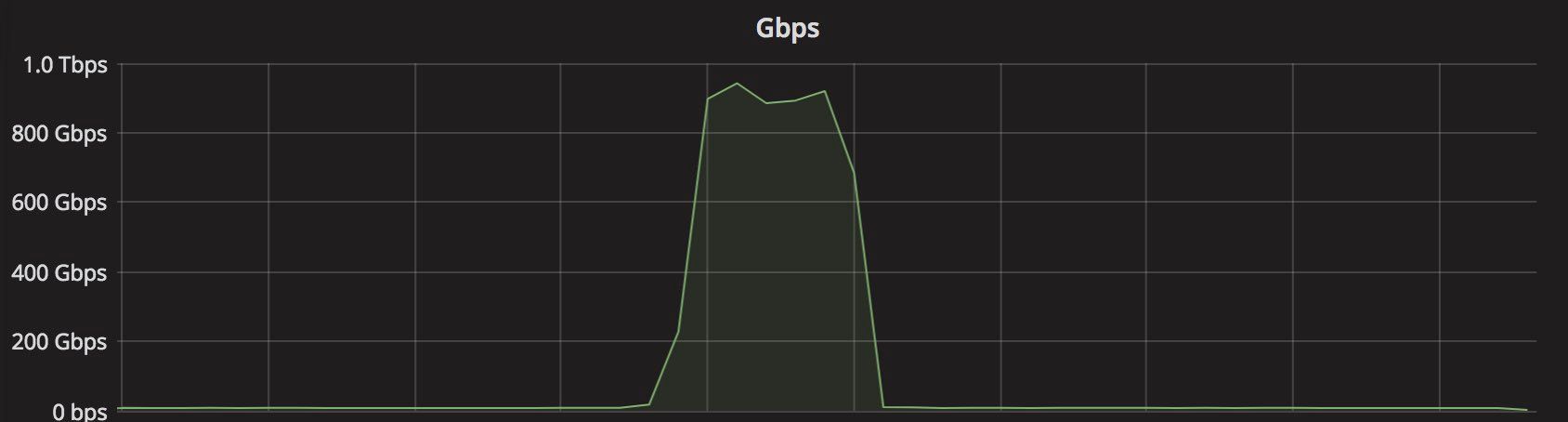
It was a notable event for a couple of reasons.
First, it was really large. Previously, we've seen only amplification / reflection attacks at terabit scale. In those cases, the attacker doesn't actually have too much capacity. They need to bounce the traffic off other servers to generate a substantial load. This is different from typical "direct" style attacks, like SYN floods. In the SYN flood mentioned by John, all 942Gbps were coming directly from attacker-controlled machines.
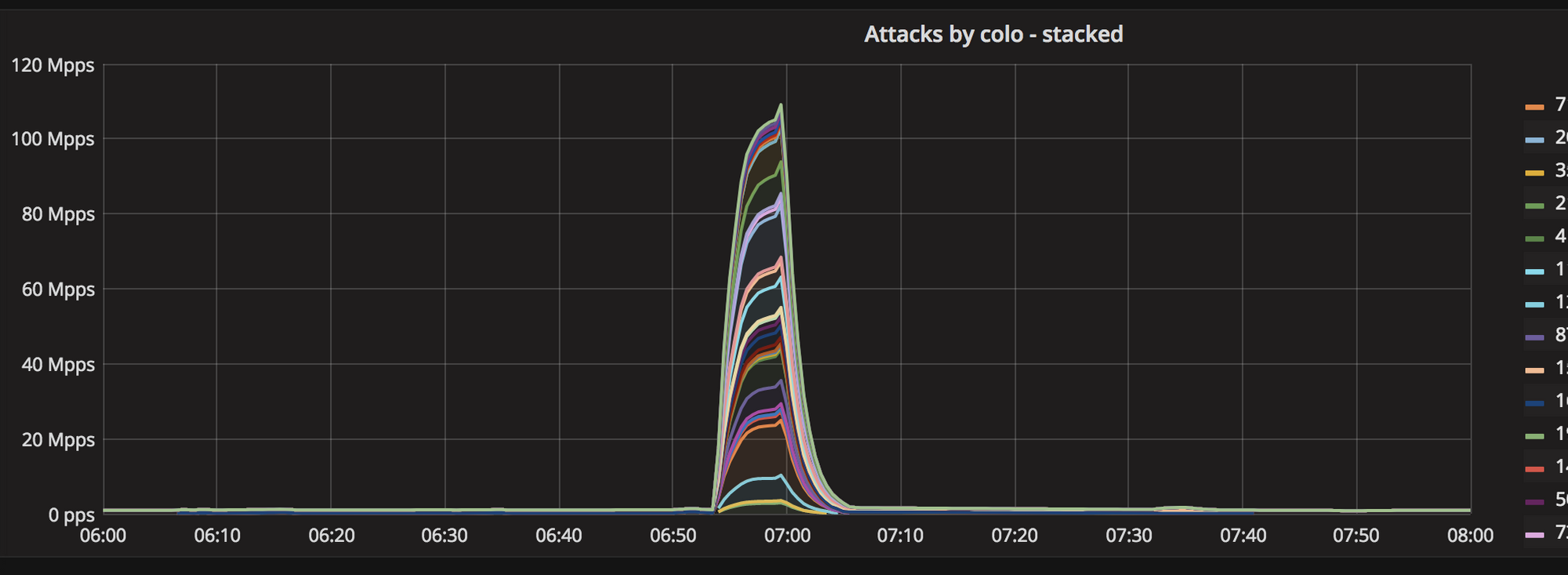
Secondly, this attack was truly distributed. Normal SYN floods come from a small number of geographical locations. This one, was all over the globe, hitting all Cloudflare data centers:
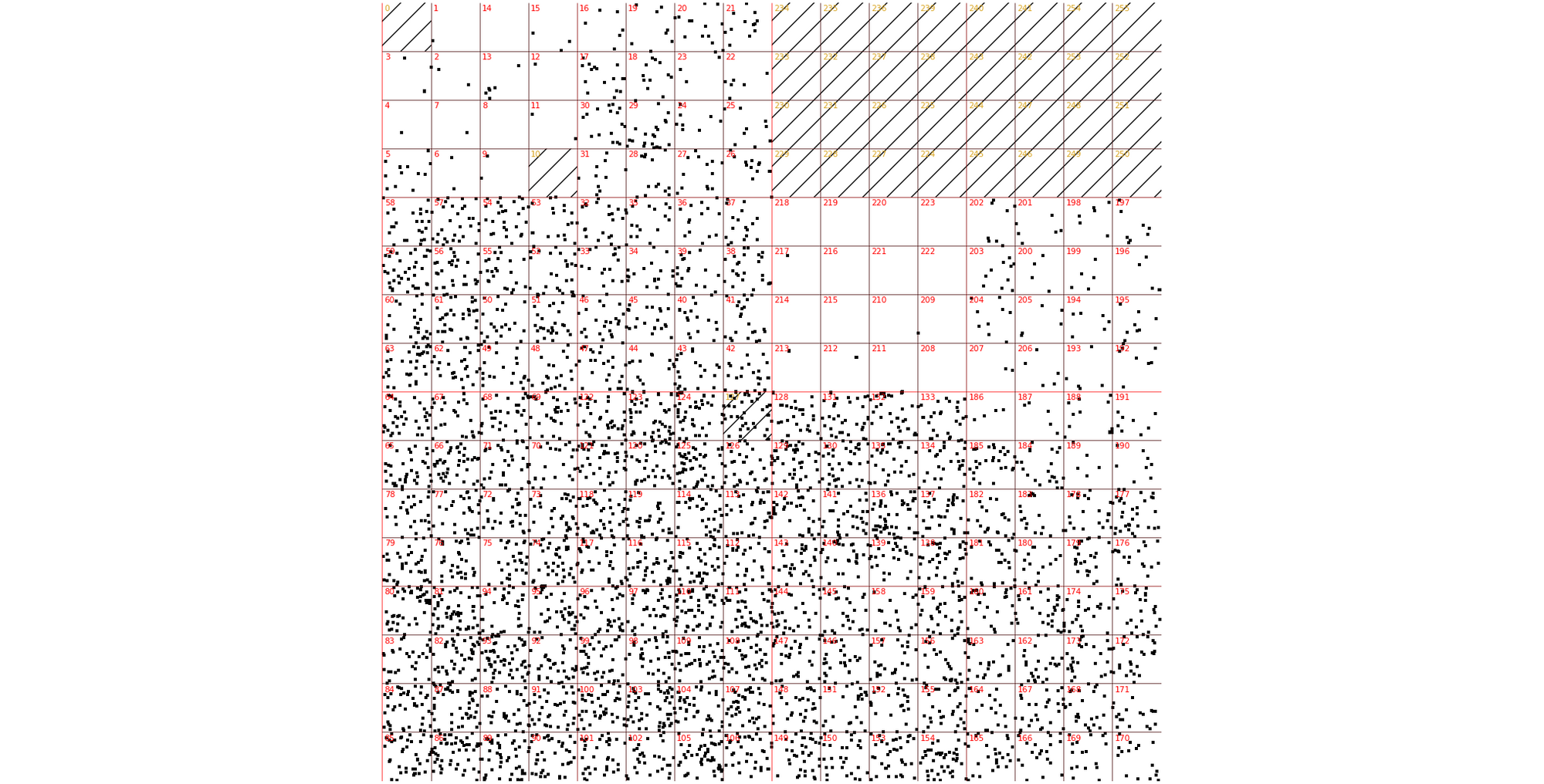
Thirdly, the attack seem to be partially spoofed. While our analysis was not conclusive, we saw random, spoofed source IP addresses in the largest internet exchanges. The above Hilbert curve shows the source IP Continue reading
How Network Automation Increases Security
This blog post was initially sent to subscribers of my SDN and Network Automation mailing list. Subscribe here.
After publishing the Manual Work Is a Bug blog post, I got this feedback from Michele Chubirka explaining why automating changes in your network also increases network security:
Read more ...Global Cybersecurity and the Internet Conundrum

Today marks the 100th anniversary of the armistice that ended the first World War. The 1918 ceasefire re-introduced a fragile peace that had collapsed when the world failed to defend common rules and international cooperation. International security and stability are as important now as they were a century ago.
That’s why French President Emmanuel Macron and leaders from around the world are about to gather in Paris for the first Paris Peace Forum. The forum will attempt to pave a way forward for a world that is shifting and changing faster than most of us can keep up with. That change and shift, and the speed of it is enabled by the Internet.
That is why the Internet Society is participating in the Forum.
I will be in Paris to speak on a panel about creating peace in cyberspace. Cybersecurity concerns across the world are real and justified and need to be addressed. We believe that the collaborative approach that helped to drive the growth of the Internet and allows it to thrive is essential for establishing cybersecurity.
The essence of a collaborative approach is that it allows stakeholders to create a shared vision for security.
The Shared Vision
At the Continue reading
ForeScout Buys SecurityMatters for $113 to Expand Network Protection
 The Netherlands-based startup provides device visibility, continuous network monitoring, and threat and anomaly detection specific to operational technology and industrial environments.
The Netherlands-based startup provides device visibility, continuous network monitoring, and threat and anomaly detection specific to operational technology and industrial environments.
Cisco Continues Kubernetes Kraze With AWS Hybrid Software
 While Cisco adds Kubernetes support across its portfolio, other vendors like VMware and IBM recently bought companies to boost their container cred.
While Cisco adds Kubernetes support across its portfolio, other vendors like VMware and IBM recently bought companies to boost their container cred.
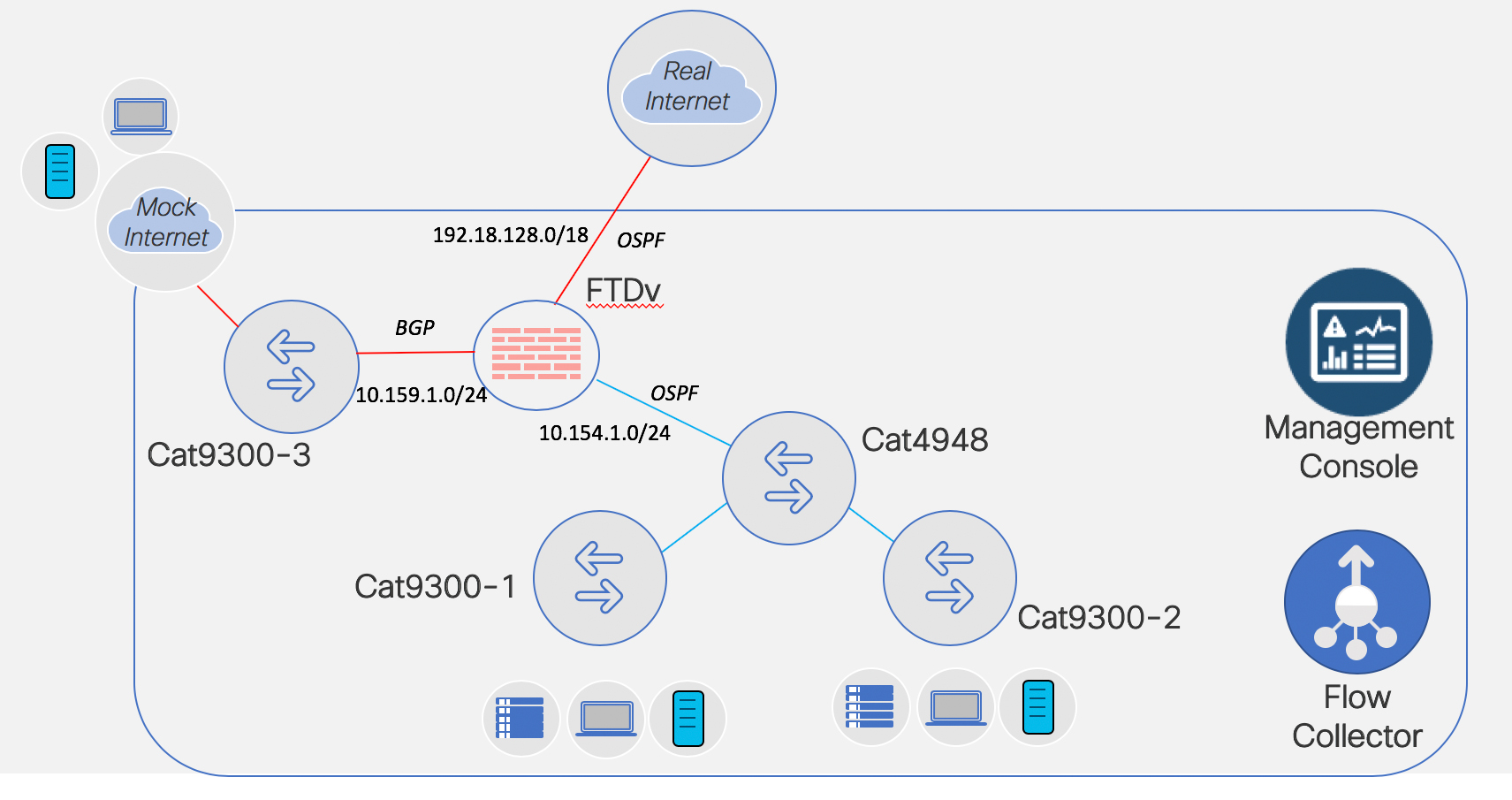
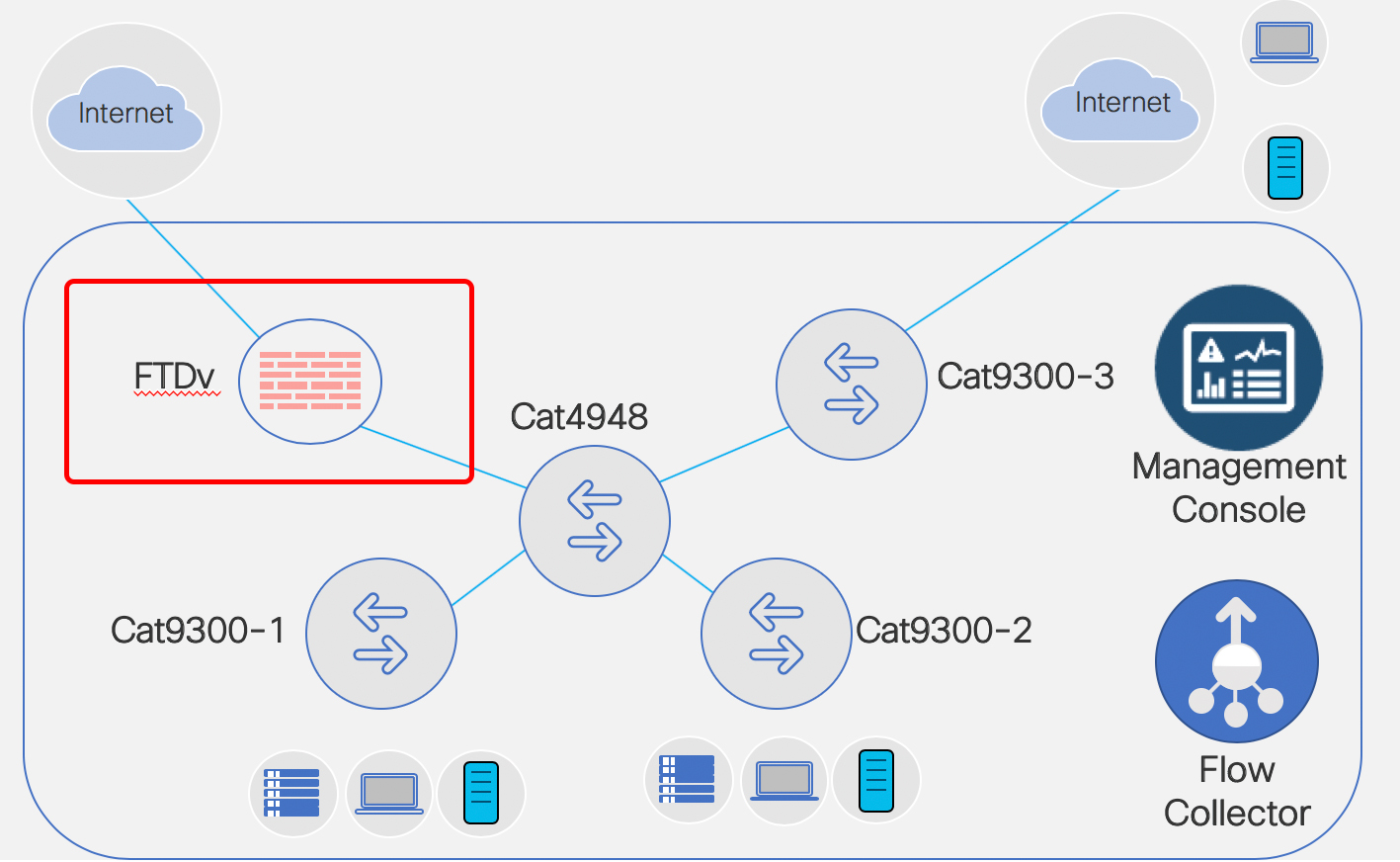
Setting Up Addressing and Routing: FTDv Fun
In my previous blog (Fun in the Lab: FTDv & FMC – Install and Deploy) we deployed a FMC VM and a FTDv VM and ended the blog with the FTDv successfully added to the FMC.
Now? Now let’s add IP addressing for the FTDv and also set up routing protocol neighbor relationships. I learned what I am about to show you from my co-worker and friend, Keith Brister. So don’t thank me, thank Keith. 
I tossed together a ~29 minute YouTube. Obviously you can watch the entire thing. Or… here you go for the big sections.
- Overview – Start to 2:17 minutes
- Physical/Logical Mapping Overview – 2:18 to 9:25
- vSwitches, vmNICs and More in VMware – 9:26 to 16:20
- FTDv Configuring IP Adresses via FMC – 16:21 to 23:18
- FTDv Configuring IP Routing via FMC – 23:19 to 29:29
Done and Done. Easy Peasy!
Research Brief: Evolution of Security in Mobile Networks – Impact of 5G
 This new Research Brief from AvidThink delves into the evolution of the mobile network and explores new threats.
This new Research Brief from AvidThink delves into the evolution of the mobile network and explores new threats.
Related Stories
Fun in the Lab: FTDv & FMC – Install and Deploy
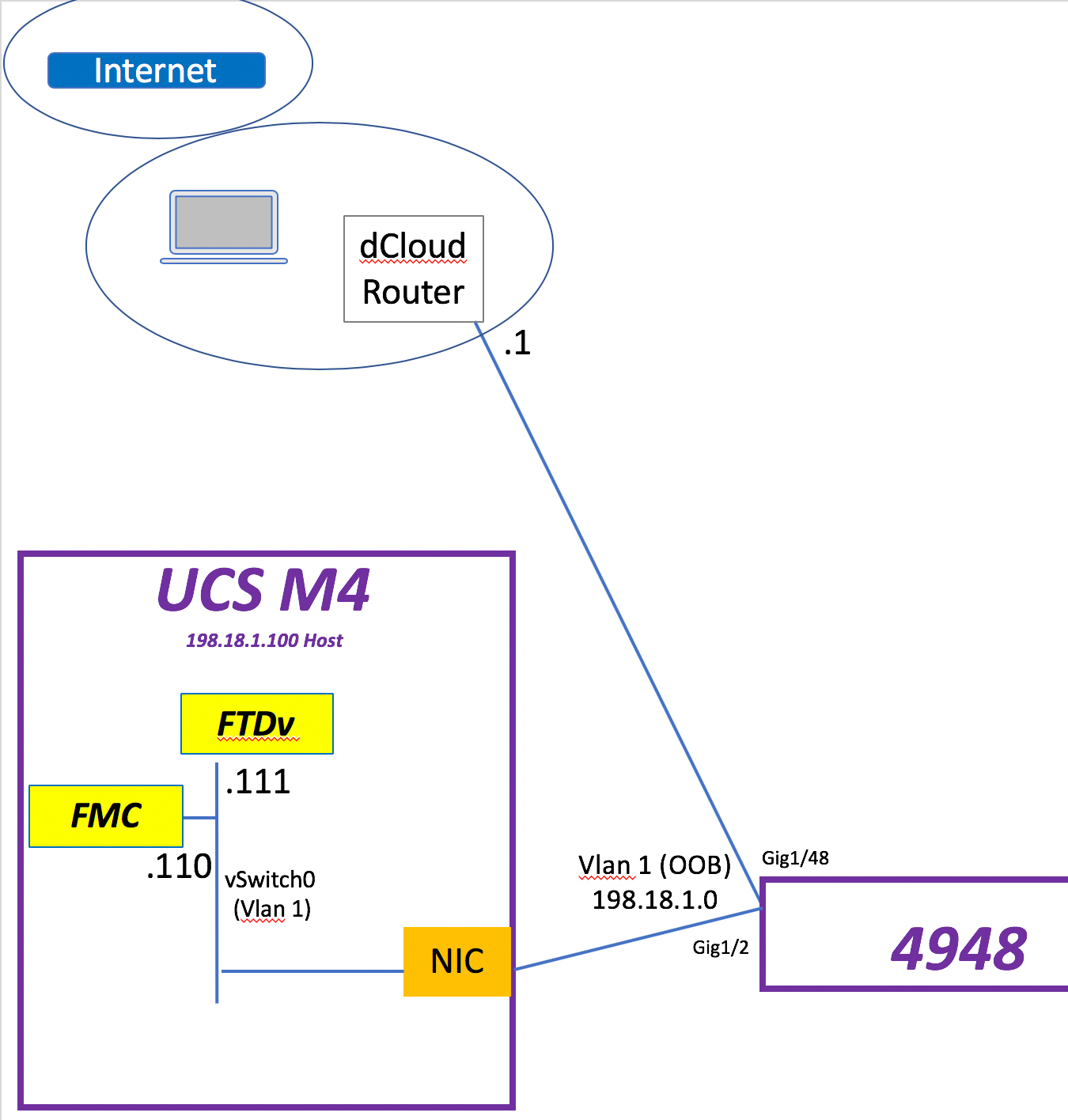
This is my Stealthwatch playground…. errrr… I mean … ahem… “work environment” for a Technical Solution Workshop I am working on for Stealthwatch.
Going to set up FTDv and FMC today. A co-worker and friend, Scott Barasch, helped me get jump started… so figure I’ll pass on what I just learned to you. 
What this blog will cover is
- DEPLOY
- Deploying the OVF for FTDv
- Deploying the OVF for FMC
- VMware settings
- Tweak for FTDv
- Tweak for FMC
- Prepping to Power On
- Snapshot Both Before Power On
- Power Both On
- Setup via Console
- FMC – console in and setup IP address
- FTDv – console in and step thru the prompts
- Test IP Connectivity
- Ping FMC and FTDv from the PC
- Notice Can’t ping FTDv
- Fix
- Ping
- Browse into FMC
- Change password
- Setup DNS
- Setup NTP
- Accept EULA
- Apply
- LICENSING
- License FMC
- FMC/FTDv: Make the Connection
- FTDv – Point FTDv to FMC
- FMC – bring the FTDv into the fold.

So let’s begin. What I have to host my FMC & FTDv VMs is a UCS M4 with a NIC connected to a Cat4948 in vlan 1. That NIC is tied to vSwitch0 in the UCS. Continue reading
VMware Embraces Containers at VMworld Europe
 The virtualization giant updated its hybrid cloud stack with new Kubernetes support and also announced a new integration with IBM Cloud’s managed Kubernetes service.
The virtualization giant updated its hybrid cloud stack with new Kubernetes support and also announced a new integration with IBM Cloud’s managed Kubernetes service.
Thoma Bravo Acquires Veracode From Broadcom for $950 Million
 Broadcom took over Veracode as part of its $18.9 billion purchase of CA Technologies, which it completed this week. CA bought Veracode in 2017.
Broadcom took over Veracode as part of its $18.9 billion purchase of CA Technologies, which it completed this week. CA bought Veracode in 2017.
T-Mobile, Sprint Merger Foes Raise Security Concerns Related to Huawei, ZTE
 It's no surprise that groups representing wireless workers claim the merger will cost American jobs. But connecting T-Mobile and Sprint to possible security risks related to China is a new angle that could have an impact on the deal.
It's no surprise that groups representing wireless workers claim the merger will cost American jobs. But connecting T-Mobile and Sprint to possible security risks related to China is a new angle that could have an impact on the deal.
Symantec Buys Appthority, Javelin Networks to Strengthen Endpoint Security
 The two acquisitions will boost the company's mobile and enterprise credentials, particularly with regard to Active Directory and mobile application security.
The two acquisitions will boost the company's mobile and enterprise credentials, particularly with regard to Active Directory and mobile application security.
BGP Hijacks: Two more papers consider the problem
The security of the global Default Free Zone DFZ) has been a topic of much debate and concern for the last twenty years (or more). Two recent papers have brought this issue to the surface once again—it is worth looking at what these two papers add to the mix of what is known, and what solutions might be available. The first of these—
Demchak, Chris, and Yuval Shavitt. 2018. “China’s Maxim – Leave No Access Point Unexploited: The Hidden Story of China Telecom’s BGP Hijacking.” Military Cyber Affairs 3 (1). https://doi.org/10.5038/2378-0789.3.1.1050.
—traces the impact of Chinese “state actor” effects on BGP routing in recent years. Whether these are actual attacks, or mistakes from human error for various reasons generally cannot be known, but the potential, at least, for serious damage to companies and institutions relying on the DFZ is hard to overestimate. This paper lays out the basic problem, and the works through a number of BGP hijacks in recent years, showing how they misdirected traffic in ways that could have facilitated attacks, whether by mistake or intentionally. For instance, quoting from the paper—
- Starting from February 2016 and for about 6 months, routes Continue reading
Brian Kemp is bad on cybersecurity
I'd prefer a Republican governor, but as a cybersecurity expert, I have to point out how bad Brian Kemp (candidate for Georgia governor) is on cybersecurity. When notified about vulnerabilities in election systems, his response has been to shoot the messenger rather than fix the vulnerabilities. This was the premise behind the cybercrime bill earlier this year that was ultimately vetoed by the current governor after vocal opposition from cybersecurity companies. More recently, he just announced that he's investigating the Georgia State Democratic Party for a "failed hacking attempt".According to news stories, state elections websites are full of common vulnerabilities, those documented by the OWASP Top 10, such as "direct object references" that would allow any election registration information to be read or changed, as allowing a hacker to cancel registrations of those of the other party.
Testing for such weaknesses is not a crime. Indeed, it's desirable that people can test for security weaknesses. Systems that aren't open to test are insecure. This concept is the basis for many policy initiatives at the federal level, to not only protect researchers probing for weaknesses from prosecution, but to even provide bounties encouraging them to do so. Continue reading
Fortinet Posts Solid Q3 Growth, Wins ‘Quadruple Competitor Displacement’ Deal
 Execs didn’t say which competitors Fortinet’s security products displaced, but it competes against companies including Palo Alto Networks, Check Point Software, and Cisco.
Execs didn’t say which competitors Fortinet’s security products displaced, but it competes against companies including Palo Alto Networks, Check Point Software, and Cisco.
Why no cyber 9/11 for 15 years?
This The Atlantic article asks why hasn't there been a cyber-terrorist attack for the last 15 years, or as it phrases it:National-security experts have been warning of terrorist cyberattacks for 15 years. Why hasn’t one happened yet?As a pen-tester who has broken into power grids and found 0dayss in control center systems, I thought I'd write up some comments.
Instead of asking why one hasn't happened yet, maybe we should instead ask why national-security experts keep warning about them.
One possible answer is that national-security experts are ignorant. I get the sense that "national" security experts have very little expertise in "cyber" security. That's why I include a brief resume at the top of this article, I've actually broken into a power grid and found 0days in critical power grid products (specifically, the ABB implementation of ICCP on AIX -- it's rather an obvious buffer-overflow, *cough* ASN.1 *cough*, I don't know if they ever fixed it).
Another possibility is that they are fear mongering in order to support their agenda. That's the problem with "experts", they get their expertise by being employed to achieve some goal. The ones who know most about an issue are simultaneously the Continue reading
Cisco Study Finds Enterprises Racing Toward ‘Preemptive’ IT
 Cisco developed a four-step model for IT operations maturity showing where organizations are now and where they would like to be in two years.
Cisco developed a four-step model for IT operations maturity showing where organizations are now and where they would like to be in two years.