Solving Container Security Requires New Tools and Processes
 This eBrief from SDxCentral delves into the latest developments in container security and looks at the techniques companies are using to ensure their container environments are secure and not vulnerable to breaches.
This eBrief from SDxCentral delves into the latest developments in container security and looks at the techniques companies are using to ensure their container environments are secure and not vulnerable to breaches.
Expanding DNSSEC Adoption


Cloudflare first started talking about DNSSEC in 2014 and at the time, Nick Sullivan wrote: “DNSSEC is a valuable tool for improving the trust and integrity of DNS, the backbone of the modern Internet.”
Over the past four years, it has become an even more critical part of securing the internet. While HTTPS has gone a long way in preventing user sessions from being hijacked and maliciously (or innocuously) redirected, not all internet traffic is HTTPS. A safer Internet should secure every possible layer between a user and the origin they are intending to visit.
As a quick refresher, DNSSEC allows a user, application, or recursive resolver to trust that the answer to their DNS query is what the domain owner intends it to be. Put another way: DNSSEC proves authenticity and integrity (though not confidentiality) of a response from the authoritative nameserver. Doing so makes it much harder for a bad actor to inject malicious DNS records into the resolution path through BGP Leaks and cache poisoning. Trust in DNS matters even more when a domain is publishing record types that are used to declare trust for other systems. As a specific example, DNSSEC is helpful for preventing Continue reading
Juniper Brings Contrail to the Edge, Works Closely With Red Hat
 Distributed computing with Red Hat OpenStack Platform allows the Contrail Edge Cloud to remotely manage the lifecycle of compute nodes and virtual machines (VMs) from a centralized data center without requiring co-located OpenStack control plane functions in each of these remote edge sites.
Distributed computing with Red Hat OpenStack Platform allows the Contrail Edge Cloud to remotely manage the lifecycle of compute nodes and virtual machines (VMs) from a centralized data center without requiring co-located OpenStack control plane functions in each of these remote edge sites.
End-to-End Integrity with IPFS
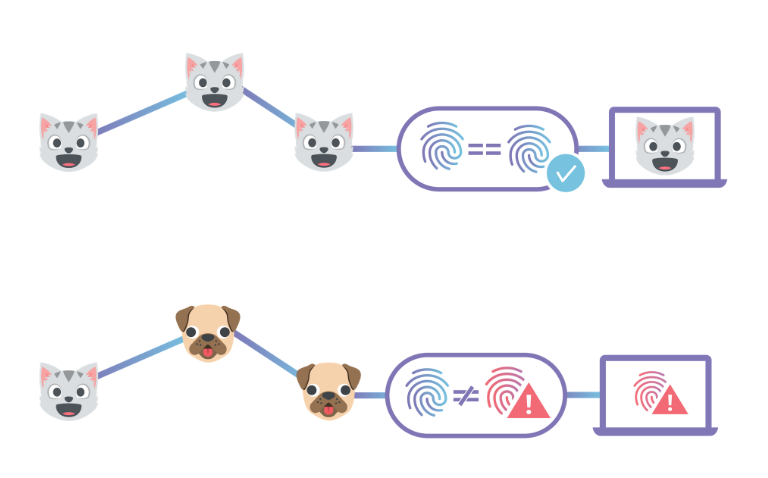
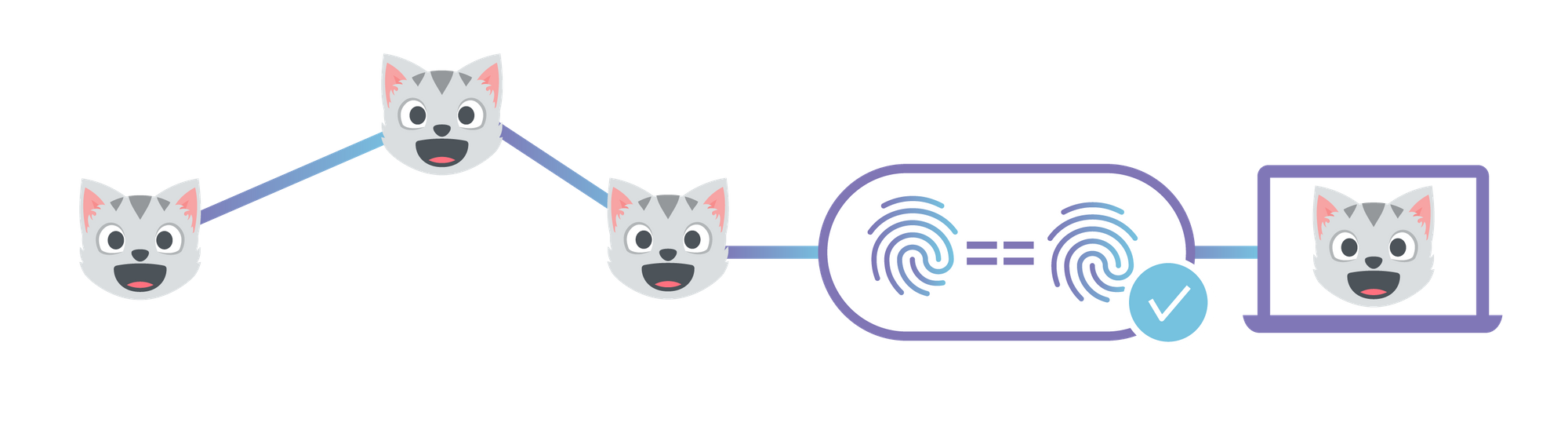
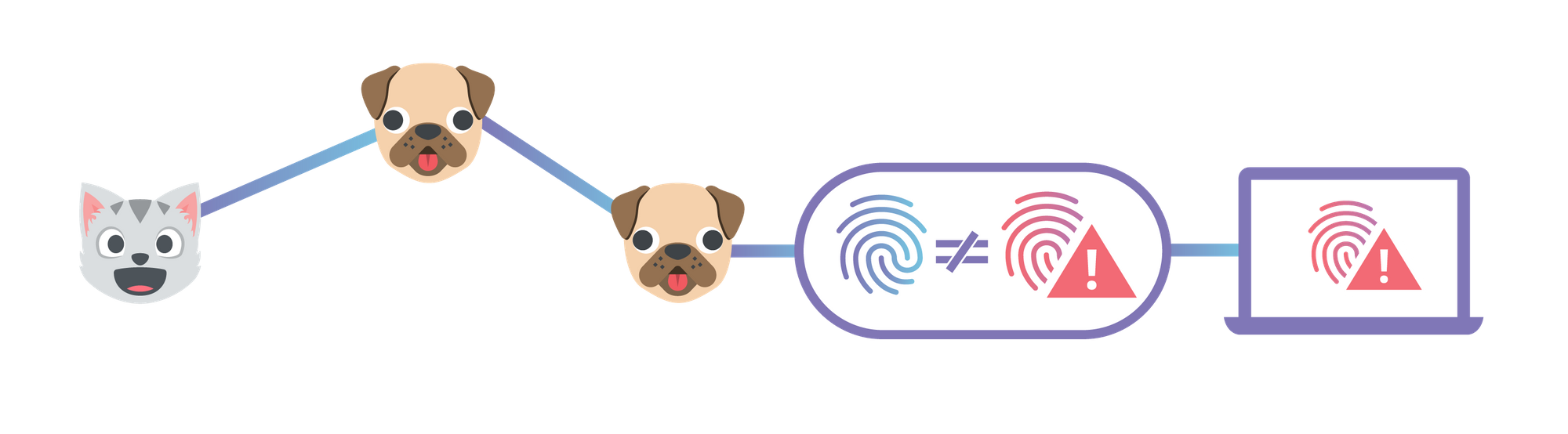
This post describes how to use Cloudflare's IPFS gateway to set up a website which is end-to-end secure, while maintaining the performance and reliability benefits of being served from Cloudflare’s edge network. If you'd rather read an introduction to the concepts behind IPFS first, you can find that in our announcement. Alternatively, you could skip straight to the developer docs to learn how to set up your own website.
By 'end-to-end security', I mean that neither the site owner nor users have to trust Cloudflare to serve the correct documents, like they do now. This is similar to how using HTTPS means you don't have to trust your ISP to not modify or inspect traffic.
CNAME Setup with Universal SSL
The first step is to choose a domain name for your website. Websites should be given their own domain name, rather than served directly from the gateway by root hash, so that they are considered a distinct origin by the browser. This is primarily to prevent cache poisoning, but there are several functional advantages as well. It gives websites their own instance of localStorage and their own cookie jar which are sandboxed from inspection and manipulation by malicious third-party documents. Continue reading
Cloudflare goes InterPlanetary – Introducing Cloudflare’s IPFS Gateway


Today we’re excited to introduce Cloudflare’s IPFS Gateway, an easy way to access content from the InterPlanetary File System (IPFS) that doesn’t require installing and running any special software on your computer. We hope that our gateway, hosted at cloudflare-ipfs.com, will serve as the platform for many new highly-reliable and security-enhanced web applications. The IPFS Gateway is the first product to be released as part of our Distributed Web Gateway project, which will eventually encompass all of our efforts to support new distributed web technologies.
This post will provide a brief introduction to IPFS. We’ve also written an accompanying blog post describing what we’ve built on top of our gateway, as well as documentation on how to serve your own content through our gateway with your own custom hostname.
Quick Primer on IPFS

Usually, when you access a website from your browser, your browser tracks down the origin server (or servers) that are the ultimate, centralized repository for the website’s content. It then sends a request from your computer to that origin server, wherever it is in the world, and that server sends the content back to your computer. This system has served the Internet well for decades, Continue reading
Welcome to Crypto Week


The Internet is an amazing invention. We marvel at how it connects people, connects ideas, and makes the world smaller. But the Internet isn’t perfect. It was put together piecemeal through publicly funded research, private investment, and organic growth that has left us with an imperfect tapestry. It’s also evolving. People are constantly developing creative applications and finding new uses for existing Internet technology. Issues like privacy and security that were afterthoughts in the early days of the Internet are now supremely important. People are being tracked and monetized, websites and web services are being attacked in interesting new ways, and the fundamental system of trust the Internet is built on is showing signs of age. The Internet needs an upgrade, and one of the tools that can make things better, is cryptography.
Every day this week, Cloudflare will be announcing support for a new technology that uses cryptography to make the Internet better. Everything we are announcing this week is free to use and provides a meaningful step towards supporting a new capability or structural reinforcement. So why are we doing this? Because it’s good for the users and good for the Internet. Welcome to Crypto Week!
A more Continue reading
Trading Off Security And Performance Thanks To Spectre And Meltdown
The revelations by Google’s Project Zero team earlier this year of the Spectre and Meltdown speculative execution vulnerabilities in most of processors that have powered servers and PCs for the past couple of decades shook the industry as Intel and other chip makers scrambled to mitigate the risk of the threats in the short term and then implement plans to incorporate the mitigation techniques into future versions of the silicon. …
Trading Off Security And Performance Thanks To Spectre And Meltdown was written by Jeffrey Burt at .
From Idea to Action: Beyond the Net Selects 15 Amazing Chapter Projects!

The Beyond the Net Funding Programme is pleased to announce the results of our 2018 Grant Cycle. A total of 49 applications were received, and after a thorough reviewing process, 15 amazing projects were selected.
These projects are at the core of our mission, and will use the Internet to develop Community Networks in underserved areas, to empower women through ICT, as well as bringing awareness on Internet policies around the world.
This is the result of months of effort from our Chapter Community. Many discussions, numerous clarifications and proposals, updates, and revisions form the Beyond the Net Selection Committee. We are proud of you all.
Please join us in celebrating the following projects!
Developing community networks in the Northern region of Brazil – Brazil Chapter
Supporting and promoting the development of the Internet to enrich people’s lives, the project aim is to contribute to the growth and improvement of community networks policies and practices in Brazilian rural areas, in order to strengthen those who are marginalized. Instituto Nupef will work to develop a new network in the state of Maranhão as well as a developing a communications plan for the Babassu coconut breakers organizations and movements. Objectives include Continue reading
Securing Hyperconverged Systems: Why Traditional Security Tools Won’t Work
 Securing hyperconverged infrastructures requires a policy-based approach that intertwines security with applications.
Securing hyperconverged infrastructures requires a policy-based approach that intertwines security with applications.
Virtualization Is Core to Sprint Curiosity IoT Platform
 The IoT platform uses virtualization to push more processing capabilities to the edge of the network and a dedicated operating system to help the platform “come alive.”
The IoT platform uses virtualization to push more processing capabilities to the edge of the network and a dedicated operating system to help the platform “come alive.”
VMware Plans to Bring More AWS, Other Cloud-Native Services on Prem
 VMware’s Rajiv Ramaswami says the virtualization company wants to bring more cloud-native services into customers’ on-premises data centers.
VMware’s Rajiv Ramaswami says the virtualization company wants to bring more cloud-native services into customers’ on-premises data centers.
Research: Tail Attacks on Web Applications
When you think of a Distributed Denial of Service (DDoS) attack, you probably think about an attack which overflows the bandwidth available on a single link; or overflowing the number of half open TCP sessions a device can have open at once, preventing the device from accepting more sessions. In all cases, a DoS or DDoS attack will involve a lot of traffic being pushed at a single device, or across a single link.
- Denial of service attacks do not always require high volumes of traffic
- An intelligent attacker can exploit the long tail of service queues deep in a web application to bring the service down
- These kinds of attacks would be very difficult to detect
But if you look at an entire system, there are a lot of places where resources are scarce, and hence are places where resources could be consumed in a way that prevents services from operating correctly. Such attacks would not need to be distributed, because they could take much less traffic than is traditionally required to deny a service. These kinds of attacks are called tail attacks, because they attack the long tail of resource pools, where these pools are much Continue reading
Sysdig Scores $68.5M Series D to Boost Container Monitoring, Security
 Sysdig CEO Suresh Vasudevan declined to comment on the company’s plans for an initial public offering.
Sysdig CEO Suresh Vasudevan declined to comment on the company’s plans for an initial public offering.
QSYM: a practical concolic execution engine tailored for hybrid fuzzing
QSYM: a practical concolic execution engine tailored for hybrid fuzzing Yun et al., USENIX Security 2018
There are two main approaches to automated test case generated for uncovering bugs and vulnerabilities: fuzzing and concolic execution. Fuzzing is good at quickly exploring the input space, but can get stuck when trying to get past more complex conditional causes (i.e., when randomly generated inputs are unlikely to satisfy them). Concolic execution, which we saw in action earlier in the week, uses symbolic execution to uncover constraints and pass them to a solver. It can handle complex branch conditions, but it’s much slower. Hybrid fuzzers combine both coverage-guided fuzzing and concolic execution, bringing in the big guns (concolic) when the fuzzer gets stuck. In non-trivial real-world applications though, even the hybrid approach has been too slow. Until now.
For me, the attention grabbing paragraph in this paper is to be found on page 8 (752) in section 5.1. Google’s OSS-Fuzz was previously used to test a number of important real-world applications and libraries including libjpeg, libpng, libtiff, lepton, openjpge, tcpdump, file, libarchive, audiofile, ffmpeg, and binutils.
It is worth noting that Google’s OSS-Fuzz generated 10 trillion test inputs Continue reading
California’s bad IoT law
California has passed an IoT security bill, awaiting the governor's signature/veto. It’s a typically bad bill based on a superficial understanding of cybersecurity/hacking that will do little improve security, while doing a lot to impose costs and harm innovation.It’s based on the misconception of adding security features. It’s like dieting, where people insist you should eat more kale, which does little to address the problem you are pigging out on potato chips. The key to dieting is not eating more but eating less. The same is true of cybersecurity, where the point is not to add “security features” but to remove “insecure features”. For IoT devices, that means removing listening ports and cross-site/injection issues in web management. Adding features is typical “magic pill” or “silver bullet” thinking that we spend much of our time in infosec fighting against.
We don’t want arbitrary features like firewall and anti-virus added to these products. It’ll just increase the attack surface making things worse. The one possible exception to this is “patchability”: some IoT devices can’t be patched, and that is a problem. But even here, it’s complicated. Even if IoT devices are patchable in theory there is no guarantee vendors will Continue reading
NAVEX: Precise and scalable exploit generation for dynamic web applications
NAVEX: Precise and scalable exploit generation for dynamic web applications Alhuzali et al., USENIX Security 2018
NAVEX (https://github.com/aalhuz/navex) is a very powerful tool for finding executable exploits in dynamic web applications. It combines static and dynamic analysis (to cope with dynamically generated web content) to find vulnerable points in web applications, determine whether inputs to those are appropriately sanitised, and then builds a navigation graph for the application and uses it to construct a series of HTTP requests that trigger the vulnerability.
It also works at real-world scale: NAVEX was used on 26 PHP applications with a total of 3.2M SLOC and 22.7K PHP files. It generated 204 concrete exploits across these applications in a total of 6.5 hours. While the current implementation of NAVEX targets PHP applications, the approach could be generalised to other languages and frameworks.
In this paper, our main contribution is a precise approach for vulnerability analysis of multi-tier web applications with dynamic features… our approach combines dynamic analysis of web applications with static analysis to automatically identify vulnerabilities and generate concrete exploits as proof of those vulnerabilities.
Here’s a example of what NAVEX can do. From the 64K Continue reading
Website Security Myths


Some conversations are easy; some are difficult. Some are harmonious and some are laborious. But when it comes to website security, the conversation is confusing.
Every organisation agrees, in theory, that their websites need to be secure. But in practice, there is resistance to investing enough time and budget. Reasons for neglecting security include misconceptions surrounding Web Application security.
Below I’ve outlined some of the most common myths and misconceptions that can often put your website at serious security risks.
My website is not the target of an attack because it is small and I run a small business.
An average small business website is attacked 44 times per day. In addition, a low profile website is a nice playground for hackers to try out new tools and techniques. Hackers often use automated tools to find various vulnerable websites and don't discriminate when it comes to the size of the target. Any web application, even if it is not itself a target, may be of interest to attackers. Web applications with lax security are easy pickings for hackers and can be subject to a mass or targeted cyber attack.
The good news is that Continue reading
We Need a Common Language for the Internet of Things

When someone tells me they have bought smart light bulbs, an Internet-connected pet cam, or any other Internet of Things (IoT) device, I always get an unsettled feeling in the pit of my stomach. They’re so excited about the affordances or their new IoT devices and apps, but I am skeptical about the privacy and security vulnerabilities. How do I have a conversation about these concerns without coming across as hyper paranoid? Perhaps the answer is that we aren’t quite ready to discuss these issues on a societal level.
Privacy and security advocates all over the world have been talking about the threats that IoT may pose to society – unless standards and regulations are put in place to help mitigate some of these risks. They champion that privacy and security should be built into design and should not come as an afterthought.
While I praise the work that advocates are doing, IoT devices are on the shelves right now and we need to be able to have conversations with everyday folk about what privacy and security risks look like in the digital economy. However, how can we have these conversations when we haven’t yet established understandable and common terms Continue reading
ETSI Releases Security Encryption Specs for 5G and IoT Uses
 The specifications are for attribute-based encryption that describes how to secure personal data, combining access control with data encryption.
The specifications are for attribute-based encryption that describes how to secure personal data, combining access control with data encryption.
PureSec Releases ‘Free’ Basic AWS Lambda Serverless Security
 The serverless security library targets the runtime environment but is not a replacement for an enterprise-grade platform deployment.
The serverless security library targets the runtime environment but is not a replacement for an enterprise-grade platform deployment.