You Are Paying The Clouds To Build Better AI Than They Will Rent You
Think of it as the ultimate offload model.
One of the geniuses of the cloud – perhaps the central genius – is that a big company that would have a large IT budget, perhaps on the order of hundreds of millions of dollars per year, and that has a certain amount of expertise creates a much, much larger IT organization with billions of dollars – and with AI now tens of billions of dollars – in investments and rents out the vast majority of that capacity to third parties, who essentially allow that original cloud builder to get their own IT operations for close to free. …
You Are Paying The Clouds To Build Better AI Than They Will Rent You was written by Timothy Prickett Morgan at The Next Platform.
HS088: Combating Analysis Paralysis
Analysis paralysis is a huge problem in IT – we “study” and “evaluate” and “keep on our radar” but then all too often have a choice and a need to act thrust upon us, and need to switch modes fast. How do we try to get more mileage out of the studying to get leverage... Read more »Joining ISE to Active Directory
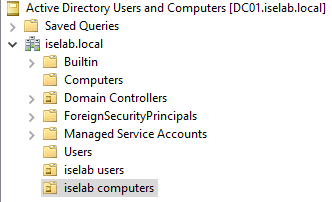
Most ISE deployments use a join to Active Directory to be able to query AD groups, perform user lookups, etc. In this post, I’ll join my ISE lab server to AD. First I’m going to create two OUs in my AD, one for users and one for computers. Why not use the default ones? They are containers, not OUs, which means you can’t apply GPOs to them. Additionally, it makes for cleaner separation from the built-in accounts and allows for applying policies that won’t affect them. I’m creating two OUs:
- iselab users.
- iselab computers.
This is done by going to Active Directory Users and Computers, then right clicking the AD domain and selecting New -> Organizational Unit:
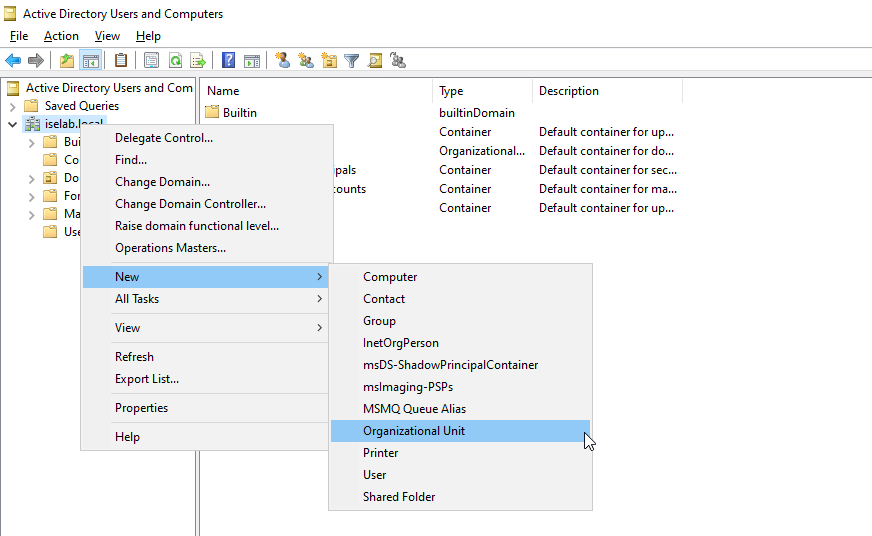
Give the OU a name and then click OK:
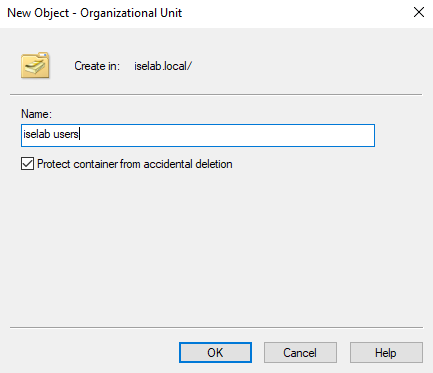
Repeat for the computers OU. You should now be able to see the OUs:
I’m going to create a user named Bob that I’ll be using to test login later. Right click the users OU and then select New -> User:
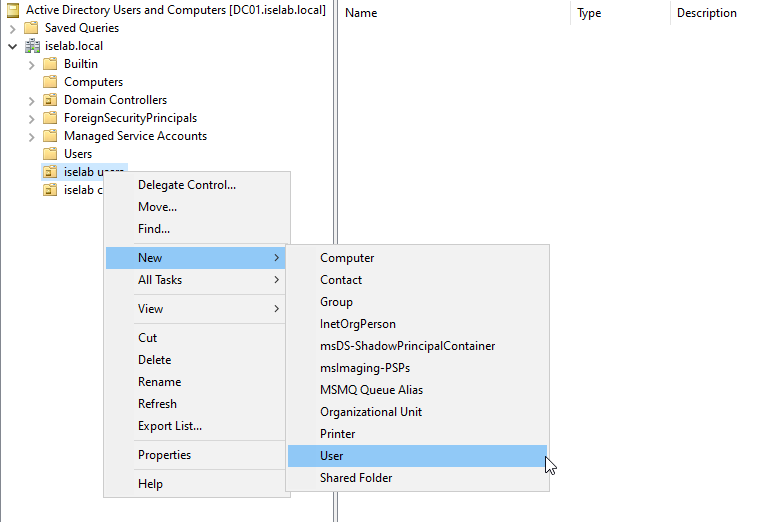
Enter the name and logon name:
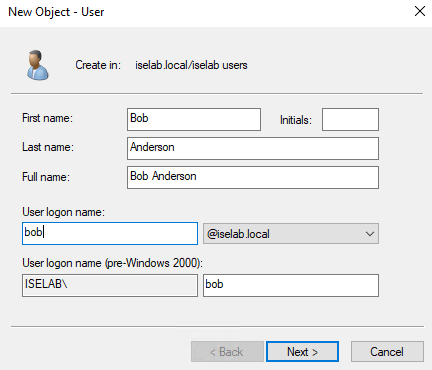
Click Next. Enter a password for the user. As this is a lab, I won’t require that the user changes the password and the Continue reading
Running Routing Protocols over Tunnels
James got confused by a statement made by Hannes Gredler in his IS-IS book:
Things behave really badly if the total IGP cost over the tunnel undermines the total topologies’ cost. What happens next is that the tunnel “wraps” around itself, ultimately causing a meltdown of the entire network.
Let’s unpack that, starting with “Why would you need a tunnel?”
NB502: AWS Revenue Growth Lags Cloud Competitors; Microsoft Entra ID Forces MFA
Take a Network Break! This week we discuss Google adding traffic shaping to its cross-cloud interconnect, Aviatrix bringing hybrid cloud transit to its cloud networking service, and Microsoft forcing MFA for Entra ID customers. Microsoft CEO Satya Nadella forgoes $5 million in incentive pay for Microsoft security lapses, Extreme Networks adds new features to its... Read more »netlab 1.9.2: STP, LAG, Cisco IOL, Edgeshark
While I was busy fixing bugs in the netlab release 1.9.2, other contributors added exciting new features:
- Jeroen van Bemmel added the spanning tree and link aggregation configuration modules, initially implemented on Arista EOS, Cumulus Linux, and FRR.
- Dan Partelly added the netlab exec command that can execute the same command on a set of network devices, support for Edgeshark, and support for Cisco IOS on Linux (IOL) and Cisco IOS layer-2 image on Linux (IOLL2), the latter after a heroic uphill battle with ancient software (part 1, part 2).
Other new features include:
From Python To Go 001. Get Started.
Dear friend,
As mentioned in previous blogpost, I’ve kicked the new series of blog posts related to Go (Golang programming language) and how to pick that up. Originally my idea was just to explain some concepts, pretty much I’ve done back in past with Code eXpress (CEX) for Python. But then I’ve thought through it further and decided to write a side-by-side guide with Python and Go together, exactly as I’ve done before with multi vendor network automation, when started writing about Nokia SR OS and Cisco IOS XR back in 2016.
Do I Need Both Python And Go?
In our opinion, yes, you do need both. Each of these programming languages shines in some areas more than another. And both of them are applicable to network and infrastructure automation. As such, we recommend to study both, but to start with Python as it is easier and at this stage is wider used than Go. So we encourage you to start with our Network Automation Trainings:
We offer the following training programs in network automation for you:
HN756: Alkira Enhances Its Multi-Cloud Networking With ZTNA and Security (Sponsored)
Alkira provides a Multi-Cloud Networking Service (MCNS) that lets you connect public cloud and on-prem locations using a cloud-delivered, as-a-service approach. But Alkira offers more than just multi-cloud connectivity. On today’s sponsored episode of Heavy Networking, we dig into Alkira’s full set of offerings, which include networking, visibility, governance, and security controls such as firewalls... Read more »TNO007: Good Foundations Are Key To Leveraging AI for Network Operations
In this episode of Total Network Operations the conversation focuses on the impact and implementation of AI on network operations. Host Scott Robohn is joined by guest Michael Wynston to discuss the foundational requirements for AI implementation, such as well-documented processes, version control, and lab testing. Michael also talks about the need for lifelong learning... Read more »Hedge 249: FR Routing Update
Alistair Woodman joins Tom and Russ to talk about the current state of the FR Routing open source routing stack project. Like all software projects, FR Routing has entered a bit of a “middle phase,” with a focus on maintenance and stability rather than new features and protocols.
download
Wake on LAN: Linux, Windows and Routers
Wake-on-LAN (WoL) is a feature that lets you turn on computers remotely. This can be […]
The post Wake on LAN: Linux, Windows and Routers first appeared on Brezular's Blog.
Intel Takes The Big Restructuring Hits As It Looks Ahead
It is beginning to look like chip maker Intel hit the bottom in its products and foundry businesses in the second quarter of this year and that revenues are slowly – we won’t go so far as to say surely – improving. …
Intel Takes The Big Restructuring Hits As It Looks Ahead was written by Timothy Prickett Morgan at The Next Platform.
IPB163: Know Your Options: DHCP vs. DHCPv6
If you’re going to use DHCPv6, you have options, but there are some things you need to know in order to be able to build out your DHCPv6 configuration properly. Today’s IPv6 Buzz explores similarities and differences between DHCP and DHCPv6, particularly the operational model. And as always, you’ll want to verify and test before... Read more »Worth Reading: Creating a Tech Blog
Would you like to start a tech blog but don’t know how to do it? Ethan Banks put together a phenomenal how-to guide in his Developing Content & Gathering Research For Your Tech Blog article.
Oh, and please use Hugo (or similar) and use walled gardens like LinkedIn solely to post summaries and links to your content. You want to be in control and retain ownership of your work, right?
N4N001: Frames and Packets: What’s the Difference?
Frames and packets: how are they different and why is it important to know those differences? On this first episode of N Is For Networking, join co-hosts Holly Metlitzky and Ethan Banks to learn the fundamentals about frames and packets, plus some bonus material on layers and addresses. N Is For Networking is the newest... Read more »Moving Baselime from AWS to Cloudflare: simpler architecture, improved performance, over 80% lower cloud costs
When Baselime joined Cloudflare in April 2024, our architecture had evolved to hundreds of AWS Lambda functions, dozens of databases, and just as many queues. We were drowning in complexity and our cloud costs were growing fast. We are now building Baselime and Workers Observability on Cloudflare and will save over 80% on our cloud compute bill. The estimated potential Cloudflare costs are for Baselime, which remains a stand-alone offering, and the estimate is based on the Workers Paid plan. Not only did we achieve huge cost savings, we also simplified our architecture and improved overall latency, scalability, and reliability.
Cost (daily) | Before (AWS) | After (Cloudflare) |
Compute | $650 - AWS Lambda | $25 - Cloudflare Workers |
CDN | $140 - Cloudfront | $0 - Free |
Data Stream + Analytics database | $1,150 - Kinesis Data Stream + EC2 | $300 - Workers Analytics Engine |
Total (daily) | $1,940 | $325 |
Total (annual) | $708,100 | $118,625 (83% cost reduction) |
Table 1: AWS vs. Workers Costs Comparison ($USD)
When we joined Cloudflare, we immediately saw a surge in usage, and within the first week following the announcement, we were processing over a billion events daily and our weekly active users tripled.
As the platform grew, so did the challenges Continue reading
Workers Builds: integrated CI/CD built on the Workers platform
During 2024’s Birthday Week, we launched Workers Builds in open beta — an integrated Continuous Integration and Delivery (CI/CD) workflow you can use to build and deploy everything from full-stack applications built with the most popular frameworks to simple static websites onto the Workers platform. With Workers Builds, you can connect a GitHub or GitLab repository to a Worker, and Cloudflare will automatically build and deploy your changes each time you push a commit.
Workers Builds is intended to bridge the gap between the developer experiences for Workers and Pages, the latter of which launched with an integrated CI/CD system in 2020. As we continue to merge the experiences of Pages and Workers, we wanted to bring one of the best features of Pages to Workers: the ability to tie deployments to existing development workflows in GitHub and GitLab with minimal developer overhead.
In this post, we’re going to share how we built the Workers Builds system on Cloudflare’s Developer Platform, using Workers, Durable Objects, Hyperdrive, Workers Logs, and Smart Placement.
The core problem for Workers Builds is how to pick up a commit from GitHub or GitLab and start a Continue reading
High Quality Data Is Key For Effective AI Agents
COMMISSIONED As enterprises increasingly adopt GenAI-powered AI agents, making high-quality data available for these software assistants will come into sharper focus. …
High Quality Data Is Key For Effective AI Agents was written by Timothy Prickett Morgan at The Next Platform.
