China Mobile closing down 3G system, complete switch-off expected by 2020

While Western telcos debate, China is moving to 5G.
The post China Mobile closing down 3G system, complete switch-off expected by 2020 appeared first on EtherealMind.

While Western telcos debate, China is moving to 5G.
The post China Mobile closing down 3G system, complete switch-off expected by 2020 appeared first on EtherealMind.
The Spring 2019 Building Network Automation Solutions course continued with an awesome presentation by David Gee. He started with what you should do before writing a single line of code (identify processes and document them in workflows and sequence diagrams) and covered tons of boring stuff nobody ever wants to talk about.
On Thursday Rachel Traylor continued exploring graphs and their relevance in networking, this time focusing on trees and spanning trees.
The Network Connectivity, Graph Theory, and Reliable Network Design webinar is part of standard ipSpace.net subscription You can access David’s presentation and all other materials of the Building Network Automation Solutions online course with Expert Subscription (assuming you choose this course as part of your subscription).
Efficient synchronisation of state-based CRDTs Enes et al., arXiv’18
CRDTs are a great example of consistency as logical monotonicity. They come in two main variations:
State-based CRDTs look attractive therefore, but over time as the state grows sending the full state every time quickly becomes expensive. That’s where Delta-based CRDTs come in. These send only the delta to the state needed to reconstruct the full state.
Delta-based CRDTs… define delta-mutators that return a delta (
), typically much smaller than the full state of the replica, to be merged with the local state. The same
is also added to an outbound
buffer, to be periodically propagated to remote replicas. Delta-based CRDTs have been adopted in industry as part of the Akka Distributed Data framework and IPFS.
So far so good, but Continue reading

If you follow the IPv6 Maintenance (6man) Working Group of the Internet Engineering Task Force (IETF), you may have noticed the 300+ message email thread on an Internet Draft that was recently published on the “Reaction of Stateless Address Autoconfiguration (SLAAC) to Renumbering Events”. This was prompted by the experiences of developing Best Current Operational Practice on IPv6 prefix assignment for end-users, an activity led by ISOC’s Jan Žorž and published as ripe-690.
SLAAC is used to automatically assign an IPv6 address to a host, but there are a number of scenario where hosts may end up using stale configuration information and thereby leading to interoperability problems.
For example, a typical IPv6 deployment scenario is when a CPE (Customer Premises Equipment) router requests an IPv6 prefix to an ISP via DHCPv6-PD, and advertises a sub-prefix of the leased prefix on the LAN-side via SLAAC.
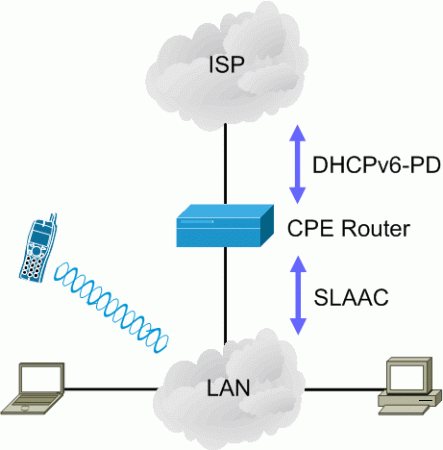
In such scenarios, if the CPE router crashes and reboots, it may lose all information about the previously leased prefix. Upon reboot, the CPE router may be leased a new prefix that will result in a new sub-prefix being advertised on the LAN-side of the CPE router. As a result, hosts will normally configure addresses for the newly-advertised prefix, Continue reading
Instana is modern, automated application performance management. How do they do this? An agent sits on a host or in a container, and performs continuous real-time discovery and monitoring of all components.
The post BiB 072: Automate Cloud Native Monitoring With Instana appeared first on Packet Pushers.

Node.js allows developers to build web services with JavaScript. However, you're on your own when it comes to registering a domain, setting up DNS, managing the server processes, and setting up builds.
There's no reason to manage all these layers on separate platforms. For a site on Cloudflare, these layers can be on a single platform. Serverless technology simplifies developers' lives and reframes our current definition of backend.
In this article I will breeze through a simple example of how converting a former Node server into a Worker untangled a part of my teams’ code base. The conversion to Workers for this example can be found at this PR on Github.
Cloudflare Marketplace hosts a variety of apps, most of which are produced by third party developers, but some are produced by Cloudflare employees.
The Spotify app is one of those apps that was written by the Cloudflare apps team. This app requires an OAuth flow with Spotify to retrieve the user’s token and gather the playlist, artists, other Spotify profile specific information. While Cloudflare manages the OAuth authentication portion, the app owner - in this case Cloudflare Apps - manages the small integration service that uses the Continue reading
Your monthly cloud bill can be shocking. On today's Day Two Cloud we talk with Iris Classon about how to optimize your cloud deployment for cost without killing performance--i.e., how to keep customers and finance happy without going insane.
The post Day Two Cloud 004: How To Optimize Cloud For Cost And Performance Without Going Insane appeared first on Packet Pushers.
 Both companies are betting big on an open, integrated platform approach. Their investments appear...
Both companies are betting big on an open, integrated platform approach. Their investments appear...

We’re celebrating International Women’s Day this year with great news: The Internet Society welcomes a new Chapter in Lesotho – and the Chapter’s president, vice president, treasurer, secretary, as well as a board member are all talented tech women.
Lesotho is a small landlocked country within South Africa, where less than a third of its population is connected to the Internet. One of the Lesotho Chapter’s key priorities this year is to start an “Internet for Education” project, which aims to encourage five schools to use the Internet to support teaching and to improve the quality of education.
Please join us in welcoming the Lesotho Chapter, then learn about its President Ithabeleng Moreke and other women around the world who are using the Internet to make a difference in their communities!

Ithabeleng Moreke enjoys the world of the Internet and all things networks, the technology behind it, and Internet security – and how they affect our everyday lives. She’s worked as network engineer for the government of Lesotho and is now with Vodacom Lesotho.

In Jazmin Fallas Kerr’s hometown, Desamparados, Costa Rica, nearly half of all families with women as head of household are in Continue reading
 SDxCentral Weekly Wrap for March 8, 2019: Huawei seeks a legal injunction. Juniper's acquisition...
SDxCentral Weekly Wrap for March 8, 2019: Huawei seeks a legal injunction. Juniper's acquisition...
 A deep dive by MTN Consulting finds that Microsoft has made great progress reorienting itself...
A deep dive by MTN Consulting finds that Microsoft has made great progress reorienting itself...
 Others have argued that 5G alone will offer the low latency, speed, and spectrum efficiency to...
Others have argued that 5G alone will offer the low latency, speed, and spectrum efficiency to...
On today's sponsored Heavy Networking, VIAVI Solutions joins the Packet Pushers to discuss the intersection of network performance management (NPM) and security. We discuss how network and security teams can leverage VIAVI's packet capture capabilities, how it enriches flow records with additional data to provide valuable context, and how the concept of end user experience informs VIAVI's approach to NPM.
The post Heavy Networking 434: Solving Network Performance And Security Problems With VIAVI Solutions (Sponsored) appeared first on Packet Pushers.