IBM, Nvidia Team Up on Converged Storage for AI Workloads
 The new converged infrastructure combines IBM’s NVMe flash storage and software with Mellanox networking on Nvidia servers. It also uses Nvidia’s AI software stack.
The new converged infrastructure combines IBM’s NVMe flash storage and software with Mellanox networking on Nvidia servers. It also uses Nvidia’s AI software stack.
Podcast: The State of Packet Forwarding
 Enterprise network architectures are being reshaped using tenets popularized by the major cloud properties. This podcast explores this evolution and looks at the ways that real-time streaming telemetry, machine learning, and artificial intelligence affect how networks are designed and operated.
Enterprise network architectures are being reshaped using tenets popularized by the major cloud properties. This podcast explores this evolution and looks at the ways that real-time streaming telemetry, machine learning, and artificial intelligence affect how networks are designed and operated.
GSMA Highlights Potential $565B GDP Boost From the ‘Right’ 5G Spectrum
 The mobile operator association uses GDP and tax arguments to persuade governments to support the allocation of sufficient mmWave spectrum for 5G at WRC-19.
The mobile operator association uses GDP and tax arguments to persuade governments to support the allocation of sufficient mmWave spectrum for 5G at WRC-19.
Napatech and Intel Partner on FPGA Technology for Standard Servers
 The big hyperscalers use field programmable gate array technology on standard servers in their data centers. But there’s a trend for other enterprises to emulate these hyperscalers.
The big hyperscalers use field programmable gate array technology on standard servers in their data centers. But there’s a trend for other enterprises to emulate these hyperscalers.
IBM’s JEDI Protest Dismissed, Oracle Takes the $10B Pentagon Cloud Deal to Court
 Oracle’s lawsuit alleges conflicts of interest and says two people involved in the procurement process have close ties to Amazon Web Services.
Oracle’s lawsuit alleges conflicts of interest and says two people involved in the procurement process have close ties to Amazon Web Services.
Verizon, Reliance Jio, TIM Join the O-RAN Alliance
 Verizon and Jio were both original members of the xRAN Forum, which merged with the C-RAN Alliance this year to form O-RAN.
Verizon and Jio were both original members of the xRAN Forum, which merged with the C-RAN Alliance this year to form O-RAN.
Datanauts 153: Understanding Metadata For IT Operations
What is metadata, and why should IT practitioners care? How is metadata stored? What impact does metadata have on enterprise IT storage? We answer these questions and more on today’s Datanauts podcast with guest Karen Lopez.
The post Datanauts 153: Understanding Metadata For IT Operations appeared first on Packet Pushers.
Episode 41 – The Value of Networking Labs for Production
If you’ve been in networking for any time, you’ve likely had to lab something up to learn a new technology or study for a certification, but labs can be so much more than learning tools. In today’s episode Jody Lemoine and Iain Leiter join Network Collective to talk about practical uses for labs outside of the classroom.
 We would like to thank VIAVI Solutions for sponsoring this episode of Network Collective. VIAVI Solutions is an application and network management industry leader focusing on end-user experience by providing products that optimize performance and speed problem resolution. Helping to ensure delivery of critical applications for businesses worldwide, Viavi offers an integrated line of precision-engineered software and hardware systems for effective network monitoring and analysis. Learn more at www.viavisolutions.com/networkcollective.
We would like to thank VIAVI Solutions for sponsoring this episode of Network Collective. VIAVI Solutions is an application and network management industry leader focusing on end-user experience by providing products that optimize performance and speed problem resolution. Helping to ensure delivery of critical applications for businesses worldwide, Viavi offers an integrated line of precision-engineered software and hardware systems for effective network monitoring and analysis. Learn more at www.viavisolutions.com/networkcollective.
Outro Music:
Danger Storm Kevin MacLeod (incompetech.com)
Licensed under Creative Commons: By Attribution 3.0 License
http://creativecommons.org/licenses/by/3.0/
The post Episode 41 – The Value of Networking Labs for Production appeared first on Network Collective.
VMware Warns That 3 Hurdles Prevent Mass Kubernetes Adoption
 In order for Kubernetes to infiltrate more than 100,000 organizations, the ecosystem needs to tackle business cases, management, and training.
In order for Kubernetes to infiltrate more than 100,000 organizations, the ecosystem needs to tackle business cases, management, and training.
More consistent LuaJIT performance
This is a guest post by Laurence Tratt, who is a programmer and Reader in Software Development in the Department of Informatics at King's College London where he leads the Software Development Team. He is also an EPSRC Fellow.
A year ago I wrote about a project that Cloudflare were funding at King's College London to help improve LuaJIT. Our twelve months is now up. How did we do?
The first thing that happened is that I was lucky to employ a LuaJIT expert, Thomas Fransham, to work on the project. His deep knowledge about LuaJIT was crucial to getting things up and running – 12 months might sound like a long time, but it soon whizzes by!
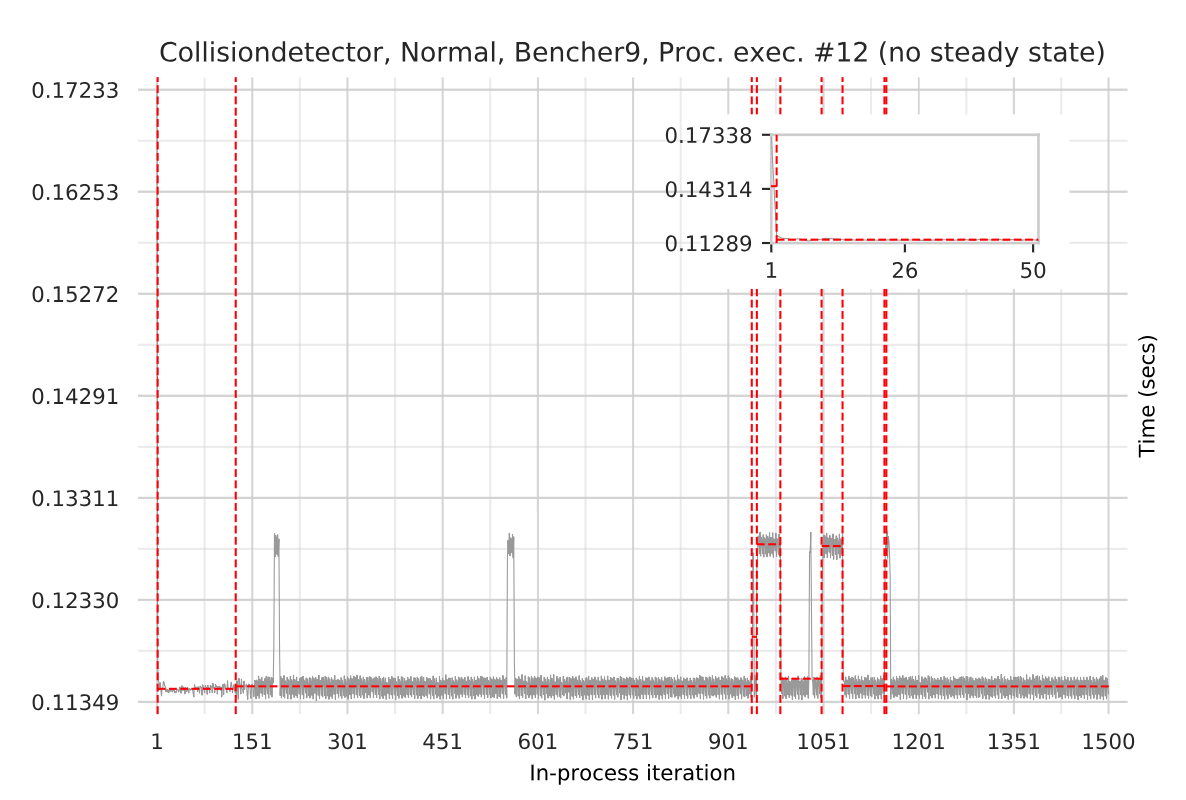
The second thing that happened was that we realised that the current state of Lua benchmarking was not good enough for anyone to reliably tell if they'd improved LuaJIT performance or not. Different Lua implementations had different benchmark suites, mostly on the small side, and not easily compared. Although it wasn't part of our original plan, we thus put a lot of effort into creating a larger benchmark suite. This sounds like a trivial job, but it isn't. Many programs make Continue reading
KubeCon 2018 Day 2 Keynote
This is a liveblog of the day 2 (Wednesday) keynotes at KubeCon/CloudNativeCon 2018 in Seattle, WA. For additional KubeCon 2018 coverage, check out other articles tagged KubeCon2018.
Kicking off the day 2 keynotes, Liz Rice takes the stage at 9:02am (same time as yesterday, making me wonder if my clock is off by 2 minutes). Rice immediately brings out Janet Kuo, Software Engineer at Google and co-chair with Rice of the KubeCon/CloudNativeCon event program. Kuo will be delivering a Kubernetes project update.
Kuo starts off by reiterating the announcement of the Kubernetes 1.13 release, and looking back on her very first commit to Kubernetes in 2015 (just prior to the 1.0 release and the formation of the CNCF). Kuo talks about how Kubernetes, as a software cycle, has matured through the cycle of first focusing on innovation, then expanding to include scale, and finally expanding again to include stability (critical for enterprise adopters).
Reviewing usage details, Kuo states that she believes Kubernetes has moved—in the context of the technology adoption curve—from early adopters to early majority, the first phase in the mainstream market (and, for those who think in these terms, has crossed the chasm). However, this also Continue reading
Video: Top 10 Misconceptions About 5G For Beginners

Breaks down the reality and practical considerations so that you can decode whether someone in marketing wrote those hypetastic 5G articles that you see everywhere.
The post Video: Top 10 Misconceptions About 5G For Beginners appeared first on EtherealMind.



