How Cloudflare protects customers from cache poisoning
A few days ago, Cloudflare — along with the rest of the world — learned of a "practical" cache poisoning attack. In this post I’ll walk through the attack and explain how Cloudflare mitigated it for our customers. While any web cache is vulnerable to this attack, Cloudflare is uniquely able to take proactive steps to defend millions of customers.
In addition to the steps we’ve taken, we strongly recommend that customers update their origin web servers to mitigate vulnerabilities. Some popular vendors have applied patches that can be installed right away, including Drupal, Symfony, and Zend.
How a shared web cache works
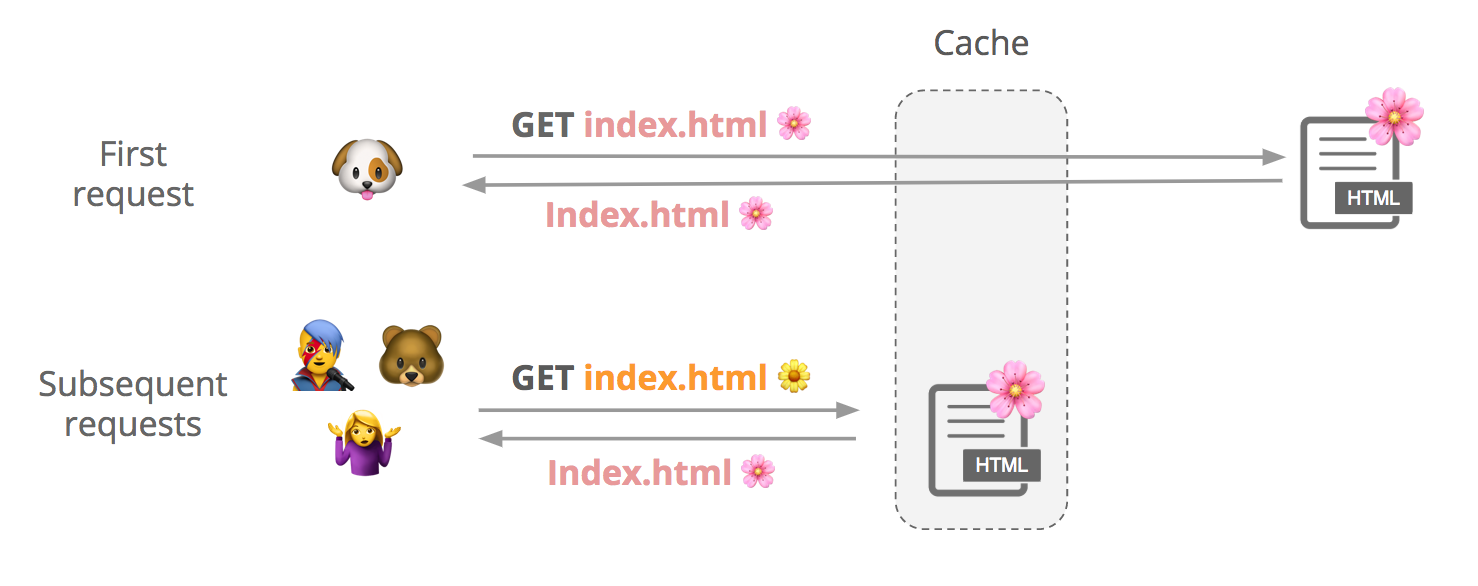
Say a user requests a cacheable file, index.html. We first check if it’s in cache, and if it’s not not, we fetch it from the origin and store it. Subsequent users can request that file from our cache until it expires or gets evicted.
Although contents of a response can vary slightly between requests, customers may want to cache a single version of the file to improve performance:
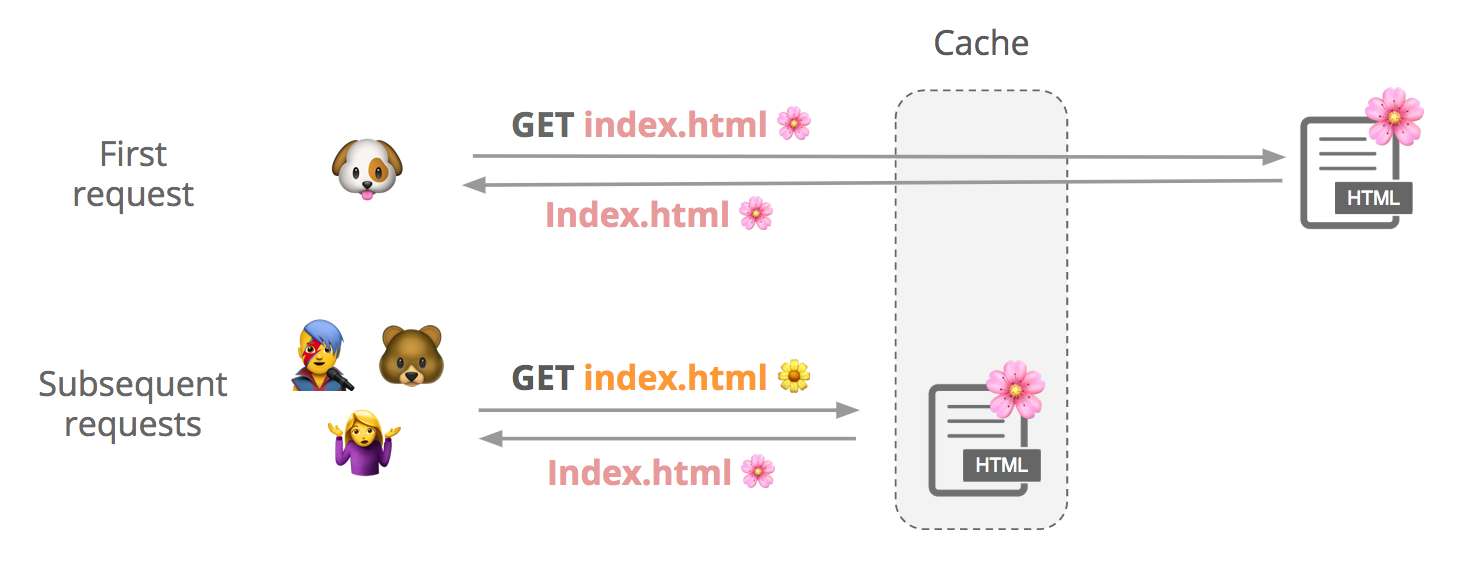
(See this support page for more info about how to cache HTML with Cloudflare.)
How do we know it’s the same file? We create something Continue reading
Security in the New World of Containers and Serverless
 This eBrief from SDxCentral takes a look at some of the security issues facing serverless and containers and delves into some of the tools and methodologies available to overcome these challenges.
This eBrief from SDxCentral takes a look at some of the security issues facing serverless and containers and delves into some of the tools and methodologies available to overcome these challenges.
VMware Cloud on AWS: Advanced Networking and Security with NSX-T SDDC
Announced in AWS Summit in New York last month and also briefly mentioned on the prior blog, Announcing General Availability of VMware NSX-T Data Center 2.2.0, NSX-T networking and security is now available in Preview Mode for new SDDC deployments on VMware Cloud on AWS. Please reach out to your sales/SE contact for more information. In this blog post, I give an overview of the advanced networking and security functionality provided by NSX-T within VMware Cloud on AWS. Continue reading
Classic Rock and Cloud-Native Attacks Collide at Black Hat
 Leading cloud access security broker (CASB) vendors McAfee and Bitglass talk security and cloud-native attacks at Black Hat.
Leading cloud access security broker (CASB) vendors McAfee and Bitglass talk security and cloud-native attacks at Black Hat.
Alibaba Cloud Eyes Expansion Into Southeast Asia With New Products, Partners
 At the Alibaba Cloud Summit this week, the cloud provider launched a wide breadth of products that span serverless, data, search and analytics, IoT, and machine learning.
At the Alibaba Cloud Summit this week, the cloud provider launched a wide breadth of products that span serverless, data, search and analytics, IoT, and machine learning.
Cisco’s Security Business, Service Provider Wins Propel Fiscal 4Q Results
 The company’s service provider business was up 6 percent year over year. But 5G isn’t the reason for the turnaround.
The company’s service provider business was up 6 percent year over year. But 5G isn’t the reason for the turnaround.
IoT Attacks Doubled in Two Months, Check Point Says
 While IoT malware made its top-three debut in July, cryptomining malware remained the top two offenders, according to the monthly report.
While IoT malware made its top-three debut in July, cryptomining malware remained the top two offenders, according to the monthly report.
Three new ways teams are using Cloudflare Access
Since leaving beta three weeks ago, Cloudflare Access has become our fastest-growing subscription service. Every day, more teams are using Access to leave their VPN behind and connect to applications quickly and securely from anywhere in the world.
We’ve heard from a number of teams about how they’re using Access. Each team has unique needs to consider as they move away from a VPN and to a zero trust model. In a zero trust framework, each request has to prove that a given application should trust its attempt to reach a secure tool. In this post, we’re highlighting some of the solutions that groups are using to transition to Cloudflare Access.
Solution 1: Collaborate with External Partners
Cloudflare Access integrates with popular identity providers (IdPs) so that your team can reach internal applications without adding more credentials. However, teams rarely work in isolation. They frequently rely on external partners who also need to reach shared tools.
How to grant and manage permissions with external partners poses a security risk. Just because you are working with a third-party doesn’t mean they should have credentials to your IdP. They typically need access to a handful of tools, not all of your internal Continue reading
Dell Technologies, Others Invest $33M in Twistlock Series C
 The container-focused vendor has now hauled in more than $63 million in funding.
The container-focused vendor has now hauled in more than $63 million in funding.
Intel Discloses New Sprectre-Like Bugs Called Foreshadow
 The flaws could allow hackers to access data that is supposed to be secured in protected areas on Intel’s Core chips or in the cloud. AMD says it's immune.
The flaws could allow hackers to access data that is supposed to be secured in protected areas on Intel’s Core chips or in the cloud. AMD says it's immune.
Obfuscated gradients give a false sense of security: circumventing defenses to adversarial examples
Obfuscated gradients give a false sense of security: circumventing defenses to adversarial examples Athalye et al., ICML’18
There has been a lot of back and forth in the research community on adversarial attacks and defences in machine learning. Today’s paper examines a number of recently proposed defences and shows that most of them rely on forms of gradient masking. The authors develop attack techniques to overcome such defences, and 9 analyse defences from ICLR 2018 claiming to protect against white-box attacks. 7 of these turn out to rely on obfuscated gradients, and 6 of these fall to the new attacks (and the other one partially succumbs). Athalye et al. won a best paper award at ICML’18 for this work.
One of the great things about work on adversarial attacks and defences, as we’ve looked at before, is that they illuminate the strengths and weaknesses of current technology. Depending on the threat model you choose, for my own part I’m currently of the opinion that we’re unlikely to find a robust adversarial defence without a more radical re-think of how we’re doing image classification. If we’re talking about the task of ‘find an image that doesn’t fool a human, but Continue reading
IBM Hackers, Cloud Security Alliance Take On IoT at Black Hat
 Armis surveyed security professionals at Black Hat and found 93 percent expect nation-states will target or exploit connected devices in the next year. So it really feels like an understatement to say IoT security was a hot topic at the event.
Armis surveyed security professionals at Black Hat and found 93 percent expect nation-states will target or exploit connected devices in the next year. So it really feels like an understatement to say IoT security was a hot topic at the event.
Exabeam Scores $50M From Lightspeed, Cisco, Security Investor Shlomo Kramer
 “We are on track to overtake Splunk and be the next SIEM market leader,” says CEO Nir Polak.
“We are on track to overtake Splunk and be the next SIEM market leader,” says CEO Nir Polak.
Cisco Execs: Cryptomining, Election Security Threats Loom Large
 When asked to rank U.S. election security preparedness, Cisco’s director of threat management and incident response said “little to none.”
When asked to rank U.S. election security preparedness, Cisco’s director of threat management and incident response said “little to none.”
Research: Are We There Yet? RPKI Deployment Considered
The Resource Public Key Infrastructure (RPKI) system is designed to prevent hijacking of routes at their origin AS. If you don’t know how this system works (and it is likely you don’t, because there are only a few deployments in the world), you can review the way the system works by reading through this post here on rule11.tech.
The paper under review today examines how widely Route Origin Validation (ROV) based on the RPKI system has been deployed. The authors began by determining which Autonomous Systems (AS’) are definitely not deploying route origin validation. They did this by comparing the routes in the global RPKI database, which is synchronized among all the AS’ deploying the RPKI, to the routes in the global Default Free Zone (DFZ), as seen from 44 different route servers located throughout the world. In comparing these two, they found a set of routes which the RPKI system indicated should be originated from one AS, but were actually being originated from another AS in the default free zone.
TLS 1.3 – Internet Security Gets a Boost
Today marks the formal publication of an overhaul of the Transport Layer Security (TLS) protocol. TLS is an Internet standard used to prevent eavesdropping, tampering, and message forgery for various Internet applications. It is probably the most widely deployed network security standard in the world. Often indicated by the small green padlock in a web browser’s address bar1, TLS is used in financial transactions, by medical institutions, and to ensure secure connections in a wide variety of other applications.
We believe the new version of this protocol, TLS 1.3, published as RFC 8446, is a significant step forward towards an Internet that is safer and more trusted.
Under development for the past four years and approved by the Internet Engineering Task Force (IETF) in March 2018, TLS 1.3 addresses known issues with the previous versions and improves security and performance, in particular it is able to establish a session more quickly than its predecessors. Because it is more efficient, TLS 1.3 promises better performance for the billions of users and organizations that use TLS every day. As with every IETF standard, TLS 1.3 was developed through open processes and participation, and included contributions from scores of individuals.
A Detailed Look at RFC 8446 (a.k.a. TLS 1.3)
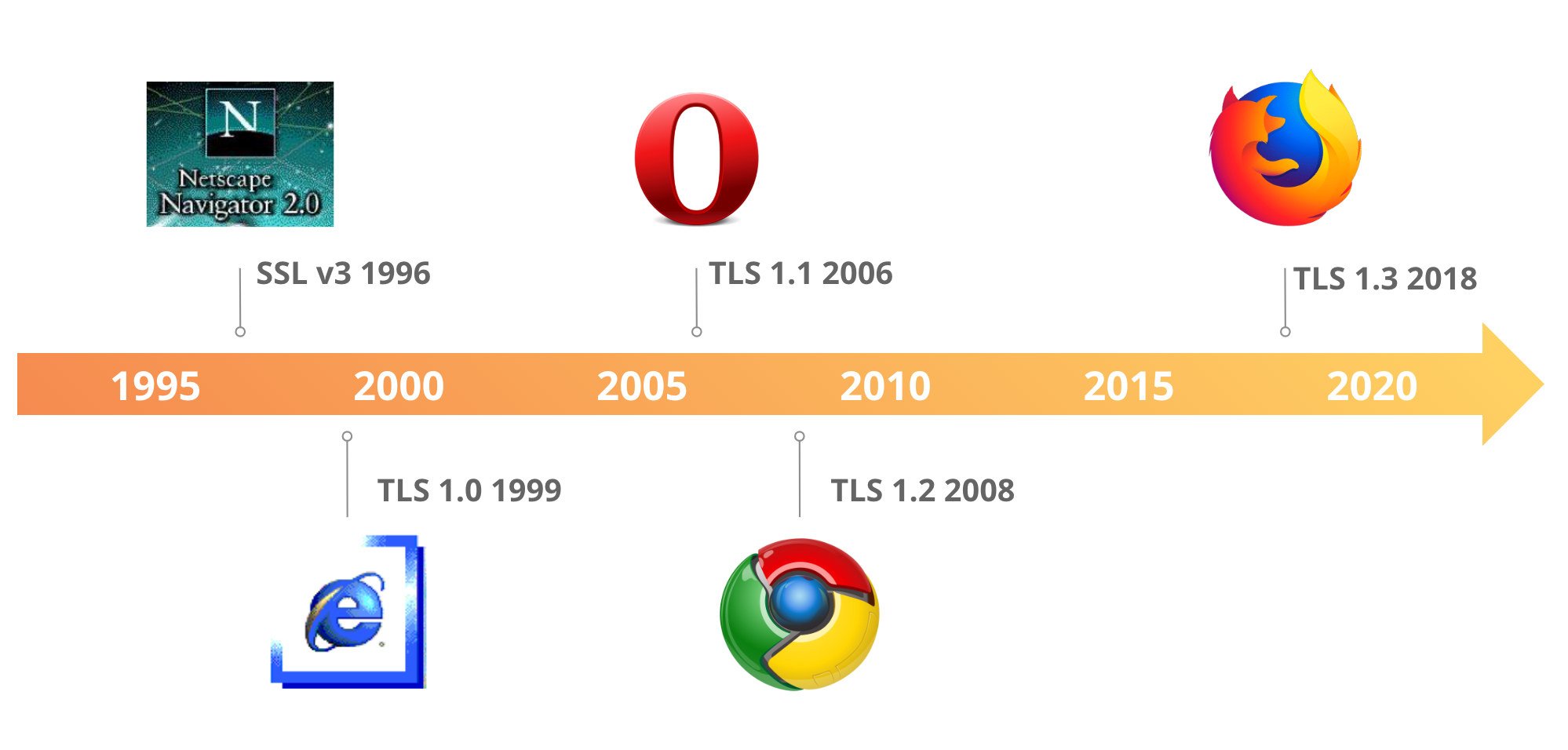
For the last five years, the Internet Engineering Task Force (IETF), the standards body that defines internet protocols, has been working on standardizing the latest version of one of its most important security protocols: Transport Layer Security (TLS). TLS is used to secure the web (and much more!), providing encryption and ensuring the authenticity of every HTTPS website and API. The latest version of TLS, TLS 1.3 (RFC 8446) was published today. It is the first major overhaul of the protocol, bringing significant security and performance improvements. This article provides a deep dive into the changes introduced in TLS 1.3 and its impact on the future of internet security.
An evolution
One major way Cloudflare provides security is by supporting HTTPS for websites and web services such as APIs. With HTTPS (the “S” stands for secure) the communication between your browser and the server travels over an encrypted and authenticated channel. Serving your content over HTTPS instead of HTTP provides confidence to the visitor that the content they see is presented by the legitimate content owner and that the communication is safe from eavesdropping. This is a big deal in a world where online privacy Continue reading
H3C Among Top Data Center Ethernet Switch Vendors, Says IHS Markit
 Respondents to IHS Markit’s survey indicated they expect a 1.5x increase in the average number of physical servers in their data centers by 2019.
Respondents to IHS Markit’s survey indicated they expect a 1.5x increase in the average number of physical servers in their data centers by 2019.
Alphabet’s Chronicle Exec Talks IoT Security
 The security company that spun out of Alphabet’s secretive X research lab in January still hasn’t set a release date for its analytics platform.
The security company that spun out of Alphabet’s secretive X research lab in January still hasn’t set a release date for its analytics platform.