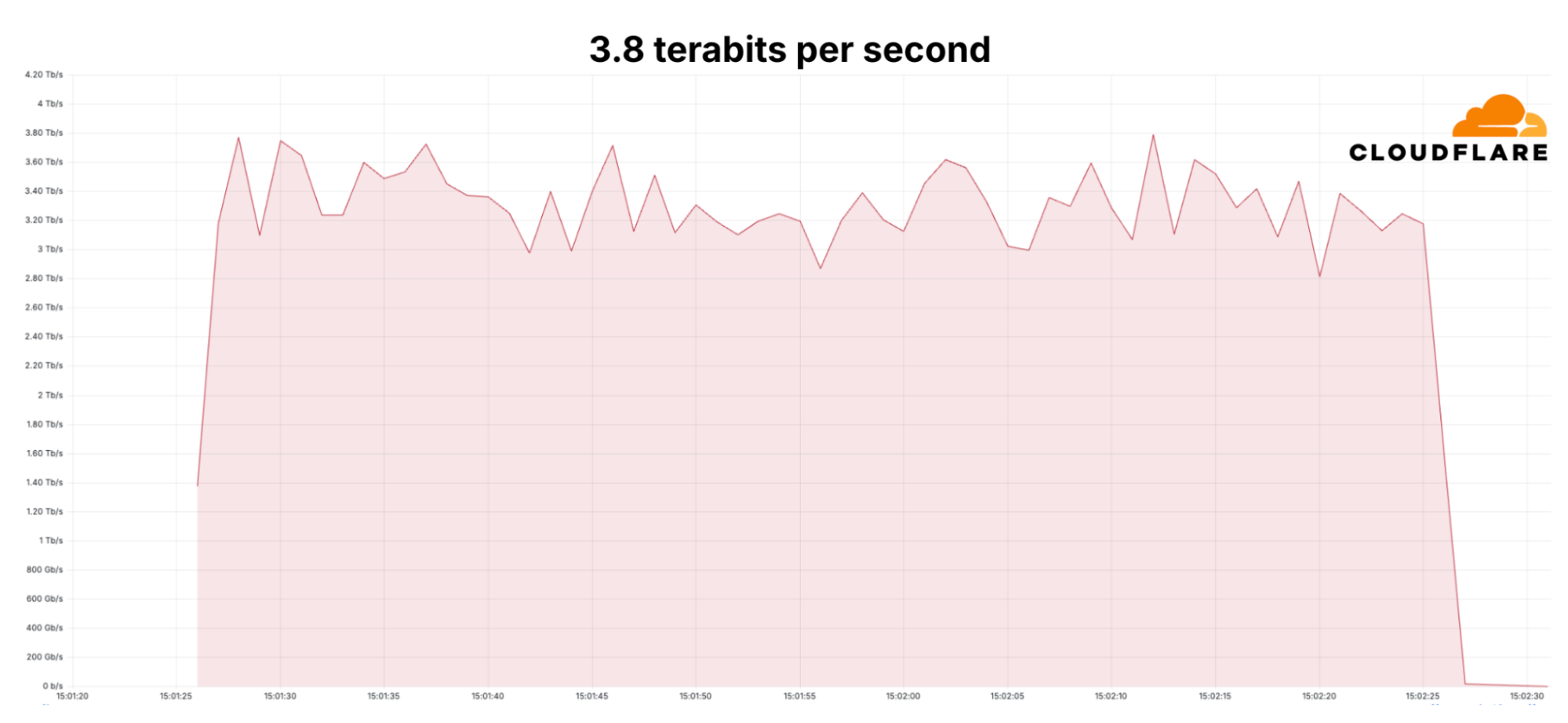
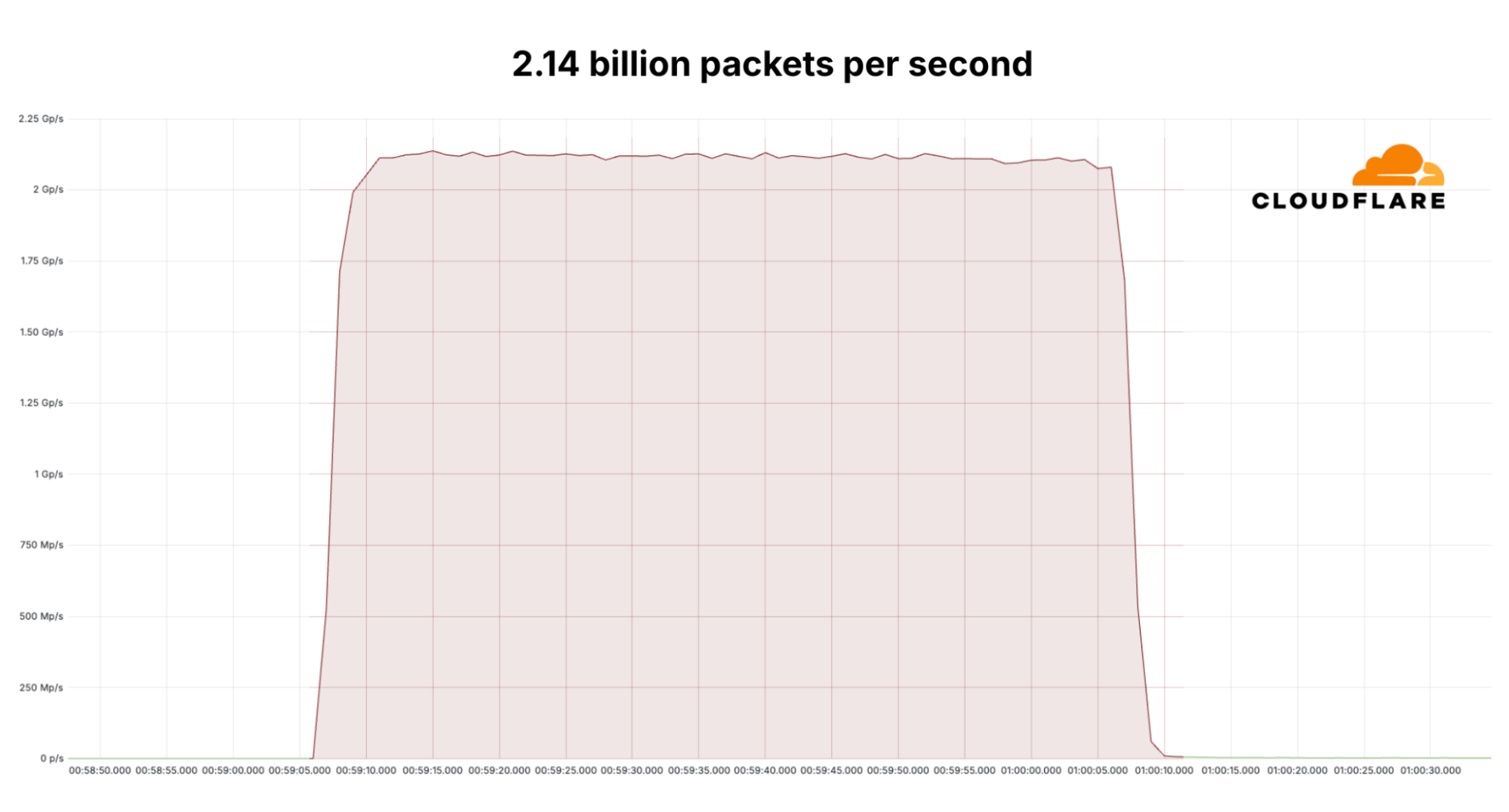
Technology Short Take 183
Welcome to Technology Short Take #183! Fall is in the air; the nights and mornings are cooler and the leaves are turning (or have already turned in some areas!). I’ve got a slightly smaller collection of links for you this time around, but I do hope that you’ll find something shared here useful. Enjoy!
Networking
- Network World provides some coverage of the recent 2024 eBPF Summit, discussing why eBPF is critical and how it’s getting better.
- I first learned of Kmesh via this article by Jimmy Song. There’s no doubt eBPF is impacting lots of different areas of networking; this is just one more example.
- ARM-based architectures continue to see expanded usage in lots of different areas; here’s just one more example.
Security
- This article is a fascinating look into a series of misconfigurations and security flaws that culminates with full cluster admin privileges and access to internal software repositories. Wow! Remember, kids: outbound sidecars are not secure enforcement points.
- A group of individuals being able to accidentally become the admins of a top-level domain (TLD) underscores just how fragile many parts of the Internet are today.
- Ricky Mondello (who works on Apple’s new Passwords app) advises people Continue reading