My Ignorance for a Year and Dell IDRAC
Hi,
I have a Dell R810 and it makes a lot of noise. So, I have put it somewhere remote in the home where it’s completely inhabitable for human beings. Now, the problem was always to go there and manually power-up the system. This has been the scenario for years. So, technically if am away from my home I need to take help from my wife. All this is going well and I was always wondered should it not have a better way to do things.
Was talking to my friend and he had some paid solution for the same thing, he doesn’t even remember and that’s for his cisco gear, now for Cisco gear as long you supply power they will be powered (if the Power button is always on), for servers however just like our Personal CPU’s and Laptops you have to manually press the power button.
Then yesterday all of a sudden I took this somewhat seriously and explored options, then I understood it was sitting right inside the server, Dell has something called Integrated DRAC system which helps you do this thing, all you need to have is a proper Lan connection, the message was Continue reading
Weekly Show 422: Hardware Supply Chains And Trusted Execution
Today's show dives into issues around IT supply chain security and mechanisms such as trusted execution. We examine how they work and how they're implemented, and look at similar measures in routing and switching.
The post Weekly Show 422: Hardware Supply Chains And Trusted Execution appeared first on Packet Pushers.
Serverless and Knative Underline Cloud Native Evolution
 Knative is seen as an important catalyst for unifying the dozens of serverless platforms in the market.
Knative is seen as an important catalyst for unifying the dozens of serverless platforms in the market.
Testing notes: simulating link failure by filtering BFD packets
In some testing I am doing, I need to prove that BFD can be used with iBGP to tell the BGP protocol when there is an interruption. This will enable BGP to be brought down much faster than if regular BGP timers are used.
To make this easier to do, I used a firewall filter on one of the two routers to filter out BFD but accept all other packets:
Single-hop BFD (i.e. across a link) uses UDP 3784, while multi-hop BFD uses 4784. Since my BFD sessions are configured between loopbacks, it is this latter type I need to filter.
In the example below, CORE1 is a BGP client of CORE2, which is the route-reflector.
The following was configured on the routers to bring up the BFD session (I am only showing one side – you can figure out the mirror of this yourself I think):
[edit protocols bgp group CORE neighbor 10.0.0.6]
bfd-liveness-detection {
minimum-receive-interval 300;
multiplier 3;
transmit-interval {
minimum-interval 100;
}
}
When the remote side was done, the session came up:
axians@CORE1> show bfd session Dec 28 17:17:10 Detect Transmit Address State Interface Time Interval Multiplier 10.0. Continue reading
Networking Vendors Jump On 400GbE in 2018
 The 400GbE standard is four times as fast as 100 gig Ethernet, and it offers an economically attractive price-per-port and better power efficiency.
The 400GbE standard is four times as fast as 100 gig Ethernet, and it offers an economically attractive price-per-port and better power efficiency.
Top 5 Blog Post 2018: Simplifying Kubernetes with Docker Compose and Friends
All this week we’ve been bringing you the top 5 blog posts for 2018 –coming in at #1 is our post on open sourcing our Docker Compose on Kubernetes capability. This new capability enables you to simplify the Kubernetes experience. To learn more, continue reading…
Today we’re happy to announce we’re open sourcing our support for using Docker Compose on Kubernetes. We’ve had this capability in Docker Enterprise for a little while but as of today you will be able to use this on any Kubernetes cluster you choose.

Why do I need Compose if I already have Kubernetes?
The Kubernetes API is really quite large. There are more than 50 first-class objects in the latest release, from Pods and Deployments to ValidatingWebhookConfiguration and ResourceQuota. This can lead to a verbosity in configuration, which then needs to be managed by you, the developer. Let’s look at a concrete example of that.
The Sock Shop is the canonical example of a microservices application. It consists of multiple services using different technologies and backends, all packaged up as Docker images. It also provides example configurations using different tools, including both Compose and raw Kubernetes configuration. Let’s have a look Continue reading
LibreRouter: A Multi-Radio Wireless Router for Community Networks
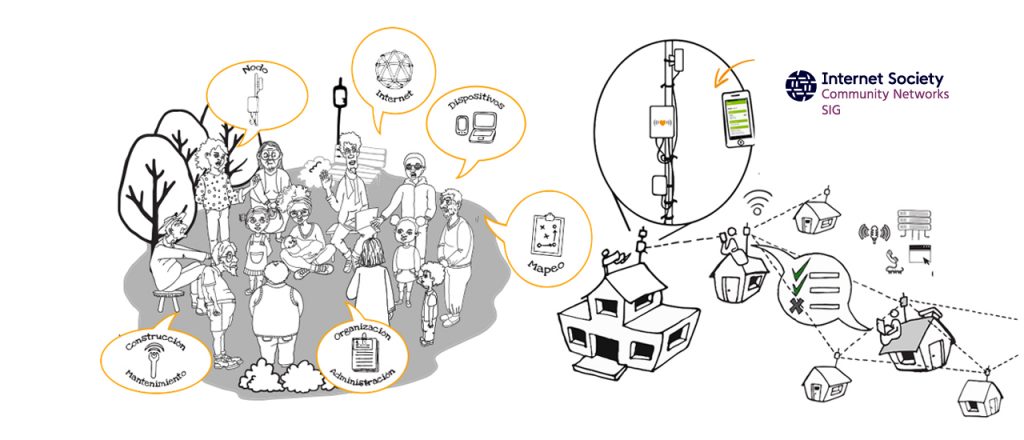
Since their inception, community networks have depended on modifying existing off-the-shelf routers to adapt them to their particular needs. Software development originated in community-network groups and the free software movement as a whole have pushed the barrier of innovation and helped commercial enterprises develop new products over the years.
The LibreRouter, created by the collaboration of the Internet Society Community Networks Special Interest Group (CNSIG) and AlterMundi with the support of Beyond the Net Funding Programme, is an open-source hardware WiFi router designed for the specific needs of community networks.
The LibreRouter Project works to achieve autonomy and technological sovereignty that allows deploying, managing, scaling, and sustaining community networks. The reality is that community networks are not a profitable market segment for the industry. This means that the equipment used is not adequate to solve the particular needs they have. To manufacture the equipment you have to be encouraged to understand it and do it in a different and integral way.
Besides the hardware development, the most important part of this project is the integral work that involves software solutions and documentation material. It’s an important work focused on the communities themselves having the capabilities to deploy their Continue reading
SD-WAN – Glorified DMVPN?
I had an interesting discussion with Jon Cooper in the Network Collective Slack. The discussion was around SD-WAN. We were discussing if SD-WAN is just a “glorified DMVPN” or if it’s something more than that. Note that this was a bit tongue in cheek comment from Jon but it’s interesting for the sake of discussion.
To compare the two, let’s look at some of the design and operational challenges of running a DMVPN.
Physical design – How many Hub routers do you need? In a DMVPN, the Hub router is a special type of device that is responsible for mapping the underlay IP address to the overlay IP address. If a Hub needs to be added, this Next Hop Server (NHS) needs to be added to the spokes. With Cisco SD-WAN, this is handled by the vBond which is a virtual machine running in a public cloud. Adding a device is simple as the WAN edge routers use a hostname (DNS) to ask for the IP of the vBond. This means that the physical design is less rigid.
Logical design – In a DMVPN, you need to decide on the number of DMVPN clouds. Do you do a single cloud Continue reading
Who Went Where: The Top Personnel Changes of 2018
 From Hans Vestberg’s quick rise at Verizon to Google Cloud’s leadership shakeup, this year was full of personnel changes that turned heads.
From Hans Vestberg’s quick rise at Verizon to Google Cloud’s leadership shakeup, this year was full of personnel changes that turned heads.
The Year in Review: Governments Try to Restrict Free Speech Online and Break Encryption

In 2018, the Internet saw concerted government efforts to restrict free speech on the Internet – some in the name of fighting “fake news” – and to compromise encryption on devices and messaging apps.
Can the government decide what’s fake news? Several countries either passed or explored laws intended to combat so-called fake news and online disinformation. In some cases, the laws contained significant prison time for those who create or disseminate fake news.
The problem, of course, is that the government decides what’s fake and what’s legitimate news. Free speech advocates have warned that the anti-fake news laws amount to censorship, with government officials playing content gatekeepers.
In Malaysia, the fake news law was quickly used to investigate an opponent of the administration in power. Malaysia repealed its anti-fake news law about four months after it passed, when opposition leader Mahathir Mohamad, one of the first people invested under the law, became prime minister.
In November, France passed its own anti-fake news law, allowing judges to determine fake news and order its removal. Distributors of news determined to be fake can face one year of prison time. India also considered but abandoned a fake news law earlier this Continue reading
Improving request debugging in Cloudflare Workers
At Cloudflare, we are constantly looking into ways to improve development experience for Workers and make it the most convenient platform for writing serverless code.
As some of you might have already noticed either from our public release notes, on cloudflareworkers.com or in your Cloudflare Workers dashboard, there recently was a small but important change in the look of the inspector.
But before we go into figuring out what it is, let's take a look at our standard example on cloudflareworkers.com:
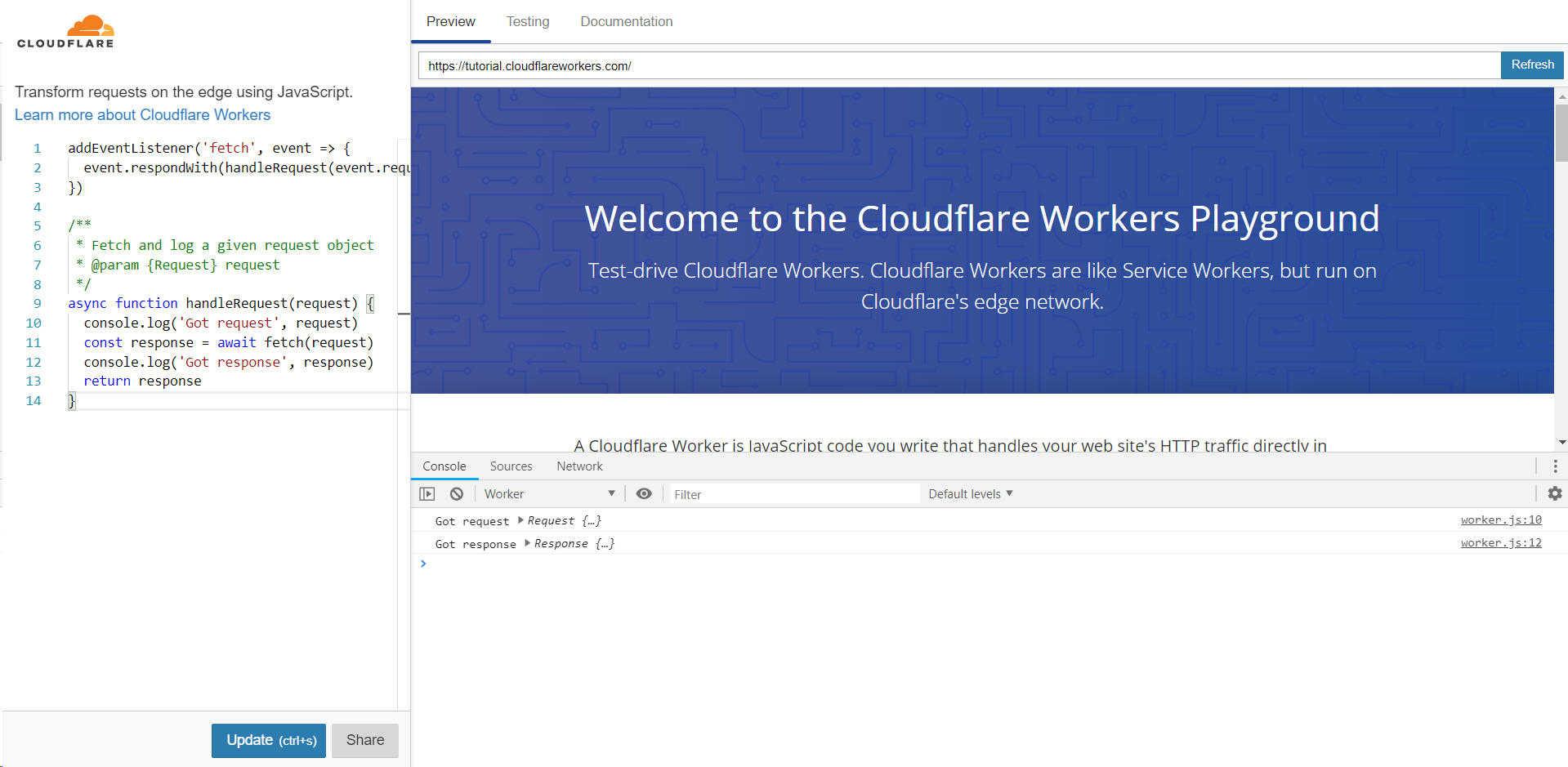
The example worker code featured here acts as a transparent proxy, while printing requests / responses to the console.
Commonly, when debugging Workers, all you could see from the client-side devtools is the interaction between your browser and the Cloudflare Worker runtime. However, like in most other server-side runtimes, the interaction between your code and the actual origin has been hidden.
This is where console.log comes in. Although not the most convenient, printing random things out is a fairly popular debugging technique.
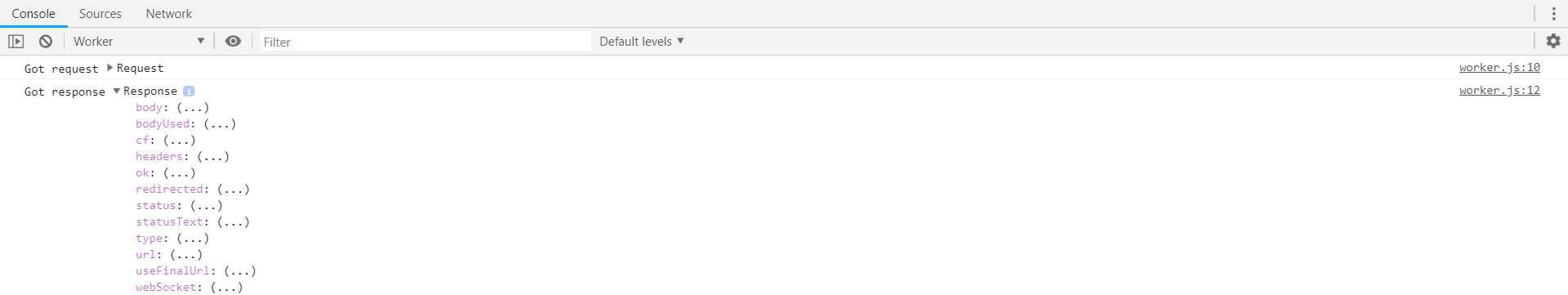
Unfortunately, its default output doesn't help much with debugging network interactions. If you try to expand either of request or response objects, all you can see is just a bunch of lazy accessors:
Will Cisco Viptela continue to be one of the Leaders in SD-WAN ?
In 2017, Cisco completed Viptela acquisition. It is not a surprise for me that Gartner published Cisco as the Leader in WAN Edge Infrastructure in 2018. This is Gartner’s famous Magic Quadrant report. I wrote a post for Silverpeak before. Silverpeak is listed in the Leaders category. Three vendors presented their solutions and I …
Continue reading "Will Cisco Viptela continue to be one of the Leaders in SD-WAN ?"
The post Will Cisco Viptela continue to be one of the Leaders in SD-WAN ? appeared first on Cisco Network Design and Architecture | CCDE Bootcamp | orhanergun.net.
Looking Back: 2018 Project Report Card
Over the last five years or so, I’ve shared with my readers an annual list of projects along with—at the year’s end—a “project report card” on how I fared against the projects I’d set for myself. (For example, here’s my project report card for 2017.) Following that same pattern, then, here is my project report card for 2018.
Here’s the list of projects I established for myself in 2018 (you can also read the associated blog post for more context):
- Become extremely fluent in Kubernetes. (Stretch goal: Pass the CKA exam.)
- Learn to code/develop in Go.
- Make three contributions to open source projects. (Stretch goal: Make five contributions.)
- Read and review three technical books. (Stretch goal: Read and review five technical books.)
- Complete a “wildcard” project.
So, how did I do? Let’s take a look.
Become extremely fluent in Kubernetes: This is, in my opinion, a hard one to accurately gauge. Why? Well, Kubernetes is a pretty massive project. I saw a tweet recently saying the project was now at a point where no one person can understand all of it. The other factor making it difficult for me to accurately gauge this is the caliber Continue reading
One Byte at a Time – Protocol Analysis
The cornerstone of effective troubleshooting is based on having clear data points. That way we can compare these values before and after the change and prove the true impact.
DNS-over-TLS in Linux (systemd)

Whilst we were putting together some content about DNS privacy recently, we learned that recent distributions of Linux ship with support or this. We therefore decided to give Ubuntu 18.10 a try on a laptop.
More recent versions of Ubuntu employ a special service for name resolution called ‘system-resolved.service(8)’. The configuration file ‘resolved.conf(5)’ specifies most of the details for name resolution, including which protocols and resolvers should be employed, whilst the ‘/etc/systemd/network/*.network’ configuration files (see ‘systemd.network(5)’ for details) of the ‘systemd-networkd.service(8)’ specify any per-link specific settings.
The default configuration of ‘systemd-resolved’ is selected at compile time, and ‘/etc/systemd/resolved.conf’ normally contains commented-out lines describing such defaults. For example, the contents of the aforementioned file on a fresh Ubuntu 18.10 installation are:
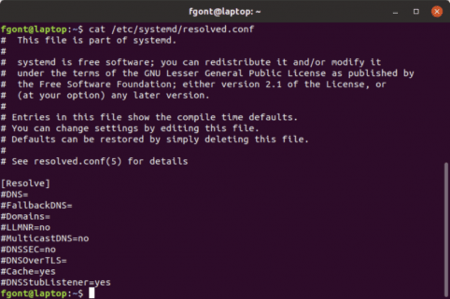
As may be inferred from the file, DNS-over-TLS (DoT) is supported, but disabled by default. At the time of writing, only opportunistic DoT is supported according to the manual, which means that the resolver will first try resolution using DoT before falling back to traditional DNS in the event of failure – thus allowing for downgrade attacks where an attacker intentionally causes a DoT failure in order to cause name resolution to downgrade Continue reading
IPv6 Buzz 016: Happy Holidays With IPv6 Haiku
Thanks to everyone that tuned in this year! We're looking forward to bringing you more IPv6 Buzz in 2019!IPv6 Buzz 016: Happy Holidays With IPv6 Haiku
Thanks to everyone that tuned in this year! We're looking forward to bringing you more IPv6 Buzz in 2019!
The post IPv6 Buzz 016: Happy Holidays With IPv6 Haiku appeared first on Packet Pushers.
لمحة عامة حول حوكمة الإنترنت (General Overview about Internet Governance)

تلقى ملايين المستخدمين عبر فيسبوك مؤخراً رسائل تفيد بأن بياناتهم الشخصية قد تسربت بسبب اختراق Cambridge Analytica لها، يأتي هذا بعد أن كشفت صحيفة Observer أن Cambridge Analytica ، التي عملت مع فريق دونالد ترامب الانتخابي استحوذت على ملايين الحسابات الشخصية لمواطنين أمريكيين واستخدمت بياناتهم لبناء برنامج حاسوبي للتنبؤ بالناخبين والتأثير عليهم.
التصدي للمشاكل والقضايا التي تخص الانترنت بما فيها قضايا الأمن والخصوصية ليس بالأمر السهل ليس فقط بسبب النمو والتطور الكبير لهذه الشبكة والأثر الكبير الذي أحدثته على شتى القطاعات ونواحي الحياة، بل أيضاً بسبب طبيعته اللامركزية أي أنه شبكة غير محكومة بسلطة مركزية واحدة تقوم بإدارة الإنترنت وحدها.
الإنترنت هو ثمرة جهود مشاريع بحثية مولتها الحكومة وجهود أفراد من الجامعات ومنظمات القطاع الخاص الذين قادوا معظم تطوره المبكر وجعلوا منه منصة قائمة على تعاون مختلف الجهات والأطراف المهتمة بالأنترنت والمتأثرة بقراراته والتي تساهم في وضع سياساته. نرى في جزء آخر من العالم التصدي لمشاكل الخصوصية وحماية البيانات الشخصية في إقرار المجلس الأوروبي لقانون حماية البيانات العامة للاتحاد الأوروبي (GDPR)، وذلك بعد سلسلة من النقاشات دامت حوالي أربع أعوام من أجل ضمان أمن بيانات الأفراد ضمن الاتحاد الأوروبي. يمكننا أن نعبر عن العمليات القائمة بين أصحاب المصالح المتعددين والتي تؤثر على كيفية إدارة الإنترنت “بحوكمة الإنترنت”.
في سياق Continue reading
In Khartoum, A DNSSEC Deployathon

At the Internet Society Sudan Chapter office, adjacent to the west bank of the Blue Nile, four men decided to set up a local server capable of DNSSEC verification. It was an unplanned deployathon: a hands on, practical session in which a solution or service is deployed in a real-world scenario. Deployathons can help build technical capacity or set up a new service, and in this case, the men hoped to increase knowledge of DNSSEC and to prepare the individuals managing Sudan’s top-level domain (.sd) for signing in the near future.
During the SdNOG5 conference, these four men – we the authors, along with Jan Zorz of the Internet Society and Sander Steffann – continued the discussion on the deep technical challenges of deploying DNSSEC, and how Jan and Sander’s presence in Sudan provided an opportunity to leverage their experience with DNSSEC. We also reflected on the importance of DNSSEC for the country code top-level domain (ccTLD) and its positive impact on the national and international levels.

Having enjoyed some delicious Sudanese coffee, the four of us started to install a new server based on Centos 7, a Linux based operating system, from scratch. On this server, a DNS service Continue reading
