Infinera Corporate Restructuring Plan Hits 53 Jobs in California
 The initial phase of the program will cost between $6 million and $8 million and is linked to Infinera's recently closed $430 million acquisition of Coriant.
The initial phase of the program will cost between $6 million and $8 million and is linked to Infinera's recently closed $430 million acquisition of Coriant.
 The initial phase of the program will cost between $6 million and $8 million and is linked to Infinera's recently closed $430 million acquisition of Coriant.
The initial phase of the program will cost between $6 million and $8 million and is linked to Infinera's recently closed $430 million acquisition of Coriant.
 But Huawei may be getting the best kind of revenge. The company says its revenues in 2018 grew 21 percent over the previous year.
But Huawei may be getting the best kind of revenge. The company says its revenues in 2018 grew 21 percent over the previous year.

2018 has been a busy year. There’s been a lot going on in the networking world and the pace of things keeps accelerating. I’ve been inundated with things this last month, including endless requests for my 2019 predictions and where I think the market is going. Since I’m not a prediction kind of person, I wanted to take just a couple of moments to talk more about something that I did find interesting from 2018 – deadlines.
Long-time readers of this blog may remember that I’ve always had a goal set for myself of trying to get one post published every week. It’s a deadline I set for myself to make sure that I didn’t let my blog start decaying into something that is barely updated. I try to hold fast to my word and get something new out every week. Sometimes it’s simple, like reflections on one of the various Tech Field Day events that I’m working on that week. But there’s always something.
That is, until Cisco Live this year. I somehow got so wrapped up in things that I missed a post for the first time in eight years! Granted, this was Continue reading
In case you missed our announcement a couple of weeks ago, Docker Hub now has an improved user experience for finding, storing and sharing Docker container images. Our second most popular blog of 2018 gives users a preview of the new Docker Hub. Read on to learn more about what’s new on Docker Hub!
Today, we’re excited to announce that Docker Store and Docker Cloud are now part of Docker Hub, providing a single experience for finding, storing and sharing container images. This means that:

Millions of individual users and more than a hundred thousand organizations use Docker Hub, Store and Cloud for their container content needs. We’ve designed this Docker Hub update to bring together the features that users of each product know and love the most, while addressing known Docker Hub requests around ease of use, repository and team management.
Repositories

 It took Michael Dell 12 months of battling shareholders — and ultimately paying them about $14 billion — to once again take his company public.
It took Michael Dell 12 months of battling shareholders — and ultimately paying them about $14 billion — to once again take his company public.
 ZTE's year included claims of espionage, direct intervention from President Donald Trump, a growing list of countries banning use of its equipment, and a $1 billion hit to its bottom line.
ZTE's year included claims of espionage, direct intervention from President Donald Trump, a growing list of countries banning use of its equipment, and a $1 billion hit to its bottom line.
Workload placement once required best guesses, but automated workload analysis is changing the game

Pink Dot SG is an event which takes place every June in Singapore to celebrate LGBTQIA+ pride! Cloudflare participated this year, on June 21st. We’re a little late, but wanted to share what we got up to. Pink Dot SG started in 2009, as a way for queer people and allies alike to demonstrate their belief that everyone deserves the “freedom to love.”
Proudflare, Cloudflare's LGBTQIA+ employee resource group, finds ways to support and provide resources for the LGBTQIA+ community, both within Cloudflare and in the larger community.
Proudflare started in 2017 in our San Francisco headquarters and in 2018, the Proudflare Singapore chapter was formed. We were excited to participate in our first public-facing event and demonstrate Cloudflare’s commitment to equality and dignity for all people!
We took to the streets this year to celebrate, but more importantly demand equality for our community in Singapore. It was an exciting event, with heaps of buzz, cheer, and joy amongst the crowd! Pink Dot SG included LGBTQIA+-themed events, information tents, a concert, and onstage were 10 Declarations for Equality, a list of changes the LGBTQIA+ community and their allies are ready for and Continue reading
As the cloud has become a ubiquitous part of business life over the last few years, there are still lingering concerns and misconceptions around cloud security.
 Can it get much worse than having its CFO arrested and being accused of violating sanctions?
Can it get much worse than having its CFO arrested and being accused of violating sanctions?
 When Air Bud’s legacy storage system gave out, leaving the film company with no way to backup or restore files, “it was panic,” said Technical Director Tyson Clark.
When Air Bud’s legacy storage system gave out, leaving the film company with no way to backup or restore files, “it was panic,” said Technical Director Tyson Clark.
 Industry trade group 5G Americas predicts that there will be 336,000 5G connections in North Americas by the end of 2019. That will account for 47 percent of global 5G connections.
Industry trade group 5G Americas predicts that there will be 336,000 5G connections in North Americas by the end of 2019. That will account for 47 percent of global 5G connections.
All this week, we have been bringing you the top 5 blog posts of 2018. Now for #3 on top 5 list – our blog post on Play with Kubernetes. Following the success of Play with Docker, earlier this year, we gave you the ability to learn Kubernetes from the convenience of our training site. Continue reading to learn more…
Every month for the last year, thousands of people have used Play with Docker and the accompanying hands-on Play with Docker Classroom training site. These sites allow you to use and learn Docker entirely within your own browser, without installing anything. Last summer, we quietly launched the companion site Play with Kubernetes, to give people a full command line while learning Kubernetes on the command line. And today we’re launching a new Kubernetes training site, the Play with Kubernetes Classroom.
The Play with Kubernetes Classroom is a workshop environment just like the Play with Docker Classroom. We currently have an extensive Kubernetes workshop originally based on Jérôme Petazzoni’s Container Training Kubernetes workshop. But instead of doing it all locally or setting up VMs in the cloud, you can now run through the workshop entirely in the browser.
In our final Datanauts episode for this year, we review how the show did over 2018, talk a little about how the show comes together, and finish with our 2019 predictions done Mad Libs-style.
The post Datanauts 155: The Mad Libs Prediction Show appeared first on Packet Pushers.

My name is Gustavo Babo, I’m from Brazil and I’m a Law and Political Science student. One of my biggest interests is to understand the best way to create national and international policies related to the Internet and other technologies such as Artificial Intelligence, IoT, and Blockchain. Having participated in the IGF as a 2018 Youth@IGF Fellow has enhanced my perspective on the future of all these technologies. Enjoy my opinion!
Throughout the IGF event, in all the panels I have attended, I have noticed one thing in common: the feeling that the human being has had less-and-less control over technology and its implications. The unpredictable factor for the future of some emerging technologies that have developed very rapidly is a situation that divided the event into two perspectives: some of those present believe that technology will bring to the world many positive situations and we need to collaborate with its acceleration to any cost. However, there are others who fear the speed and lack of control of the impacts of these technologies – which are really transforming the world – believing also that the human being may be tracing a disastrous path for itself, since we no longer control Continue reading
I was asked the other day what my New Year’s Resolutions for 2019 were. The truth is I don’t actually have any. I haven’t, in my life, been the best at “using New Year’s Resolutions” in the “healthiest of ways“. What do I mean by that? Well for example, one... Read More ›
The post 2019: Taking One Day at a Time appeared first on Networking with FISH.
 Open source and containers found themselves at the center of M&A activity this year.
Open source and containers found themselves at the center of M&A activity this year.
A security team with a broader view of issues can provide better plans and solutions to problems and the ability to react effectively and quickly in a security emergency.
Recent releases of Firefox have introduced the concept of DNS privacy under the name “Trusted Recursive Resolver”. Although Firefox ships with DNS-over-HTTPS (DoH) disabled by default, there has been some discussion within the Mozilla developer community about changing the default to “enabled”.
Although DoH is somewhat controversial because it moves control plane (signalling) messages to the data plane (data forwarding), and can thereby bypass local network policies, DoH advocates argue that it makes it harder to block or monitor DNS queries which is a commonly used method for restricting access to the Internet and/or monitoring user behaviour.
But putting these arguments aside, if you want to try out DoH then the DNS privacy (or “TRR” in Firefox speak) configuration in Firefox can be accessed as follows:
A sample output of DNS privacy configuration in Mozilla Firefox is as follows:
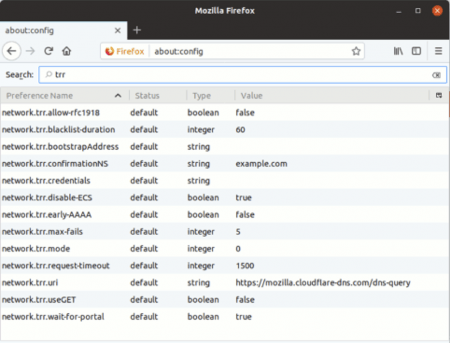
Firefox offers its technical users quite a few settings to play with, but the most important options (along with their recommended settings) for TRR are:
“network.trr.bootstrapAddress” specifies the IP address of a recursive resolver that should Continue reading