Tracing Soon-to-Expire Federal .gov Certificates with CT Monitors

As of December 22, 2018, parts of the US Government have “shut down” because of a lapse in appropriation. The shutdown has caused the furlough of employees across the government and has affected federal contracts. An unexpected side-effect of this shutdown has been the expiration of TLS certificates on some .gov websites. This side-effect has emphasized a common issue on the Internet: the usage of expired certificates and their erosion of trust.
For an entity to provide a secure website, it needs a valid TLS certificate attached to the website server. These TLS certificates have both start dates and expiry dates. Normally certificates are renewed prior to their expiration. However, if there’s no one to execute this process, then websites serve expired certificates--a poor security practice.
This means that people looking for government information or resources may encounter alarming error messages when visiting important .gov websites:
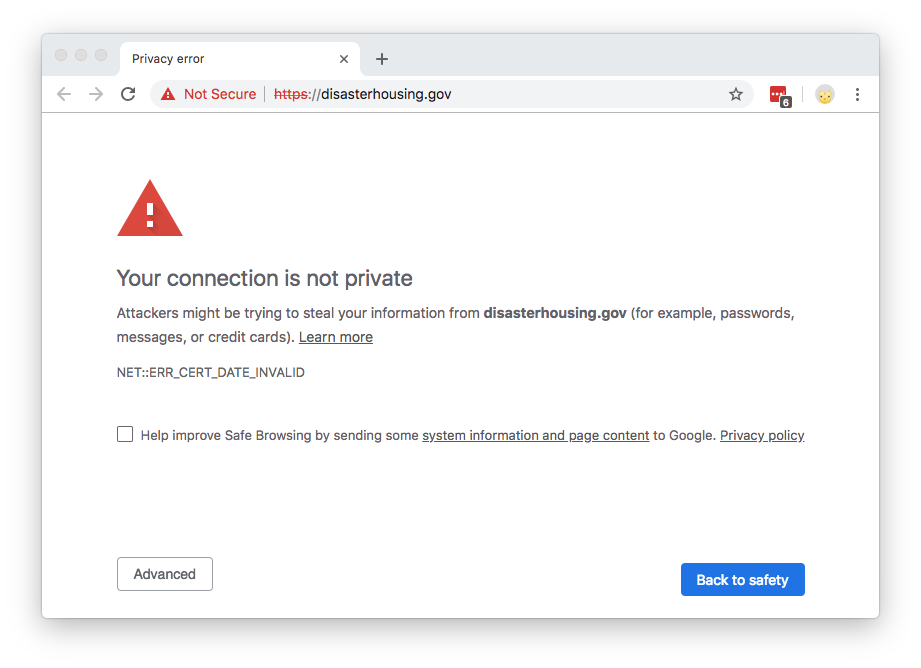
The content of the website hasn’t changed; it’s just the cryptographic exchange that’s invalid (an expired certificate can’t be validated). These expired certificates present a trust problem. Certificate errors often dissuade people from accessing a website, and imply that the site is not to be trusted. Browsers purposefully make it difficult to continue to Continue reading
 We would like to thank VIAVI Solutions for sponsoring this episode of Network Collective. VIAVI Solutions is an application and network management industry leader focusing on end-user experience by providing products that optimize performance and speed problem resolution. Helping to ensure delivery of critical applications for businesses worldwide, Viavi offers an integrated line of precision-engineered software and hardware systems for effective network monitoring and analysis. Learn more at
We would like to thank VIAVI Solutions for sponsoring this episode of Network Collective. VIAVI Solutions is an application and network management industry leader focusing on end-user experience by providing products that optimize performance and speed problem resolution. Helping to ensure delivery of critical applications for businesses worldwide, Viavi offers an integrated line of precision-engineered software and hardware systems for effective network monitoring and analysis. Learn more at  We would also like to think PathSolutions for sponsoring this episode of Network Collective. PathSolutions TotalView is designed to automatically dig deep into network devices to learn what they know about your network’s performance. This means your network is no longer full of mysteries because you know everything your network knows. Try TotalView on your network, and it will show you 5 things about your network that you didn’t previously know. You can find out
We would also like to think PathSolutions for sponsoring this episode of Network Collective. PathSolutions TotalView is designed to automatically dig deep into network devices to learn what they know about your network’s performance. This means your network is no longer full of mysteries because you know everything your network knows. Try TotalView on your network, and it will show you 5 things about your network that you didn’t previously know. You can find out  Silver Peak’s EdgeConnect SD-WAN platform is now certified by Google Cloud, Amazon Web Services, Microsoft Azure, and Oracle Cloud.
Silver Peak’s EdgeConnect SD-WAN platform is now certified by Google Cloud, Amazon Web Services, Microsoft Azure, and Oracle Cloud. The Nutanix-VMware battle escalated with a Nutanix blog accusing VMware COO Sanjay Poonen of “bullying” Nutanix customers.
The Nutanix-VMware battle escalated with a Nutanix blog accusing VMware COO Sanjay Poonen of “bullying” Nutanix customers. Canonical says the latest version of its platform for IoT and container deployments will reduce three things: time to market, software development risk, and security maintenance costs.
Canonical says the latest version of its platform for IoT and container deployments will reduce three things: time to market, software development risk, and security maintenance costs. SDxCentral is pleased to announce Dan Meyer has been promoted to editor in chief at SDxCentral. Read more in this post by CEO Matt Palmer.
SDxCentral is pleased to announce Dan Meyer has been promoted to editor in chief at SDxCentral. Read more in this post by CEO Matt Palmer.

 The German carrier signed an agreement with the Berlin Senate Department for Economics, Energy and Public Enterprises to drive 5G deployment in the capital.
The German carrier signed an agreement with the Berlin Senate Department for Economics, Energy and Public Enterprises to drive 5G deployment in the capital.